Method for upgrading software on line
A technology of software and software files, applied to electrical components, public keys for secure communication, program control devices, etc., can solve problems such as software system crashes, software implanted functional components, data errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
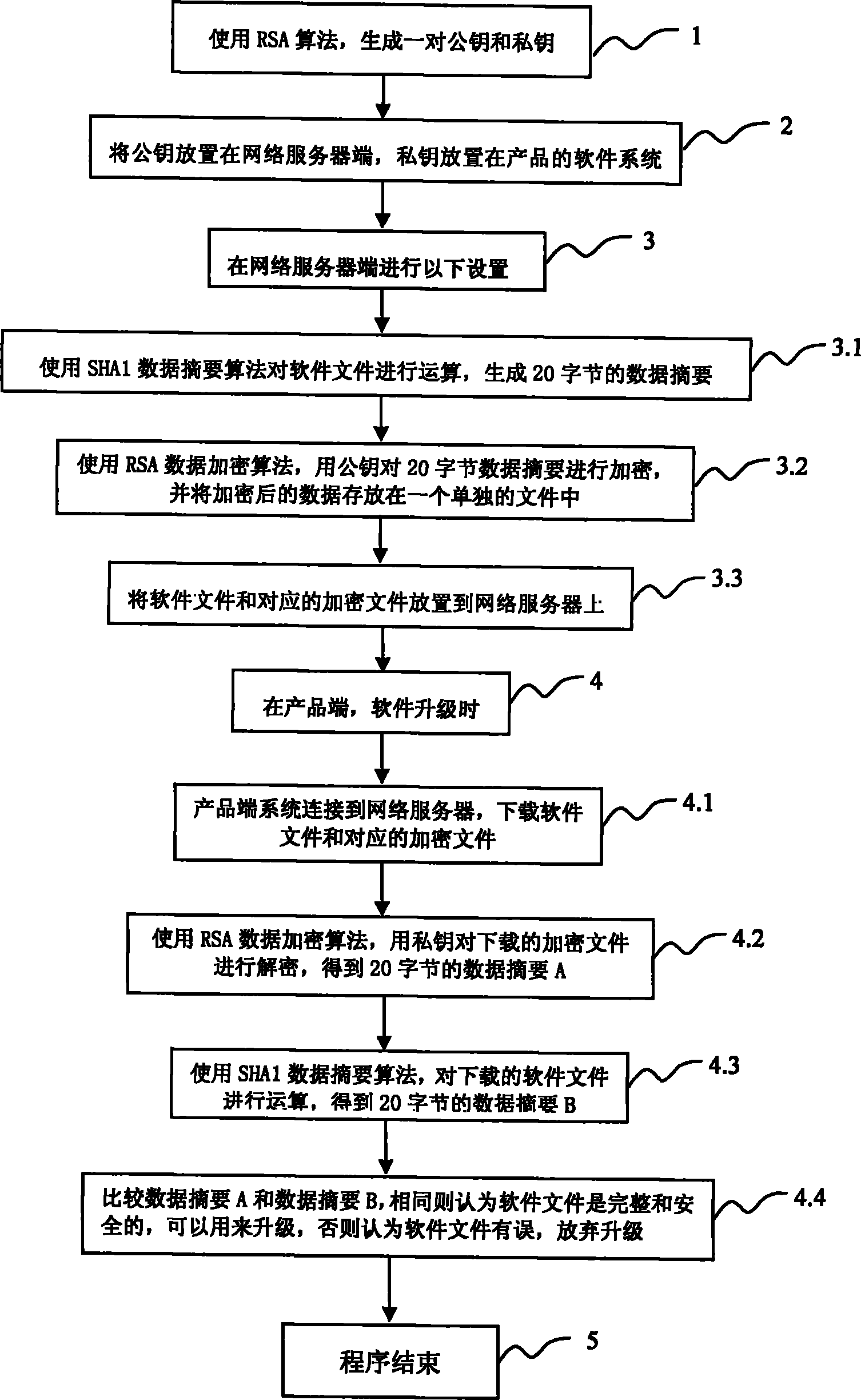
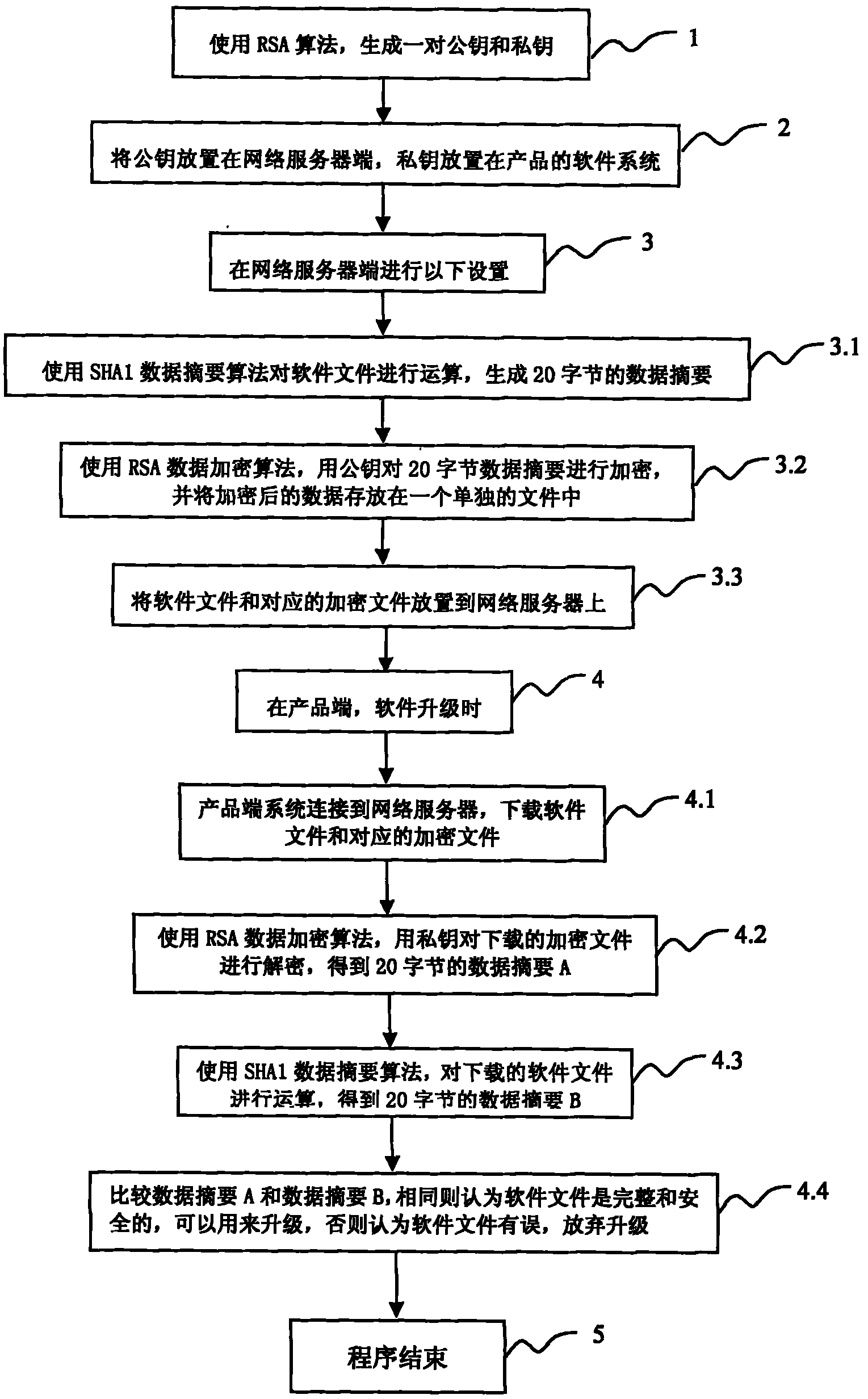
[0020] The gist of the present invention is to overcome the deficiencies of the prior art and provide a software online upgrade method, which establishes an associated verification and encryption mechanism at both ends of the network server and the product software system, so as to correctly identify the integrity of the software and prevent Wrong or tampered software is upgraded to the product, so that the product side can safely upgrade the software.
[0021] This software online upgrade method uses the asymmetry of the RSA encryption algorithm to encrypt the upgrade software to generate a pair of keys, that is, a public key and a private key. The public key is placed on the network server side, and the private key is placed in the software system of the product. , the public key is used for encryption, and the private key is used for decryption when the product is upgraded. The RSA algorithm is based on a very simple number theory fact. It multiplies two prime numbers and m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com