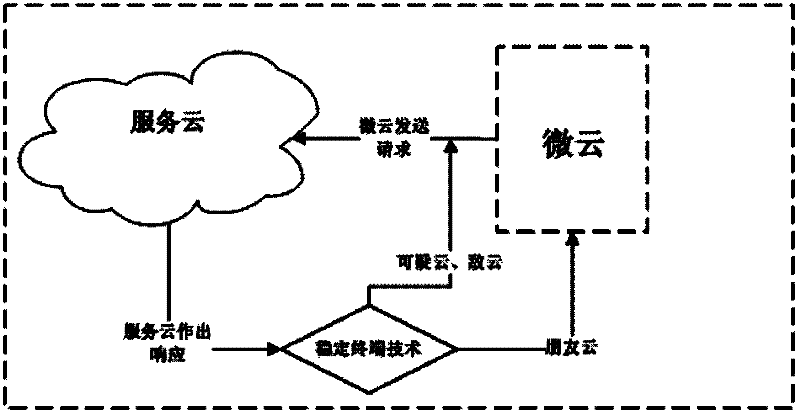
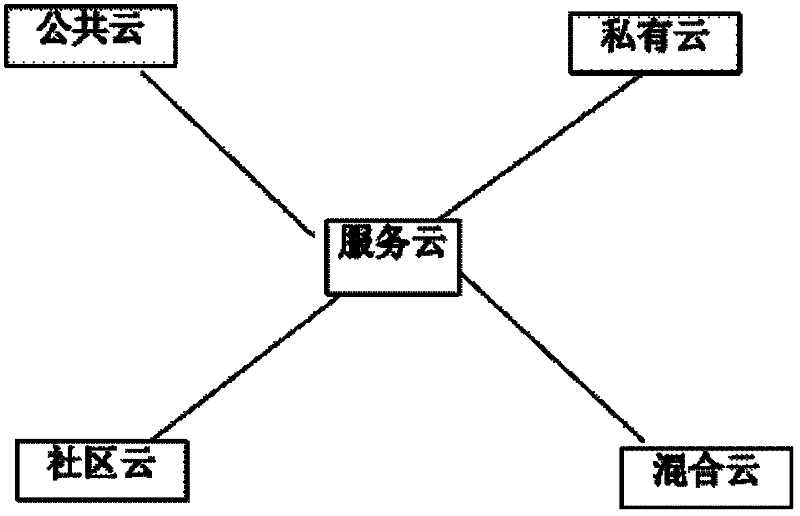
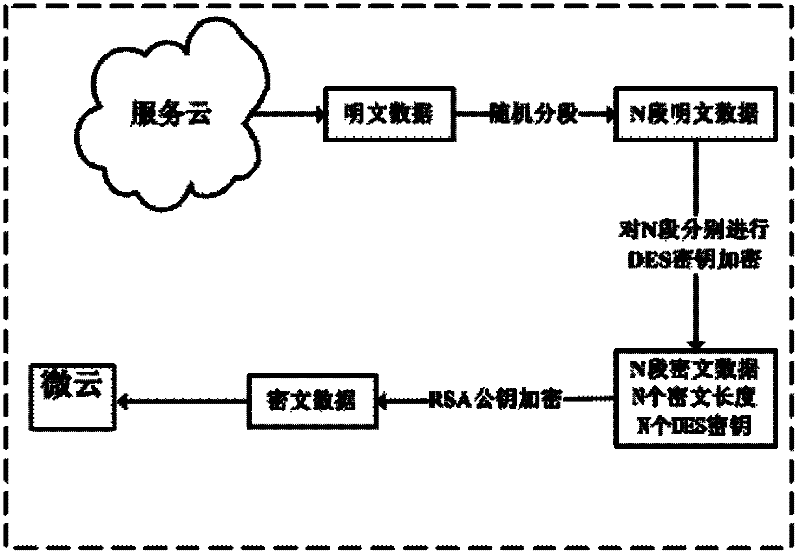
Data security insurance method in cloud computing environment
A cloud computing environment and data security technology, applied in the field of cloud computing services, can solve problems such as imperfect industry standard national supervision and management system, catastrophic impact, hidden dangers, etc., and achieve clear and feasible results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Embodiments of the present invention are described in detail below in conjunction with the accompanying drawings:
[0031] The data security guarantee method in the cloud computing environment first needs to carry out the following operations: improve the relevant use mechanism of cloud technology, and impose requirements on the service life of cloud computing. Once you become a cloud computing service provider, you cannot terminate the service at will within five years.
[0032] The provision or termination of cloud computing services requires the approval and approval of strict legal procedures, and the market cannot be allowed to enter and terminate at will. This guarantees the threshold of entering the enterprise to a certain extent, and also helps to control the independent property rights of cloud computing services in the hands of the state and powerful enterprises, so that users can enjoy services conveniently. At the same time, when problems arise, there are la...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com