Domain name structural feature-based hang horse web page detection method
A detection method and construction technology, applied in the computer field, can solve the problems of consuming large server resources and network resources, low efficiency of hanging horse webpages, divergence of detection targets, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
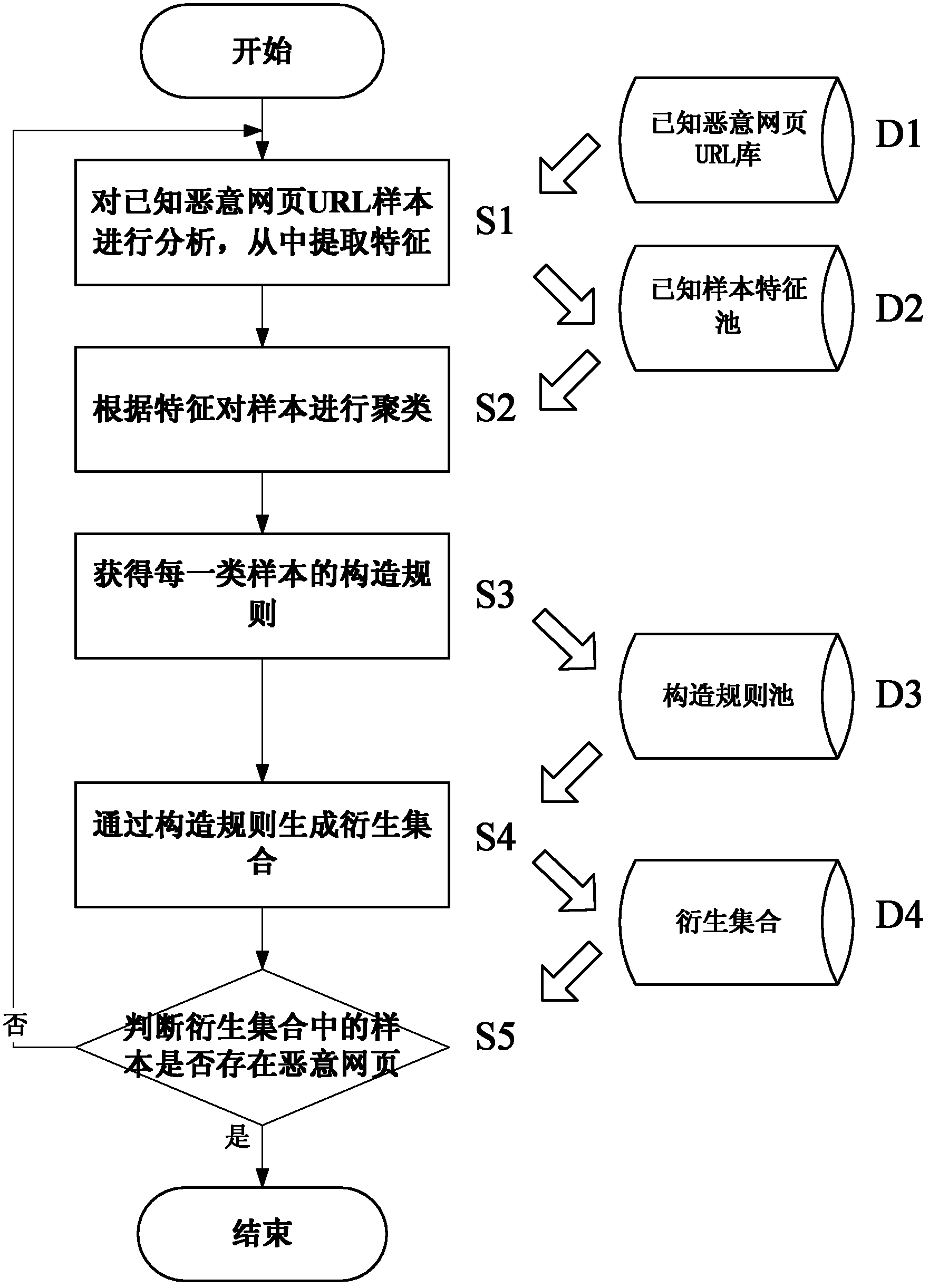
[0039] The present inventor, through statistical analysis of a large number of captured web page Trojan data, found that the hacker Trojan activity has the characteristics of tools and batches. Hackers will apply for a batch of domain names before hanging horses, and the composition of these domain names has certain rules and similarities.
[0040] The URL of the linked horse website is as follows:
[0041] http: / / baidu-opop1.cn / Bfyy.htm
[0042] http: / / baidu-opop1.cn / ce.htm
[0043] http: / / baidu-opop2.cn / ce.htm
[0044] http: / / baidu-opop2.cn / Bfyy.htm
[0045] http: / / baidu-opop3.cn / Bfyy.htm
[0046] http: / / baidu-opop3.cn / real10.htm
[0047] http: / / baidu-opop3.cn / ce.htm
[0048] http: / / baidu-opop4.cn / Bfyy.htm
[0049]http: / / baidu-opop4.cn / ie7.htm
[0050] http: / / baidu-opop6.cn / ce.htm
[0051] http: / / baidu-opop7.cn / Bfyy.htm
[0052] http: / / baidu-opop7.cn / ie7.htm
[0053] In these website addresses, the domain name portion:
[0054] baidu-opop.cn
[0055] baidu-opop1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com