Authentication system and method
An identity verification and identity certificate technology, applied in the field of identity verification systems that support cross-system verification, can solve the problems of not being able to verify the identity of system personnel, not supporting personnel identity verification, wasting social resources, etc., so as to reduce the number of issuances and reduce duplication of construction. , the effect of saving social resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
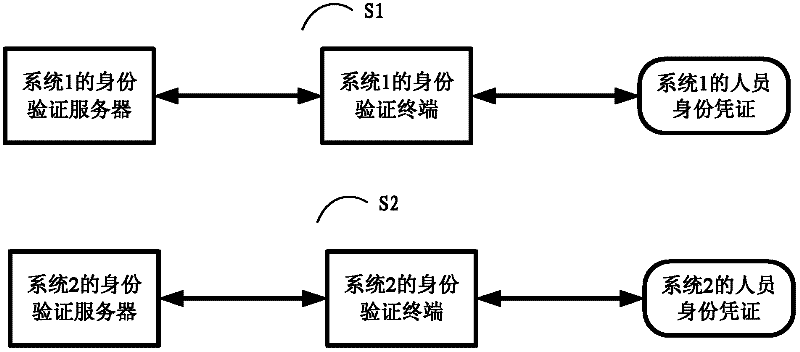
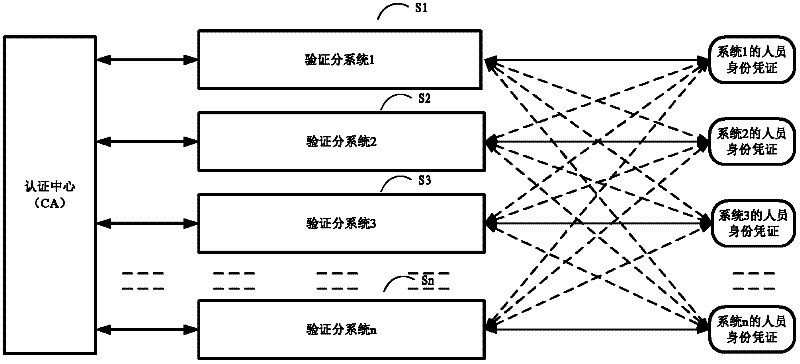
[0023] The inventor noticed that if a certification center recognized by them is set for multiple verification subsystems, and the certification center issues system digital certificates for each verification subsystem, since the system digital certificate is also recognized by other verification subsystems, Therefore, the personal digital certificates and identity certificates issued by each verification subsystem can also be verified in other verification subsystems.
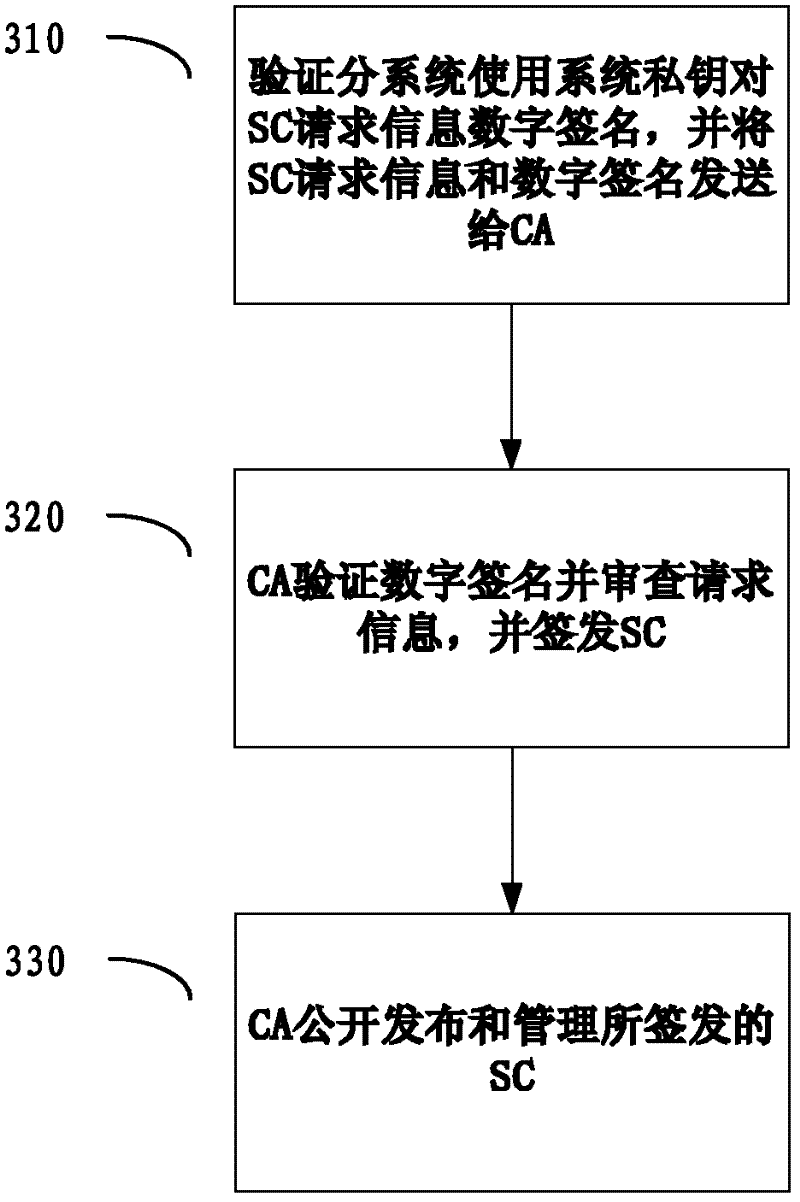
[0024] figure 2 is a schematic structural diagram illustrating an identity verification system according to an embodiment of the present invention. Such as figure 2 As shown, the identity verification system includes: the certification center CA and multiple verification subsystems S1, S2, ..., Sn, where the certification center CA uses the certification center private key RK Pri The system digital certificates SC1, SC2, ..., SCn of the verification subsystems are respectively issued for the plurality of v...
no. 2 example
[0033] Figure 4 A schematic structural diagram of an identity verification system according to another embodiment of the present invention is shown. from Figure 4It can be seen that the verification subsystem includes an identity verification server and an identity verification terminal respectively. In the drawings, for the sake of clarity, only the identity verification server 410 and the identity verification terminal 420 in the verification subsystem 1 are shown with reference numerals. When the identity verification server 410 or identity verification terminal 420 and its components are mentioned below, if there is no special description, it should not be understood as being limited to the relevant components in the verification subsystem 1, but can be extended to other verification subsystems corresponding parts in .
[0034] The identity verification terminal 420 is a terminal device, which can support the public key cryptographic algorithm, and can read the inform...
no. 3 example
[0057] In the second embodiment, the identity verification control subsystem sends the first system list SID_List1 to the identity verification terminal, and the identity verification terminal uses the verified second system list SID_List2 to verify the personal digital certificate PC. In the third embodiment, the identity verification control subsystem can also send the special personnel list PID_List to the identity verification terminal. Among them, the special entry personnel may not belong to any verification subsystem in the first system list SID_List1. Therefore, when the identity verification terminal verifies the personal digital certificate PC in the identity certificate, it also considers the special personnel list PID_List. A detailed description is given below.
[0058] In this embodiment, the identity verification control subsystem 4102 of the identity verification server 410 uses the public key RK of the certification center CA Pub Or the public key certificat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com