Malicious call dialing prevention method for mobile intelligent terminal and system thereof
A mobile intelligent terminal, malicious phone technology, applied in the direction of telephone communication, electrical components, branch equipment, etc., can solve emergencies such as inability to prevent malicious phone calls well, occupy large system resources, and system operation efficiency is low. and other problems, to achieve the effect of timely and efficient system complexity, optimizing system structure, and not increasing system complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
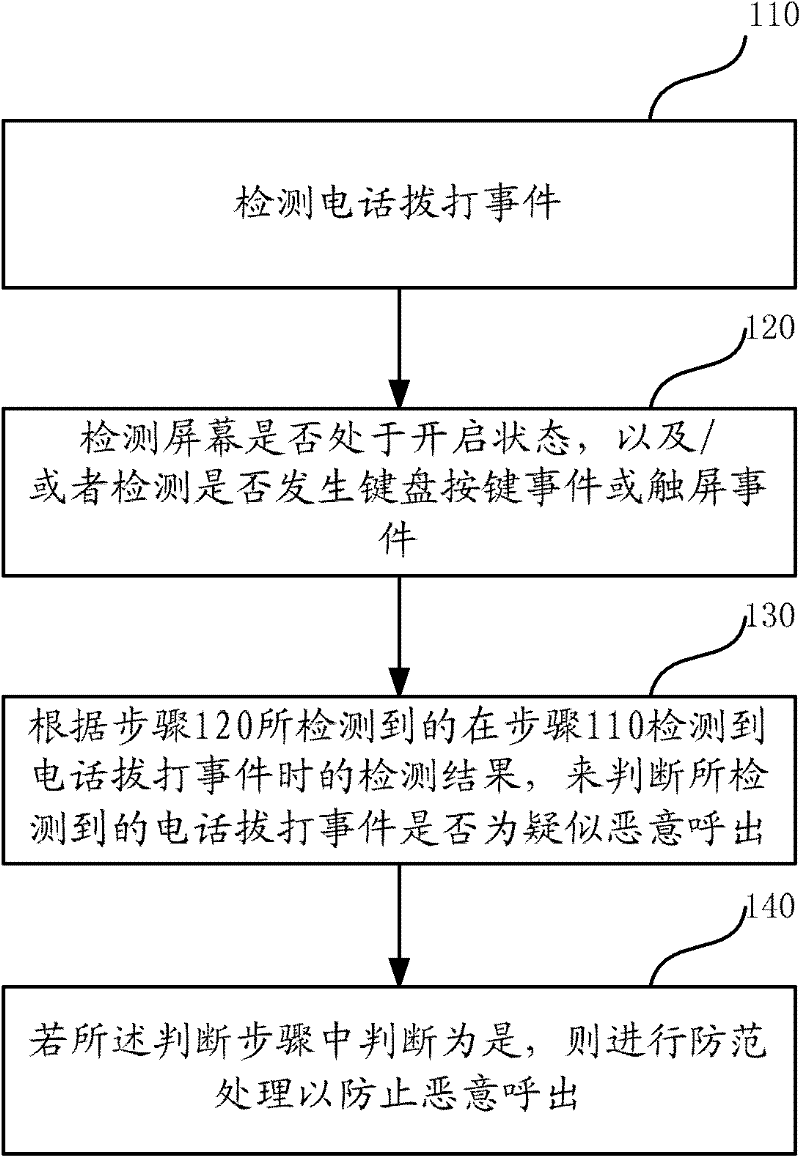
[0043] figure 1 A schematic flow diagram of the method for preventing malicious calls from mobile smart terminals according to the first embodiment of the present invention is given. The steps of this embodiment will be described in detail below with reference to the accompanying drawings:
[0044] Step 110: Detecting a phone call event;
[0045] Step 120: Detect whether the screen of the smart mobile terminal is turned on, and / or detect whether a keyboard key event or a touch screen event occurs on the smart mobile terminal;
[0046] Step 130: According to the detection result detected in step 120 when the call-out event is detected in step 110, determine whether the detected call-out event is a suspected malicious call;
[0047] Step 140: If the determination in step 130 is yes, preventive processing is performed to prevent malicious outgoing calls.
