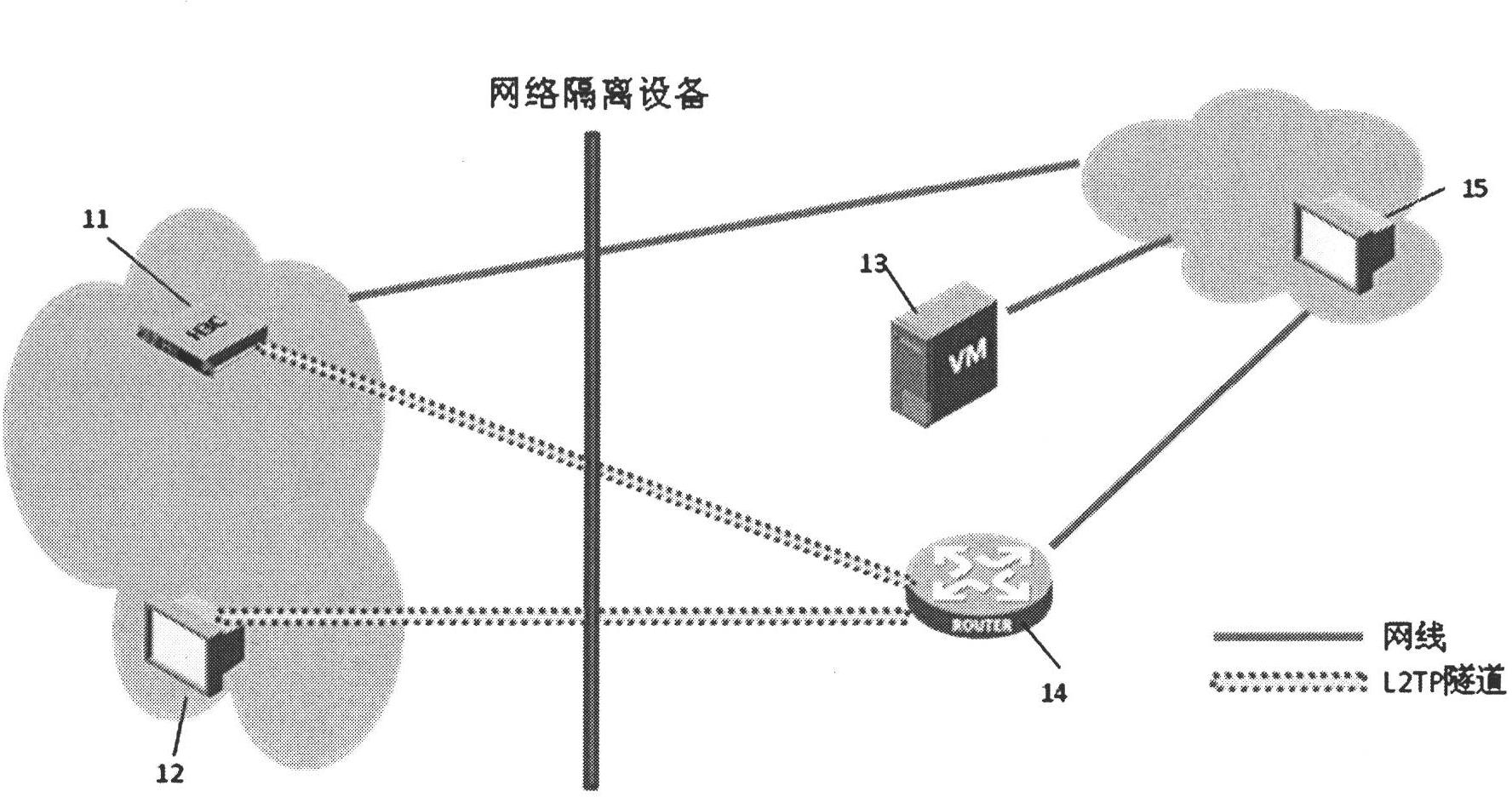
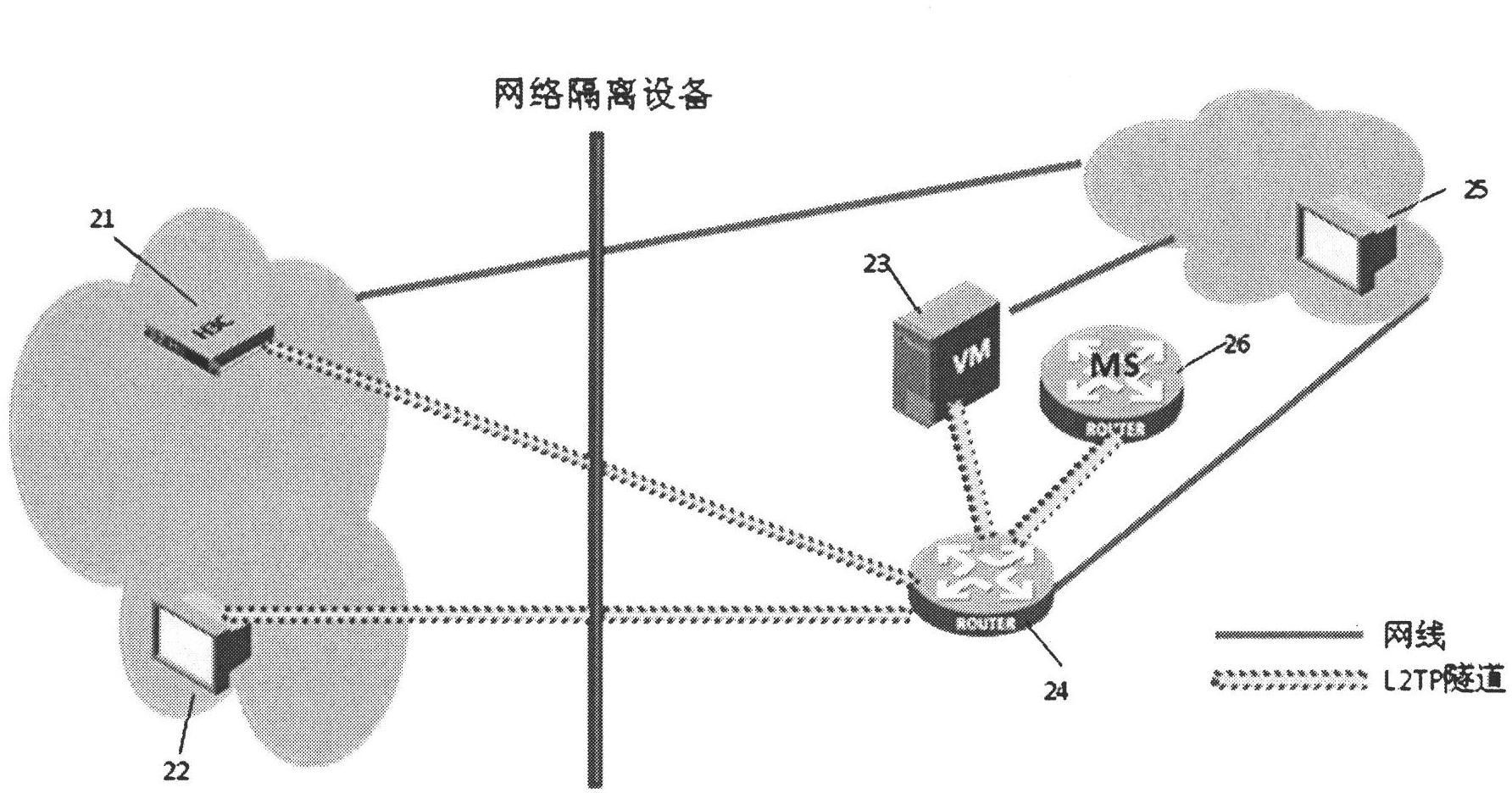
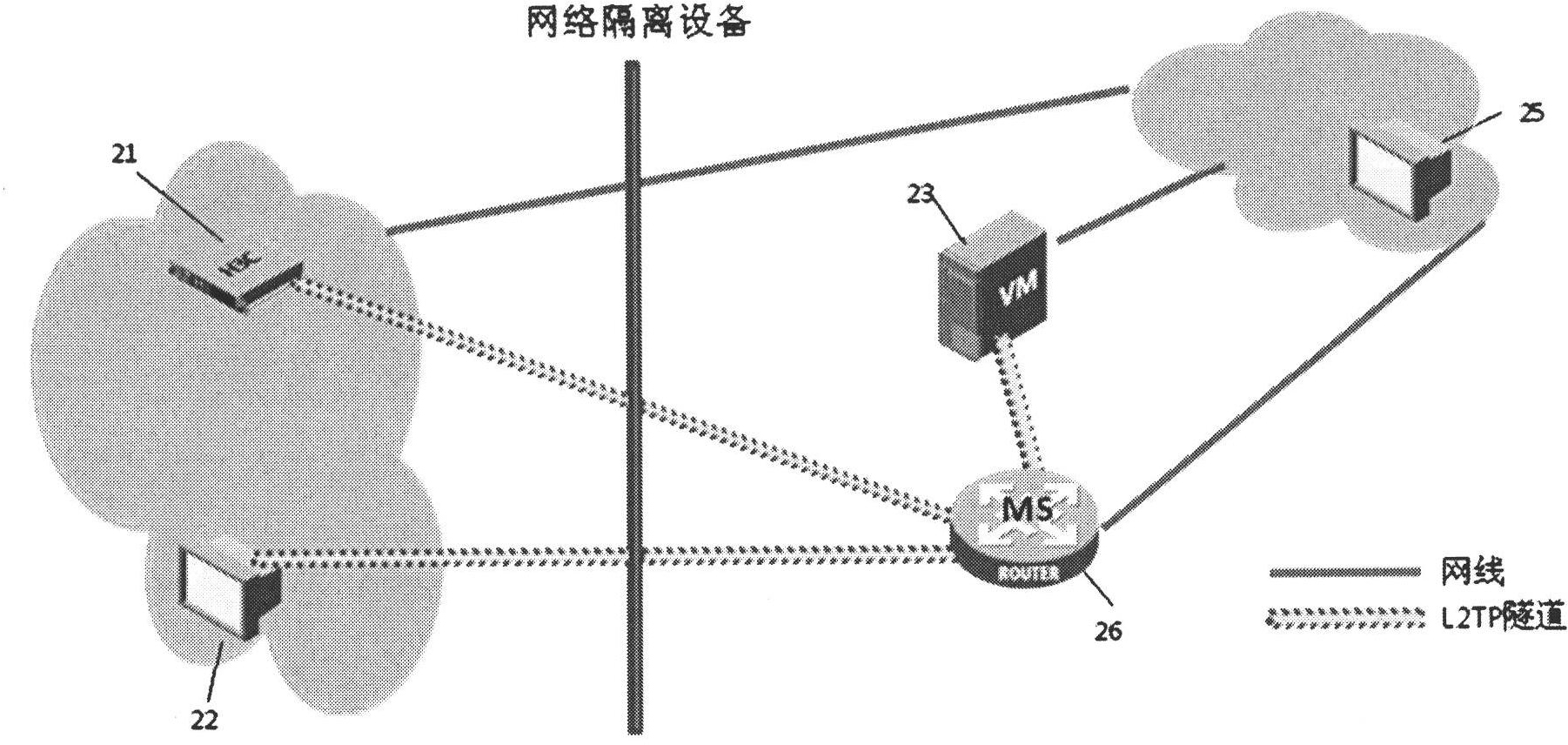
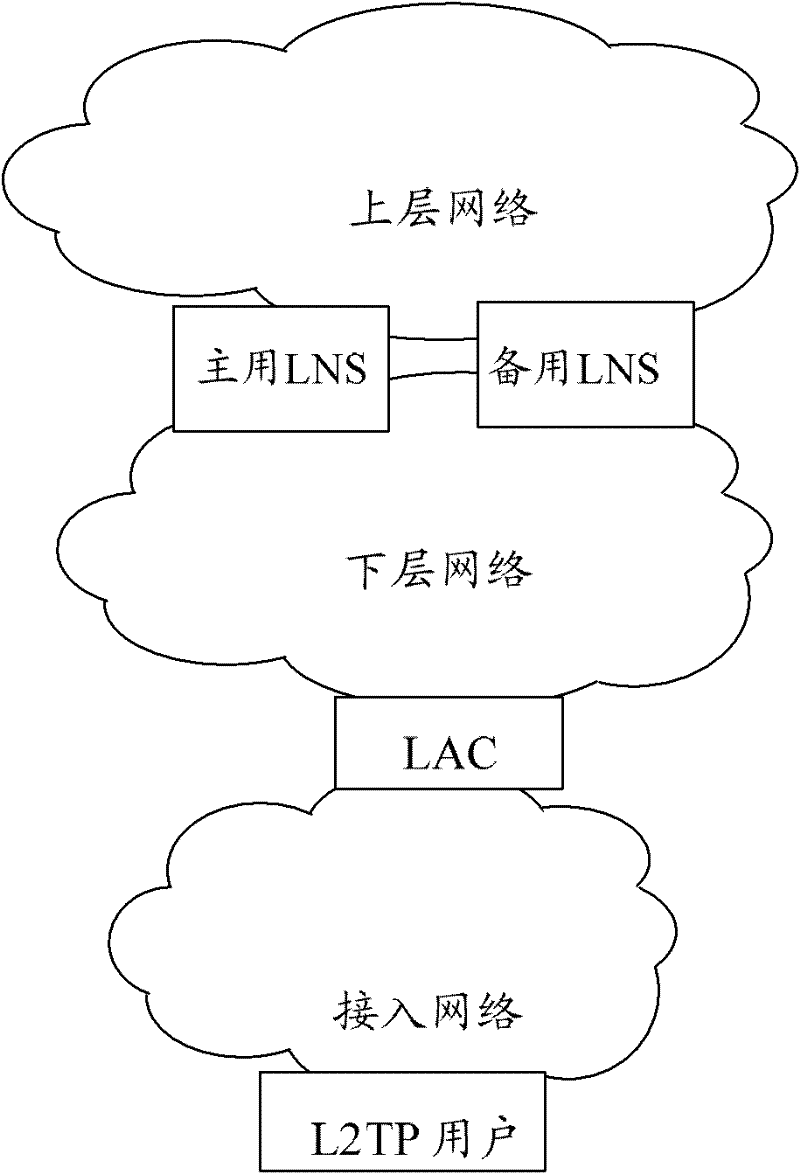
Patents
Literature
71 results about "Layer 2 Tunneling Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
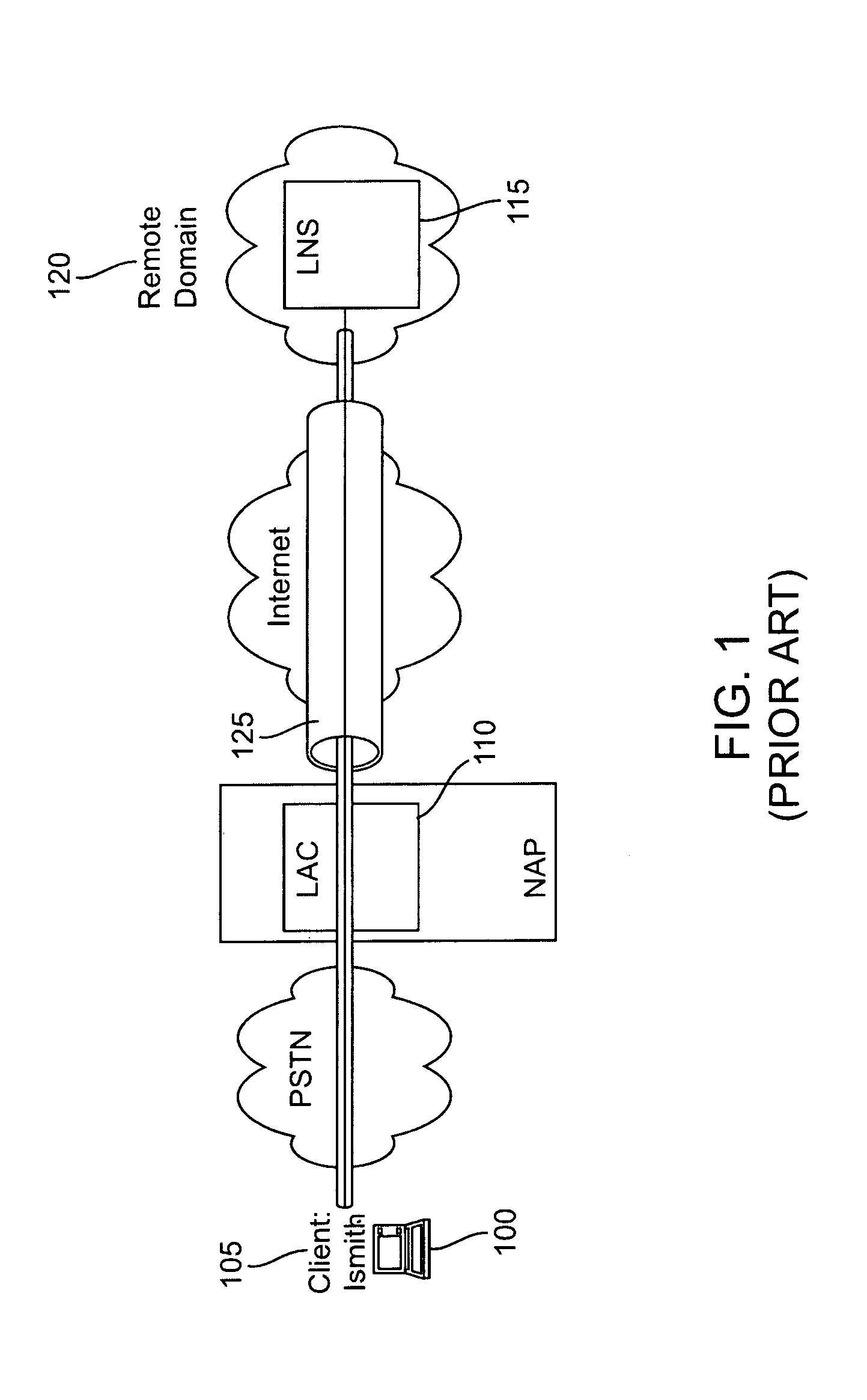
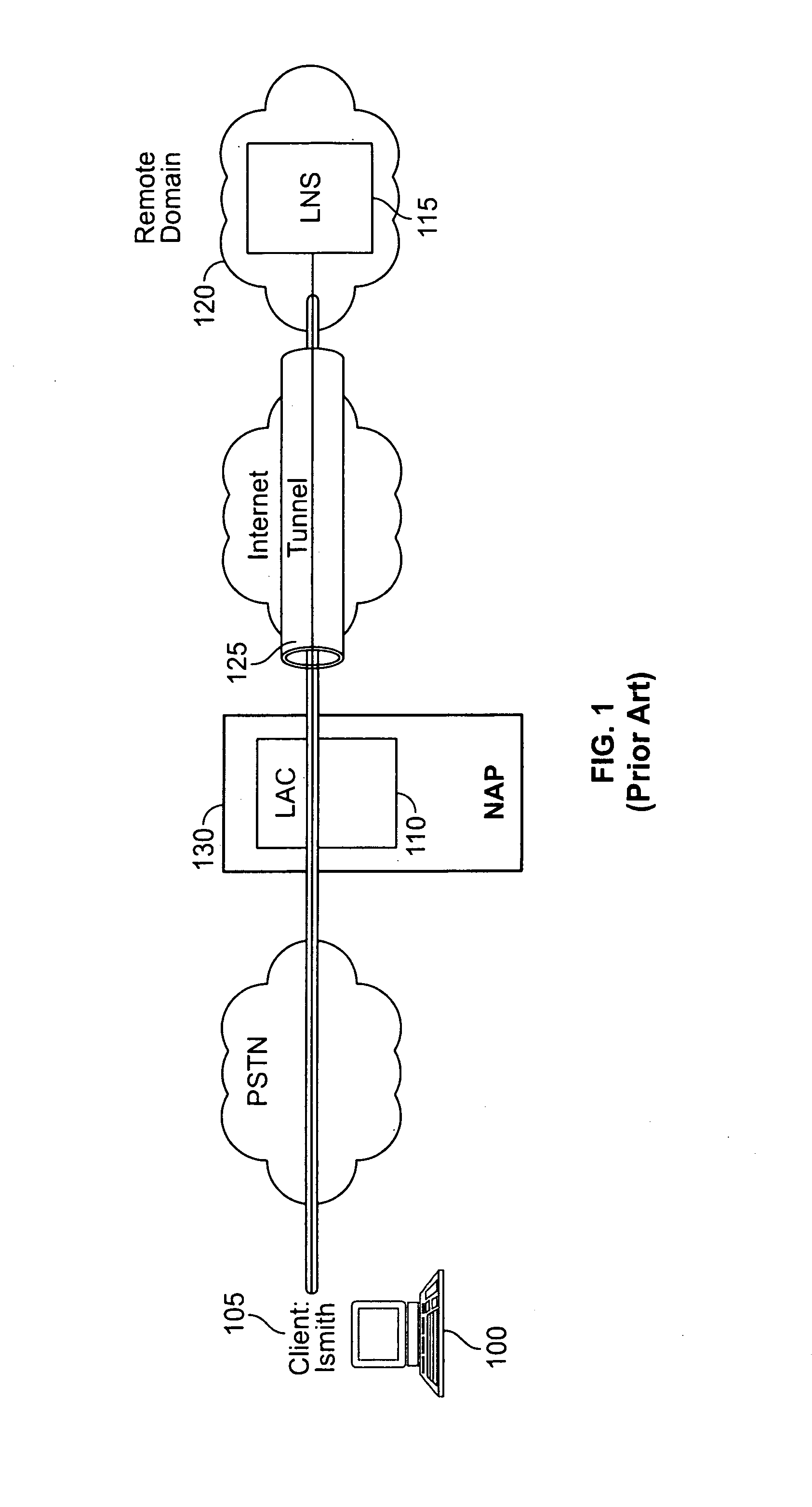
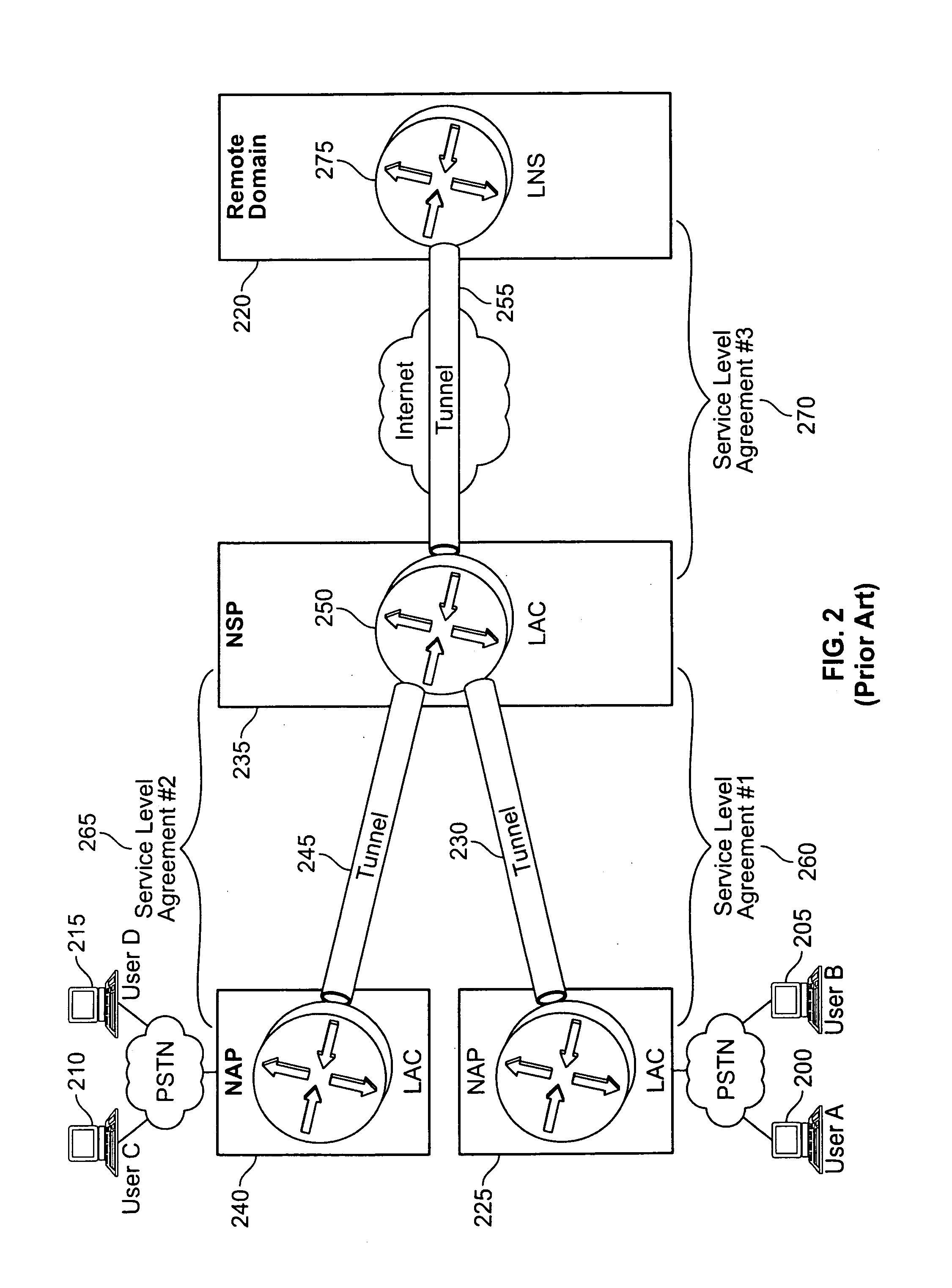
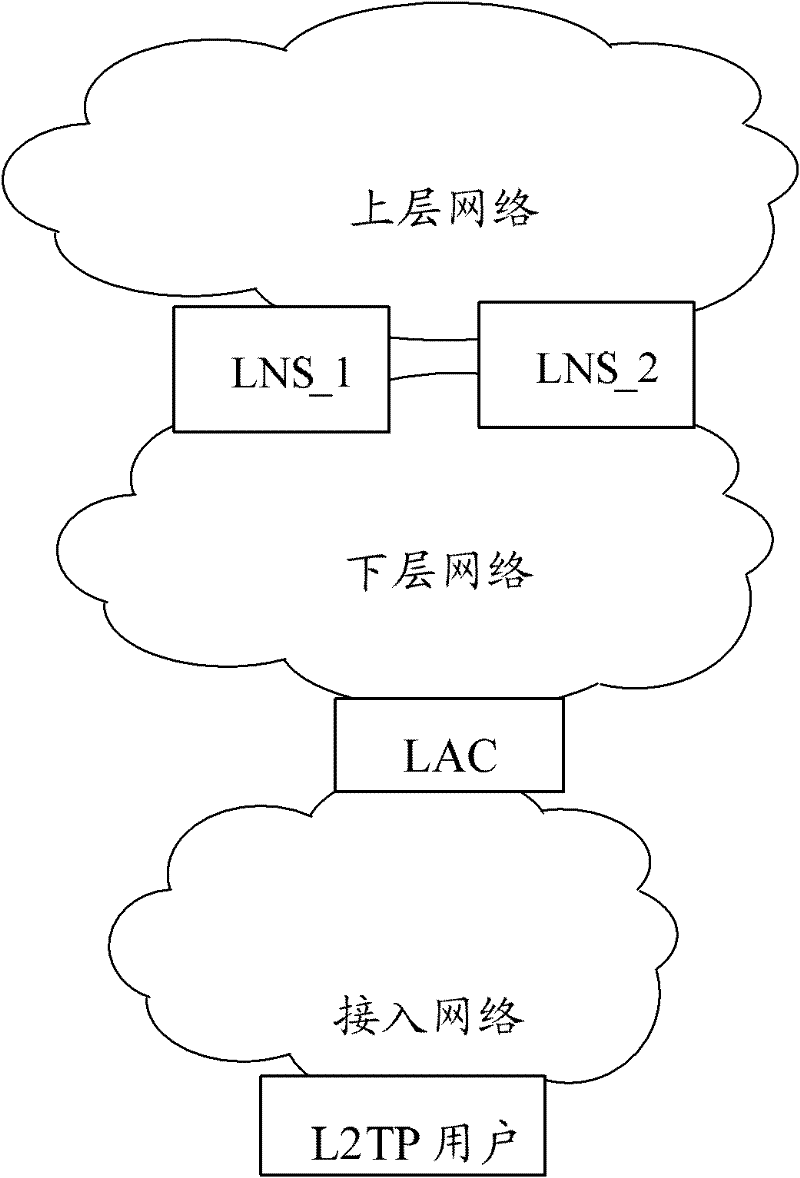
