Content recommending method and device based on user characteristics
A technology of user equipment and user characteristics, applied in the network field, can solve problems such as less recommended content, inability to obtain interesting content in a timely and effective manner, and inability to share information and content, so as to promote information dissemination and improve user experience Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings.
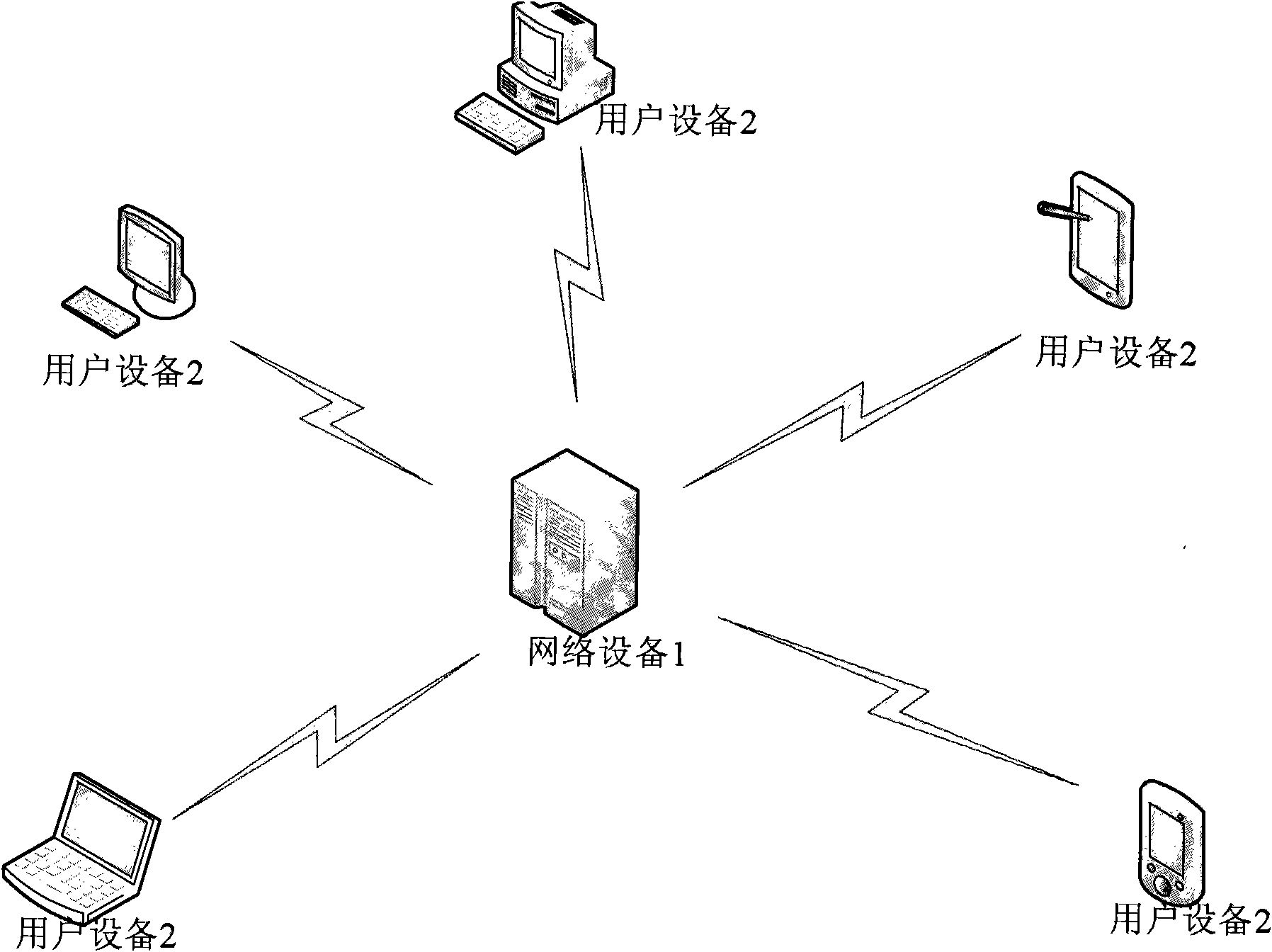
