Method for updating seeds of dynamic password token
A dynamic password and seed technology, applied in the field of information security, can solve the problems of token security loopholes, inability to update seeds, and no ability to change hardware interfaces, etc., to achieve the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
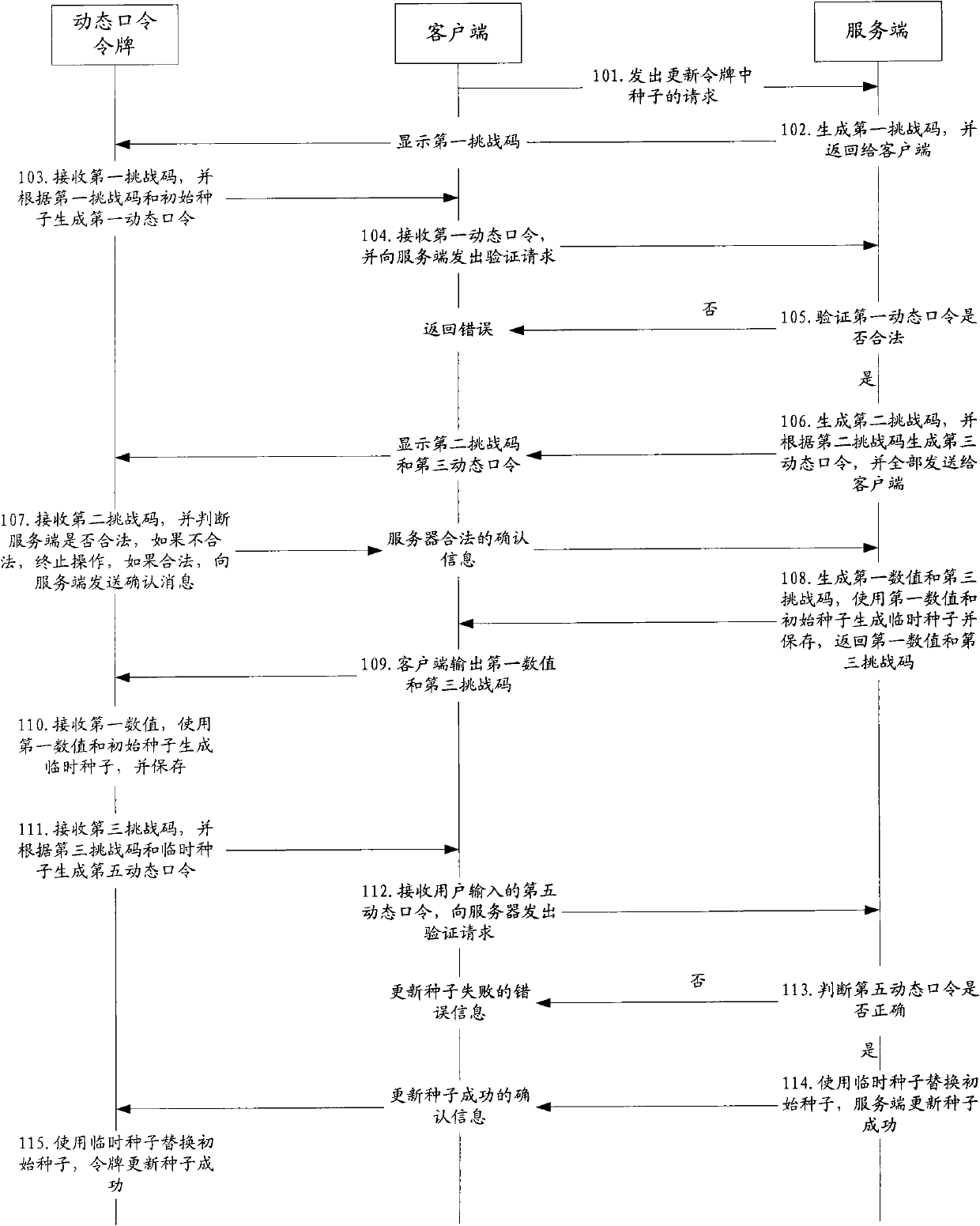
[0055] This embodiment provides a method for updating the seed of the dynamic password token. figure 1 ,Specific steps are as follows:
[0056] Step 101, the user sends a request to update the seed in the dynamic password token to the server through the client;
[0057] In this embodiment, the dynamic password token used by the user is a challenge-response dynamic password token, and input and output devices are placed on the token, preferably, the input device adopts a keyboard, and the output device adopts a display output or an audio broadcast output in the form of;
[0058] The user sends a request to update the seed in the dynamic password token through the client. Specifically, the user accesses the server through the browser installed in the client, and the server returns the function of updating the seed of the dynamic password token through the browser. page, the user enters the number of the OTP token that needs to update the seed, and chooses to update the seed, a...
