Operation system architecture based on separation of permissions and implementation method thereof
A technology of operating system and separation of three powers, which is applied in the directions of instruments, electrical digital data processing, platform integrity maintenance, etc., and can solve problems such as excessive authority
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Below in conjunction with accompanying drawing of description, specific embodiment of the present invention is described:
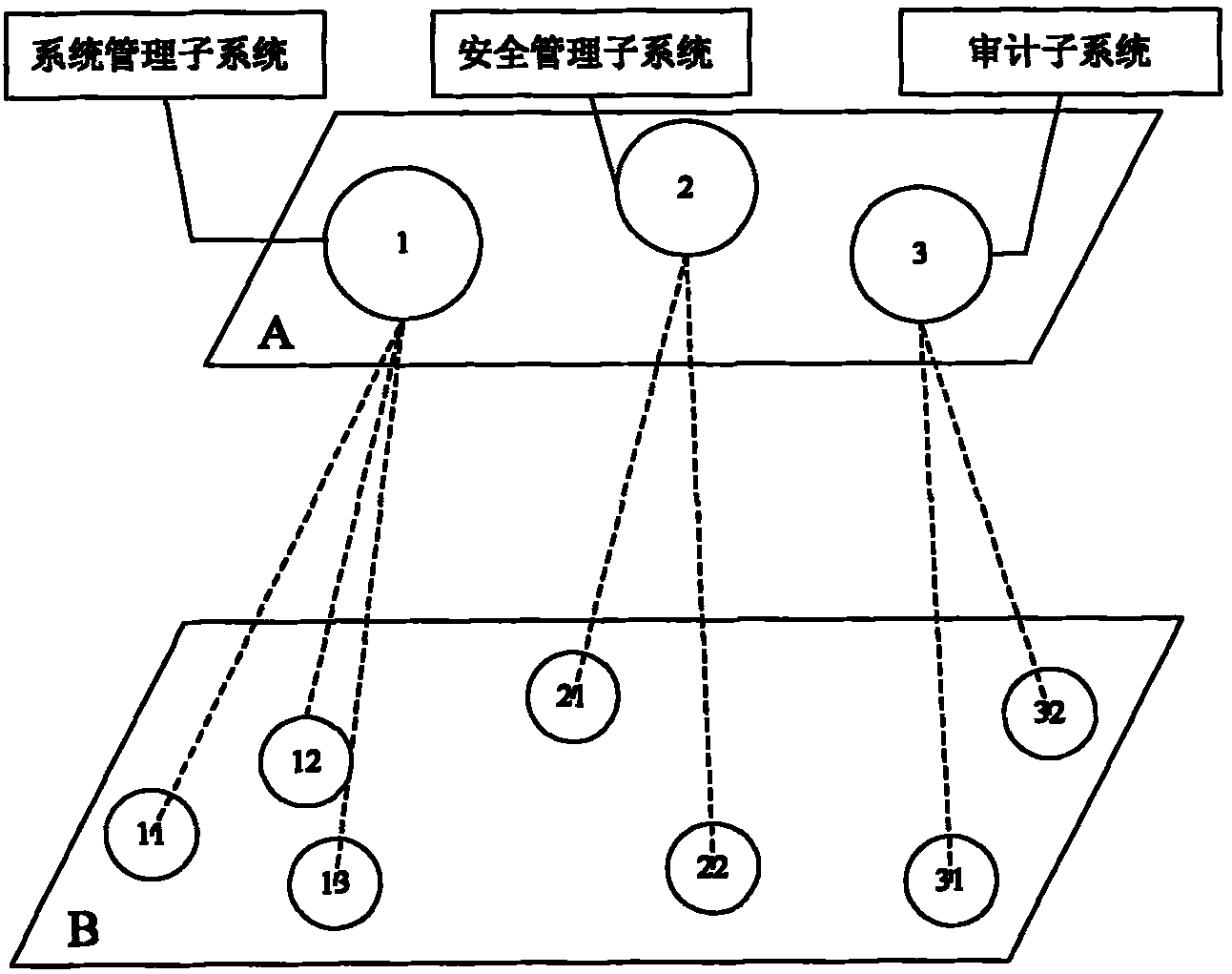
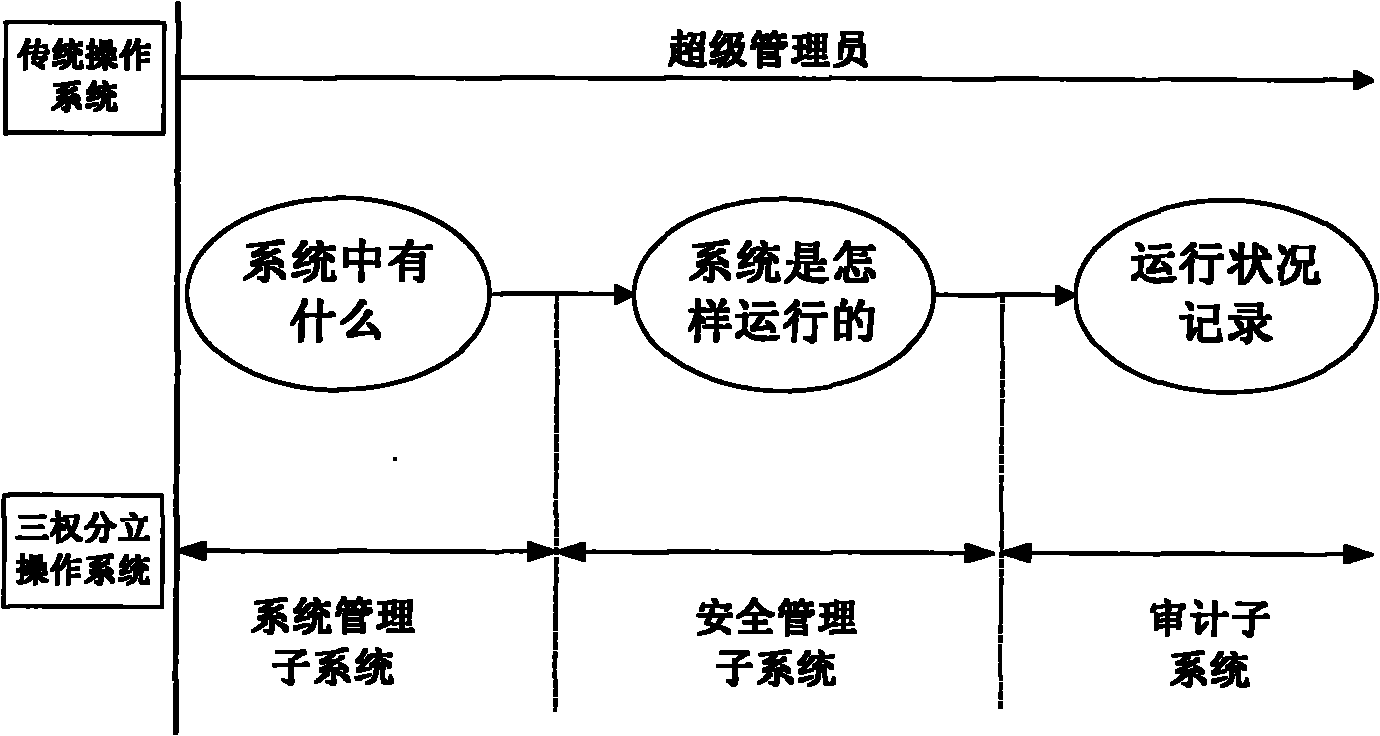
[0045] An operating system architecture based on the separation of three rights. The operating system rights are divided into system management rights, security management