Protocol identification method, device and system
A technology of protocol identification and identification table, which is applied in the field of communication to achieve the effect of reducing misidentification and improving identification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
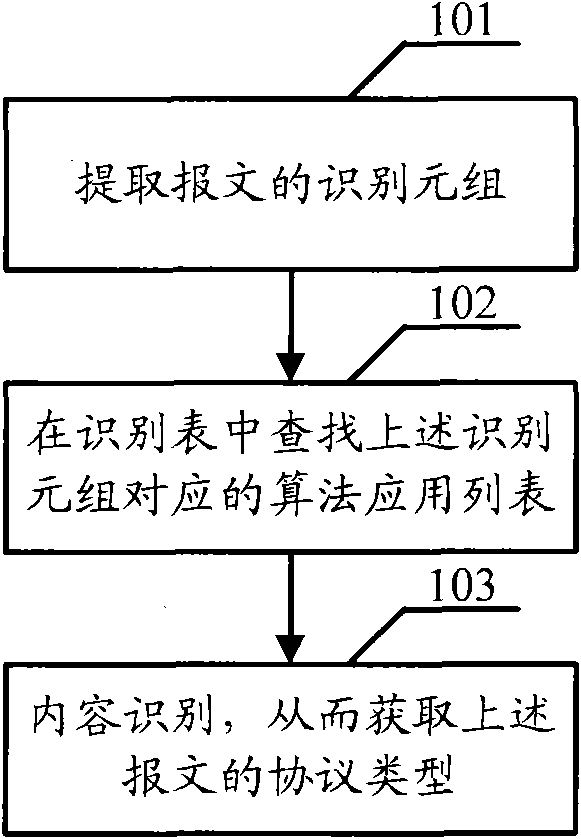
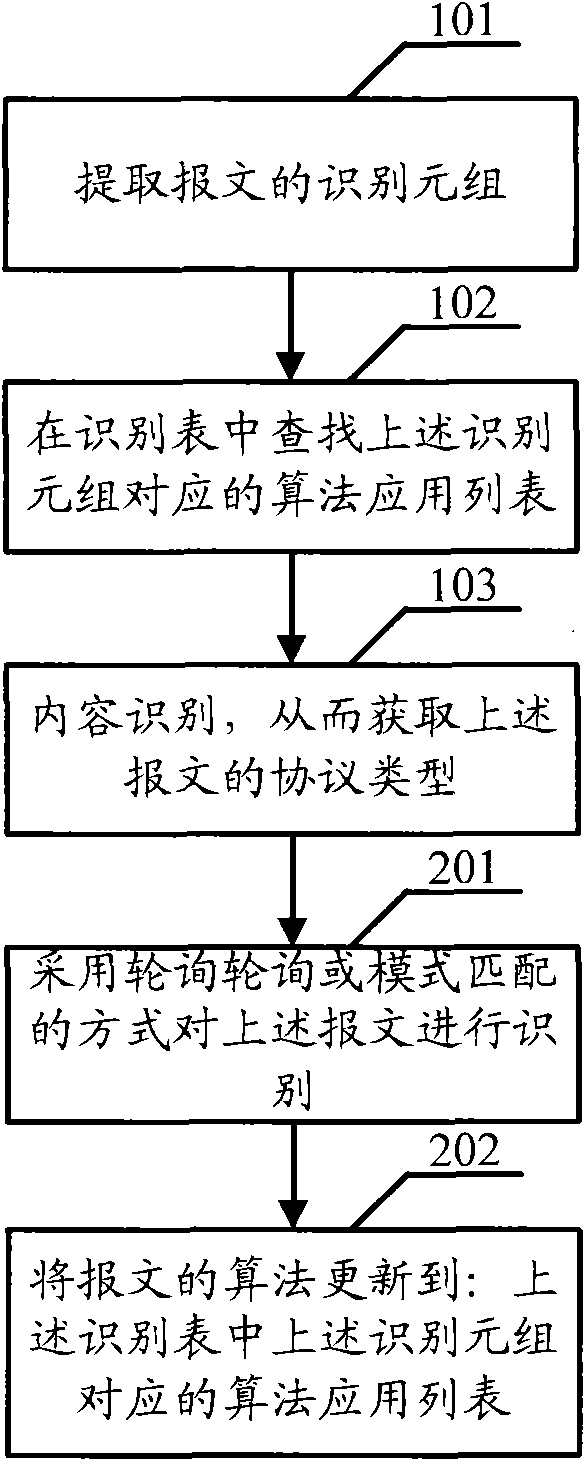
[0027] Embodiment one, such as figure 1 As shown, the embodiment of the present invention provides a method for protocol identification, including:
[0028] 101: Extract the identification tuple of the message; the identification tuple at least includes a network address;
[0029] The identification tuple mentioned above may be an N-tuple such as: one-tuple: network address; or, two-tuple: network address and port; or, three-tuple: network address, port (port), and transport layer protocol. Of course, the specific number of tuples can be set according to the needs of protocol identification, which is not limited in this embodiment. The above IP address can be the IP address of the source end of the message or the IP address of the destination end of the message. If the IP address of the source end is used, the port also uses the port of the source end. If the IP address of the destination end is used, the port also uses the port of the destination end.