Embodiment 2
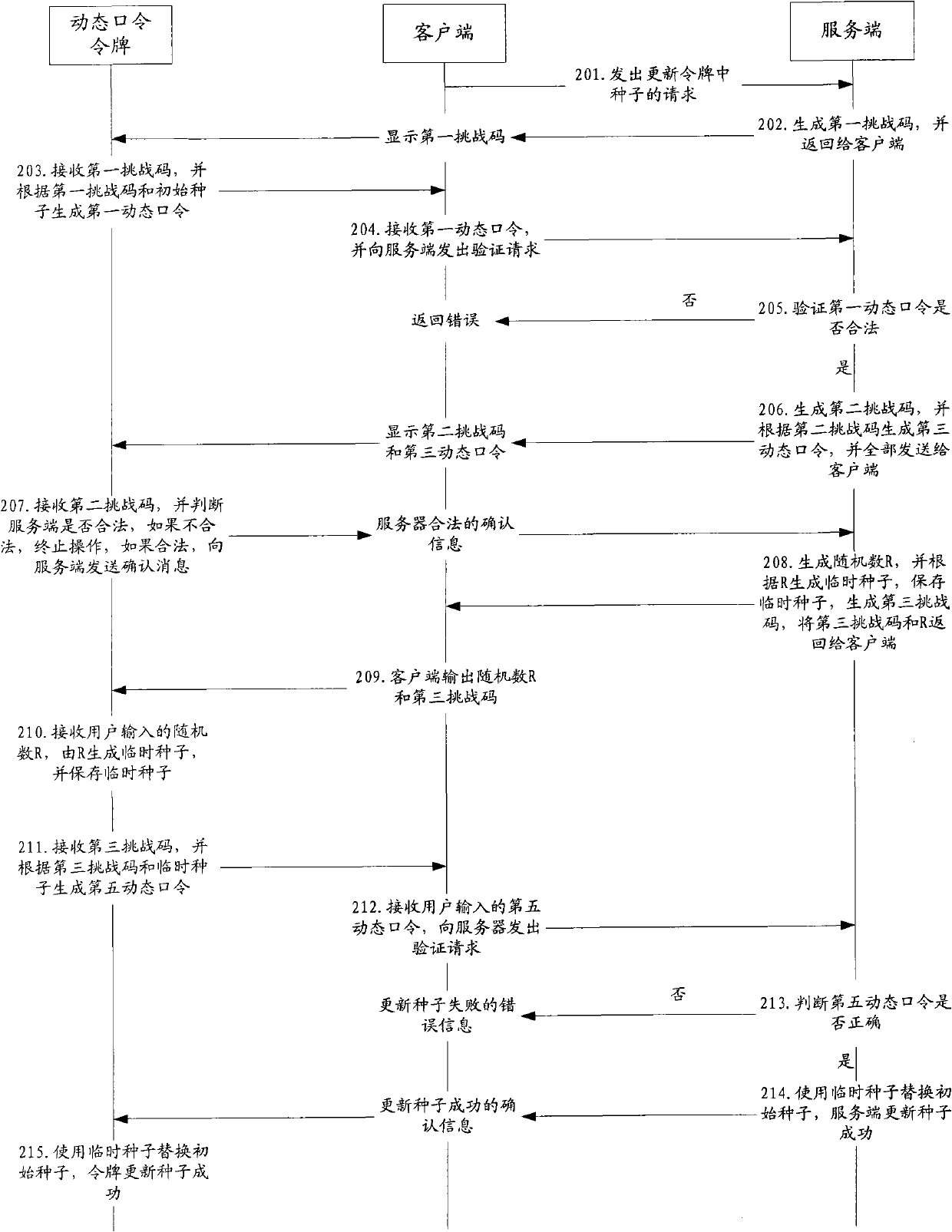
[0087] This embodiment provides a method for updating the seed of the dynamic password token. figure 2 ,Specific steps are as follows:
[0088] Step 201, the user sends a request to the server to update the seed in the dynamic password token through the client;
[0089] In this embodiment, the dynamic password token used by the user is a challenge-response dynamic password token, and input and output devices are placed on the token, preferably, the input device adopts a keyboard, and the output device adopts a display output or an audio broadcast output in the form of;
[0090] The user sends a request to update the seed in the dynamic password token through the client. Specifically, the user accesses the server through the browser installed in the client, and the server returns to the dynamic password token through the browser to update the seed. On the function page, the user enters the number of the OTP token that needs to update the seed, and selects to update the seed,...
