Method for customizing role authorization in management information system
A management information system and self-definition technology, which is applied in the field of custom role authority in the management information system, can solve the problem of large amount of data in the UserAction table, and achieve the effects of clear design structure, high execution efficiency, and strong reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The method of the present invention is described in detail below with reference to the accompanying drawings.
[0022] A method for customizing role permissions in the management information system of the present invention, design of permissions based on roles and operations: the present invention is achieved through the following technical solutions:
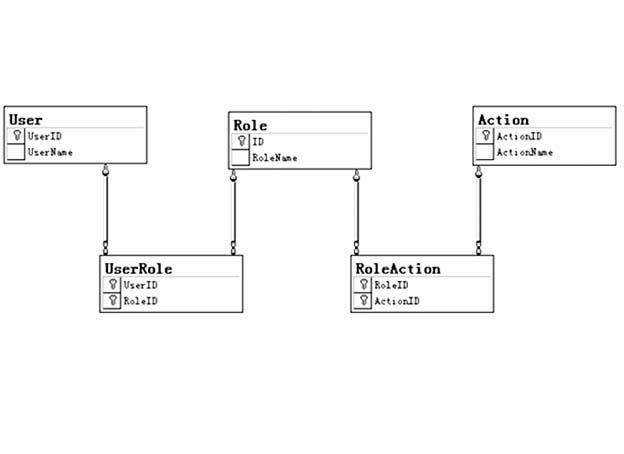
[0023] (1) Create two tables in the system, user table and permission table. Among them, the user table includes not only user name and password and other necessary information, but also user permission fields, and the permission table includes role names and various permission definition fields. These two tables are associated through the Role field;
[0024] (2) Set a corresponding field in the permission table for each user operation or even each event that requires permission control. A value of "1" means that there is permission to perform this operation, and a value of "0" means that there is no such permission. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com