[0030] 102: Search t...
Embodiment 2
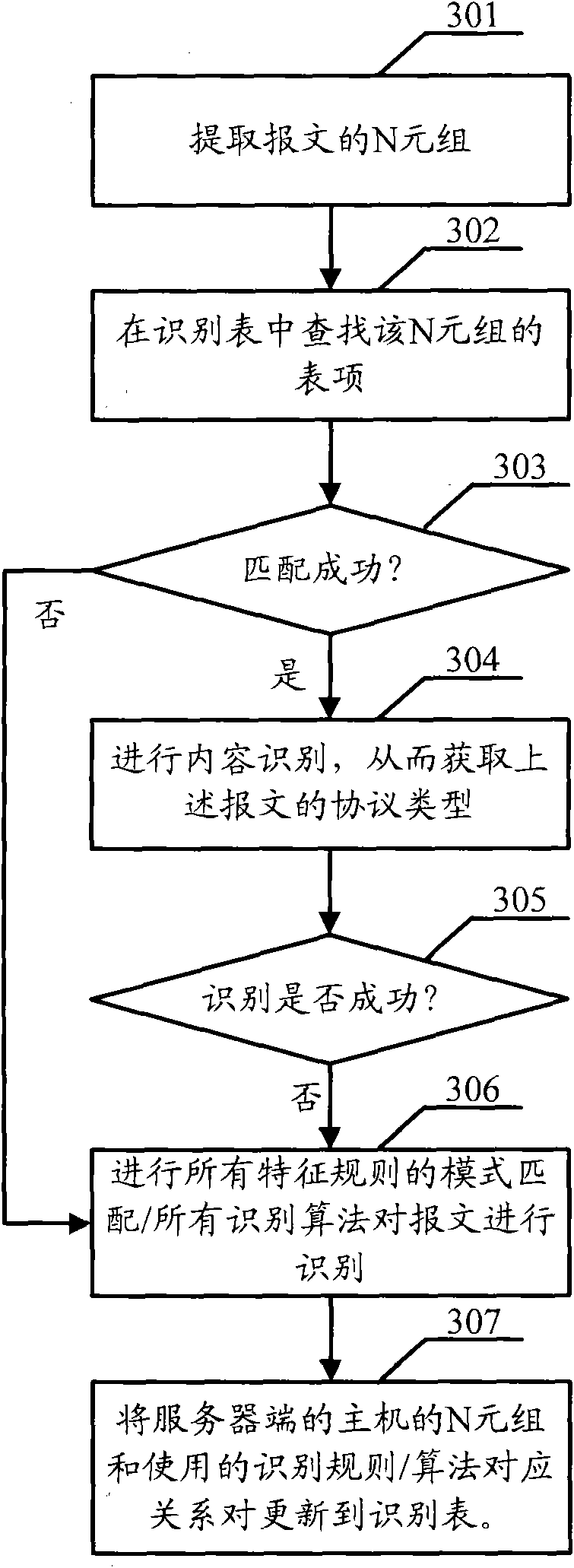
[0039] Embodiment 2, this embodiment will take the extraction of N-tuple information as an example, use the matching method to search the identification table, and determine whether the search and identification is successful through the judgment method as an example, and explain the method of protocol identification, as follows: image 3 shown, including:
[0040] 301: Extract an N-tuple of the message, where the N-tuple includes the network address, port, and transport layer protocol of the message.
[0041]Above-mentioned N-tuple can refer to unary (only network address), two-tuple (comprising network address, port) and triple (comprising network address, port, transport layer protocol (for example: Transmission Control Protocol (Transmission Control Protocol, TCP) / User Datagram Protocol (User Datagram Protocol, UDP) / Stream Control Transmission Protocol (Stream Control Transmission Protocol, SCTP)).
[0042] On the live network, many data flows belong to client / server appl...
Embodiment 3
[0053] Embodiment three, such as Figure 4 As shown, the embodiment of the present invention also provides a device for protocol identification, including:
[0054] An extraction unit 401, configured to extract the identification tuple of the message; the identification tuple at least includes a network address;
[0055] a storage unit 402, configured to store an identification table;
[0056] The algorithm search unit 403 searches the identification table for the algorithm application list corresponding to the identification tuple;
[0057] The protocol identification unit 404 is configured to use the algorithm in the algorithm application list to identify the content of the message, so as to obtain the protocol type of the message.
[0058] Specifically, the extracting unit 401 is specifically configured to extract the network address of the packet; or, the network address and port; or, the network address, port, and transport layer protocol.
[0059] Such as Figure 5 A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com