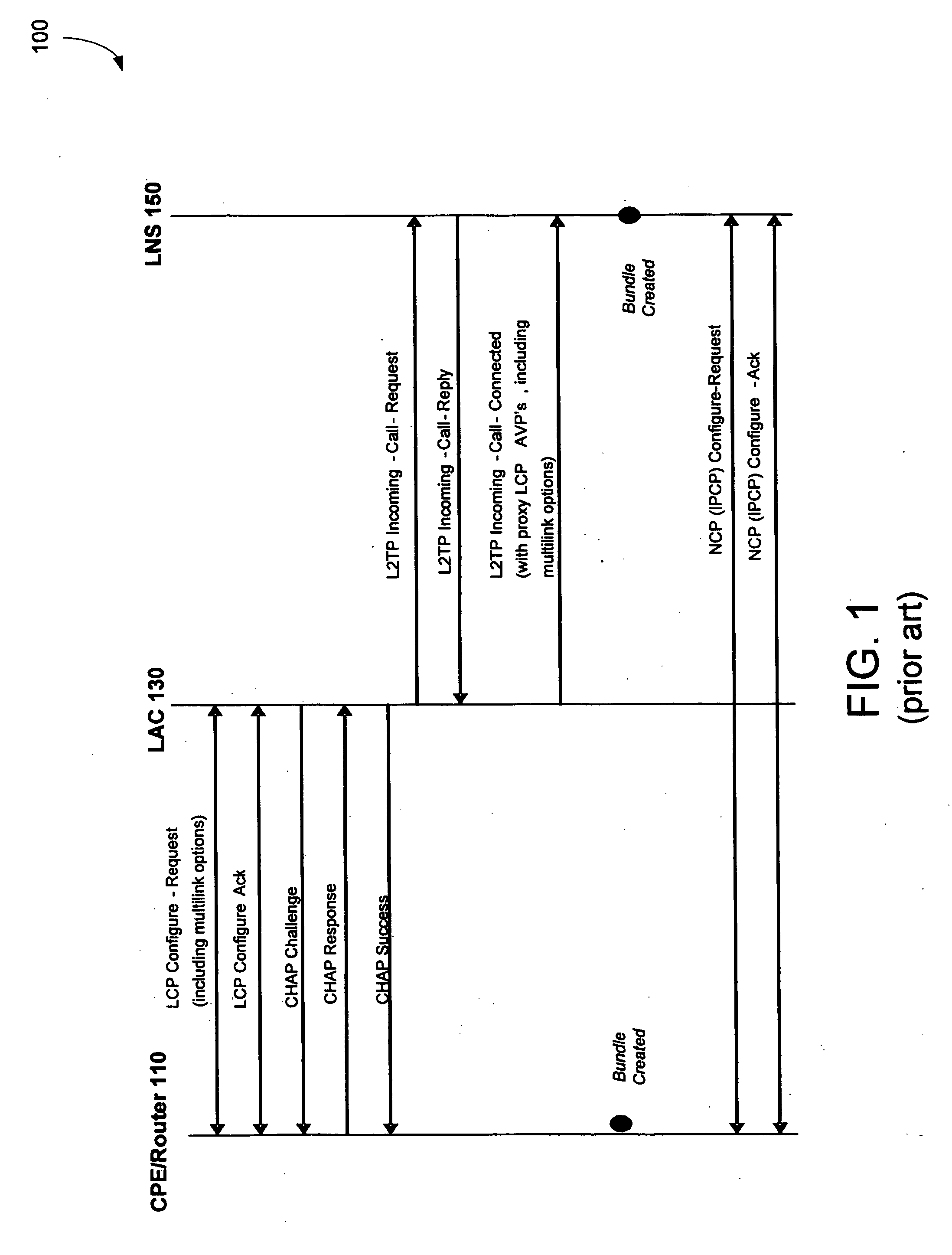
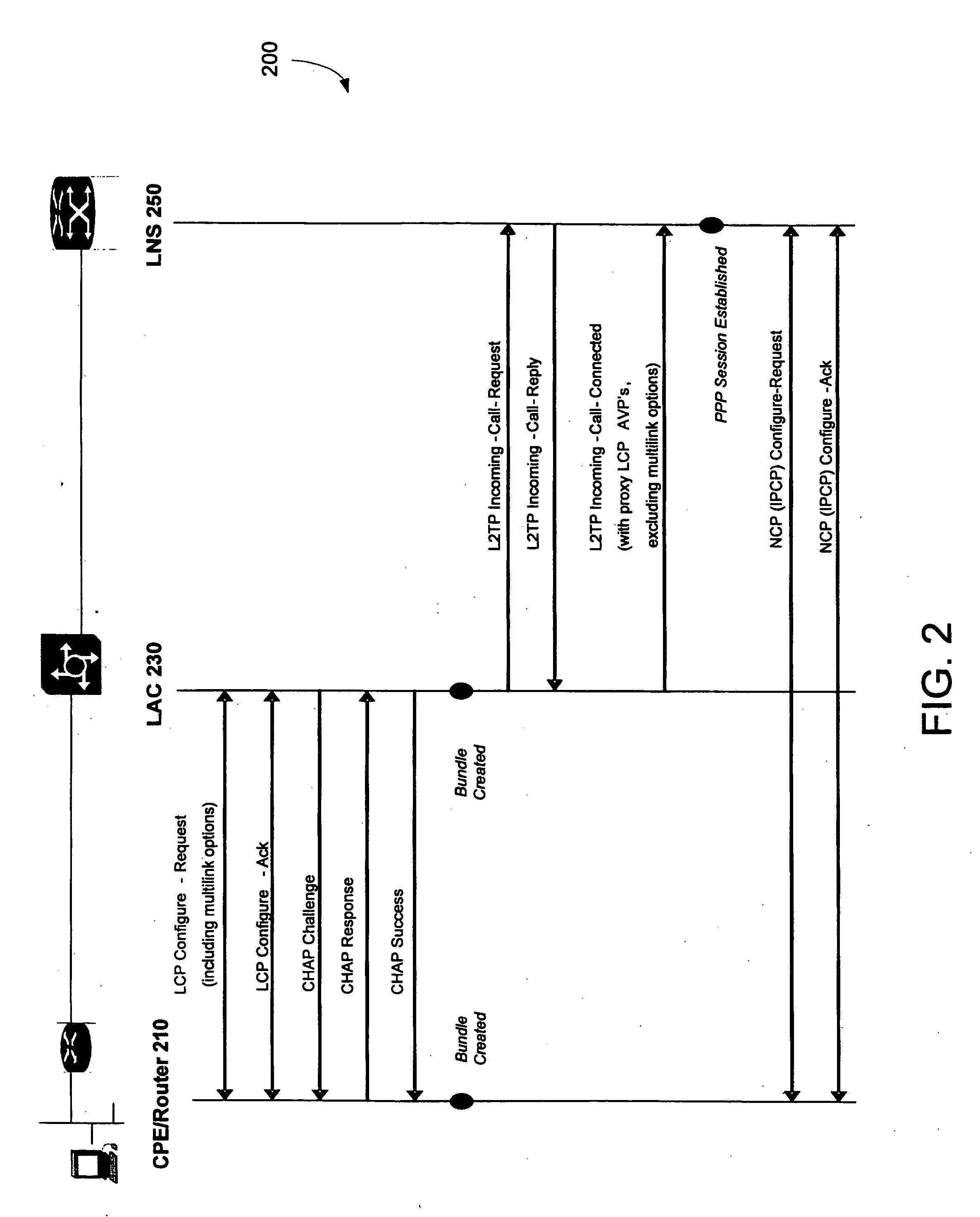
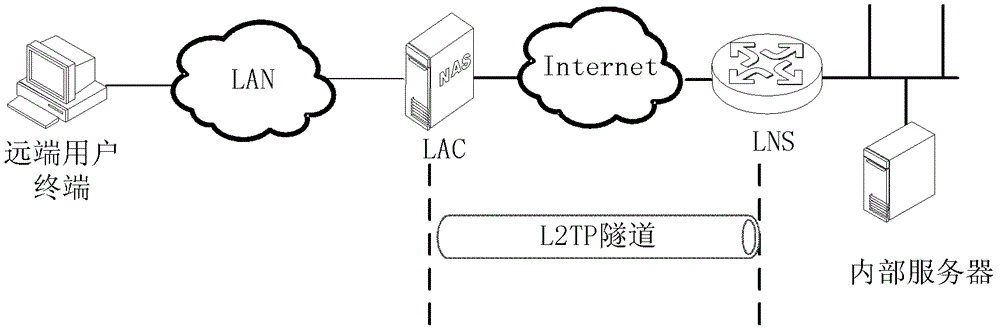
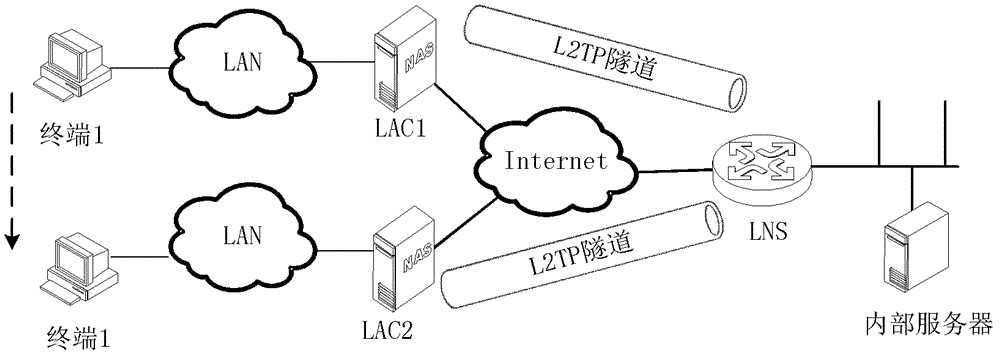
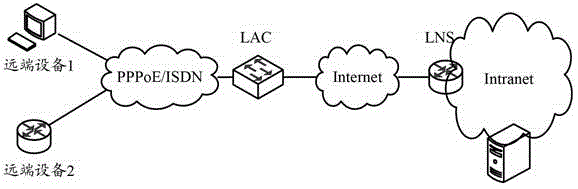
In computer networking, Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the delivery of services by ISPs. It does not provide any encryption or confidentiality by itself. Rather, it relies on an encryption protocol that it passes within the tunnel to provide privacy.
