Anti-theft method and anti-theft system for mobile terminal, mobile terminal and anti-theft device
A technology of mobile terminals and anti-theft devices, applied in location-based services, advanced technologies, electrical components, etc., can solve problems such as single setting and inability to automatically set the working status of alarm devices, so as to save energy and ensure timeliness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
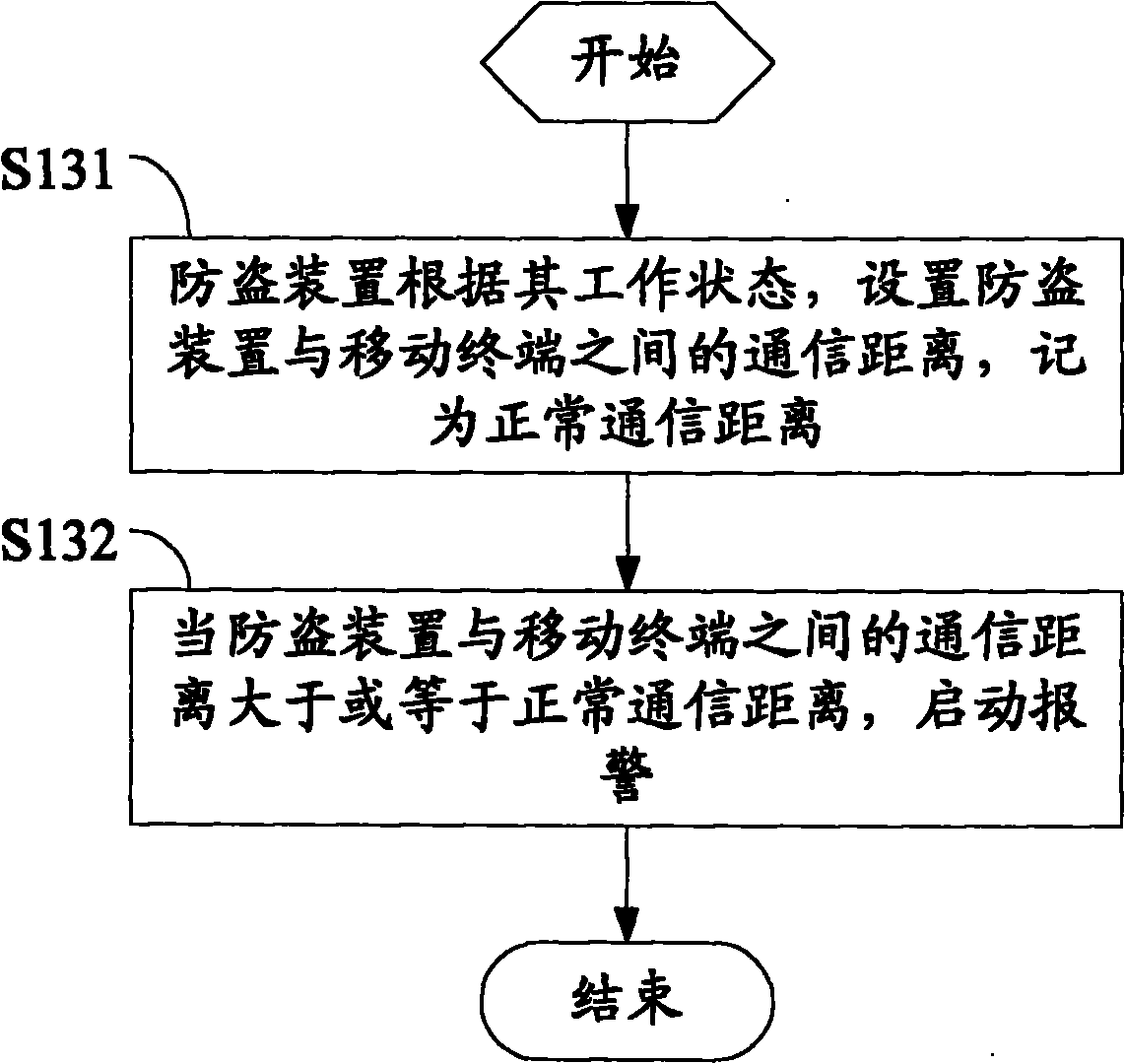
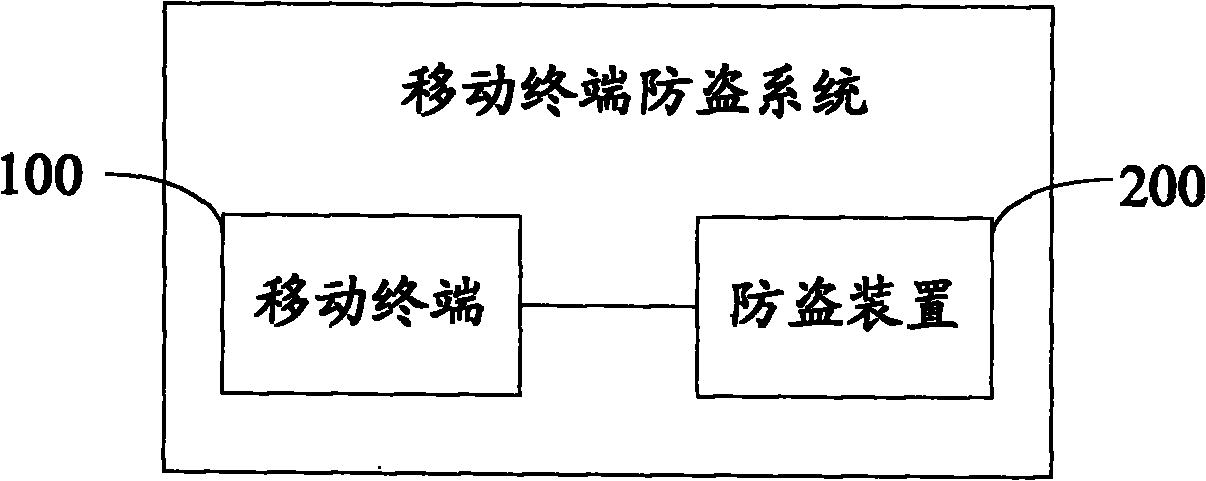
[0049] The invention dynamically adjusts the anti-theft working state according to the different geographical areas, so that the mobile terminal and the anti-theft device communicate according to the anti-theft working state, and perform corresponding anti-theft operations.
