Prevention of masquerade by using identification sequences
A technology of identification sequence and identification, which is applied in the direction of data exchange, digital transmission system, bus network, etc. through path configuration, which can solve the problems of misinterpretation of information, distortion of message analysis and processing of message identification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
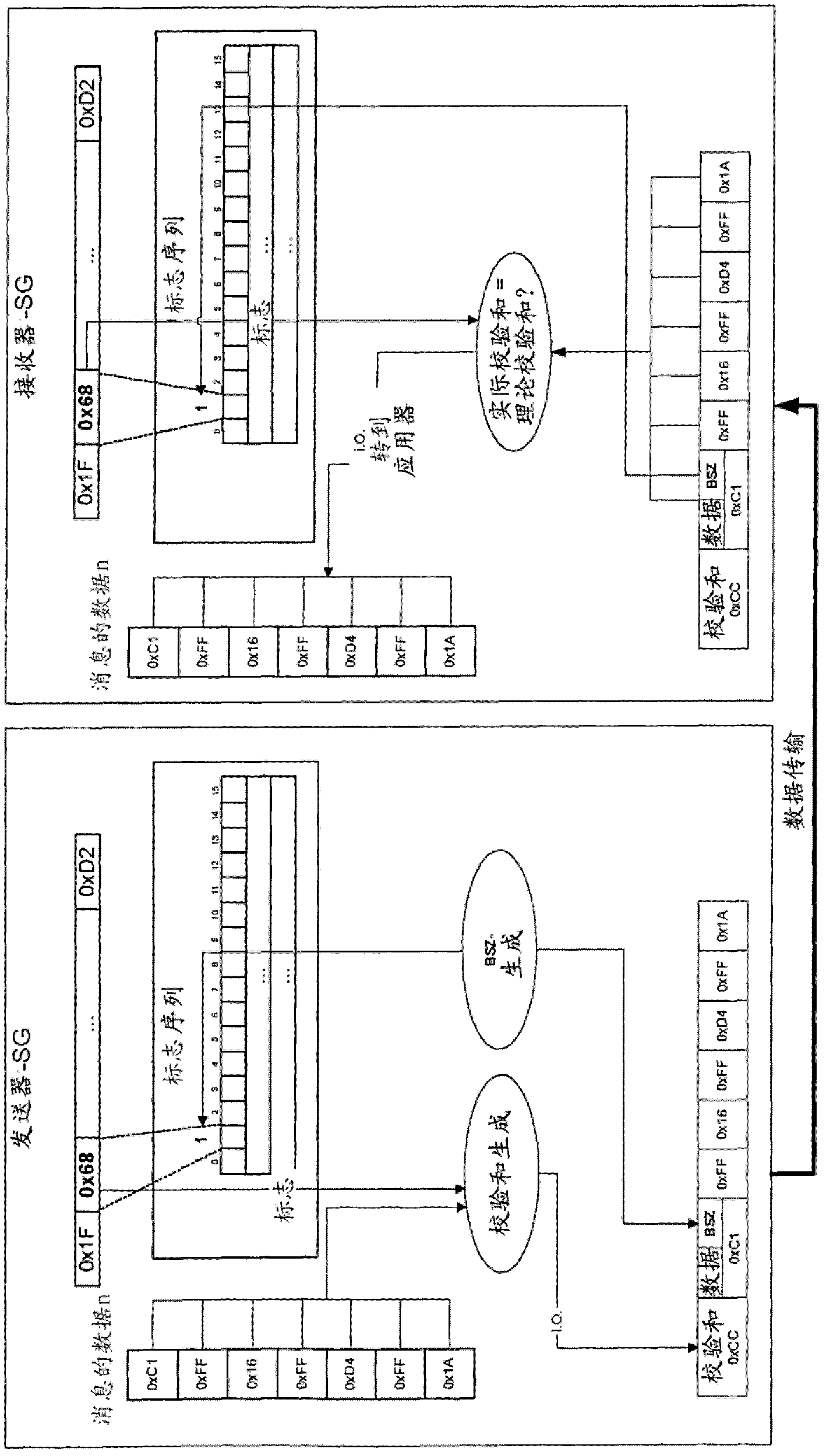
[0032] In order to transmit messages on the bus, an applicator provides usable data from dense signals for cyclic transmission. For security measures against transmission errors, a message counter (BSZ) and CRC-8 checksum are added to the available data. Then the S-PDU generated in this way is transmitted from the applicator to the standard software and is transmitted to the communication controller (CC) for transmission.
[0033] In the described method for anti-counterfeiting security measures, both in the transmitter and the receiver, in order to calculate the CRC checksum according to the available data to be secured, a static one is calculated and is related to the transmitter / receiver section. The message ID. However, the message identification is not sent over the bus and is therefore not a part of the secured message. For each receiver, the message identification is known a priori for all messages to be received. The correct assignment of the message identifier to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com