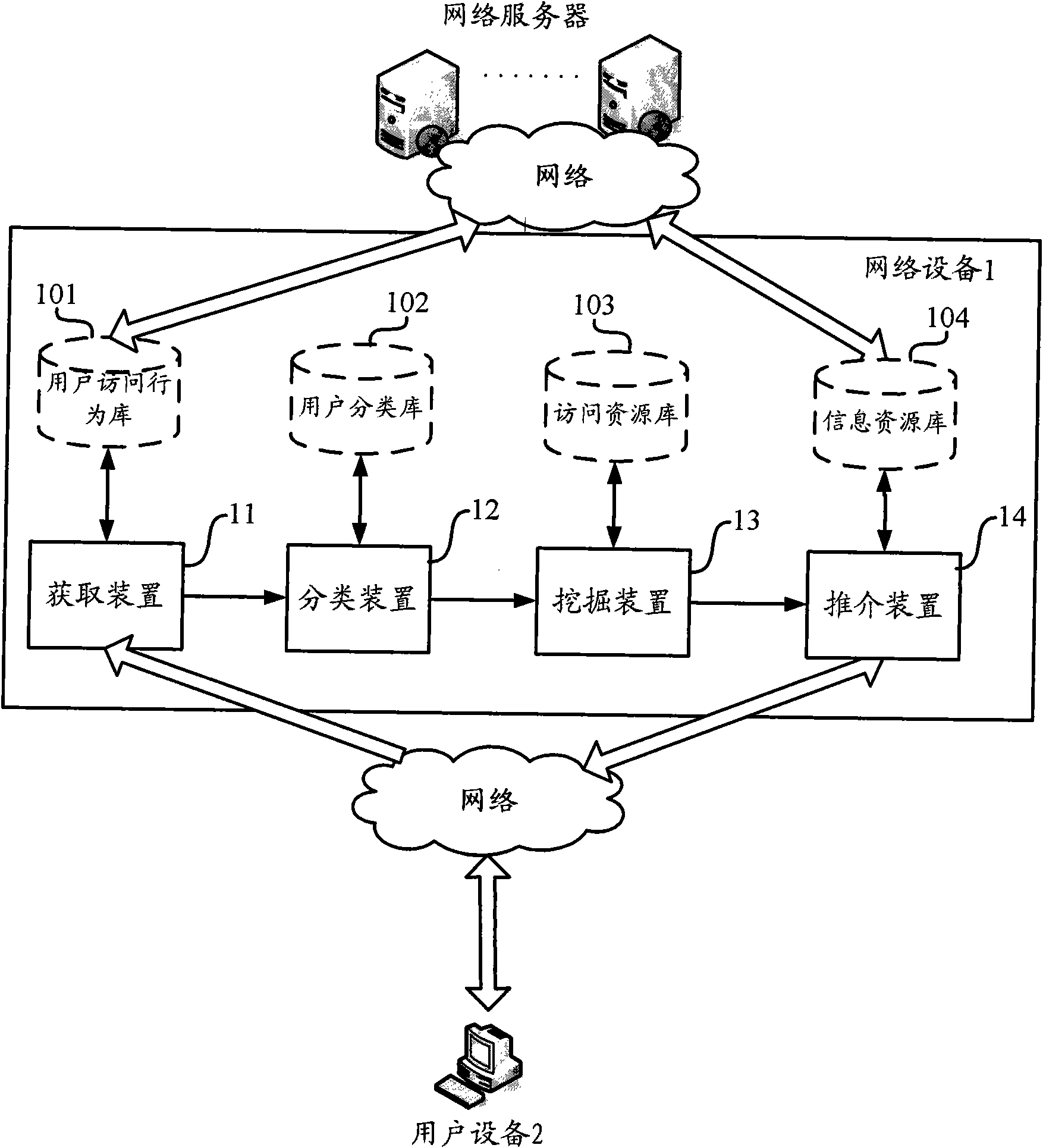
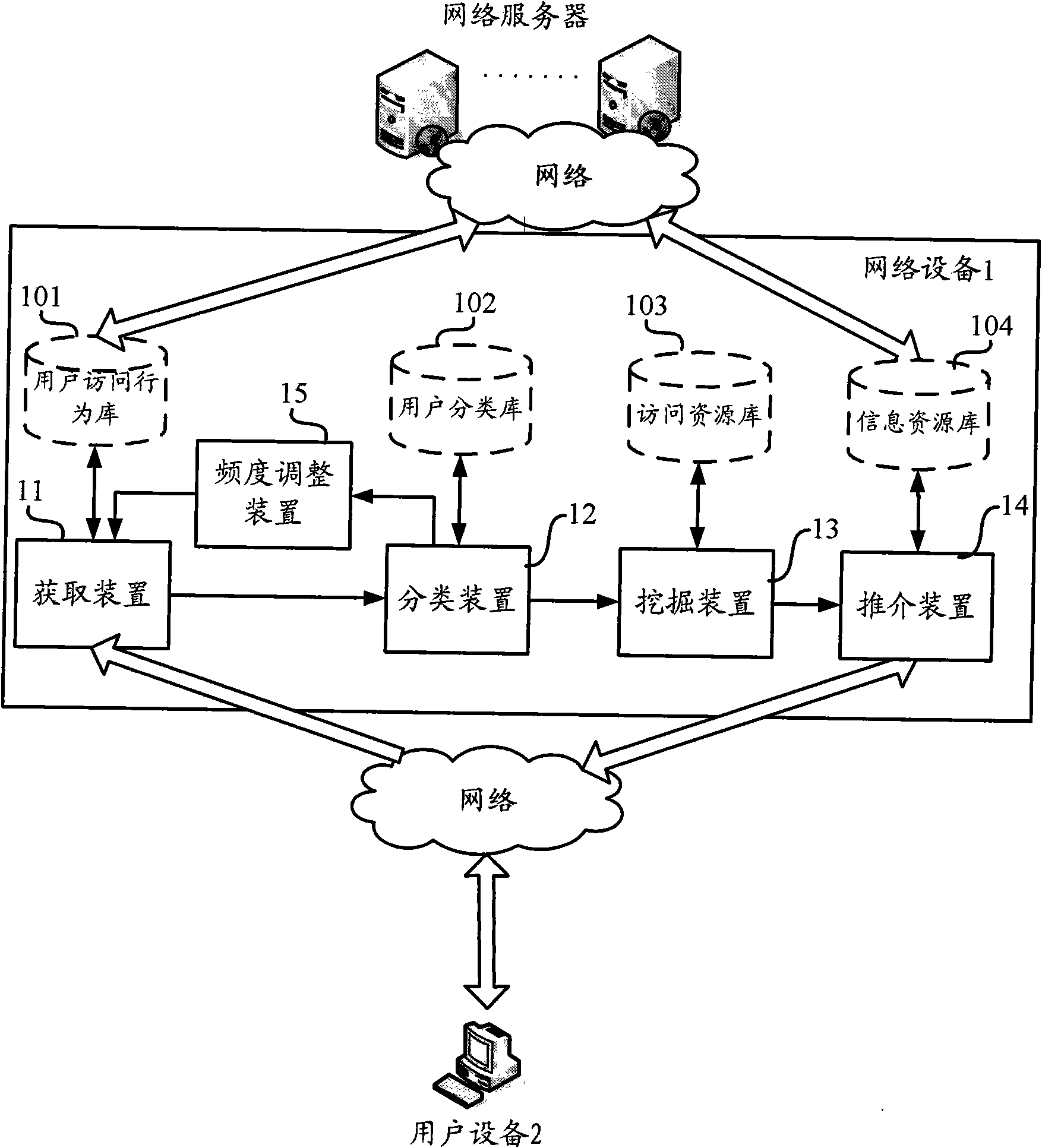
[0033] figure 1 A topological diagram of a system for content recommendation based on user characteristics according to one aspect of the present invention is shown, which includes a network device 1 and multiple user devices 2 . Among them, the network device 1 can be connected to multiple user devices 2 via a network, and recommend content for users according to the user access behavior initiated by the user from the user devices 2 . Here, the network includes but not limited to Internet, wide area network, metropolitan area network, local area network, VPN network, wireless self-organizing network (AdHoc network) etc.; , interaction with friends, shopping and other activities; the content recommended by the network device 1 for the user includes but is not limited to information resources such as network information, network services, online shopping, onl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com