Method for encrypting in sections by using uncertain encryption algorithm
A technology of segmented encryption and encryption algorithm, applied in the field of cryptography, can solve the problems affecting the security of the algorithm, and achieve the effect of increasing the generalized key space, optimizing the comprehensive performance and enhancing the security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The following are embodiments of the invention, For convenience, the example is relatively simple.
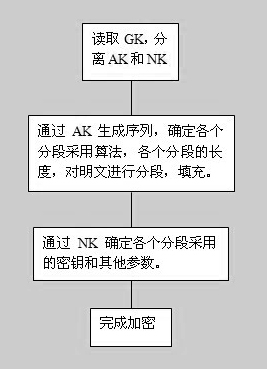
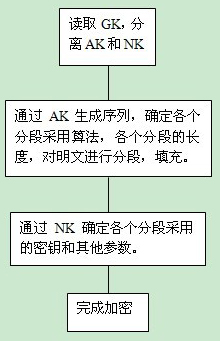
[0025] First of all, in terms of the design of the encryption system, a 256-bit stream cipher is used to generate an algorithm-encoded sequence. The stream cipher is used to ensure security. Even if the algorithm used in some previous segments is known, it is impossible to use it to obtain other segmented encryption algorithms. The structure of the generalized key is that the first 256 bits are AK, and the last 512 bits are NK. It is agreed that the encrypted plaintext length of each algorithm is: block cipher algorithm and other block algorithm is a single block length, stream cipher and one-time pad algorithm is 128bit, the purpose of this selection is to make the algorithm change more frequently, and the same algorithm The encryption length of is as small as possible, and try not to exceed the unique solution distance.
[0026] Determination and coding of the alg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com