Method for accessing private network through layer 2 tunneling protocol and server
A layer-2 tunneling protocol and server technology, applied in the field of methods and servers, to achieve the effect of convenient access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the object, technical solution and advantages of the present invention clearer, the solutions of the present invention will be further described in detail below with reference to the accompanying drawings and examples.
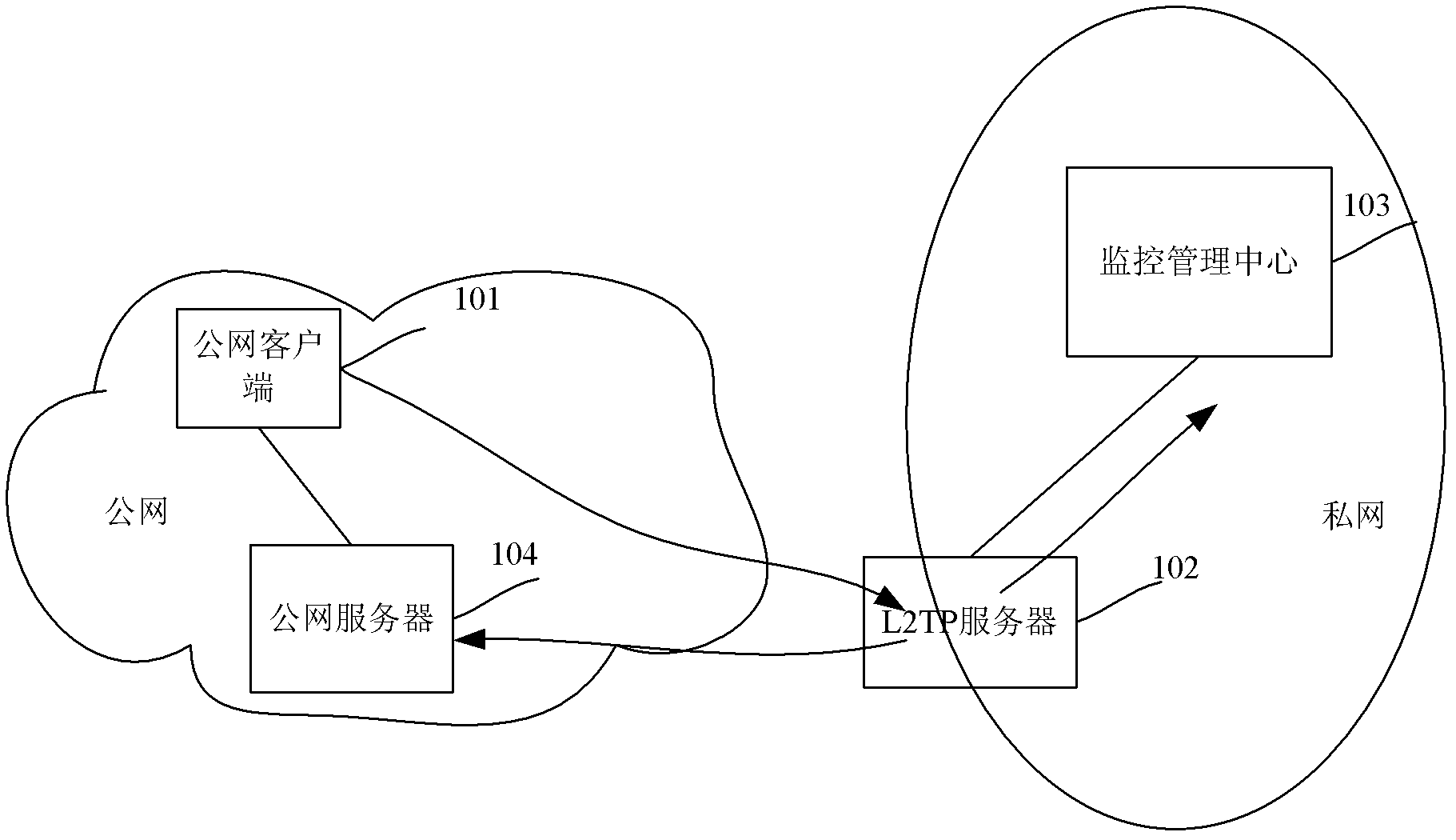
[0022] In the embodiment of the present invention, a method for accessing a private network through L2TP is proposed. After the LNS establishes a connection with the public network client, the public network client forwards all messages through the established connection, that is, after the connection is established, the public network The client will add a default route locally, and all packets sent by default will be forwarded through the established connection. The process of establishing a connection is the same as the existing implementation, and will not be repeated here.