rights, and security audit rights; the system management rights correspond to the System Management Subsystem (SMS) in the operating system , the security management right corresponds to the security management subsystem (Security Management Subsystem, SEMS) in the operating system, and the security audit right corresponds to the audit subsystem (Audit Subsystem, AS) in the operating system; deleting the administrator will log in to the operating system The user who performs the actual operation is named as the operator;
[0046] (1) System Management Subsystem (SMS)
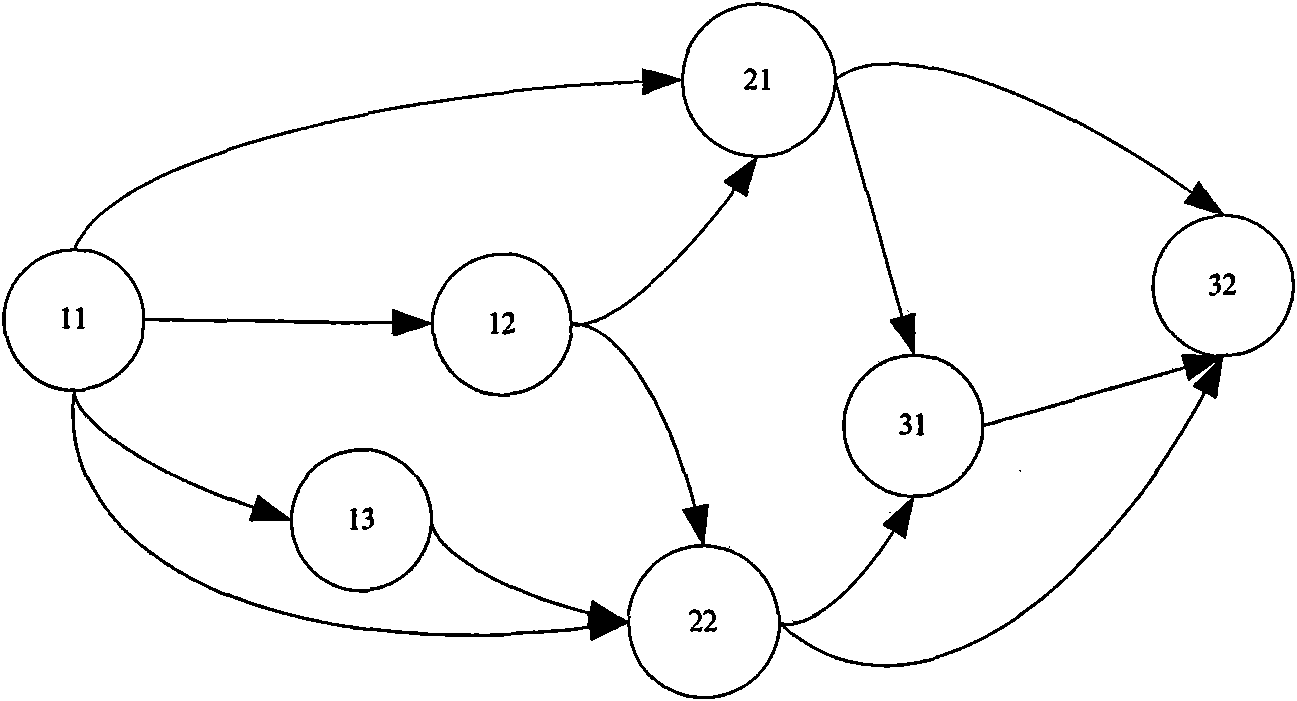
[0047] The system management subsystem is composed of trusted measurement, trusted service, trusted reference l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com