Method for detecting flooding attack by wireless self-organizing network route query
A wireless self-organization and flooding attack technology, applied in wireless communication, network topology, electrical components, etc., can solve problems such as mistaking attack nodes, multi-route query messages, detection effect dependence, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments.
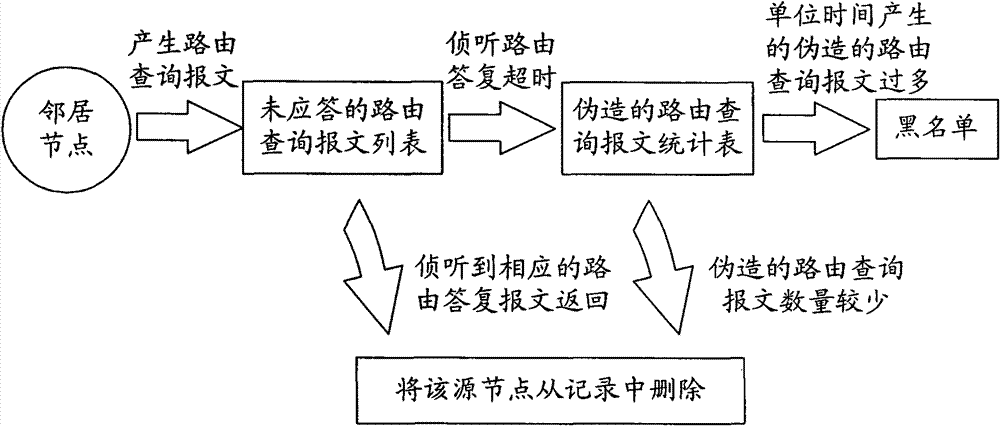
[0025] See Figure 1 ~ Figure 4 , Introduce the detection method of the wireless ad hoc network routing query message flooding attack of the present invention. The method includes the following operation steps:
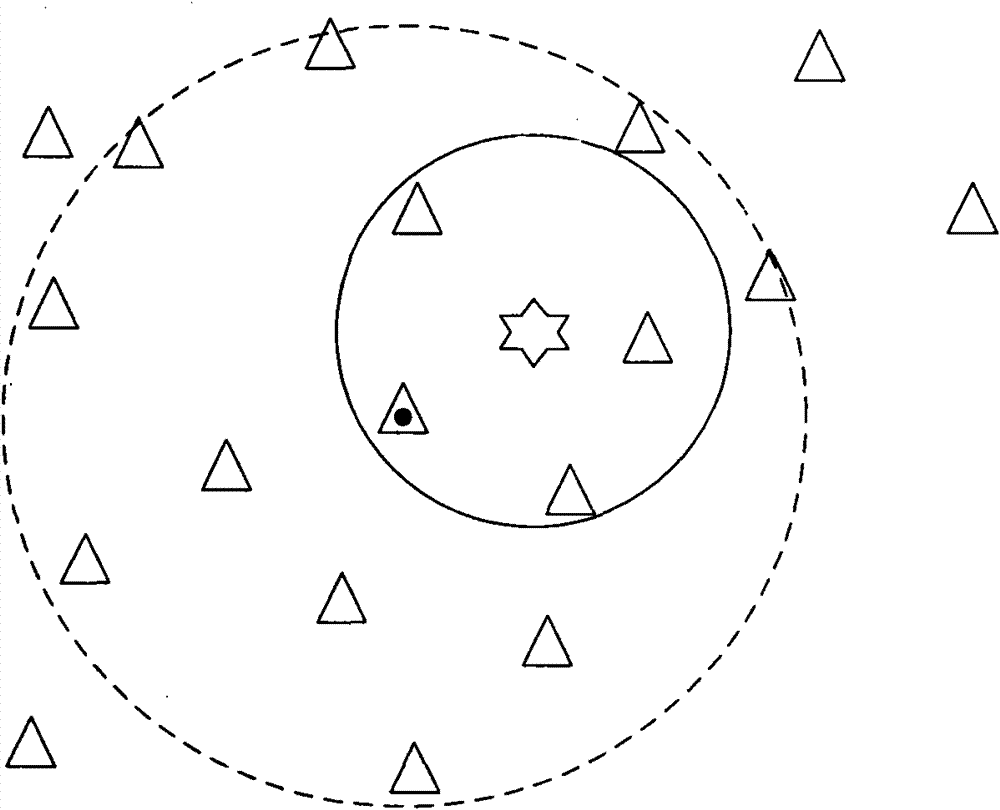
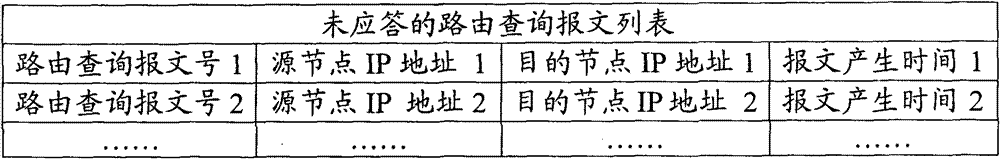
[0026] Step 1. In a wireless ad hoc network using reactive routing protocols, each node monitors and counts the routing query messages generated by its surrounding nodes (see figure 1 Shown), and listen to each routing query message whether there is a routing reply message: when a routing query source node ( figure 1 , Which is represented by a six-pointed star) generates a routing query message and broadcasts it, the neighboring nodes around it (that is, the one-hop node on the route, figure 1 The middle is represented by a triangle, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com