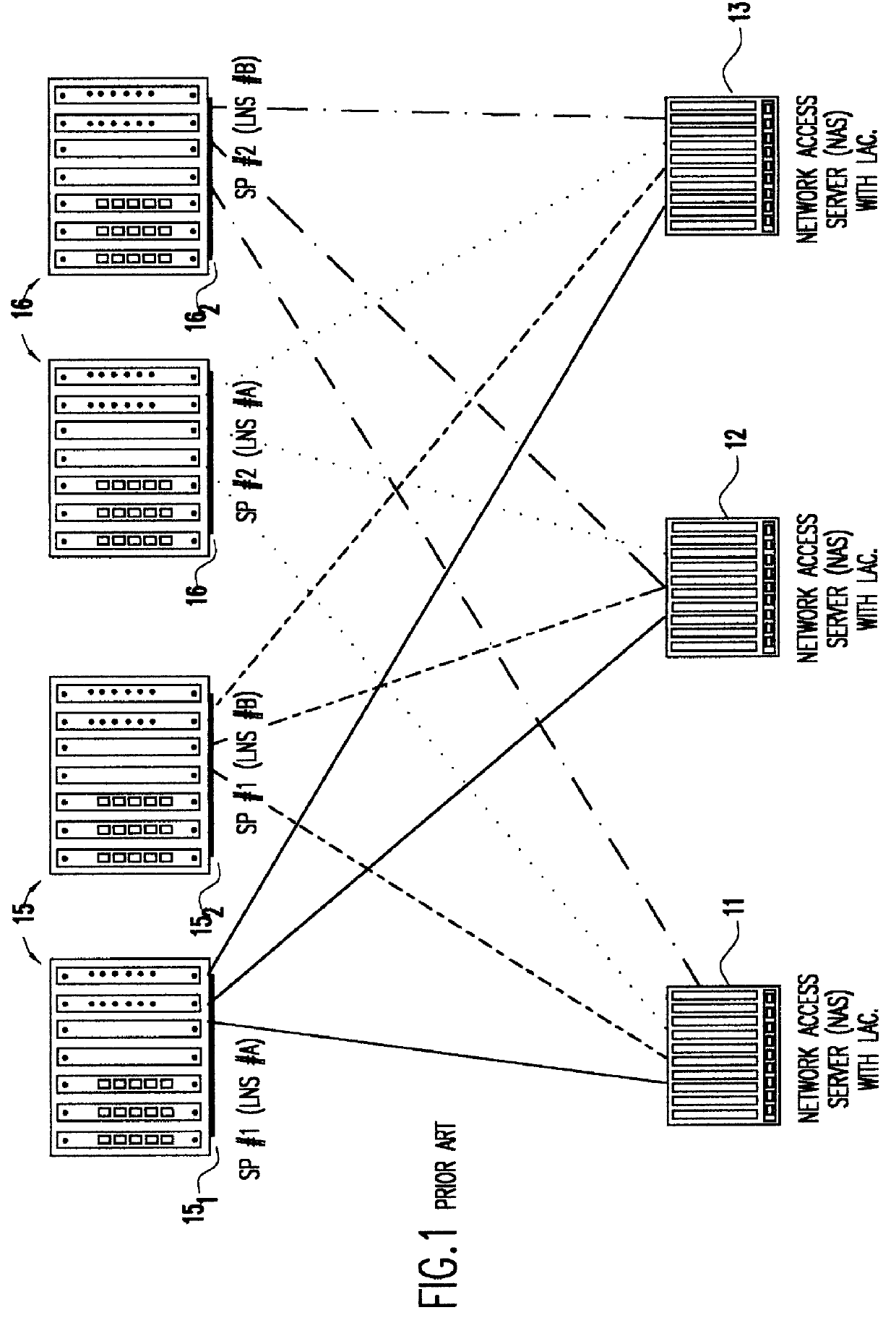
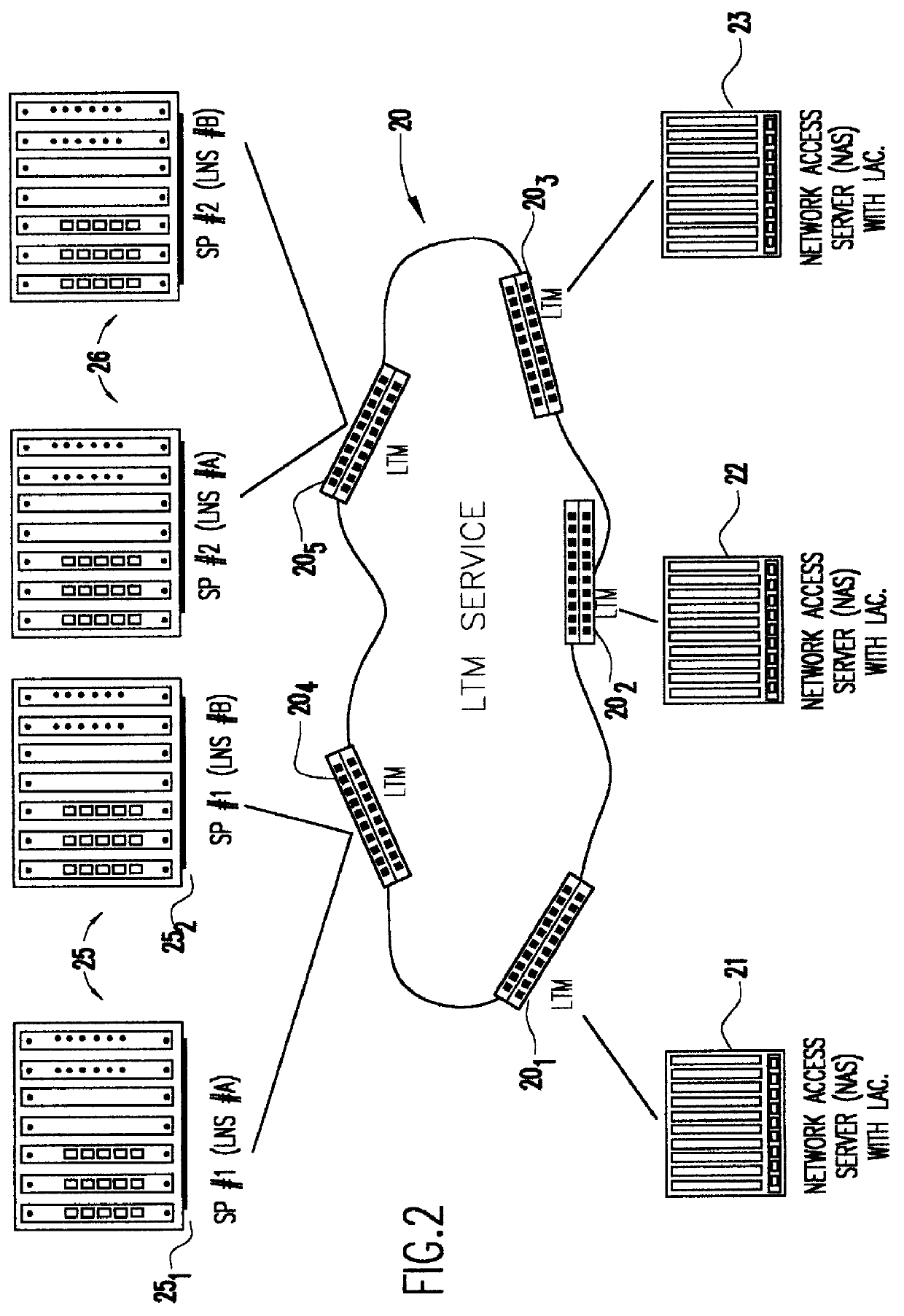
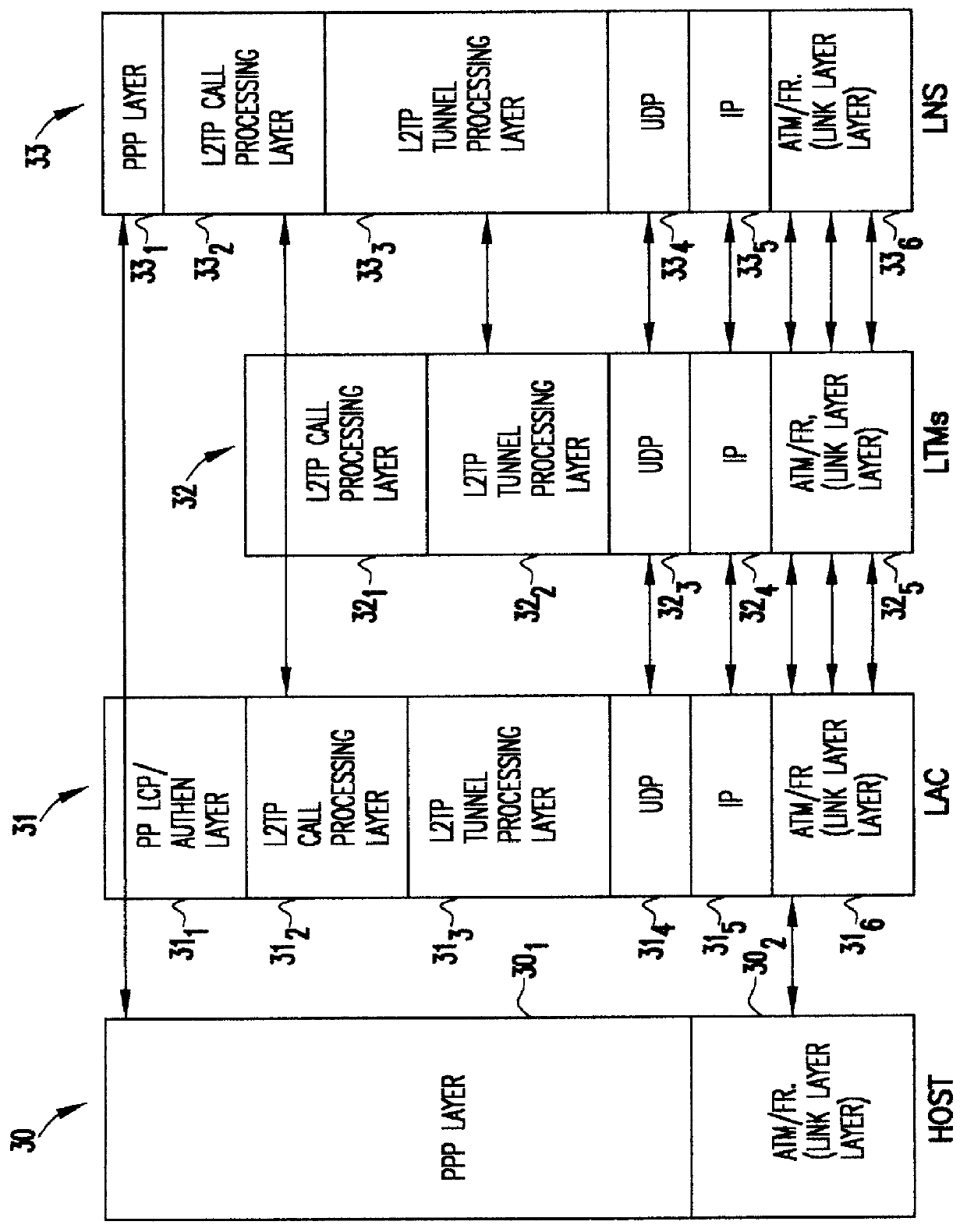
Layer two tunneling protocol (L2TP) merging and management
InactiveUS6094437AEasy to implementReduce complexityData switching detailsNetworks interconnectionDistributed computingEdge device
A system is provided for creating a tunneling service from the use of a traditional tunneling protocol, such as the layer two tunneling protocol (L2TP). In particular, the L2TP tunneling protocol, which is designed to go point-to-point between an L2TP Access Concentrator (LAC) and an L2TP Network Server (LNS), is abstracted so that L2TP becomes an access protocol to a tunneling service. A new L2TP tunnel merger and management (LTM) service is created which severs the tight configuration relationships between LAC and LNSs. Only a tight configuration between an LAC and its LTM edge device and between an LNS and its LTM edge device is required. An internal trunk protocol (INT protocol) carries needed information between LTM edge devices to establish ingress / egress L2TP access calls inside of separate L2TP access tunnels on opposite LTM edge devices. The addition of another LAC is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LNSs, and the addition of another LNS is accomplished by re-routing L2TP tunnels within the LTM service without reconfiguration of the LACs. The LTM service determines the need for both additional trunk and access resources and establishes both new trunk / access tunnels to provide additional resources. The LTM service also determines excess resources on both trunk and access entities and releases trunk / access tunnels to provide the needed additional resources.
