Short message service access control method and base station subsystem
A technology of service access and control method, applied in the field of communication, can solve the problem that basic voice services cannot be guaranteed, and achieve the effect of preventing wanton attacks by spam messages and ensuring normal operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
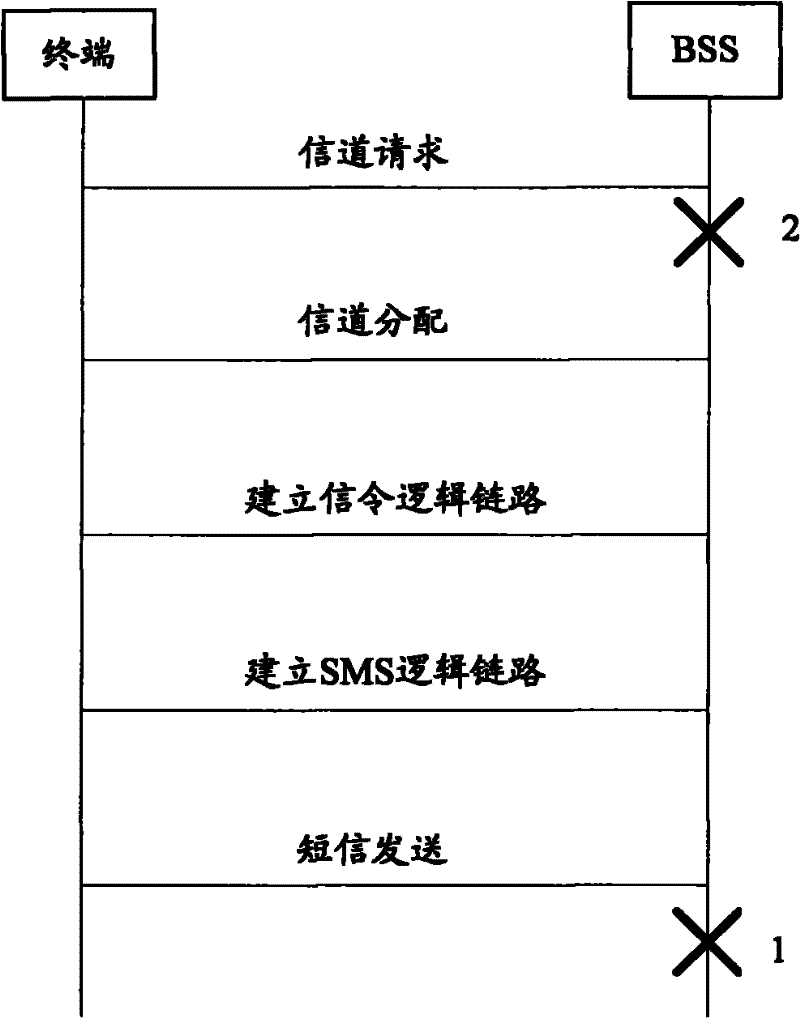
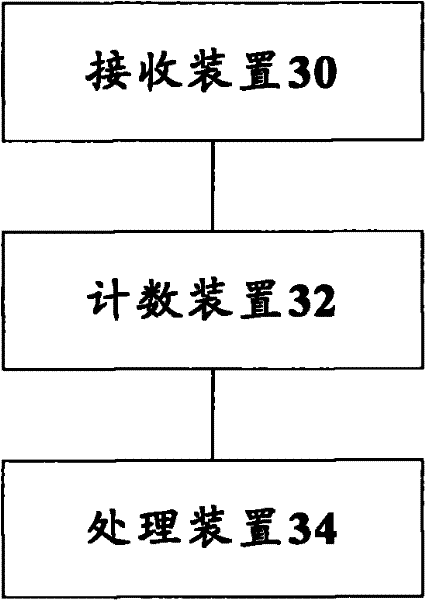
[0020] Hereinafter, the present invention will be described in detail with reference to the drawings and examples. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
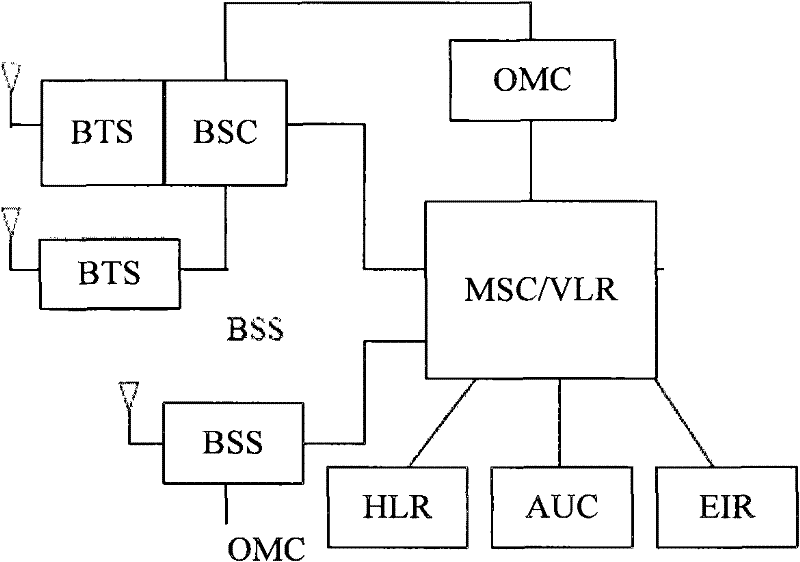
[0021] figure 2 It is the location diagram of BSS in the overall structure of the GSM system. Such as figure 2 As shown, the GSM system includes: BSS, mobile switching center (Mobile Switching Center, referred to as MSC) / visiting location register (Visiting Location Register, referred to as VLR), home location register (Home Location Register, referred to as HLR), authentication Authentication Center (AUC for short), Equipment Identity Register (EIR for short), Operation Maintenance Center (OMC for short), etc., wherein the BSS includes: Base Station Controller (Base Station Controller for short) BSC), base transceiver station (Base Tranceiver System, referred to as BTS). MSC / VLR is the core of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com