Method for reading attributes from an ID token
A technology for marking cards, attributes, used in the activation of coded identification cards or credit cards, coin-free or similar appliances, digital data authentication, etc., can solve problems such as insufficient data protection, achieve a high level of trust, convenience processing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
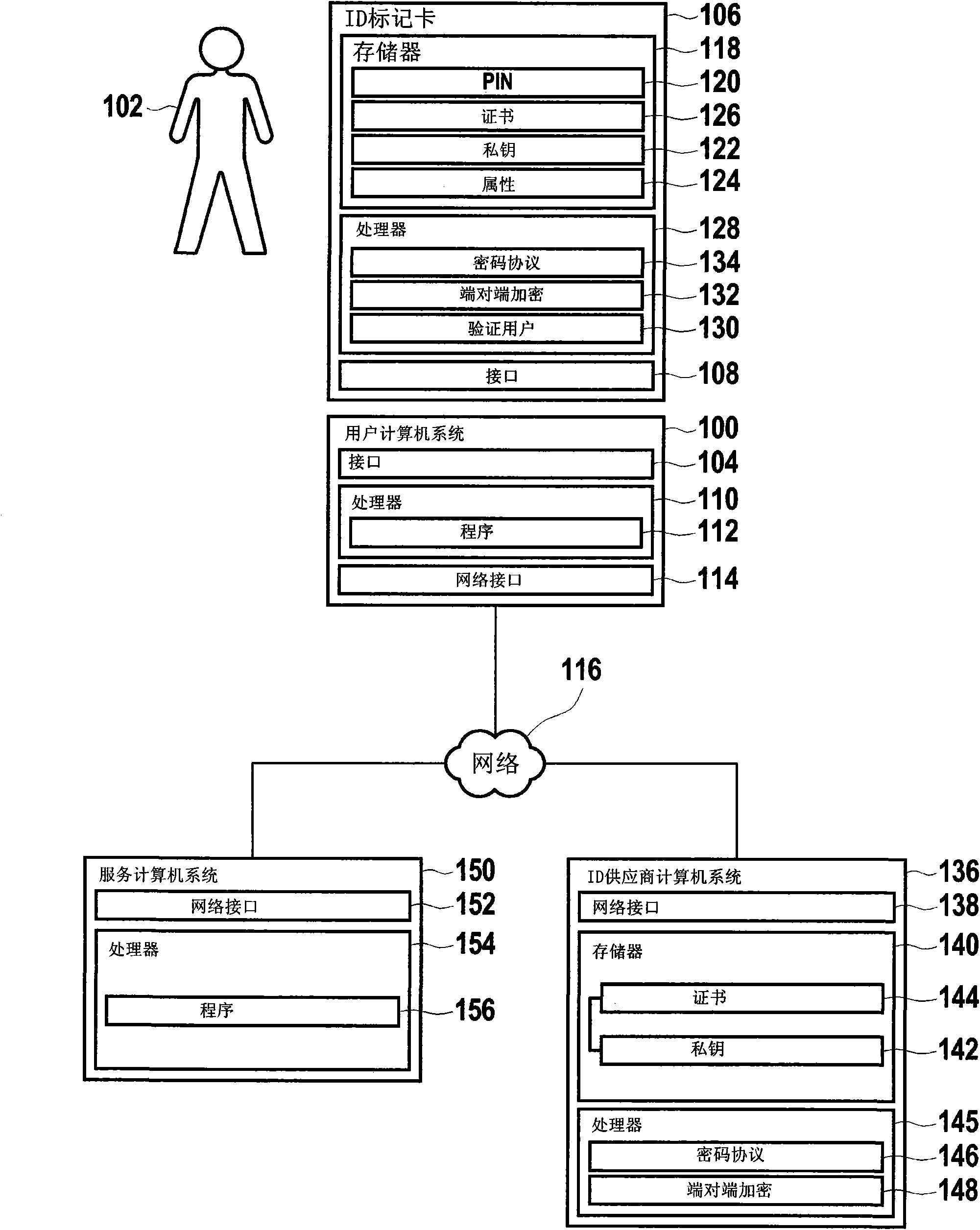
[0039] figure 1 A user computer system 100 of a user 102 is shown. The user computer system 100 may be a personal computer, a portable computer such as a laptop or a palmtop, a personal electronic organizer, a mobile communication device, especially a smart phone, or the like. The user computer system 100 has an interface 104 for communicating with an ID token 106 having a corresponding interface 108 .