Owner:TDC THE
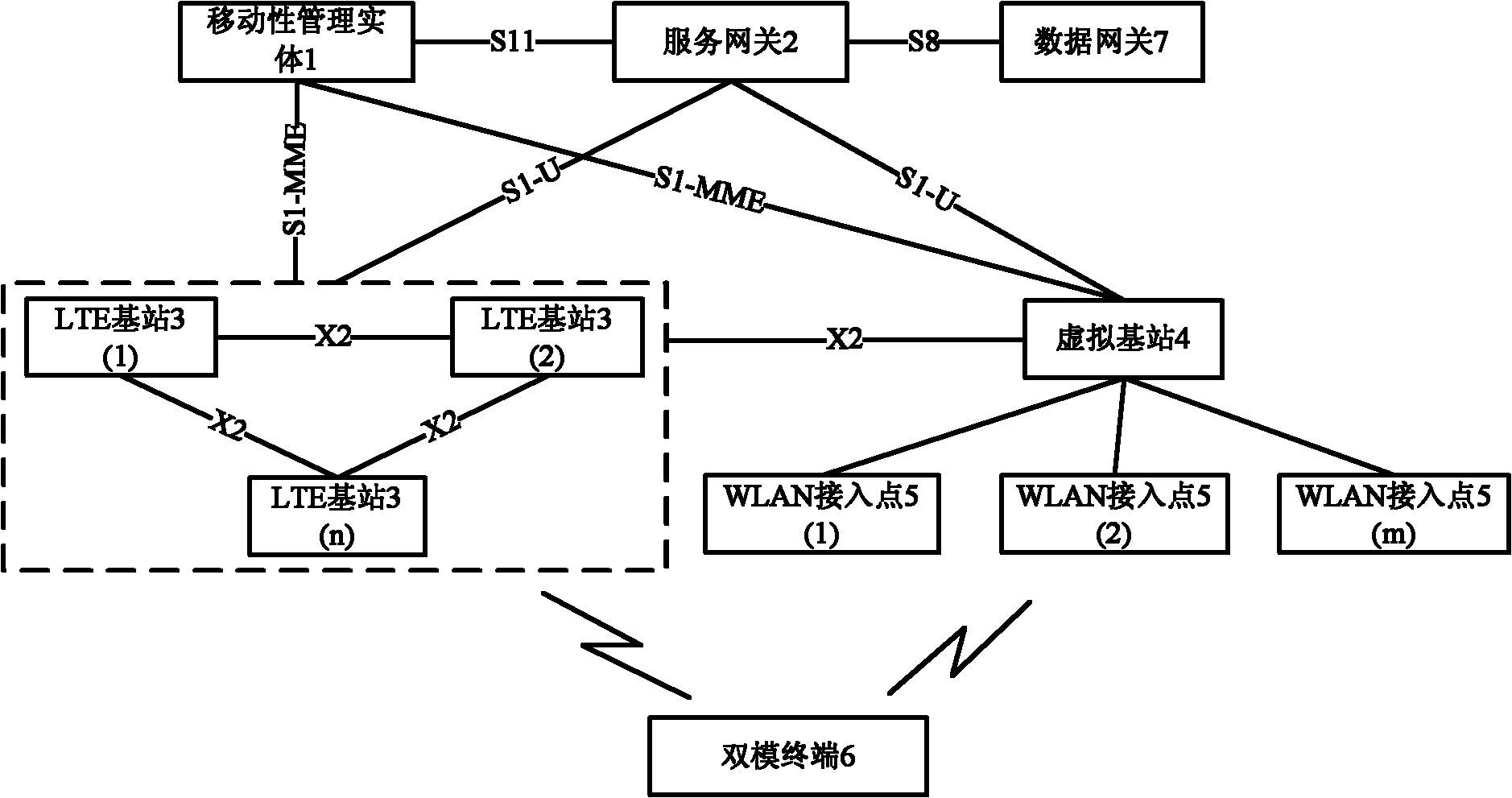
LTE and WLAN interconnecting system and switching method
InactiveCN101841880AMeet business quality requirementsReduce latencyWireless communicationTime delaysCoupling
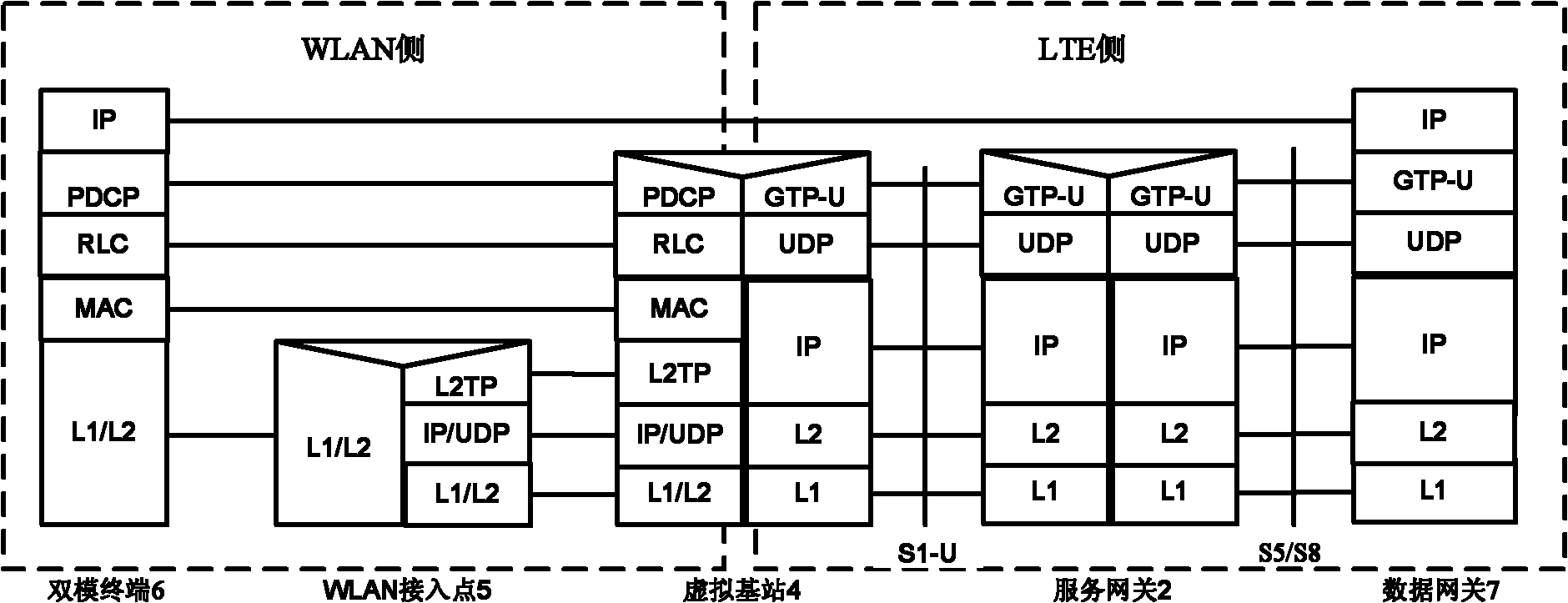
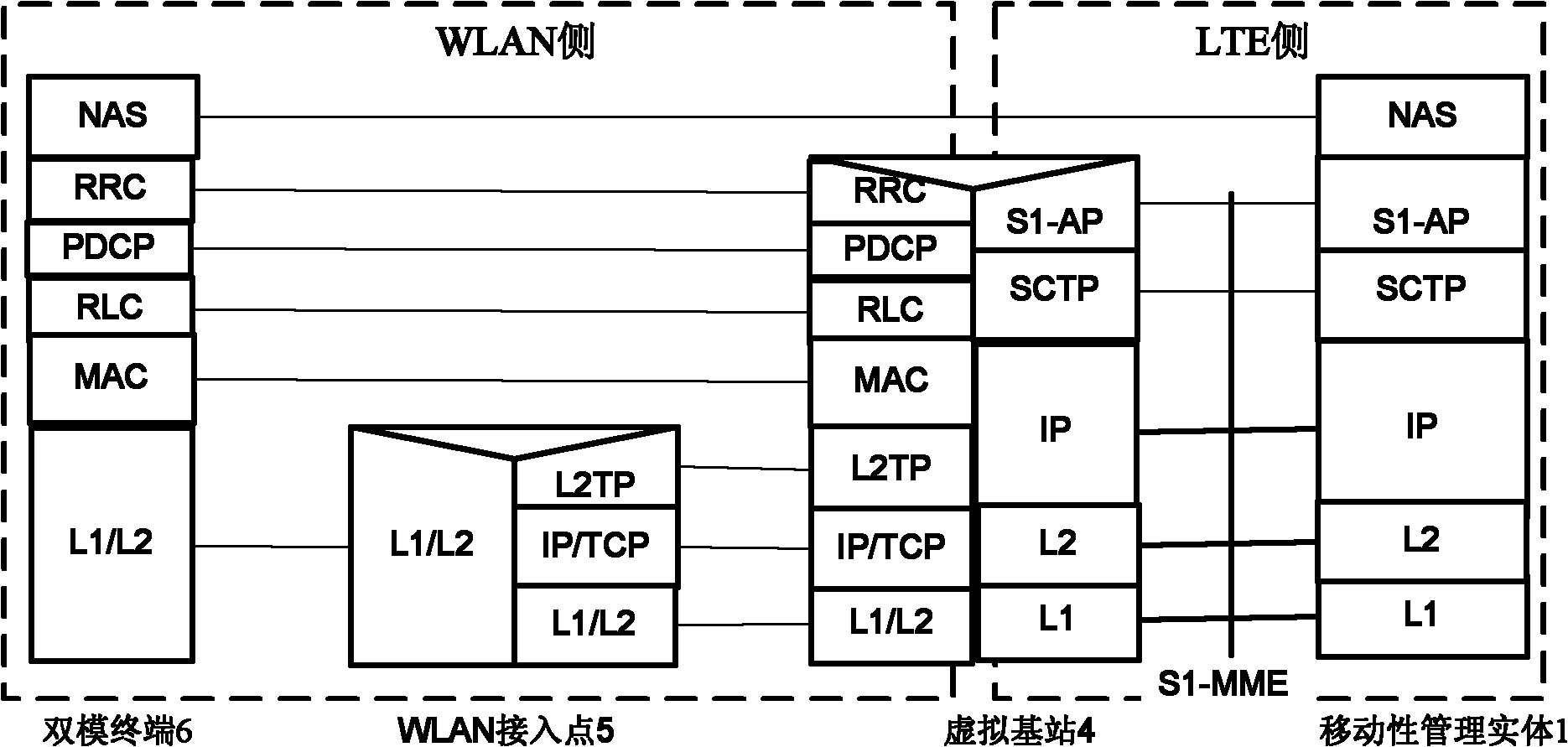
The invention provides an LTE and WLAN interconnecting system and a switching method; and the system introduces the entity of a virtual base station under an LTE architecture, and accesses the entity into the interface of the LTE as WLAN. On the LTE side, the virtual base station remains transparent relative to the LTE side, and is provided with the functions of a general LTE base station. On the WLAN side, the virtual base station can control the WLAN access point. The switching between the LTE and the WLAN is realized through the virtual base station through a standard X2 interface. A second layer tunneling protocol or an Ethernet tunneling protocol is adopted between the virtual base station and the WLAN access point to realize the transmission and the receiving of data and signaling during the switching process, and the WLAN serves as the bottom layered transmission channel of the data and the signaling of an LTE