Computer system for data divulgence protection
A computer system and computer technology, applied in the field of information security, can solve problems such as the inability to balance the convenience and security of the data leakage protection system, and achieve the effects of reducing the possibility of illegal operations, simplifying the implementation method, and ensuring ease of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
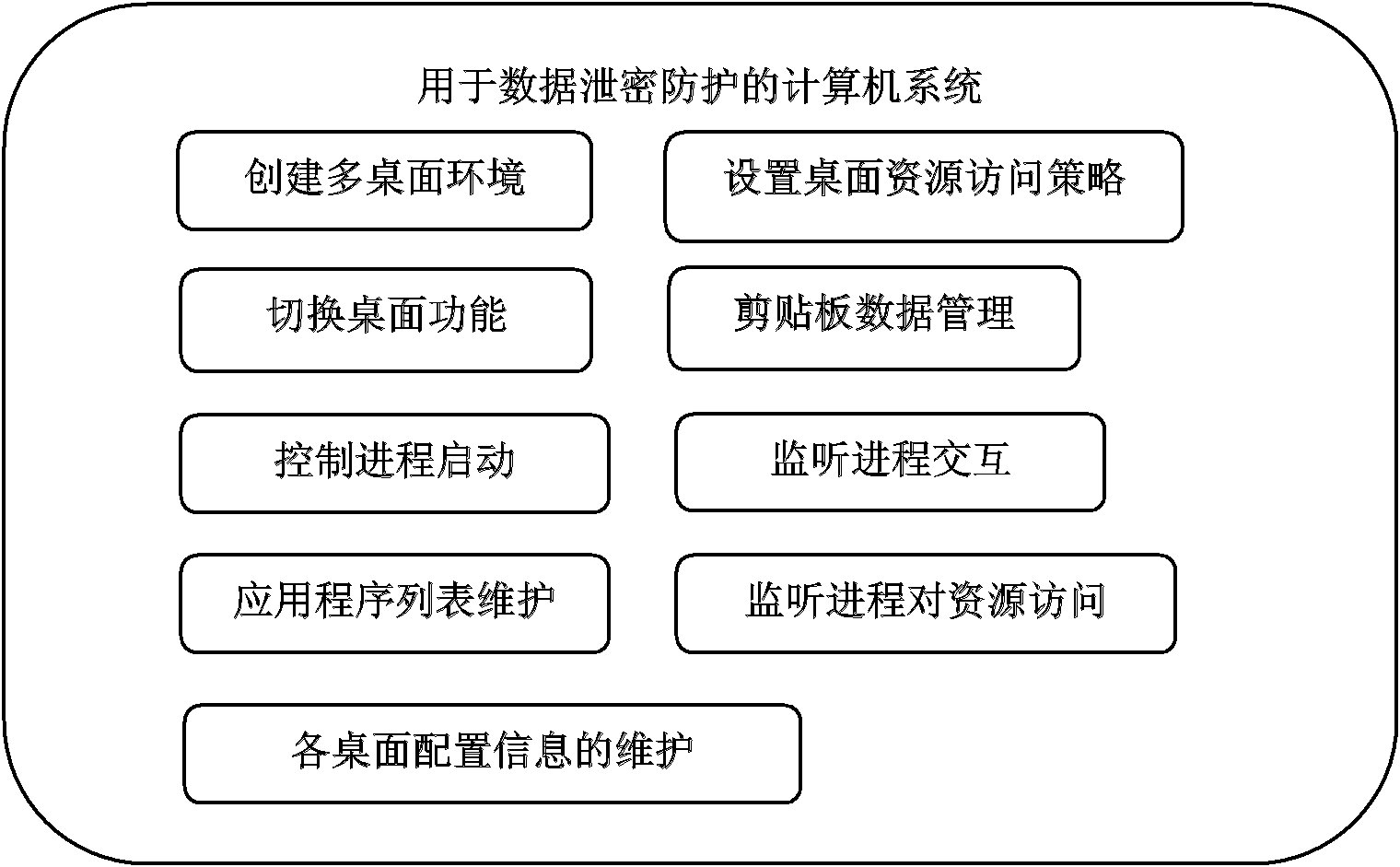
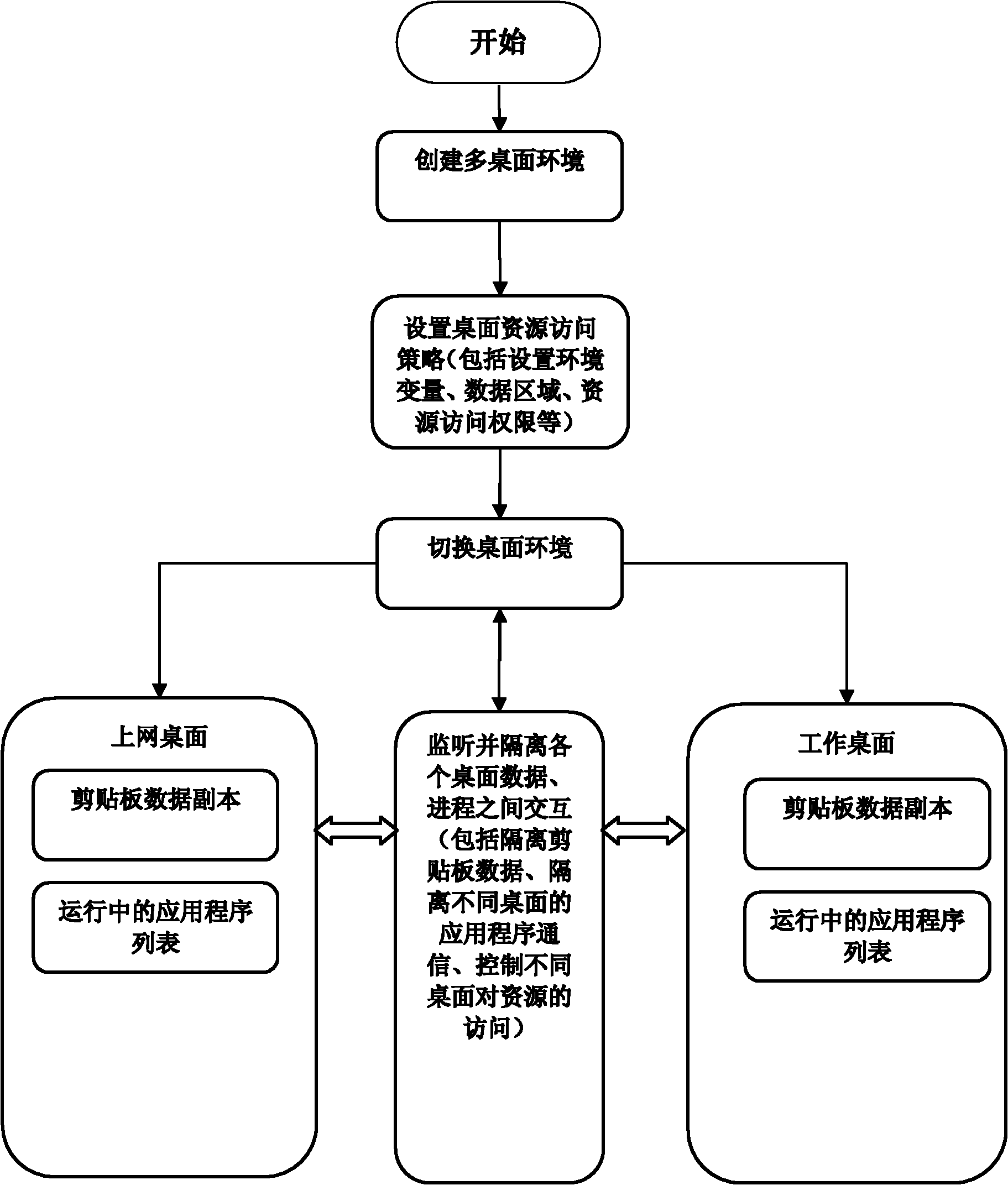
[0057] In this embodiment, the problem to be solved is to create different computer operating environments for users, so that users are in separate operating interfaces when operating sensitive data and non-sensitive data, so as to effectively protect data.
[0058] The application environment of this embodiment: all users who normally log in to the computer system and have successfully installed the application software of the multi-desktop management system.
[0059] according to figure 1 with figure 2 As shown, the specific scheme of the present embodiment is as follows:
[0060] 1. The desktop management system first creates multiple desktops for the logged-in user and names them. For example, create two desktops: "Work Desktop" and "Internet Desktop". In the Windows operating system, a new desktop can be created by calling the system interface function "CreateDesktop".
[0061] 2. The desktop management system sets the security level of "working desktop" and "Interne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com