[0040] The user computer system 100 has at least a processor 110 for executing program instructions 112 and a network interface 114 for communicating via a network 116 . The network may be a computer network, such as the Internet.
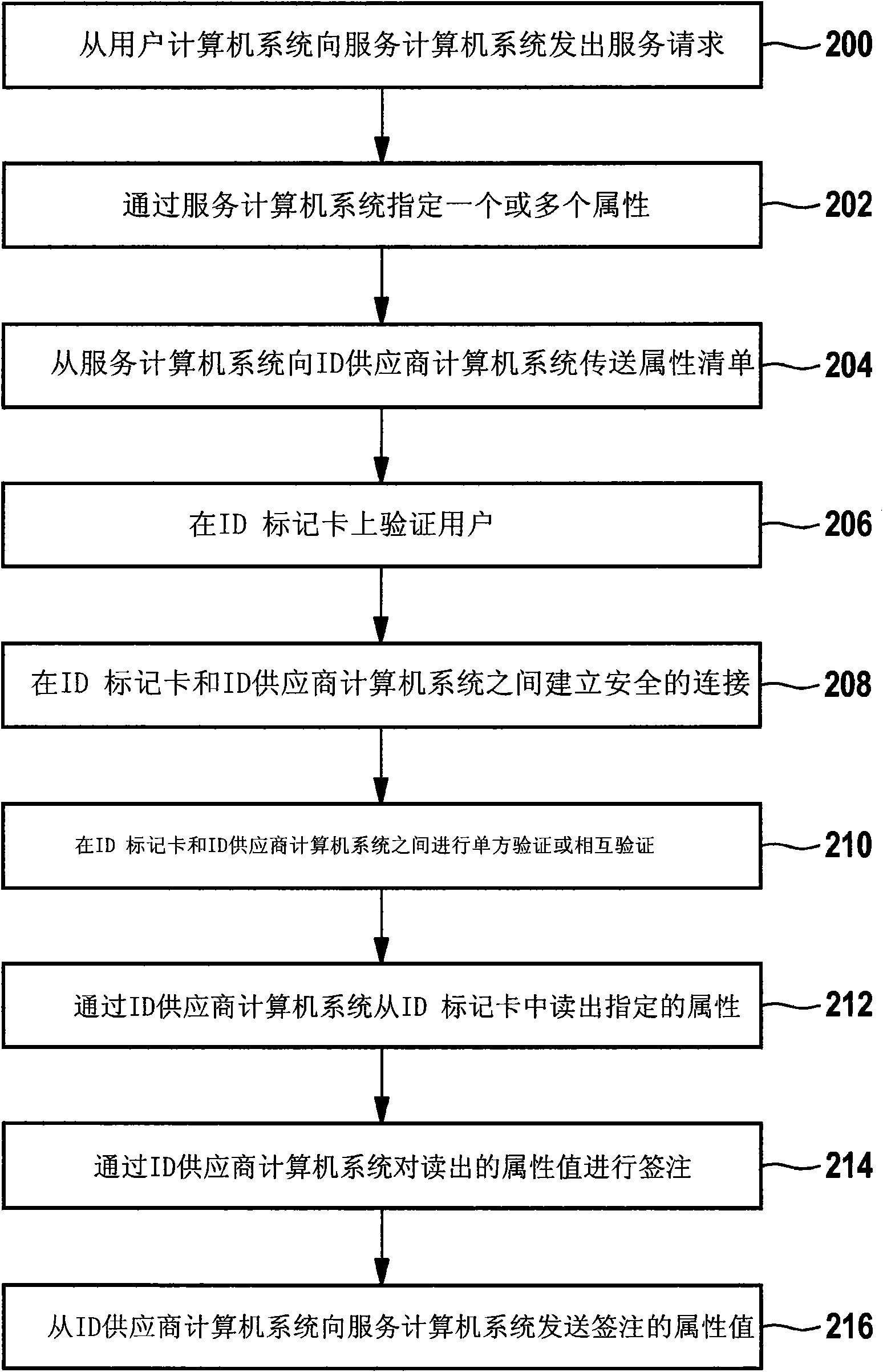
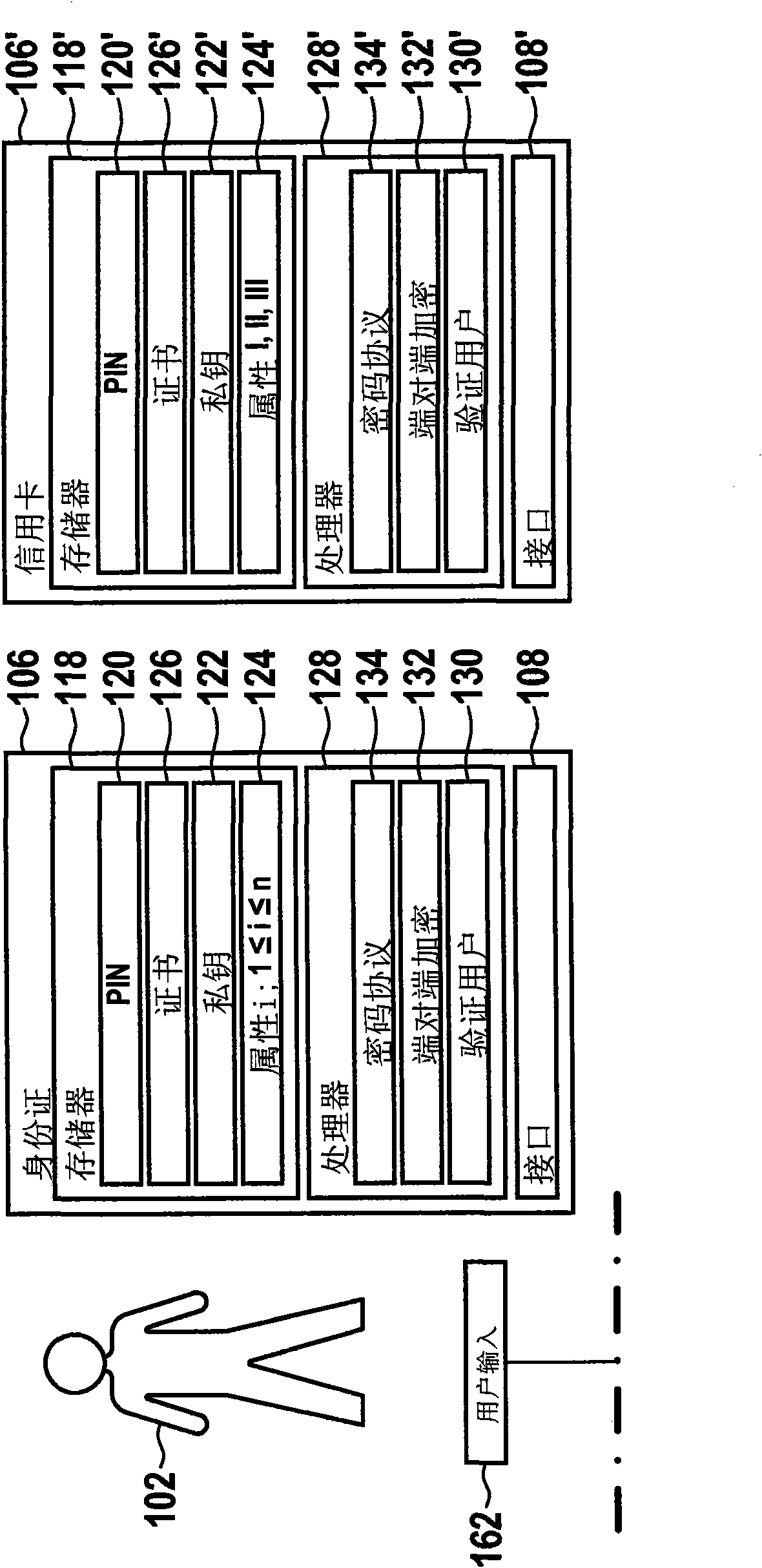
[0041] ID token 106 has electronic memory 118 with protected storage areas 120 , 122 and 124 . Protected memory area 120 is used to store a parameter value (Referenzwert), which is required for authenticating user 102 on ID token 106 . For example, the parameter value is an identifier, in particular a so-called personal identification number (P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com