system. The method has the advantage that for the LTE, the switching process is kept consistent with the LTE switching process, which has very small impact on the traditional LTE. The WLAN is connected with the LTE in a tight coupling way, thereby greatly meeting the business requirement requirements, reducing the time delay caused by system switching, and ensuring the system performance.
Owner:HUAZHONG UNIV OF SCI & TECH
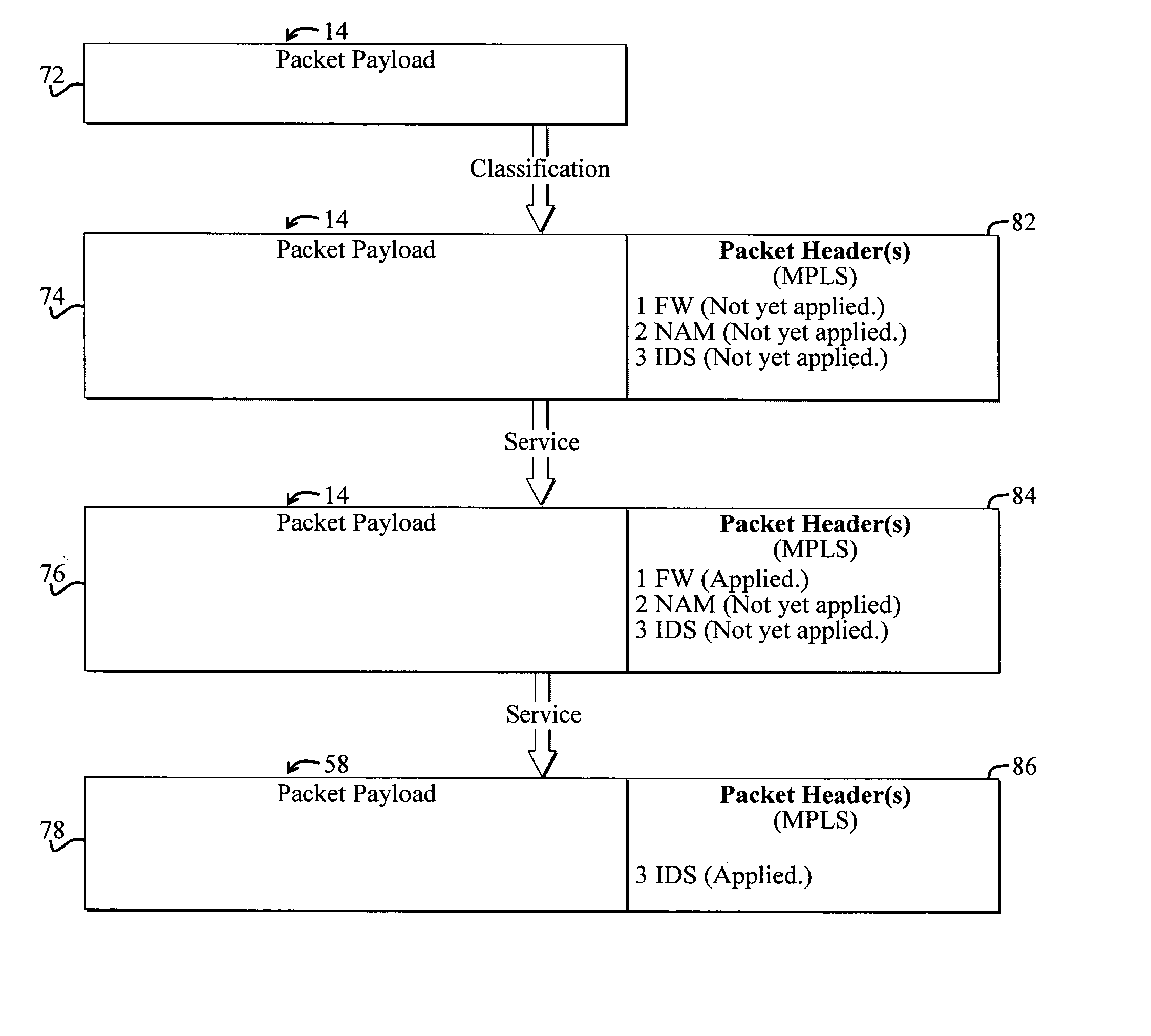
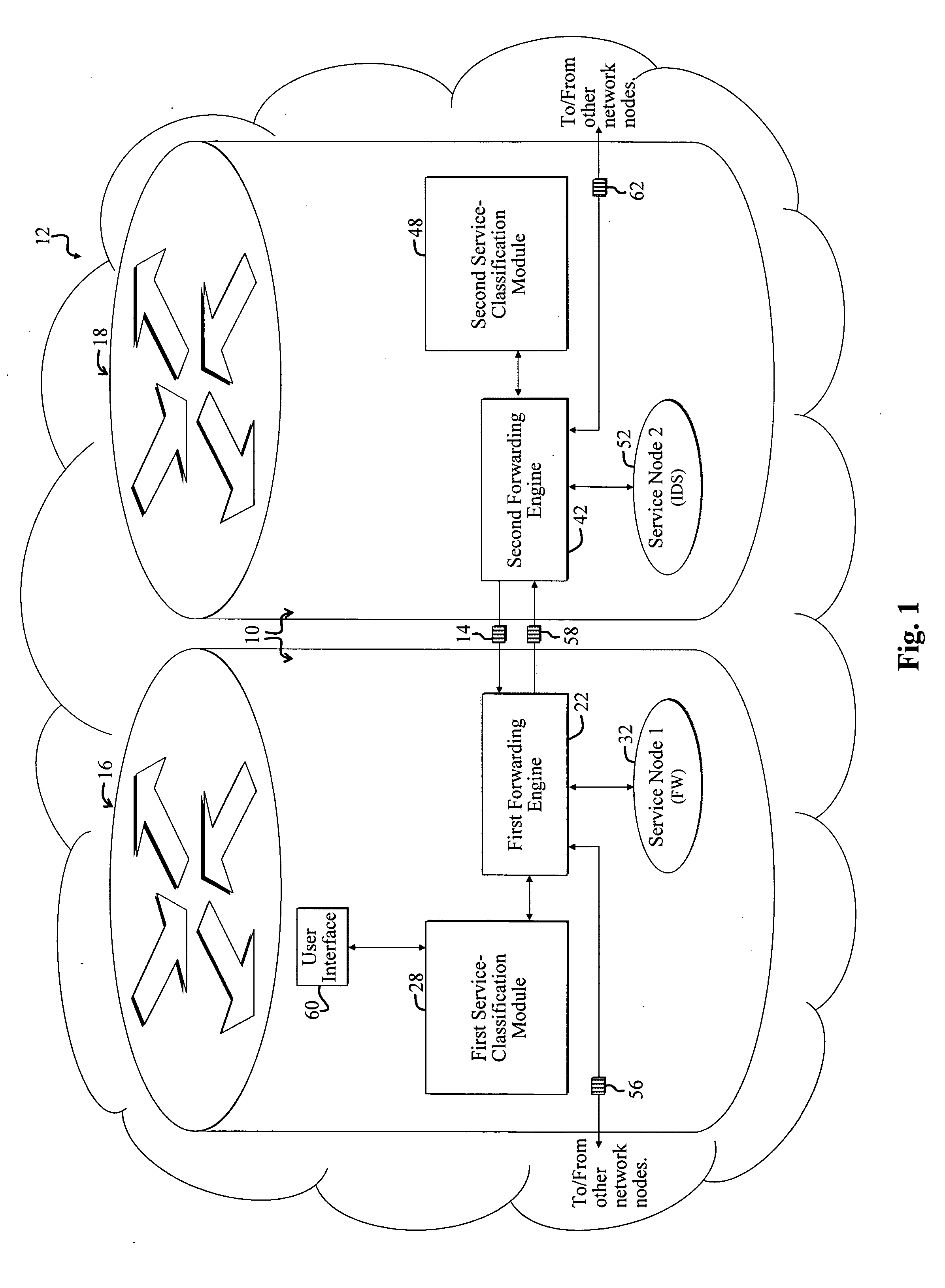
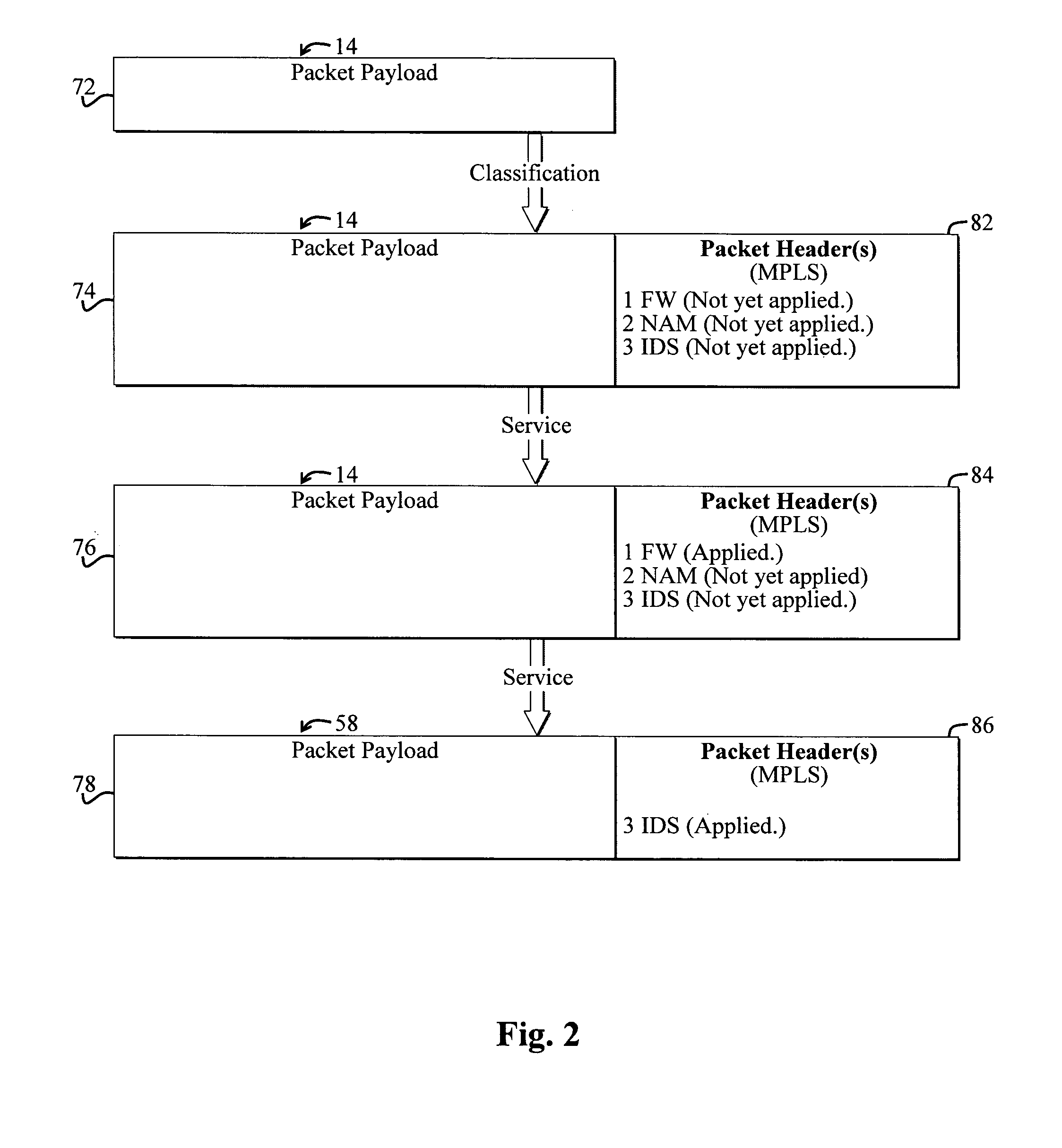
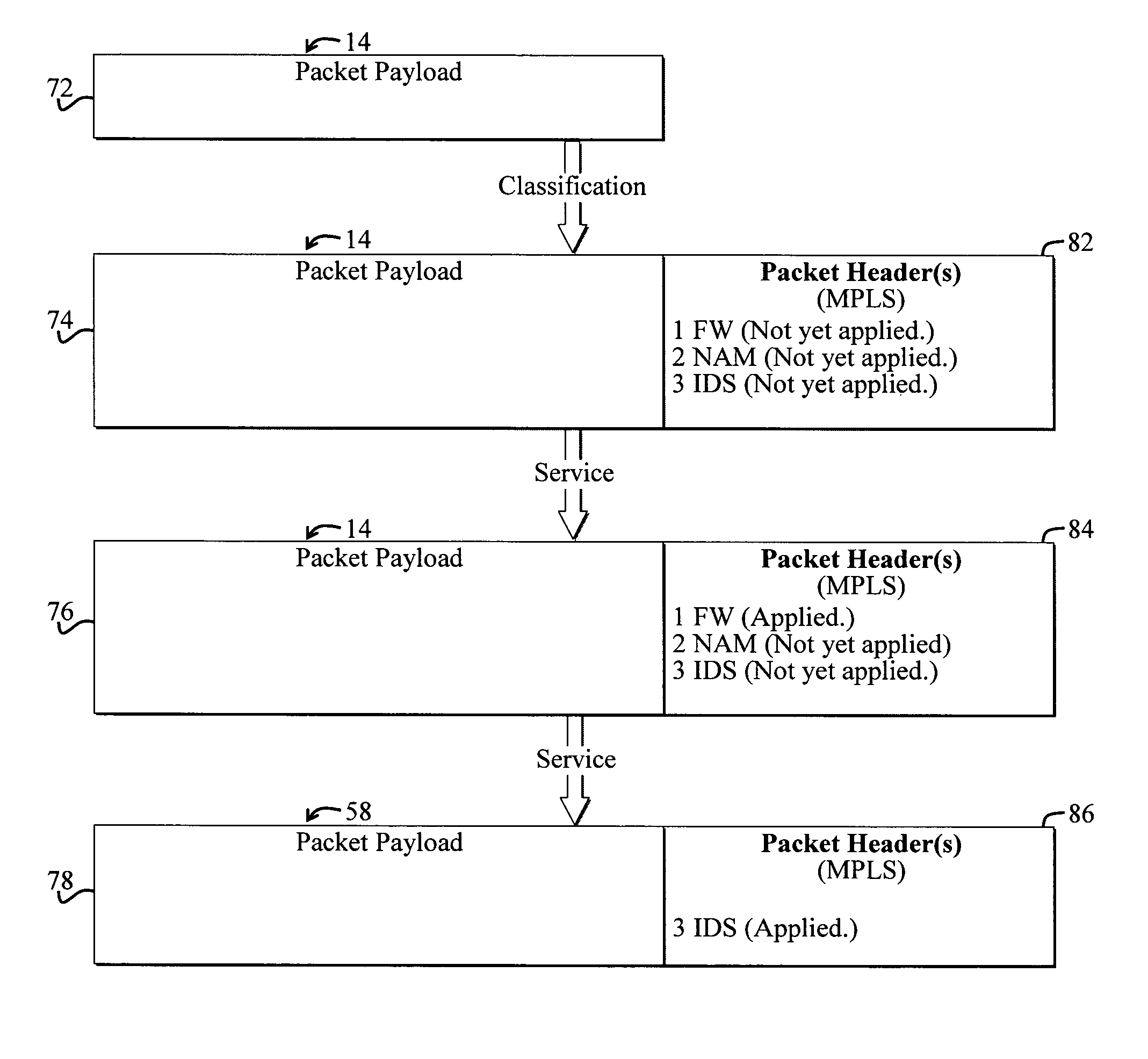
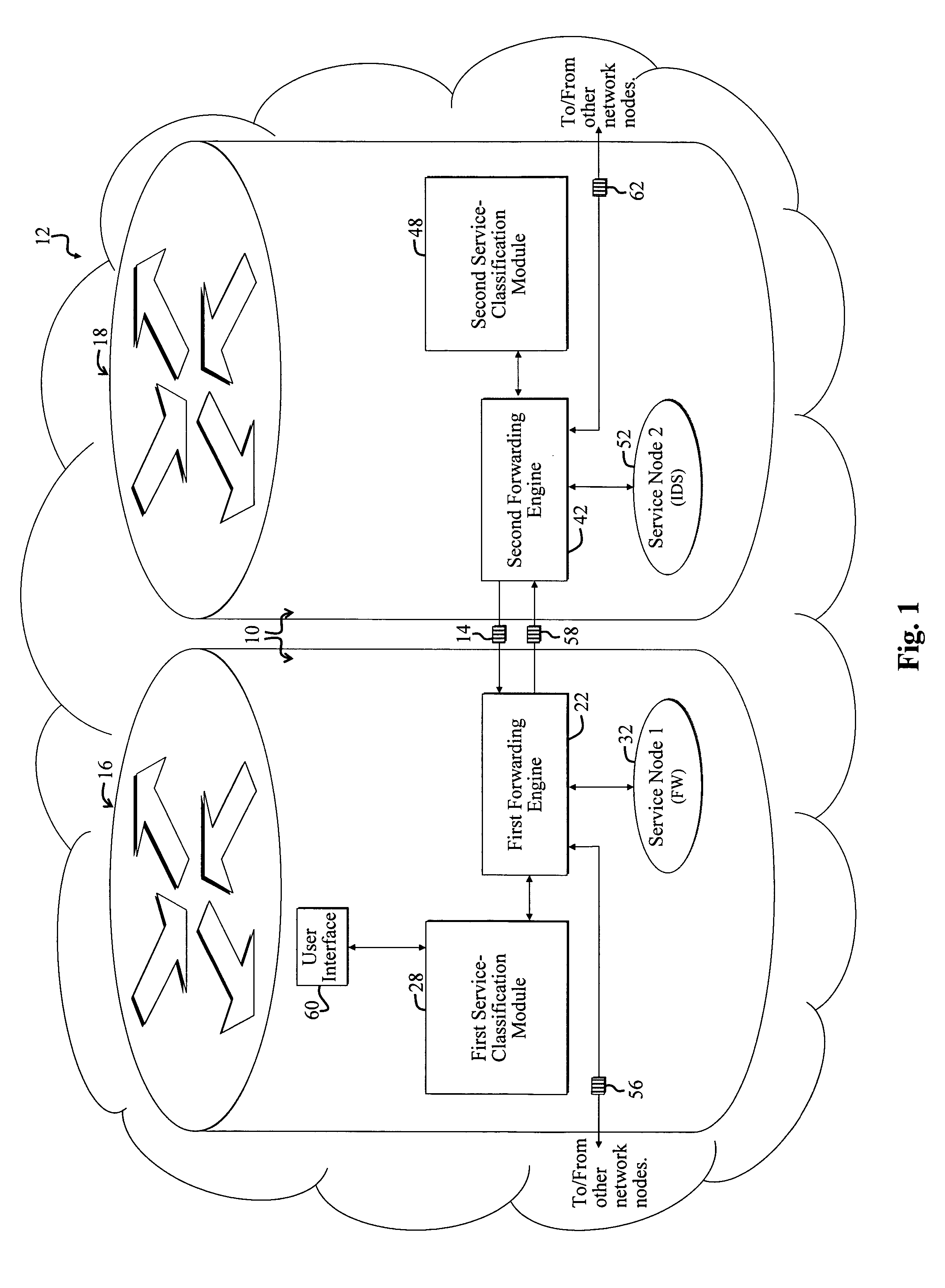
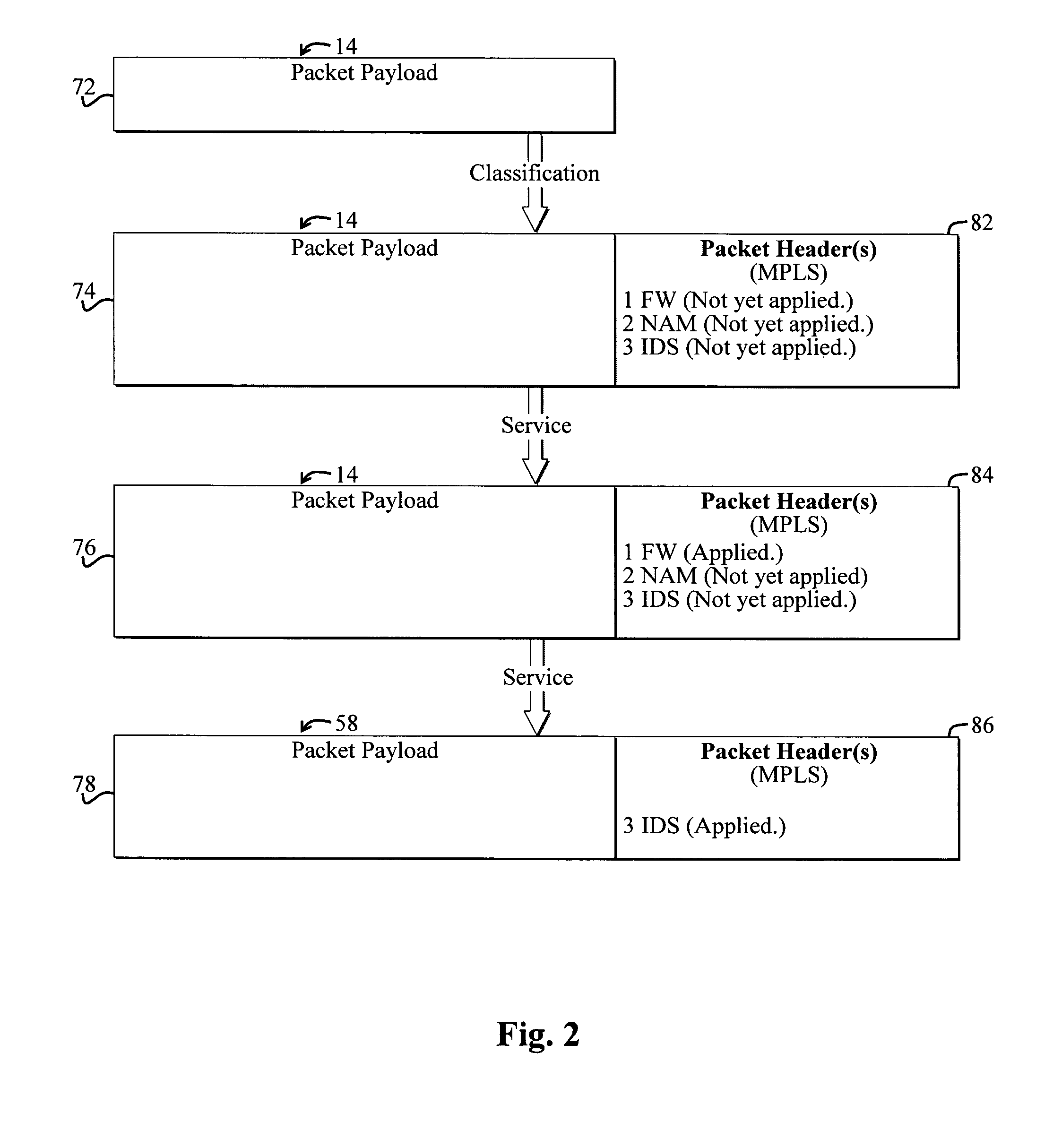
System and method for selectively applying a service to a network packet using a preexisting packet header
A system for selectively applying a service to a packet in a network. In a specific embodiment, the system includes a mechanism for encoding service information in a network-compatible packet header and providing encoded data in response thereto. In a more specific embodiment, the network-compatible header includes a Multi-Protocol Label Switching (MPLS) header, a Generic Route Encapsulation (GRE) header, and / or a Layer-2 Tunneling Protocol (L2TP) header.