Embodiment 3
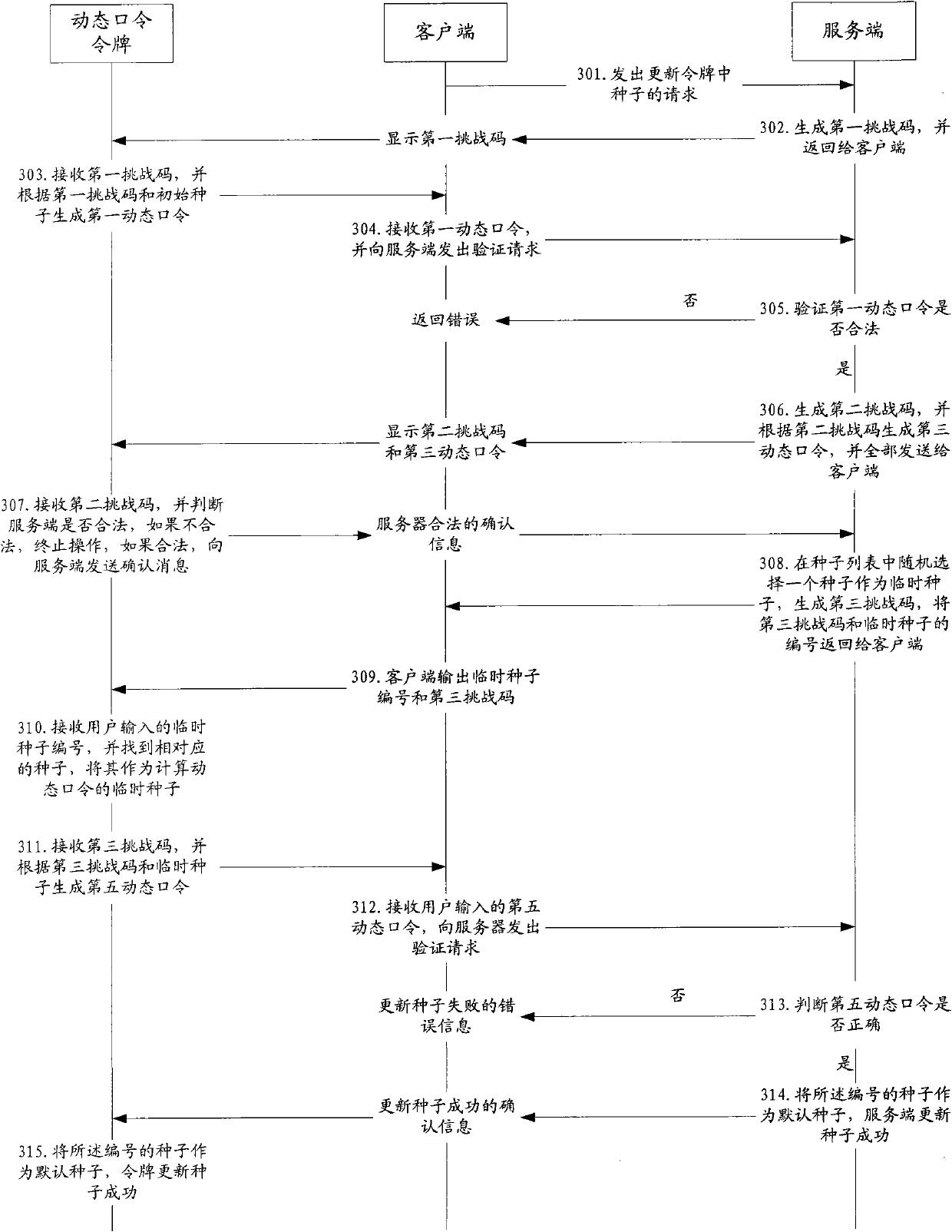
[0119] This embodiment provides a method for updating the seed of a dynamic password token. The dynamic password token provided by this embodiment stores a plurality of seeds in the dynamic password token, and stores information corresponding to a plurality of seeds. The list, referred to as the seed list in this embodiment, is written when the dynamic password token is produced or initialized. When the dynamic password token leaves the factory, use one of the multiple seeds as the initial seed to perform dynamic password calculation. The seed is defined as the initial seed, and the same seed list is also saved on the server side for the dynamic password token with this number. After the user purchases the dynamic password token, the seed used for calculating the dynamic password can be updated. image 3 , specifically as follows:
[0120] Step 301, the user sends a request to the server to update the seed in the dynamic password token through the client;
[0121] In this emb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com