Method and device for authenticating zero knowledge proof
An authentication method and identity authentication technology, applied in the field of authentication devices, can solve the problems of complex speed, unable to fully support the authentication system or encryption system, etc., and achieve the effect of satisfying application requirements, improving security, and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
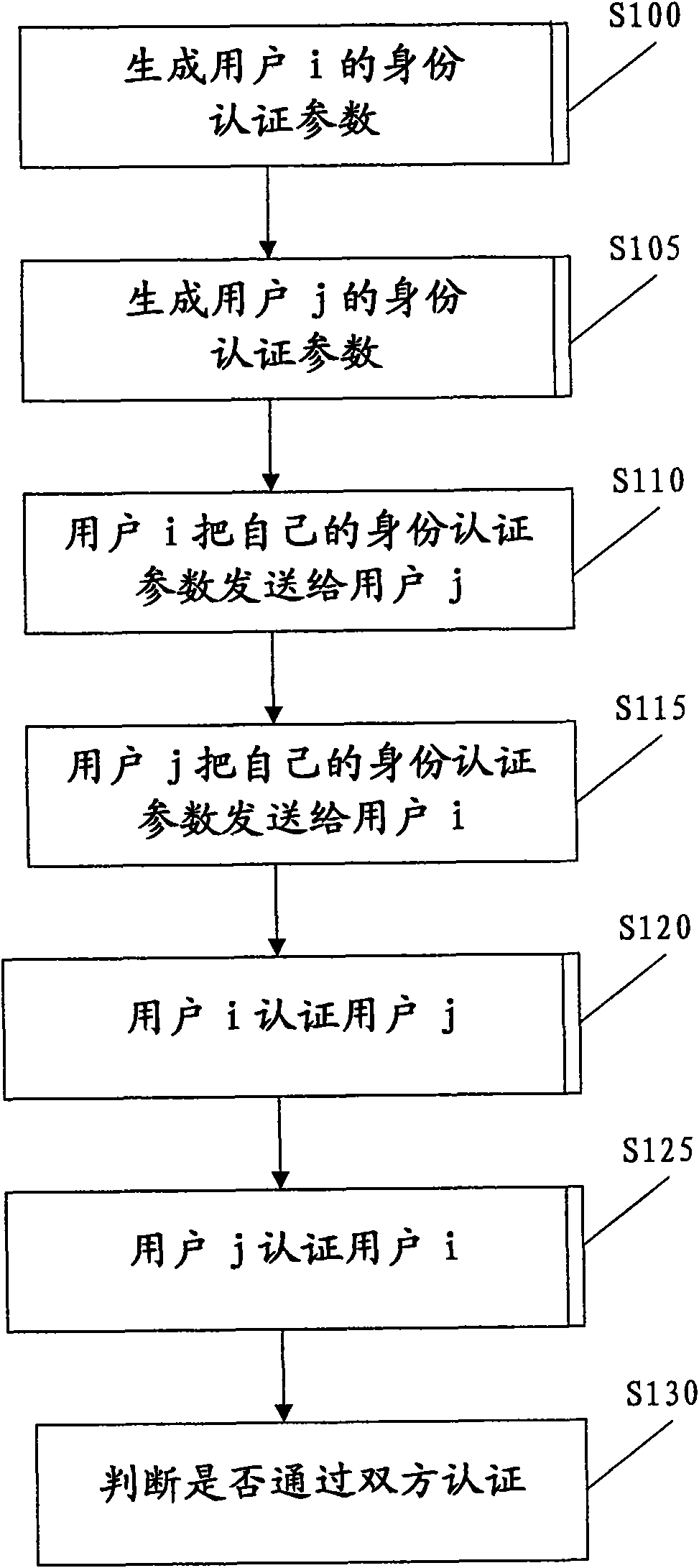
[0039]The first embodiment of the present invention describes an example where only one authority manages users.
[0040] The authorized authority adopts the national public key cryptosystem SM2 algorithm (compatible with the public key cryptosystem RSA algorithm).