[0048] It should be noted that step 110 and step 120 may be performed simultaneously. In addition, step 110 or step 120 ca...
no. 2 example
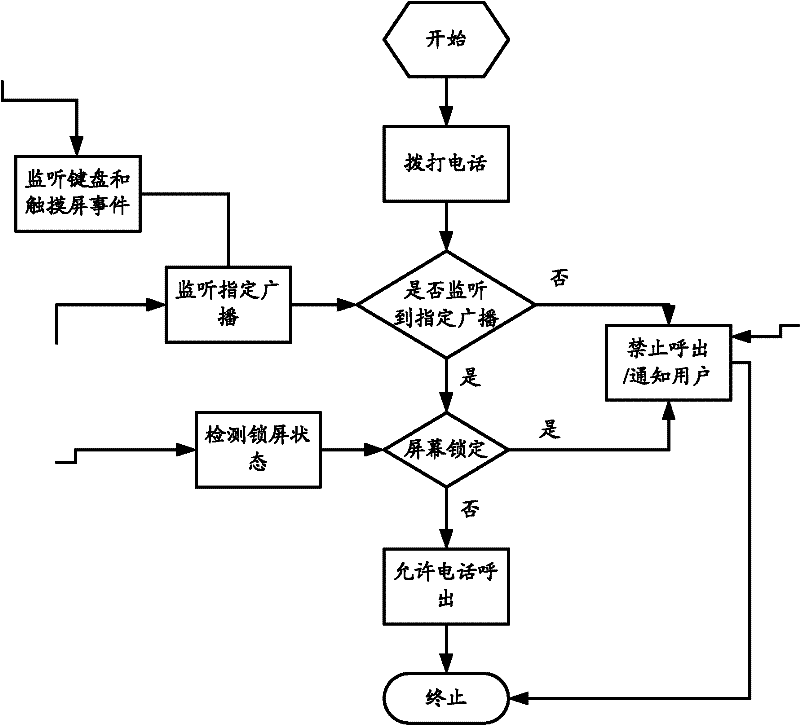
[0056] This embodiment describes in detail the method for preventing malicious calls from terminals based on the Android operating system by monitoring specified broadcast messages. figure 2 A flow example of the method for preventing malicious phone calls from terminals based on the Android operating system according to the present embodiment is given, and the steps of the present embodiment will be described in detail below with reference to the accompanying drawings.
[0057] For ease of description, the same steps as those in the foregoing embodiments will not be described in detail, but only the differences from the foregoing embodiments will be highlighted. exist figure 1 and 2 In the same or similar steps as those in the foregoing embodiments, the same reference numerals are used.
[0058] Step 110: Detect a phone call event.
[0059] Specifically, by modifying the source code of the Android operating system framework layer, a broadcast message can be sent to the ap...
no. 3 example
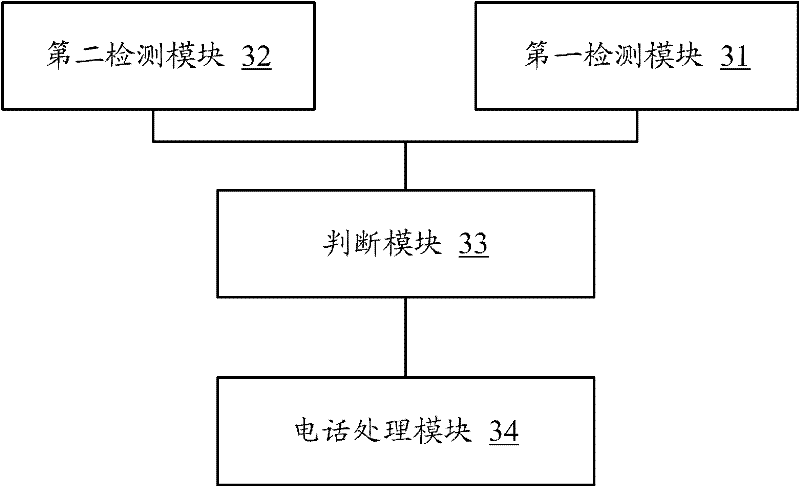
[0067] image 3 According to the third embodiment of the present invention, the mobile intelligent terminal operating system is a schematic diagram of the structure of a malicious phone dialing prevention device, which is referred to below image 3 To illustrate the composition of each part of this embodiment.
[0068] refer to image 3 , the first detection module 31 of this embodiment executes the processing of step 110 of the first embodiment. The second detection module 32 executes the processing of step 120 in the first embodiment. The judging module 33 executes the processing of step 130 in the first embodiment. In addition, the call processing module 34 executes the processing of step 140 in the first embodiment. It will not be expanded in detail here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com