Detection system and method of Domain Flux data stream
A data stream and database technology, applied in the field of network security, can solve problems such as large lag and inability to meet real-time requirements, and achieve the effect of real-time detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] A system and method for detecting Domain Flux data streams provided by the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments.
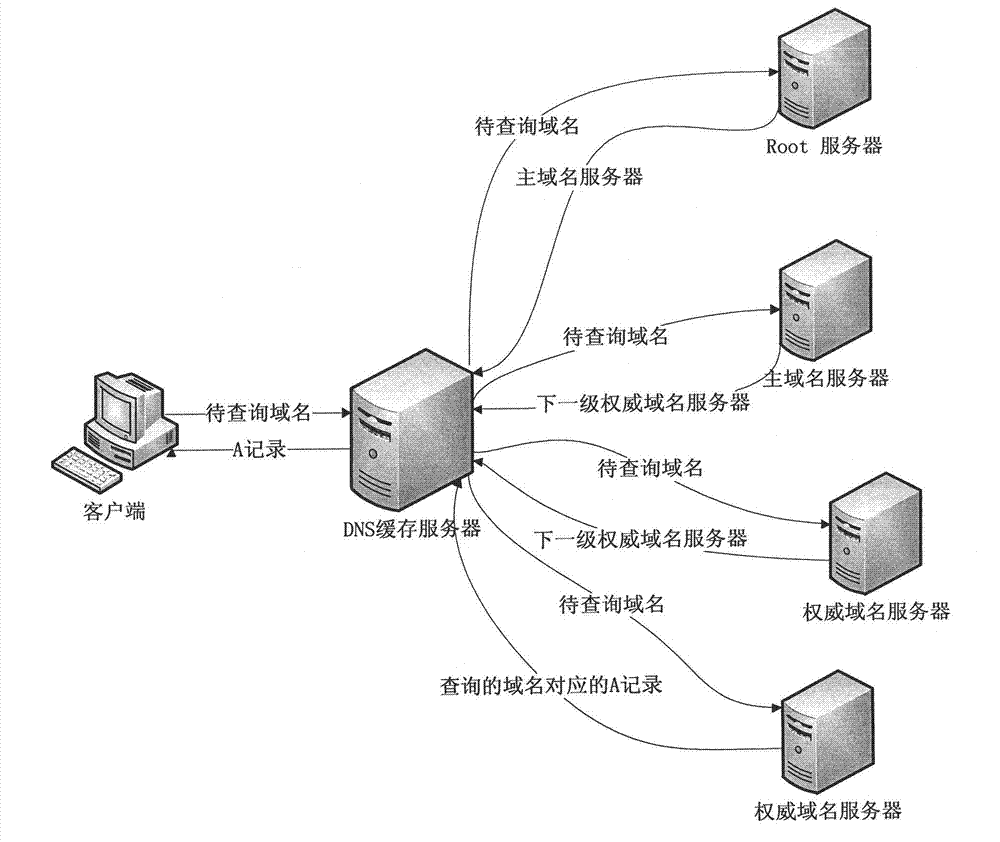
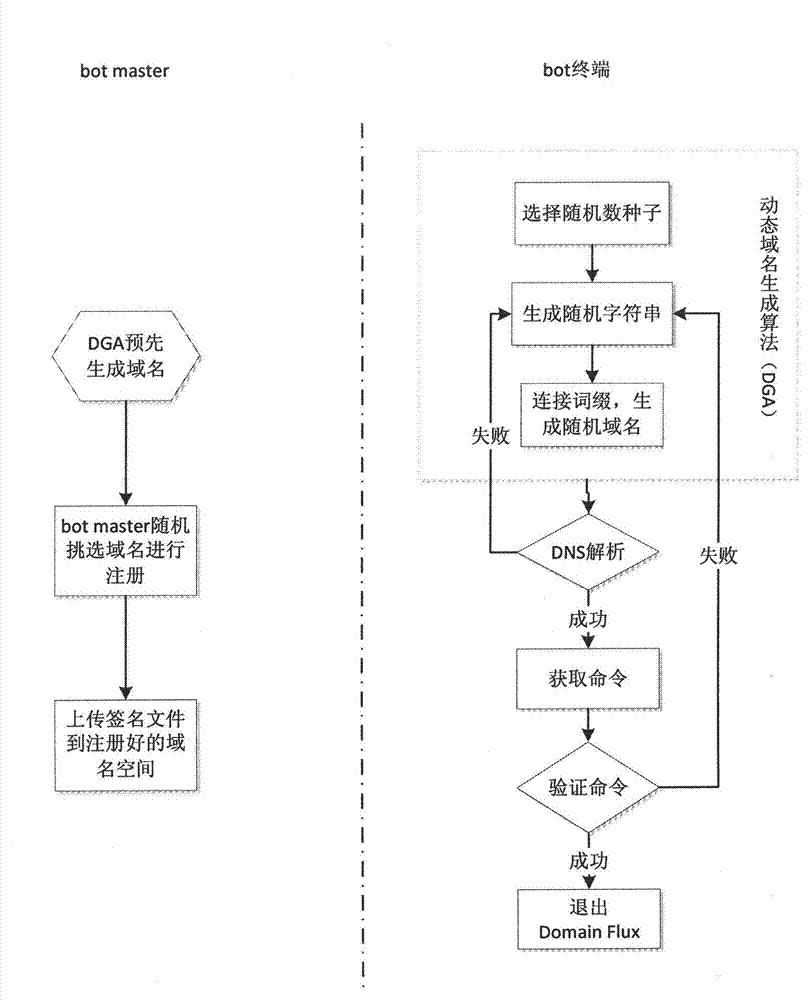
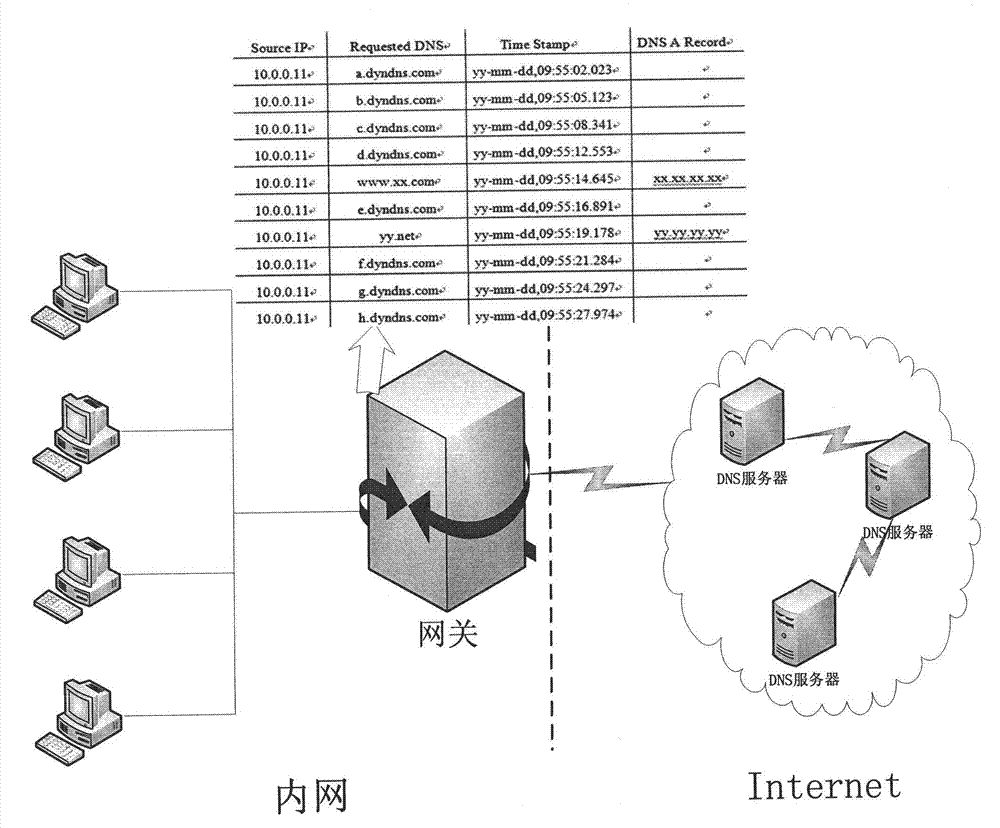
[0024] In general, the present invention proposes a method for detecting Domain Flux traffic at the network border. According to the three characteristics of the Domain Flux technology mentioned in the background technology, this method listens to and records all DNS query data streams in the LAN, and calculates the number of occurrences of the largest common substring in the same time window and the probability of DNS resolution failure , based on which it is calculated whether the data flow in the current window belongs to the Domain Flux data flow. The method can detect the existence of Domain Flux traffic in real time, and can determine the source of the data flow, thereby inferring that the host in the LAN is infected with the bot program.
[0025] In one embodiment of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com