Method and system for hierarchically connecting trusted networks
A credible and network technology, applied in the field of information security, can solve problems such as malicious code, network security risks, sensitive information leakage, etc., and achieve the effect of reducing network and management load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
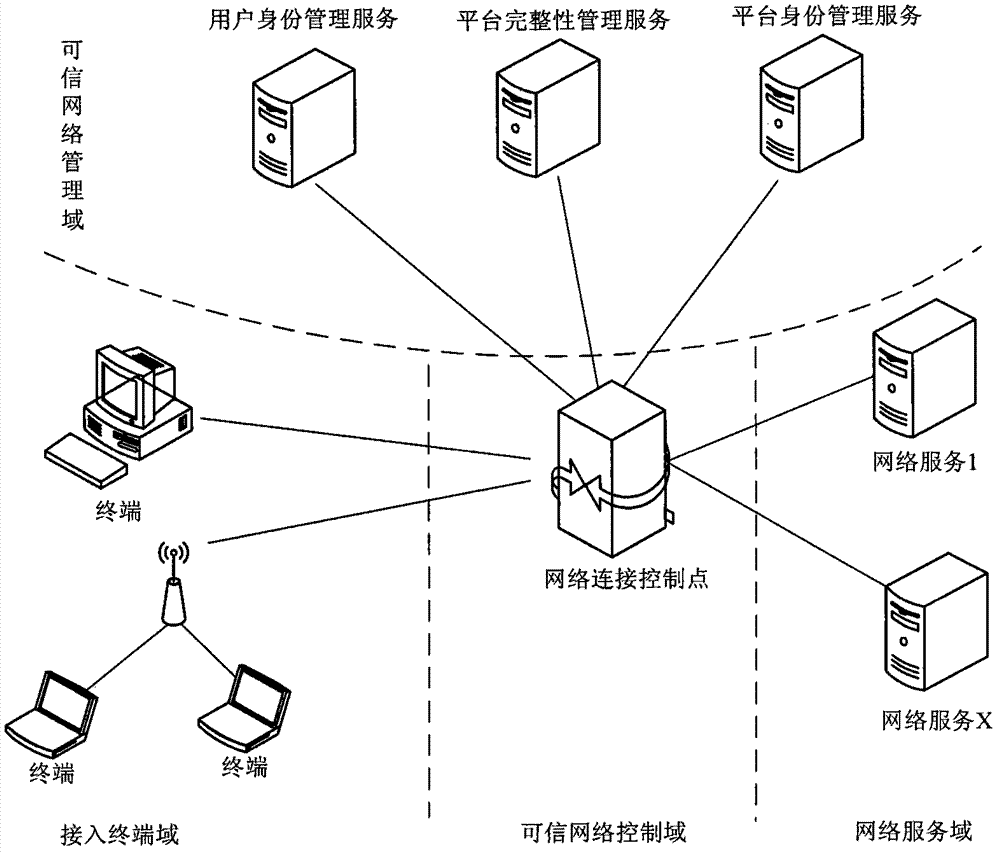
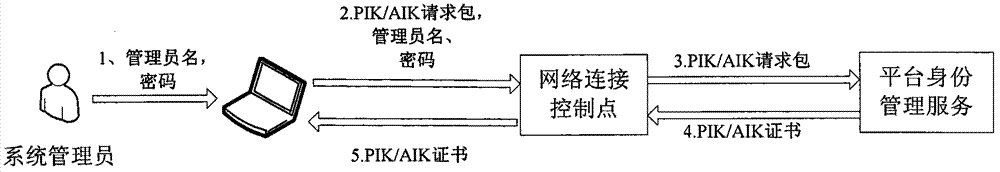
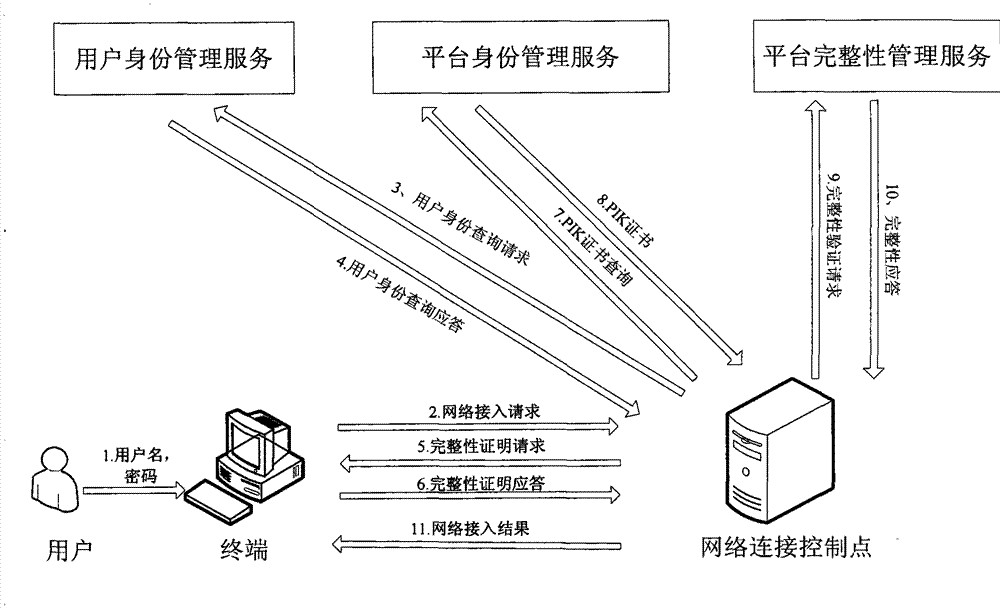
[0067] The method of the present invention is realized by the following system. Including the network access system on the terminal platform or device, that is, the access terminal domain, the network connection control point in the trusted network control domain, the platform identity management service, platform integrity management service and user identity management service in the trusted network management domain . The network service domain corresponds to the specific network services provided by various network service providers in reality, such as portal websites and email services. see figure 1 , the network access system accesses various network services in the network service domain through the network connection control point of the trusted network control domain, and the trusted network management domain provides platform management services and user identity management for the connection process through the network connection control point Service and Integrit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com