[0041] The public key certificate of the authority is, for example:
[0042] C = (T, id, e, n, g, G)
[0043] The notes for each parameter of the certificate are:
[0044] T: time-varying parameters (registration time, valid time)
[0045] id: Authorization center authority parameters (URL, phone number, identity, authorization authority identification)
[0046] A: The authorized agency uses the encryption algorithm information of the symmetric cryptosystem
[0047] K: The authorized authority uses the encryption key of the symmetric cryptosystem
[0048] G: Authority to manage information
[0049] S: Authority private key
[0050] [e, n, g]: public key system key of the authority
[0051] [e, n, g, S]: Au...
no. 2 example
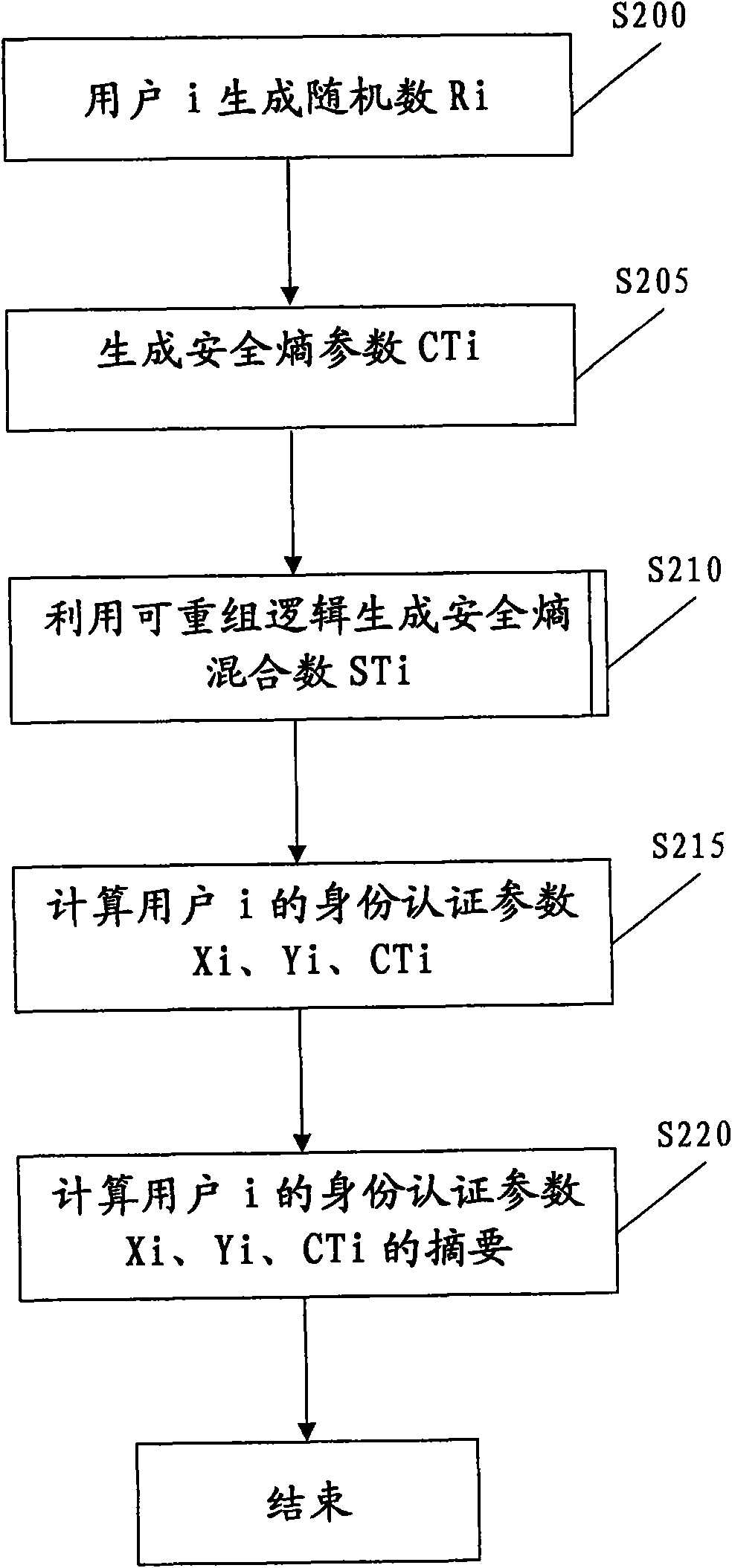
[0163] The second embodiment of the present invention also adopts figure 1 , figure 2 , Figure 6 The flowchart shown. The second embodiment differs from the first embodiment in that figure 2 step S205 and step S210.
[0164] In step S205, the security entropy information parameter CTi generated by user i includes not only random number Rsi, but also user security entropy CSTi and system security entropy CSKi. Specifically, CTi is given by the following expression:
[0165] CTi=CSTi, CSKi, Rsi Expression (10)
[0166] In step S210, the above-mentioned security entropy information parameter CTi is used to generate a security entropy mixing parameter STi.
