A method and device for preventing tcp insertion denial of service attack
A denial of service attack and plug-in technology, applied in the field of Internet transmission, can solve the problems of protocol principle attack and failure to consider, and achieve the effect of ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
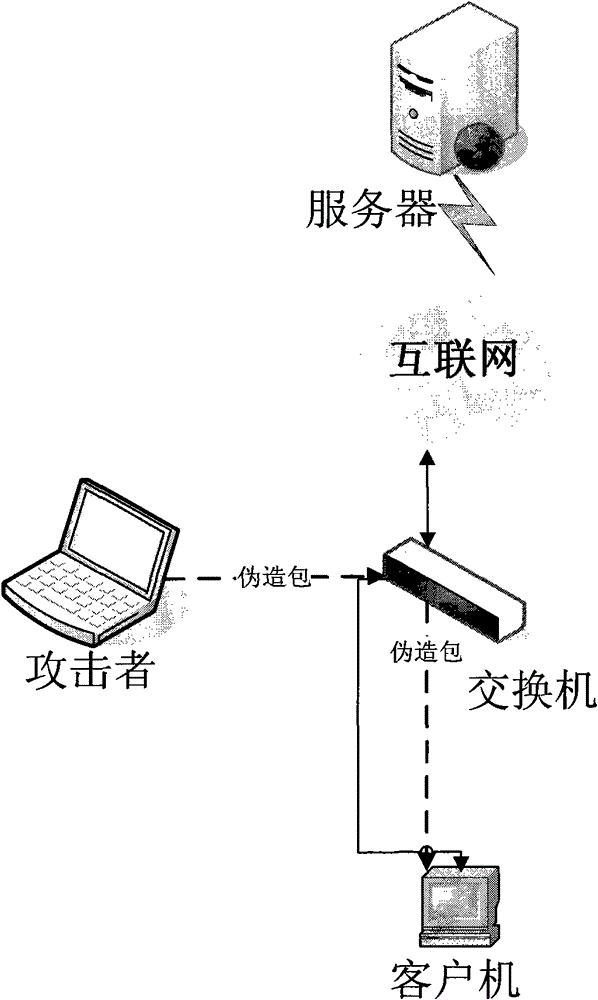
[0028] At present, the TCP insertion denial of service attack needs to meet three conditions: 1) the attacker must be able to monitor all the TCP communication data packets between the client and the server; 2) the attacker can write his forged data packets to the network 3) According to the requirements of the TCP protocol, if a TCP connection receives the RST end packet sent by the other party, this connection must be closed.
[0029] Such as figure 1 As shown, we analyze the TCP insertion denial-of-service attack. First, let’s look at the process of ending the connection normally initiated by the client. The TCP connection should be closed without sending any notification.
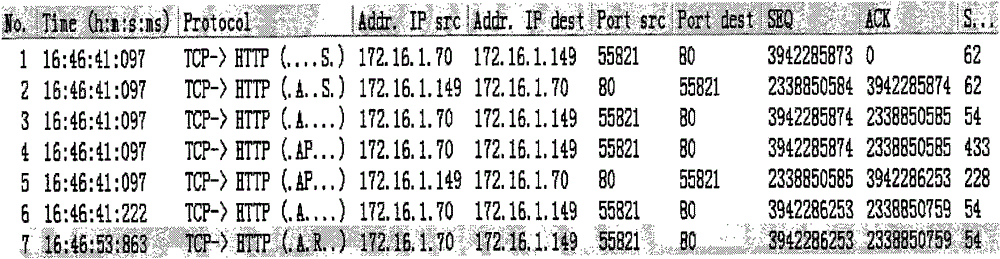
[0030] Such as figure 2 It is a TCP communication process of a normal communication packet. The data packet No.7 in the figure is the RST packet initiated by the client (the TCP data packet is marked as AR). After the data packet is sent, the TCP connection is directly closed.
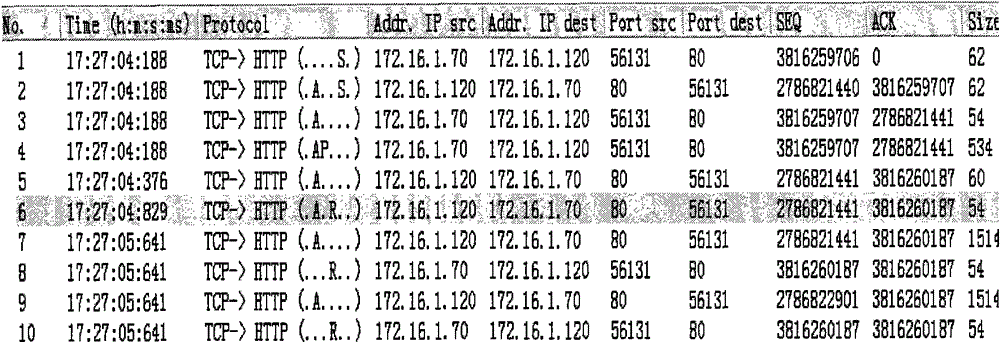
[0031] Let's take a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com