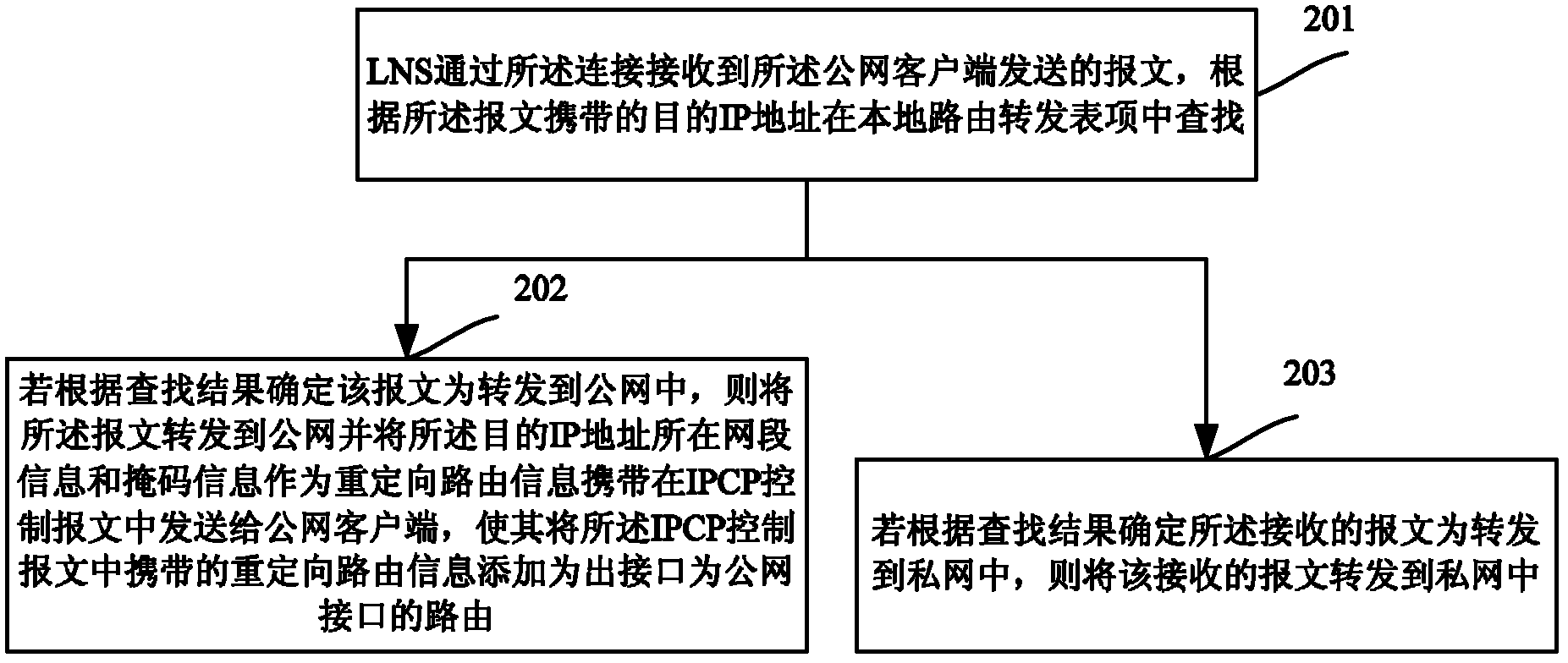
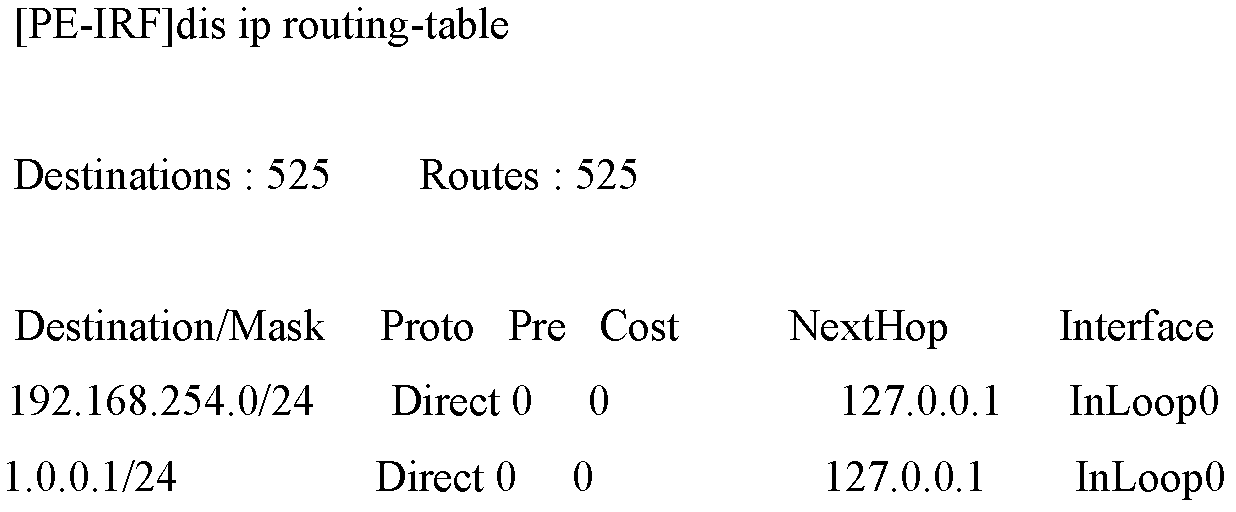
[0023] see figure 2 , figure 2 It is a schematic flowchart of a method for accessing a private network through L2TP in an embodiment of the present inventi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com