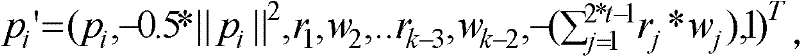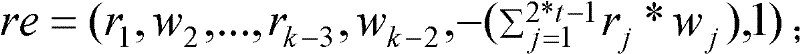Vector and matrix operation-based calculation-supported encryption method
An encryption method and a matrix operation technology, applied in the computer field, can solve the problems of using experience discount, the complex calculation amount of the fully homomorphic scheme, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0092] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific implementation examples.
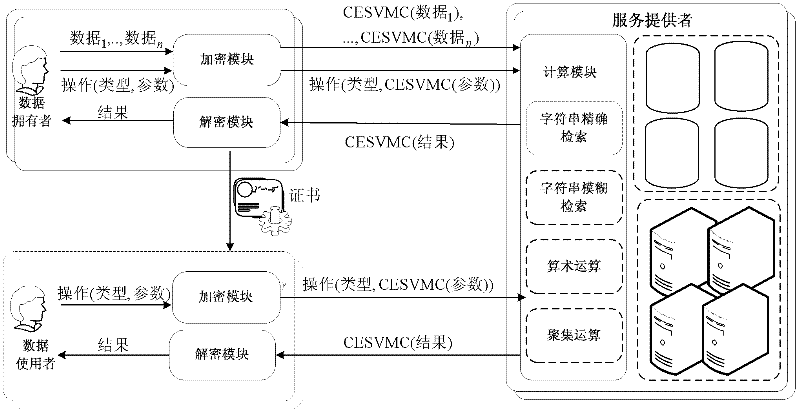
[0093] The framework of the encryption method CESVMC (computable encryption scheme based on vector and matrix calculations) based on vector and matrix calculations of the present invention is as follows: figure 1shown. The scheme first constructs a vector composed of calculation element groups and random element groups, and obtains encrypted vectors through operations with encrypted matrices, thereby converting the original data into a vector, which makes it indistinguishable and indistinguishable by introducing random numbers. It cannot be deciphered in polynomial time; secondly, in the process of string fuzzy matching, the difference between the distance between the outsourced string and the retrieval parameter is used to achieve sorting and fuzzy query, and the attacker cannot get the outsourced string and the The dist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com