Network security situation fuzzy evaluation method based on uncertain data
A network security and fuzzy evaluation technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the ambiguity of ignoring attribute data and network security status. Network security attribute importance uncertainty, great influence, uncertainty There are many factors, etc., to achieve the effect of solving the problem of data uncertainty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
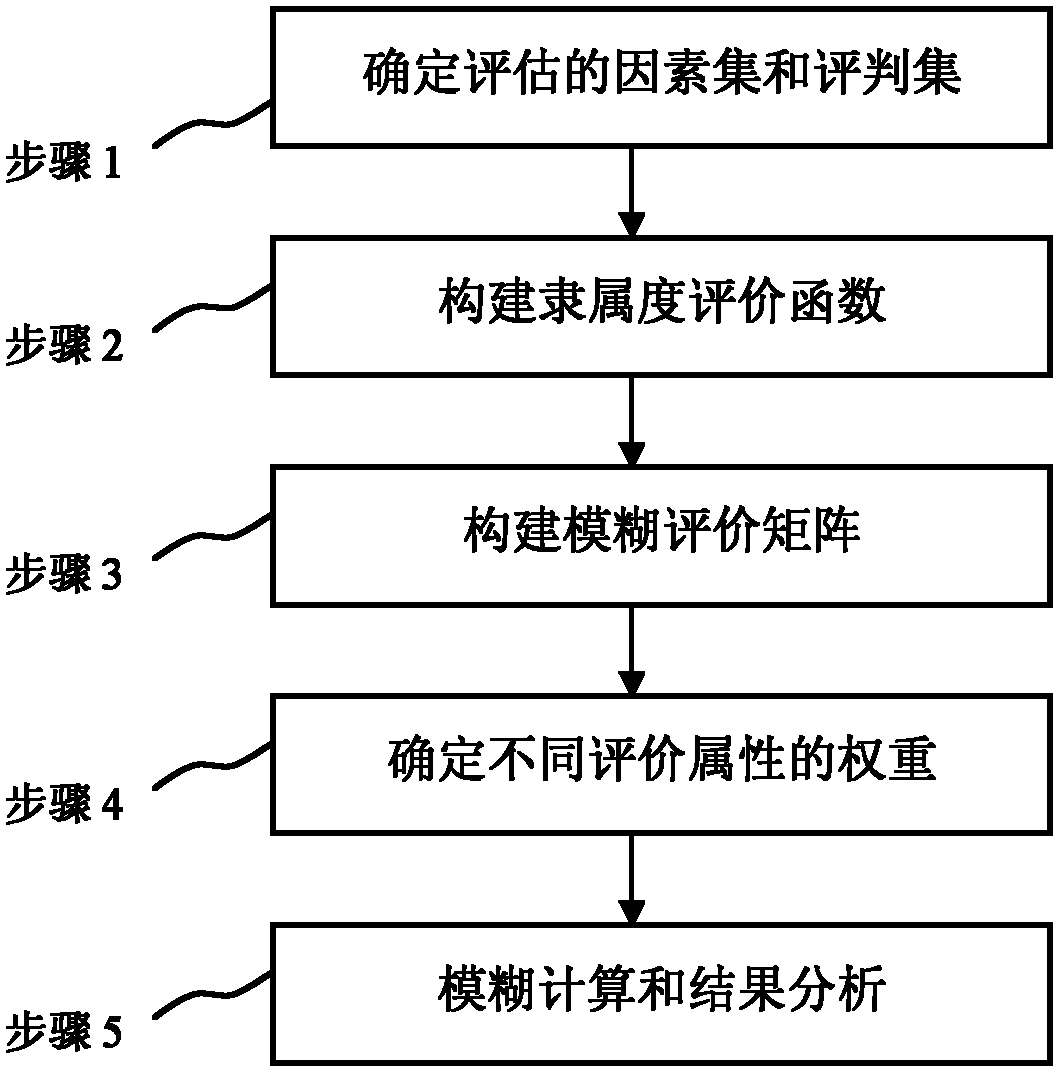
[0045] The present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
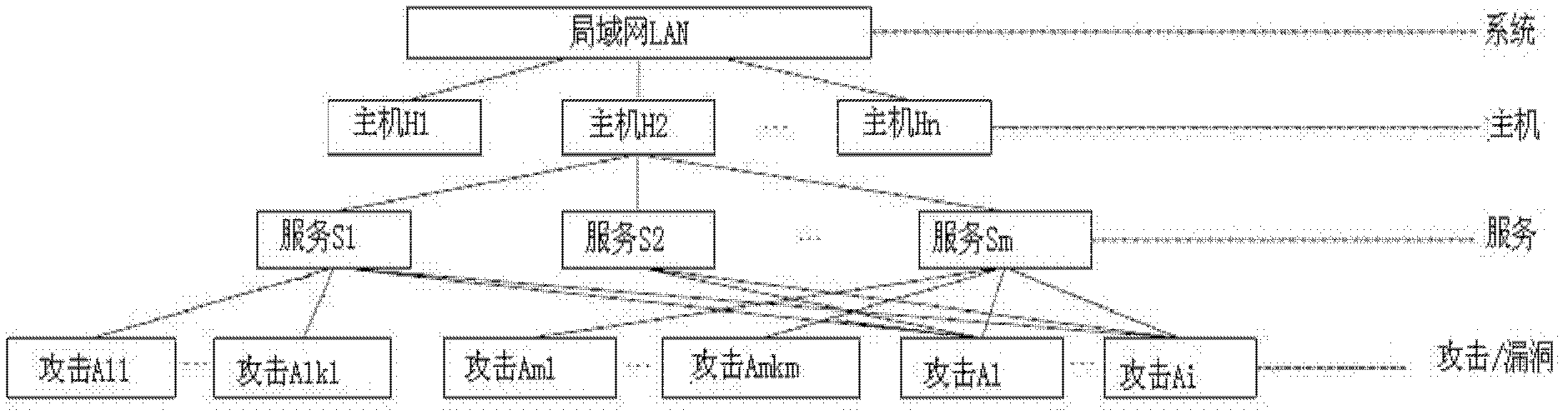
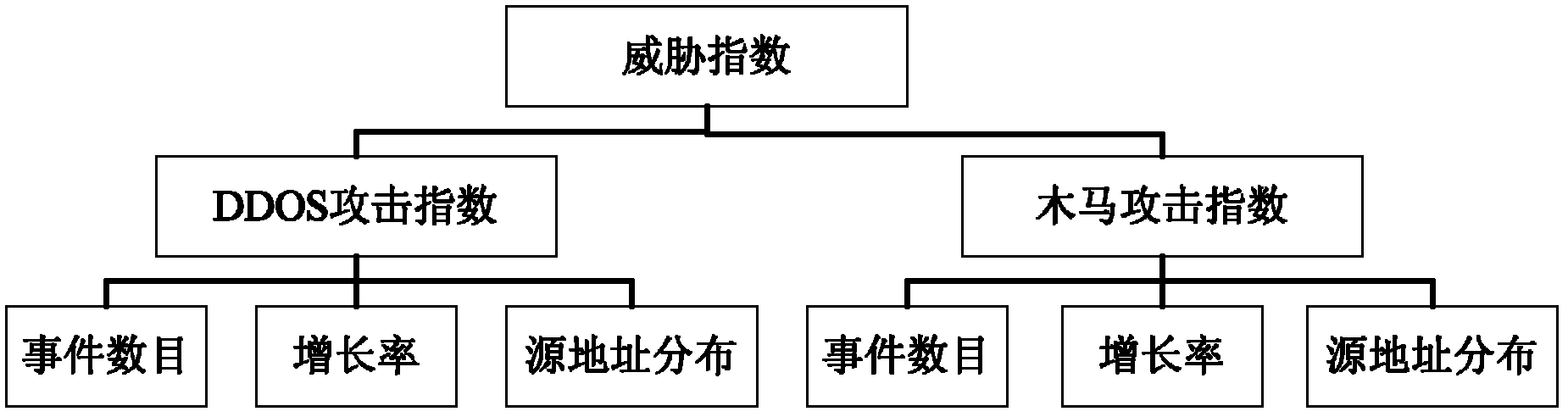
[0046] figure 2 It is a hierarchical model of the network security index system according to the embodiment of the present invention. Such as figure 2 As shown, the model includes three index layers, namely: the top index layer including the top layer nodes, the middle index layer including the middle layer child nodes, and the bottom index layer including the bottom layer child nodes. Among them, each node represents an attribute of the network security index system, such as figure 2 As shown in , the top-level node is the network attack situation that network security managers are concerned about, which is measured by the threat index; the middle-level sub-nodes are the distributed denial-of-service attack index and the Trojan attack index used to evaluate the threat index; the bottom-level sub-nodes Usually it is attribute data that can be col...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com