Owner:CISCO TECH INC
System and method for selectively applying a service to a network packet using a preexisting packet header
ActiveUS8311045B2Time-division multiplexData switching by path configurationNetwork packetMulti protocol
Owner:CISCO TECH INC
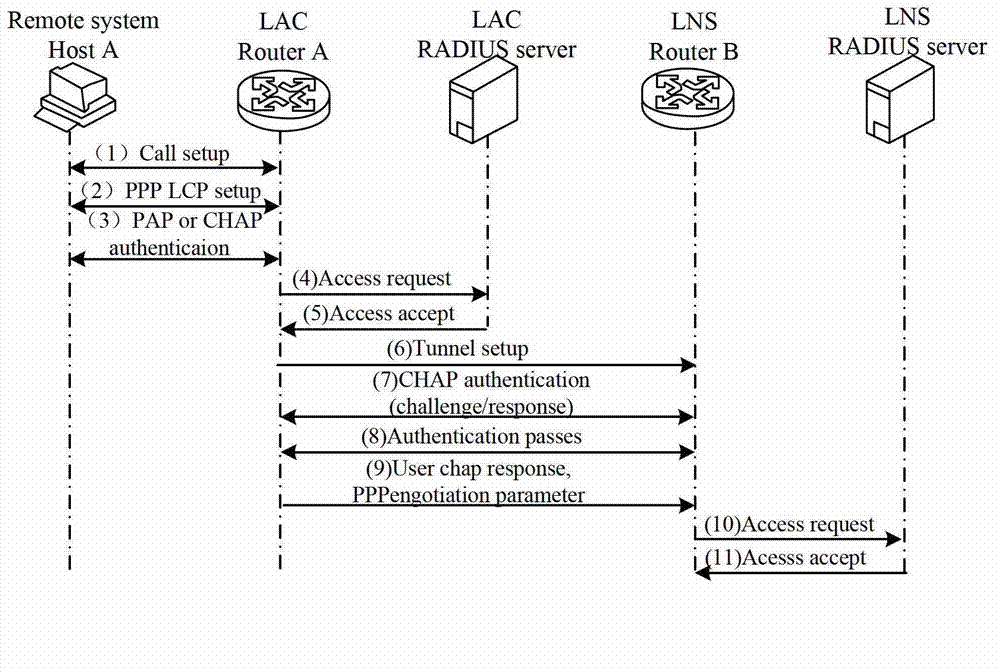
System and method for providing end to end authentication in a network environment
ActiveUS7024687B2Improve securityEffectively closedError preventionTransmission systemsGeneral Packet Radio ServiceNetwork service
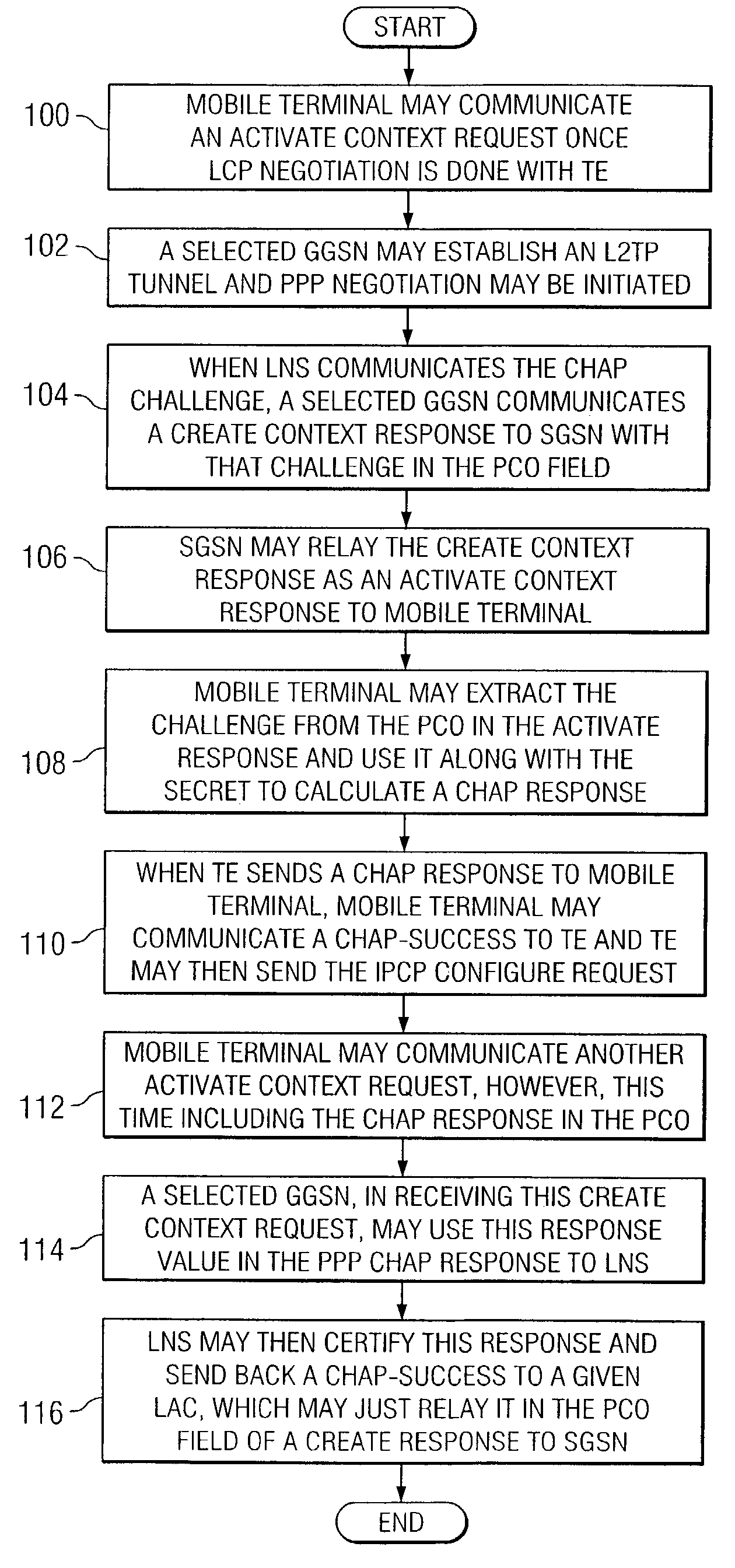
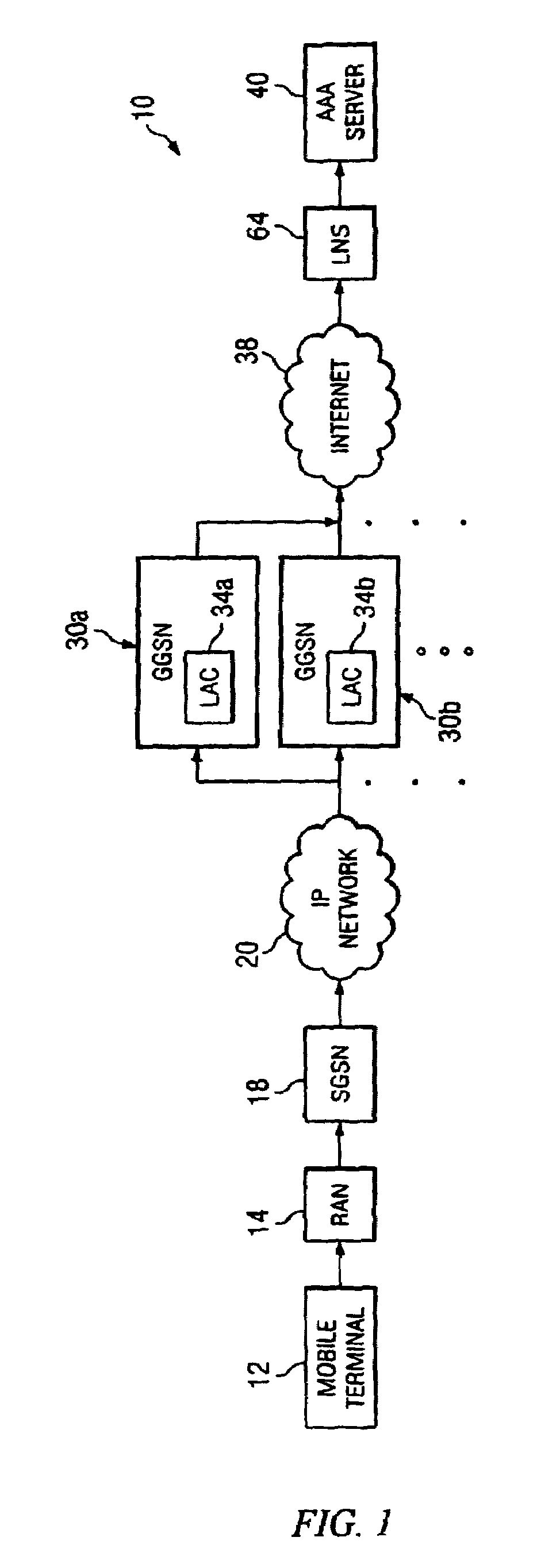
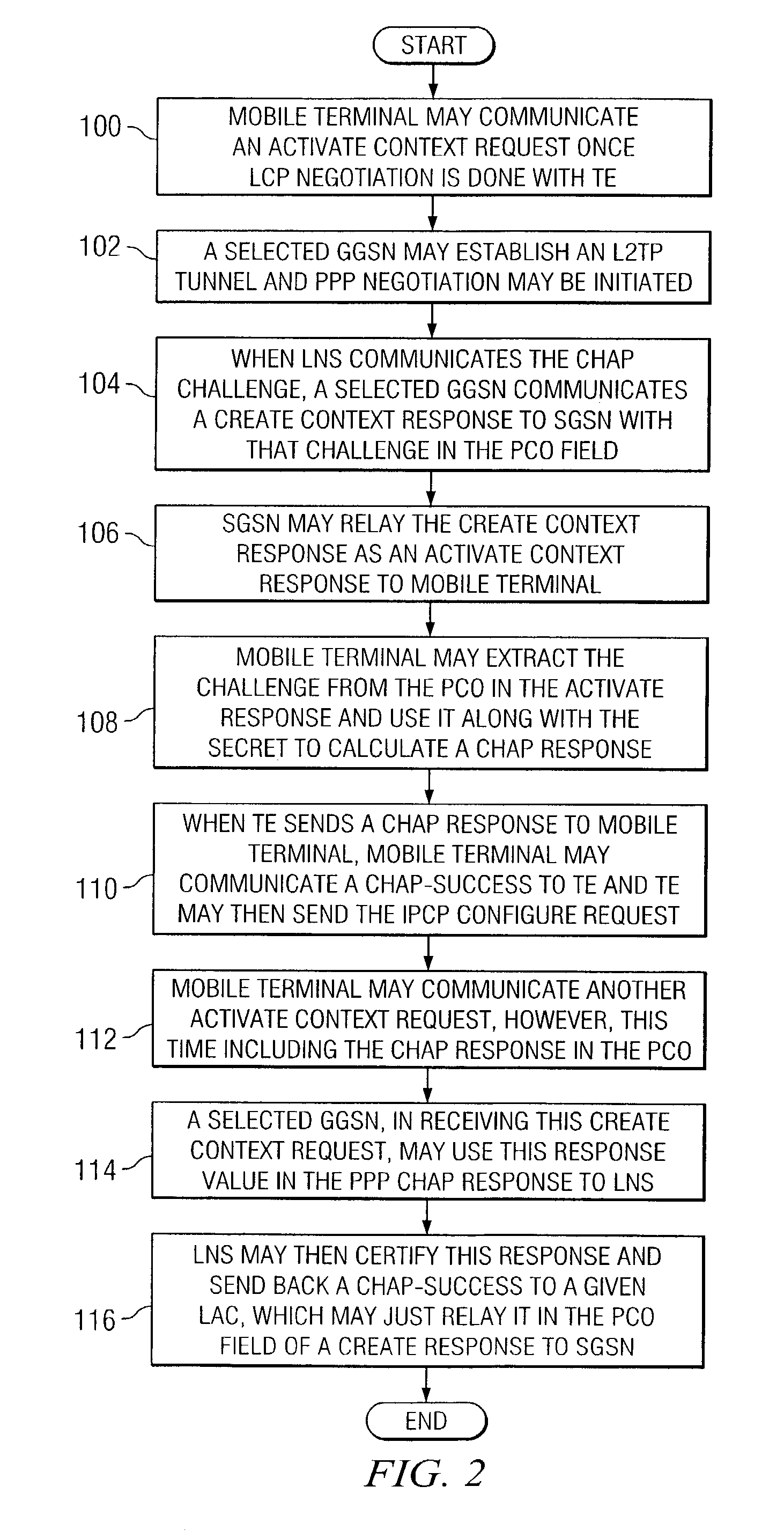
A method for executing end to end authentication in a network environment is provided that includes initiating a communications tunnel with a layer two tunnel protocol (L2TP) network server (LNS) and communicating an activate context request that includes an authentication protocol in a protocol configuration option (PCO) field, the activate context request being received by a gateway general packet radio service (GPRS) support node (GGSN) that initiates a link control protocol (LCP) negotiation with the LNS, the GGSN being operable to communicate an activate context response that may be received by the mobile terminal. An authentication response may be calculated by using a secret value and a challenge value which is provided by the GGSN, the authentication response being used to establish a communication session associated with the mobile terminal.