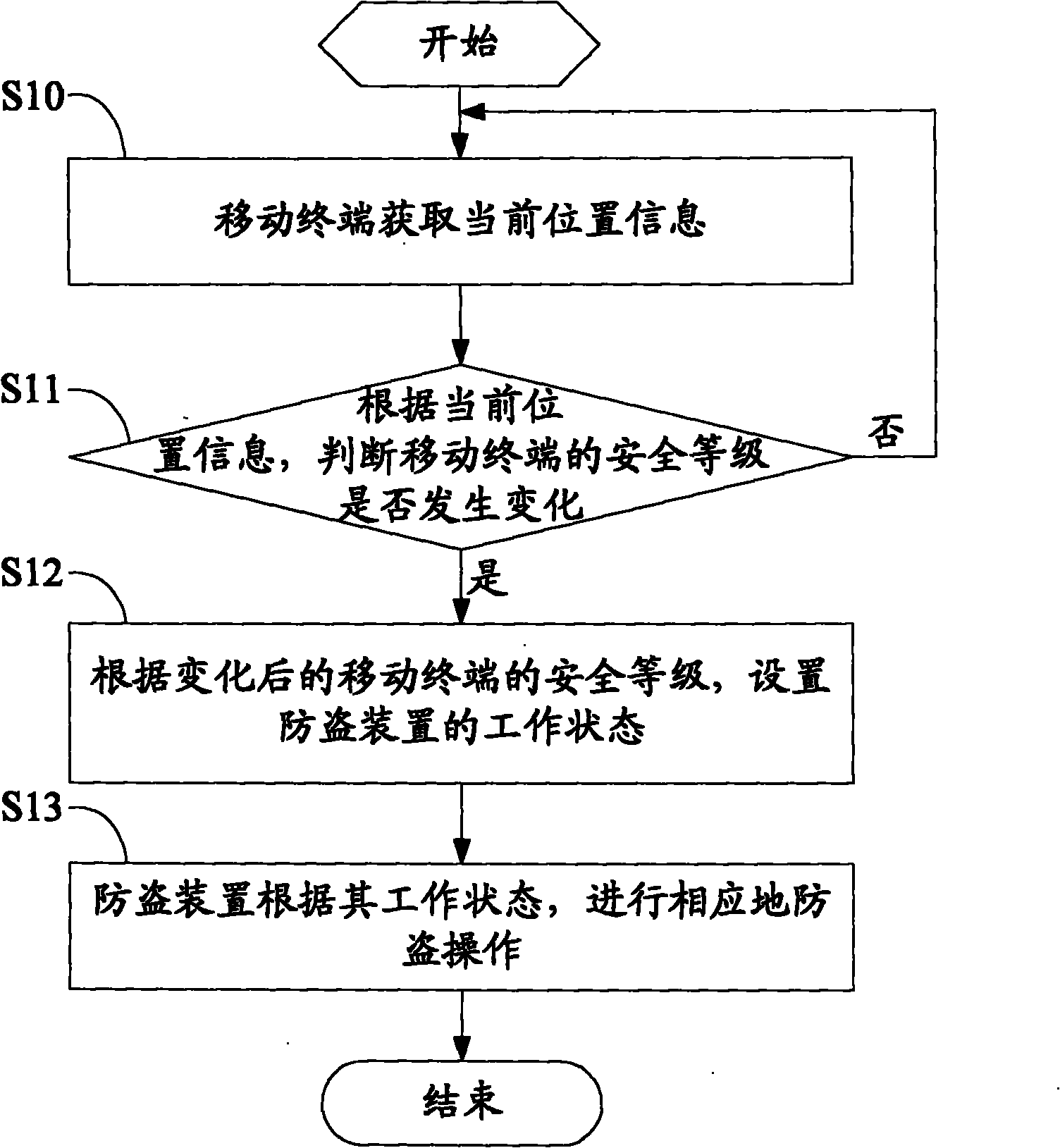
[0050] figure 1 It is a schematic flowchart of an embodiment of the mobile terminal anti-theft method of the present invention.
[0051] The mobile terminal anti-theft method of this embodiment includes the following steps:
[0052] Step S10, the mobile terminal acquires current location information;
[0053] The current location information of the mobile terminal can first obtain the geographic location on the network side (that is, a large-scale regional location) through the mobile terminal, and then control the GPS navigation module to obta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com