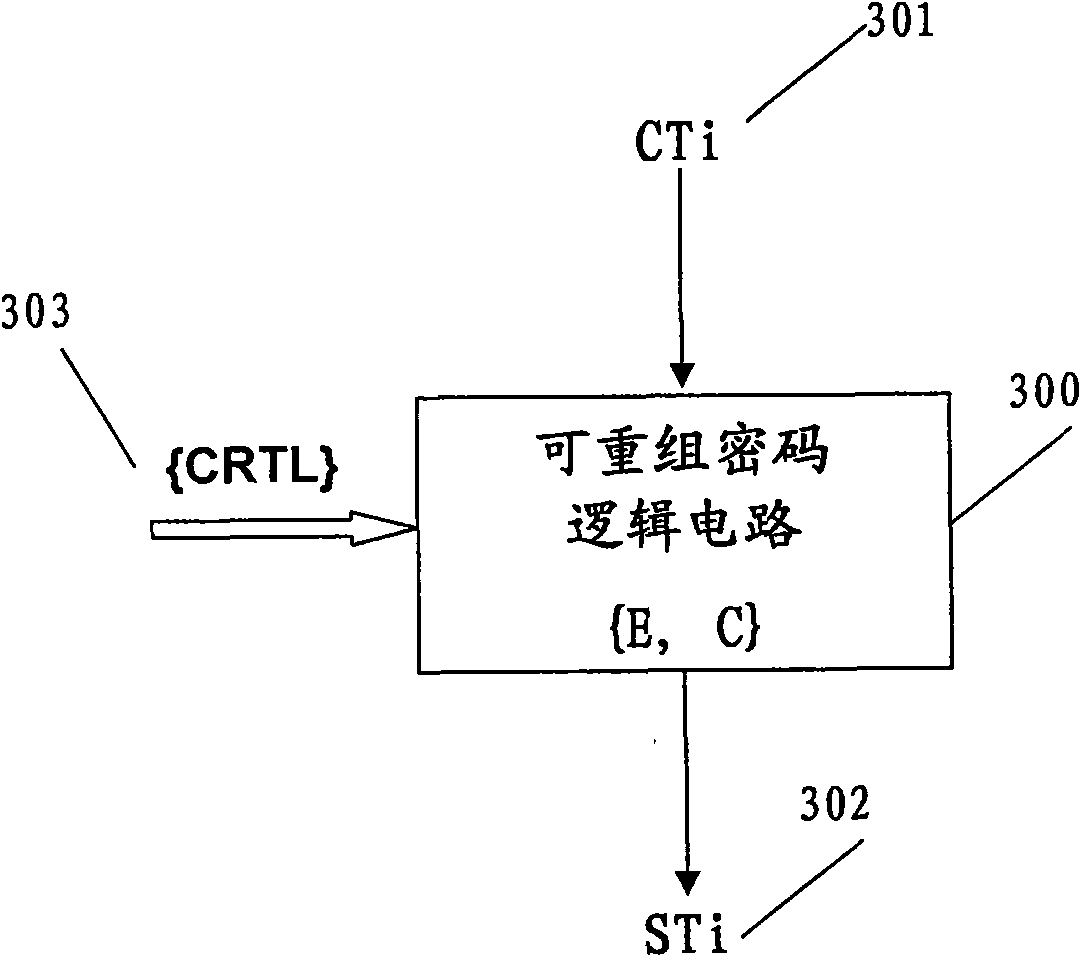
[0167] Figure 7 The reconfigurable cryptographic logic circuit 700 used in the implementation process of step S210 according to the second embodiment of the present invention is shown.
[0168] The reconfigurable cryptographic logic circuit 700 includes a user reconfigurable logic circuit Sa and a system reconfigur...
no. 3 example
[0187] The first embodiment and the second embodiment discuss an example of an authority. The third embodiment of the present invention discusses three examples of authorities.
[0188] In the third embodiment, the joint management of three authorized agencies is supported. At this time, both users i and j need to obtain certificates from the three authorized agencies before they can communicate.
[0189] FIG. 9 shows a schematic diagram of three authorization agencies: the authorization center, the management center, and the network management center jointly managing users. The security of the three-certificate authorization system is guaranteed by the security management of the authorization certificates of the authorization center, management center and network management center. The three authorization agencies manage authorization information separately, and can authorize each other separately and independently. When updating the authorization, the authorization informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com