Owner:CISCO TECH INC
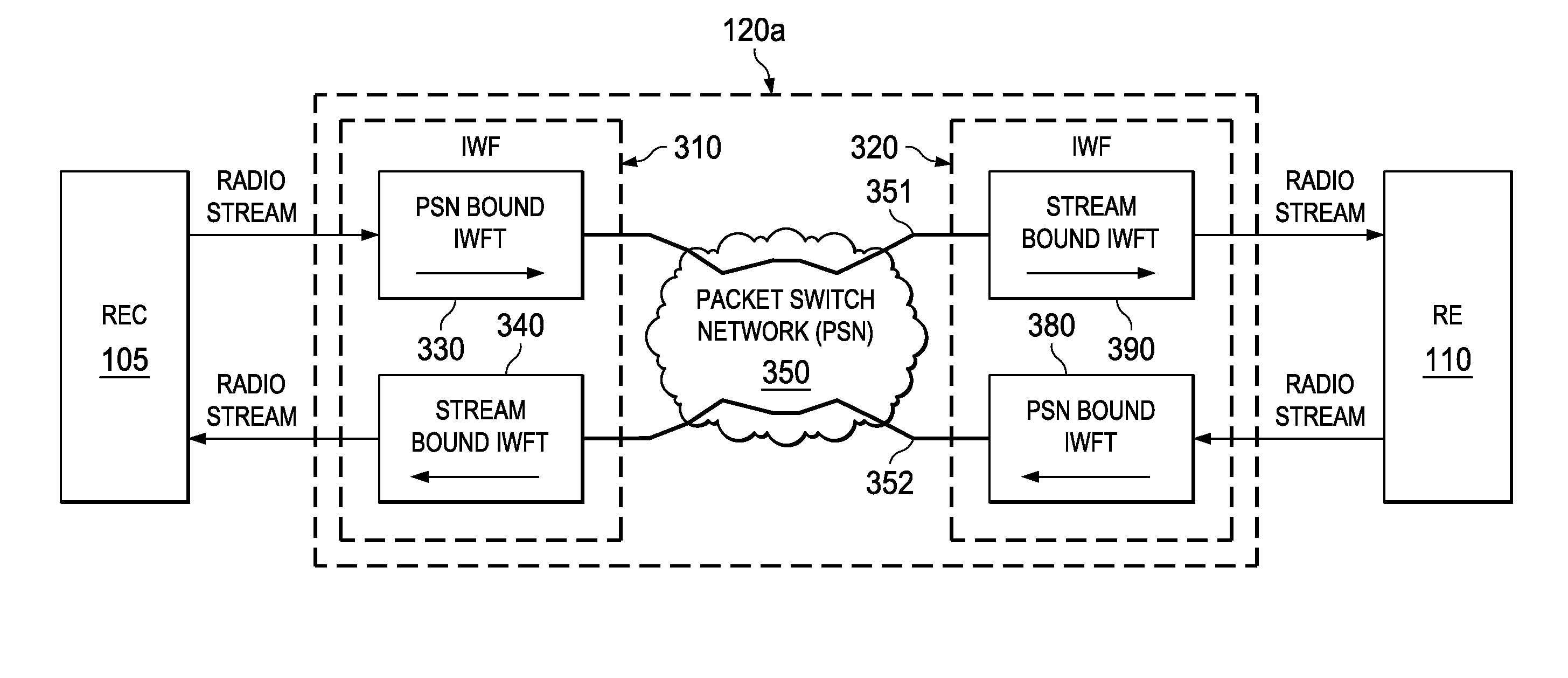
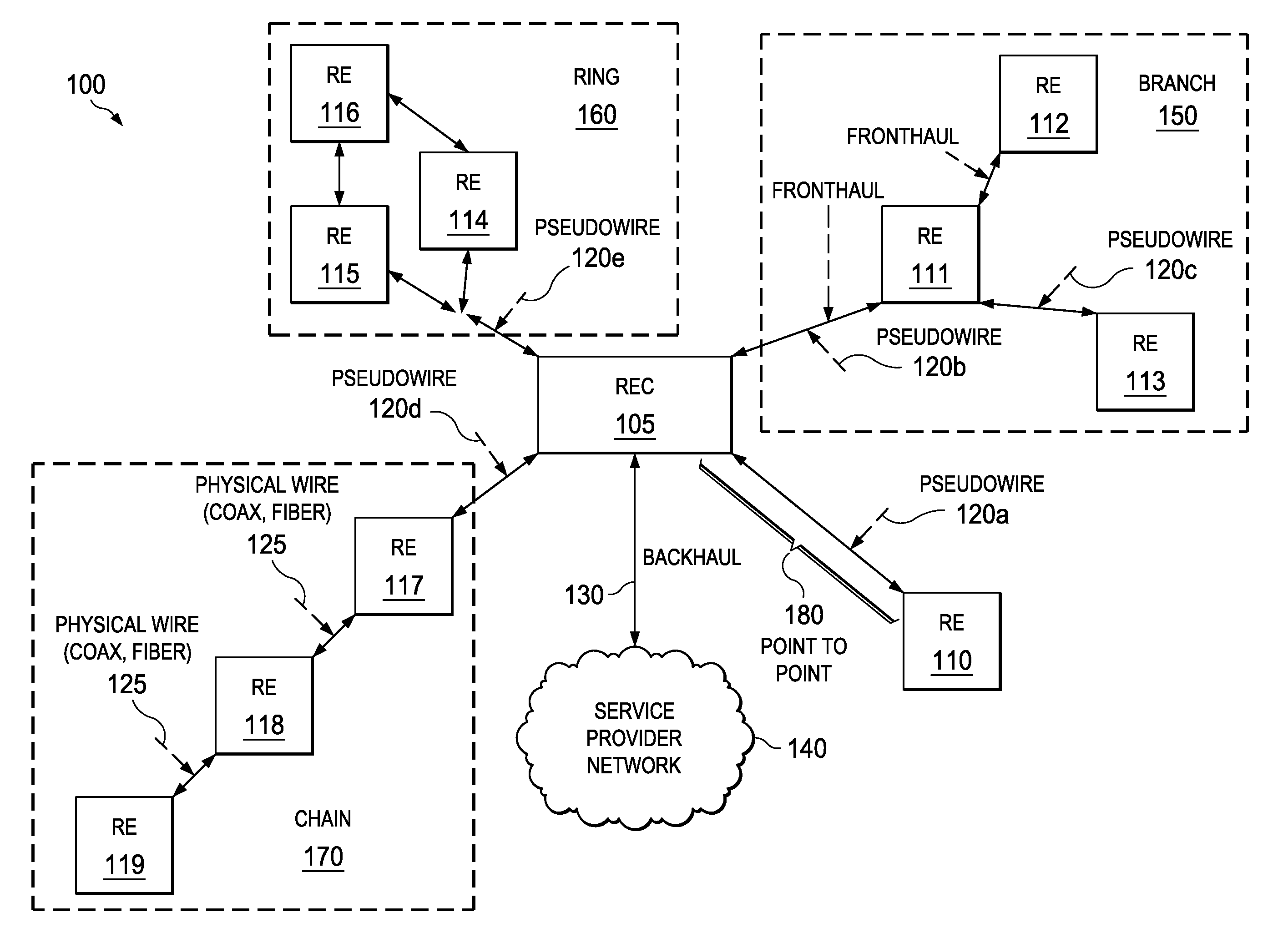
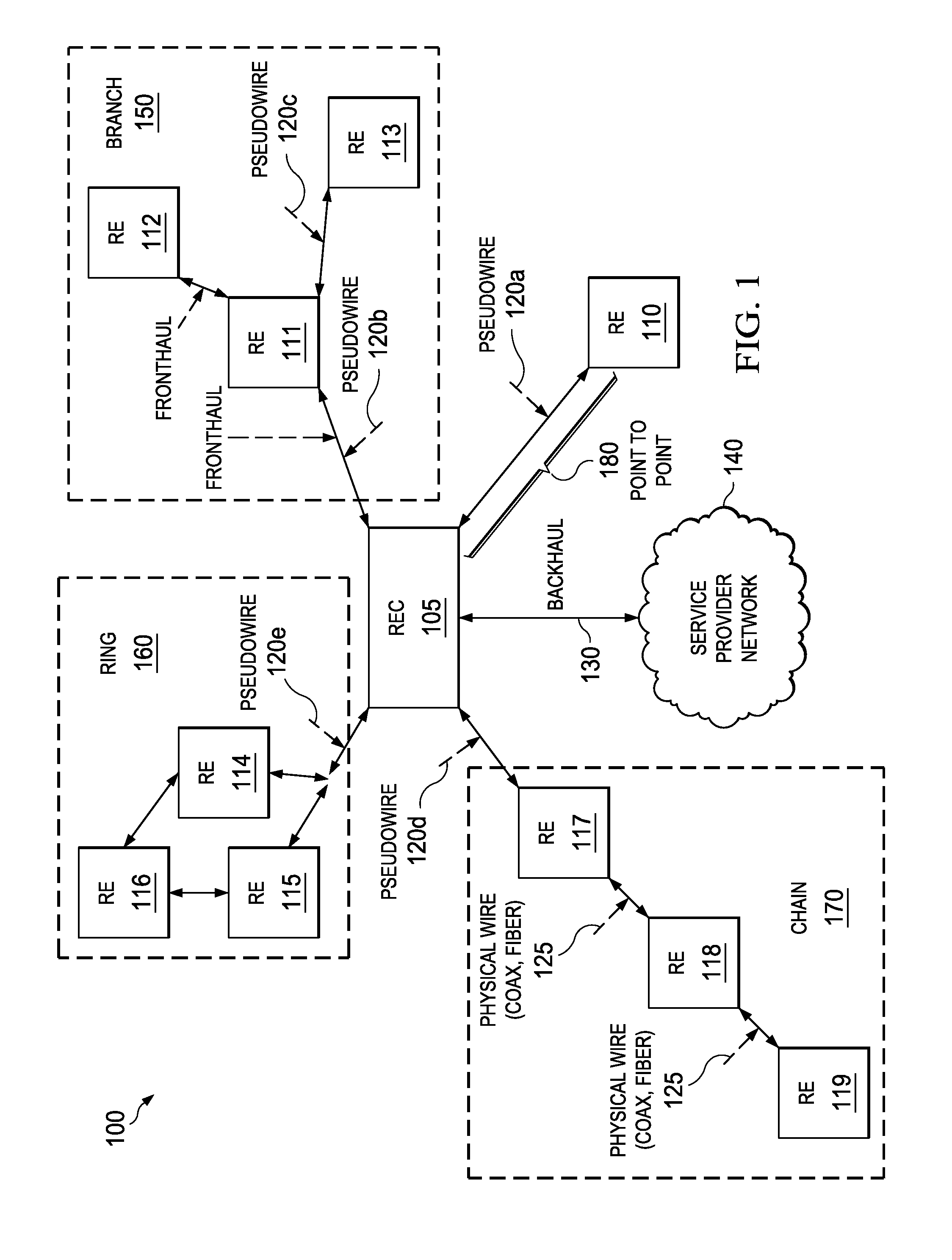
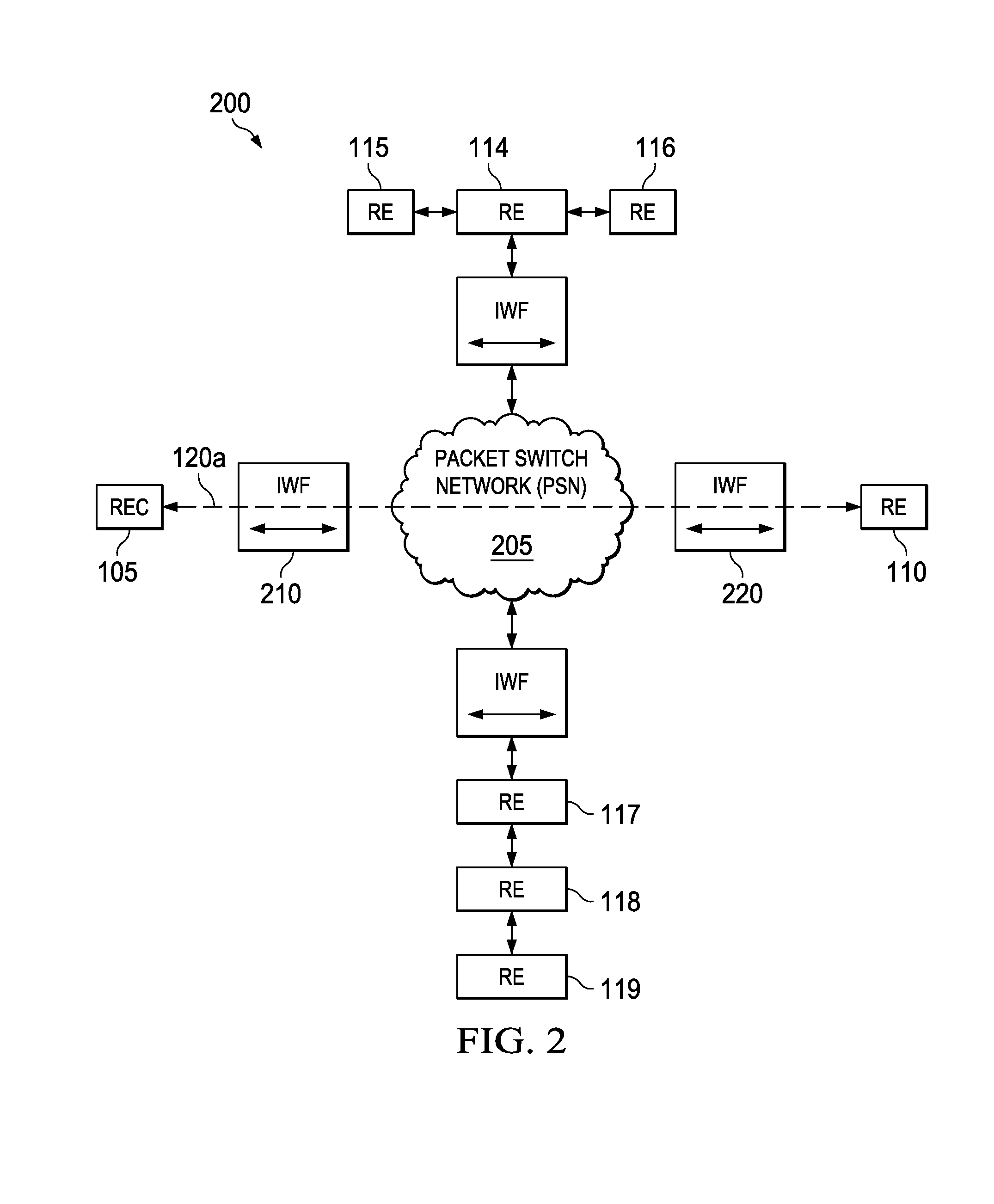
System and method for transporting digital baseband streams in a network environment
ActiveUS20130329633A1Time-division multiplexWireless commuication servicesApplication programming interfaceMulti protocol
A method is provided in example embodiments that include receiving a radio signal stream and segmenting the radio signal stream into segments. The segments may be packetized and transported in packets over a pseudowire in a packet-switched network. The radio signal stream can be reconstructed from the segments. In more particular embodiments, the pseudowire may be a multi-protocol label switching pseudowire or a layer 2 tunneling protocol pseudowire, for example. In yet other specific example embodiments, the radio signal stream may be received using a common public radio interface or a femtocell application programming interface.
Owner:CISCO TECH INC
Network-based dedicated backup service
InactiveUS20060092955A1Time-division multiplexData switching by path configurationPoint-to-Point ProtocolPrivate network
A system and method for providing alternate dedicated connections are described. A primary dedicated connection may be configured to connect a first network and a second network, and a second dedicated network-based connection, which may include a point-to-point protocol (PPP) / layer 2 tunneling protocol (L2TP) tunnel, may be configured to automatically connect the first network and the second network when the primary dedicated connection fails.
Owner:VERIZON PATENT & LICENSING INC
Method and apparatus for providing a VPN service according to a packet data protocol in a wireless communication system
InactiveUS20050201388A1Reduce constraintsConnection managementData switching by path configurationPoint-to-Point ProtocolCommunications system
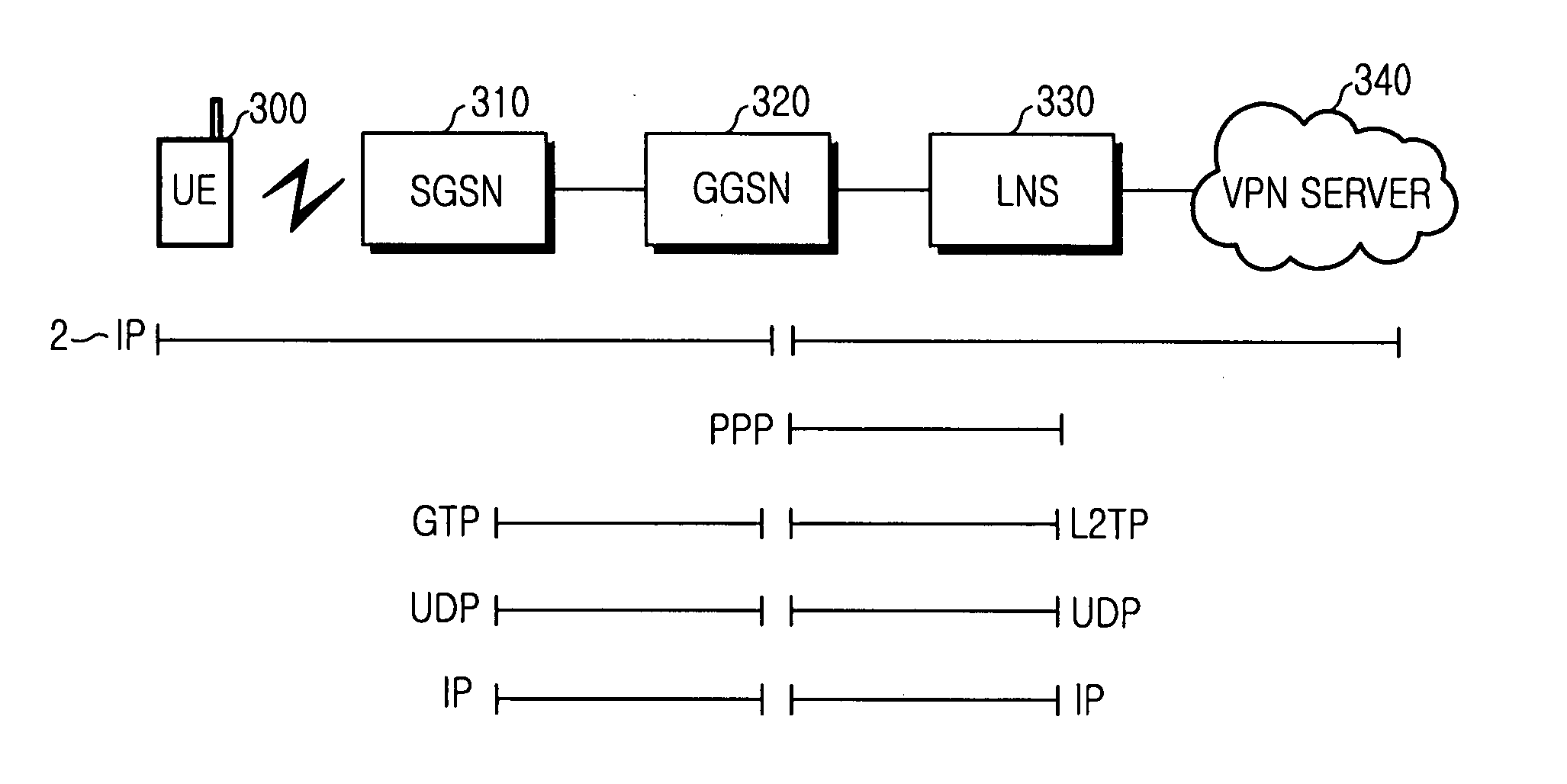
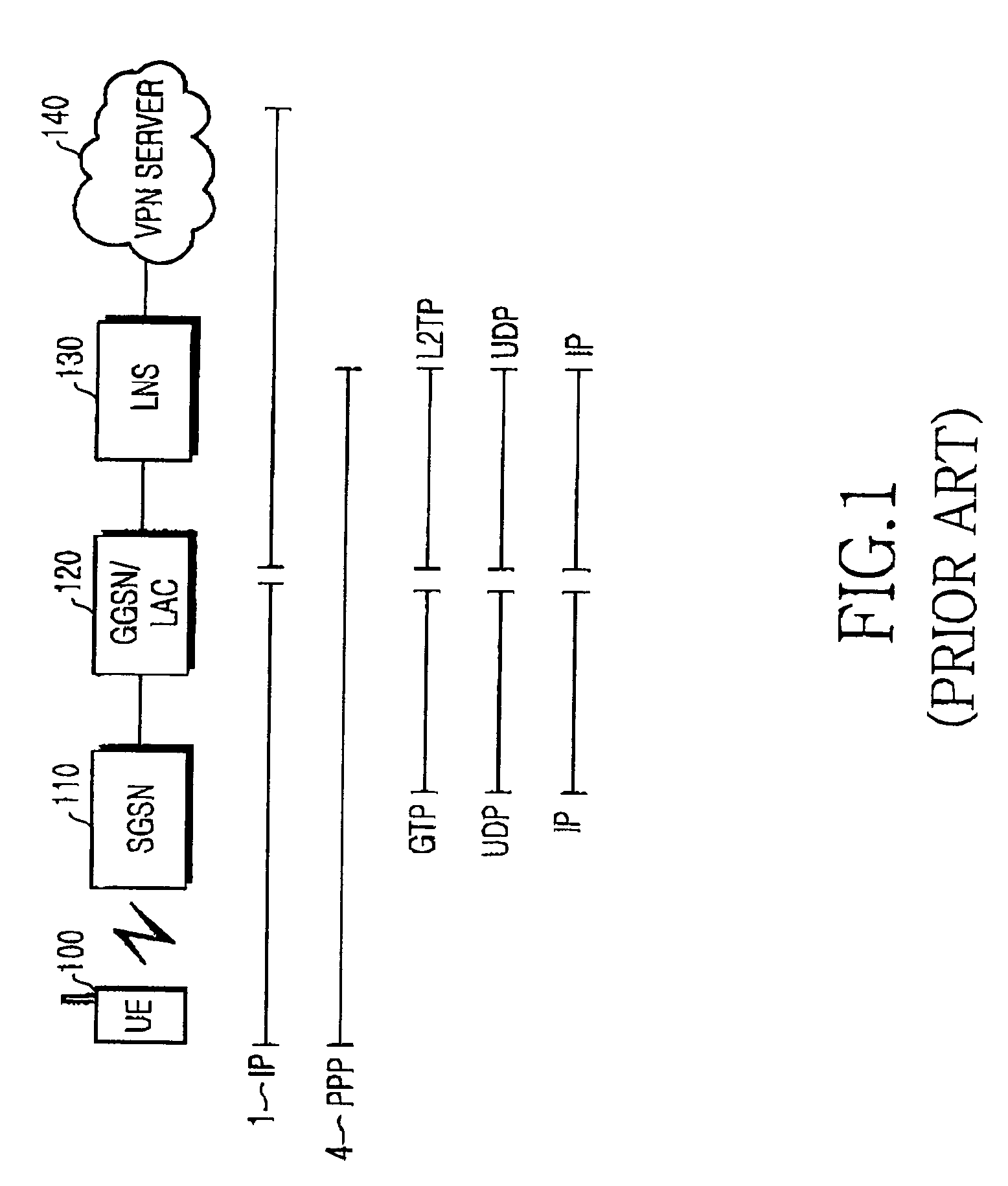
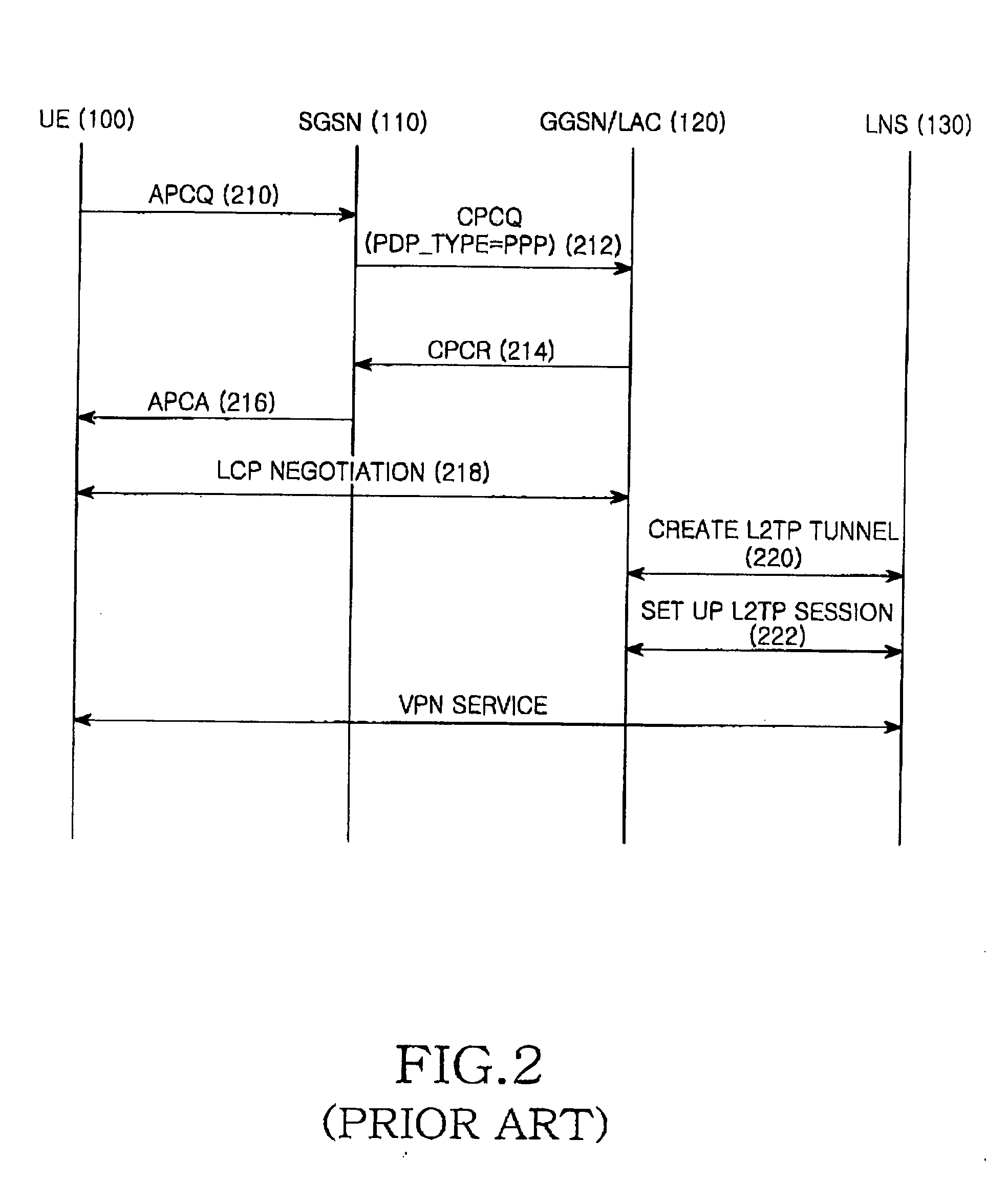
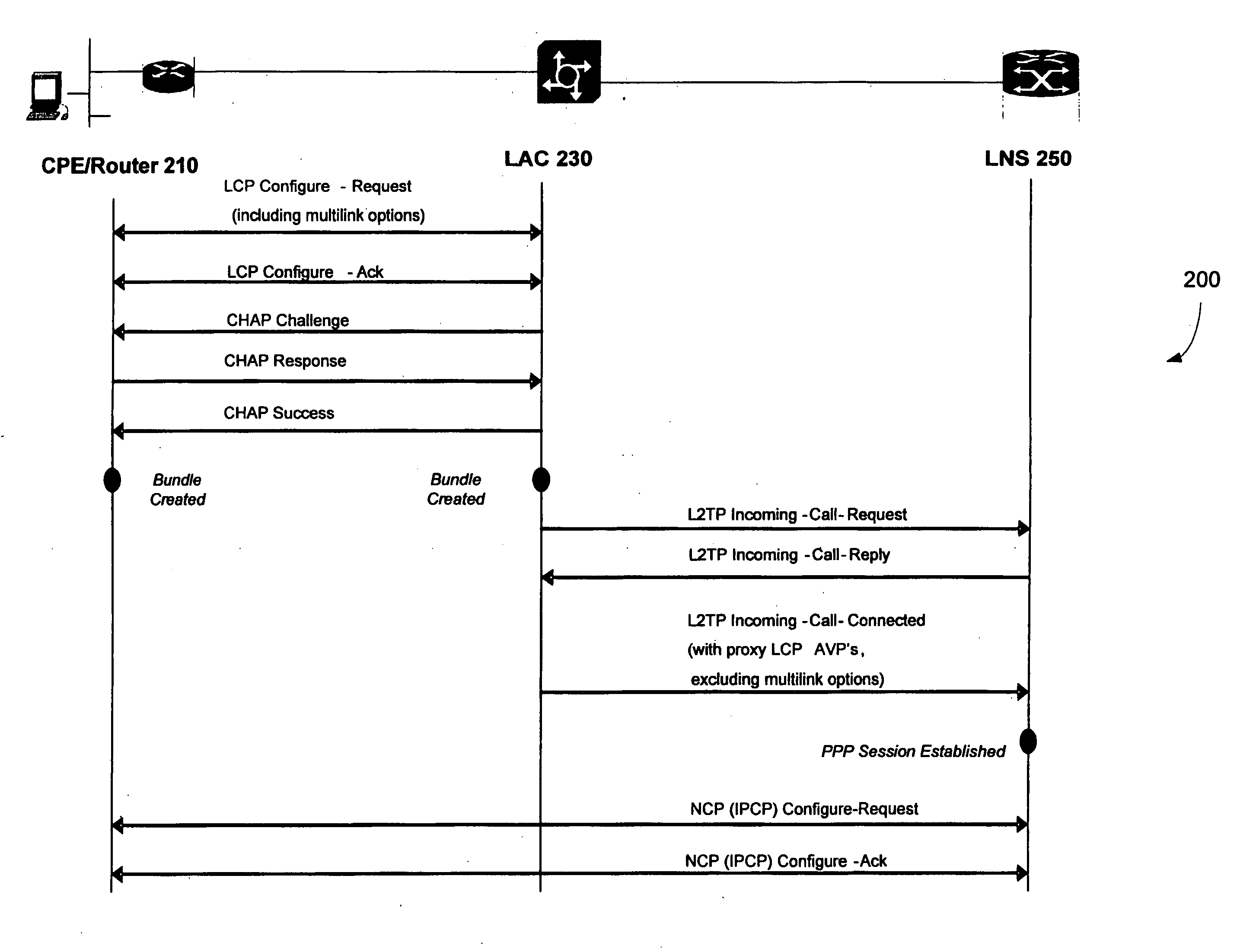
A method and apparatus for providing a Virtual Private Network (VPN) service to a user equipment (UE) according to the Packet Data Protocol (PDP) type of call are provided. In the VPN service providing method, a Gateway GPRS Support Nodes (GGSN) receives a create PDP connection request message from a Serving GPRS Support Nodes (SGSN), for the VPN service of the UE, initializes a Point-to-Point Protocol (PPP) session if the call is an IP call, creates a layer 2 tunneling protocol (L2TP) tunnel with a layer 2 tunneling protocol (L2TP) network server (LNS), sets up a session, sets up a PPP connection with the LNS, and transmits a create PDP context response message to the service node, after the PPP connection.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for combining fixed network and mobile network
InactiveCN102457444AAchieve fixationNetworks interconnectionNetwork connectionsPoint-to-Point ProtocolBridge pattern
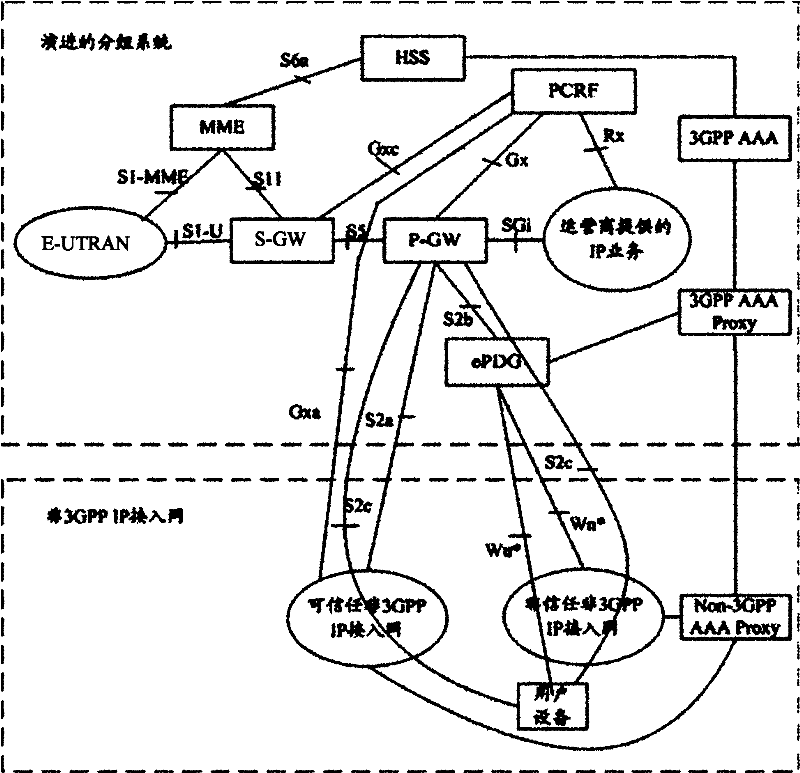
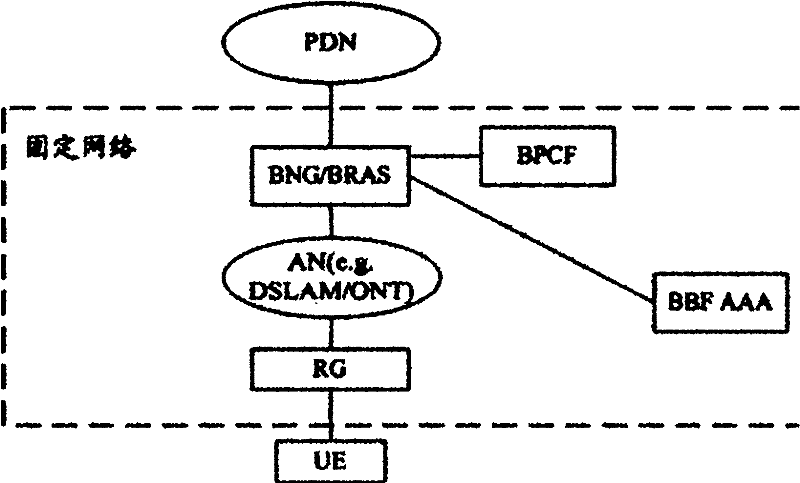
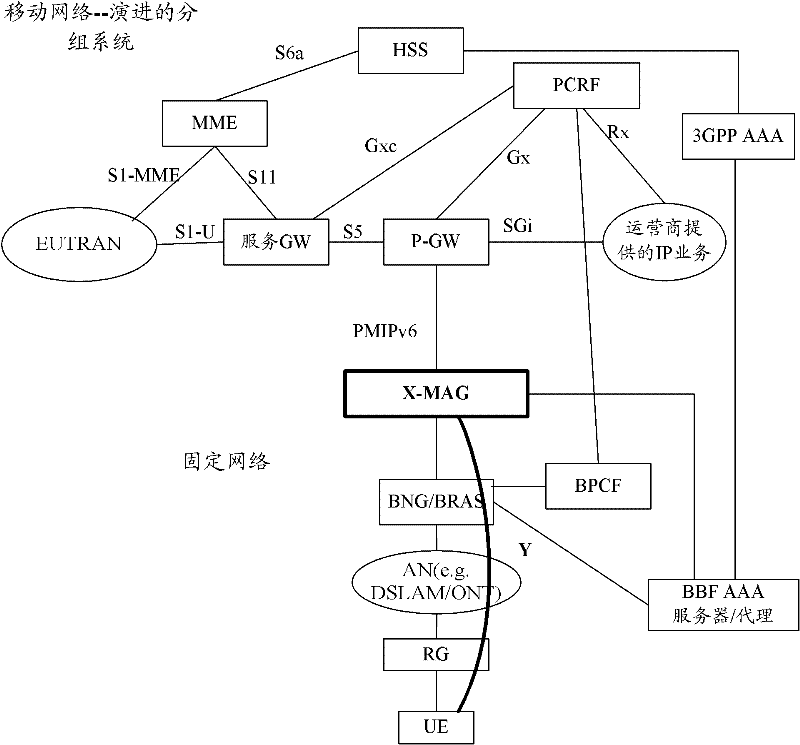
The invention discloses a system and a method for combining a fixed network and a mobile network. The system is characterized in that: aiming at the fixed network in a bridge pattern, an X-mobile anchor gateway (X-MAG) used for realizing trusted non 3rd generation partnership project (3GPP) access is arranged and connected between the fixed network and the mobile network, a Ya interface is arranged between user equipment (UE) and a broadband network gateway / broadband remote access server (BNG / BRAS), and a Yb interface is arranged between the BNG / BRAS and the X-MAG, so the UE can access an evolved packet system (EPS) of the mobile network by the fixed network in the bridge pattern through the X-MAG in a trusted non 3GPP IP access way; and aiming at the fixed network in a route pattern, a point-to-point protocol (PPP) signaling is borne by supporting the use of a layer 2 tunneling protocol (L2TP) on a terminal and the X-MAG based on the conventional framework. By the system and the method, the UE can realize the trusted non 3GPP access in a simple and feasible way, namely the UE can access the mobile network through the fixed network in the bridge pattern or the route pattern, and the combination between the fixed network and the mobile network is realized.
Owner:ZTE CORP
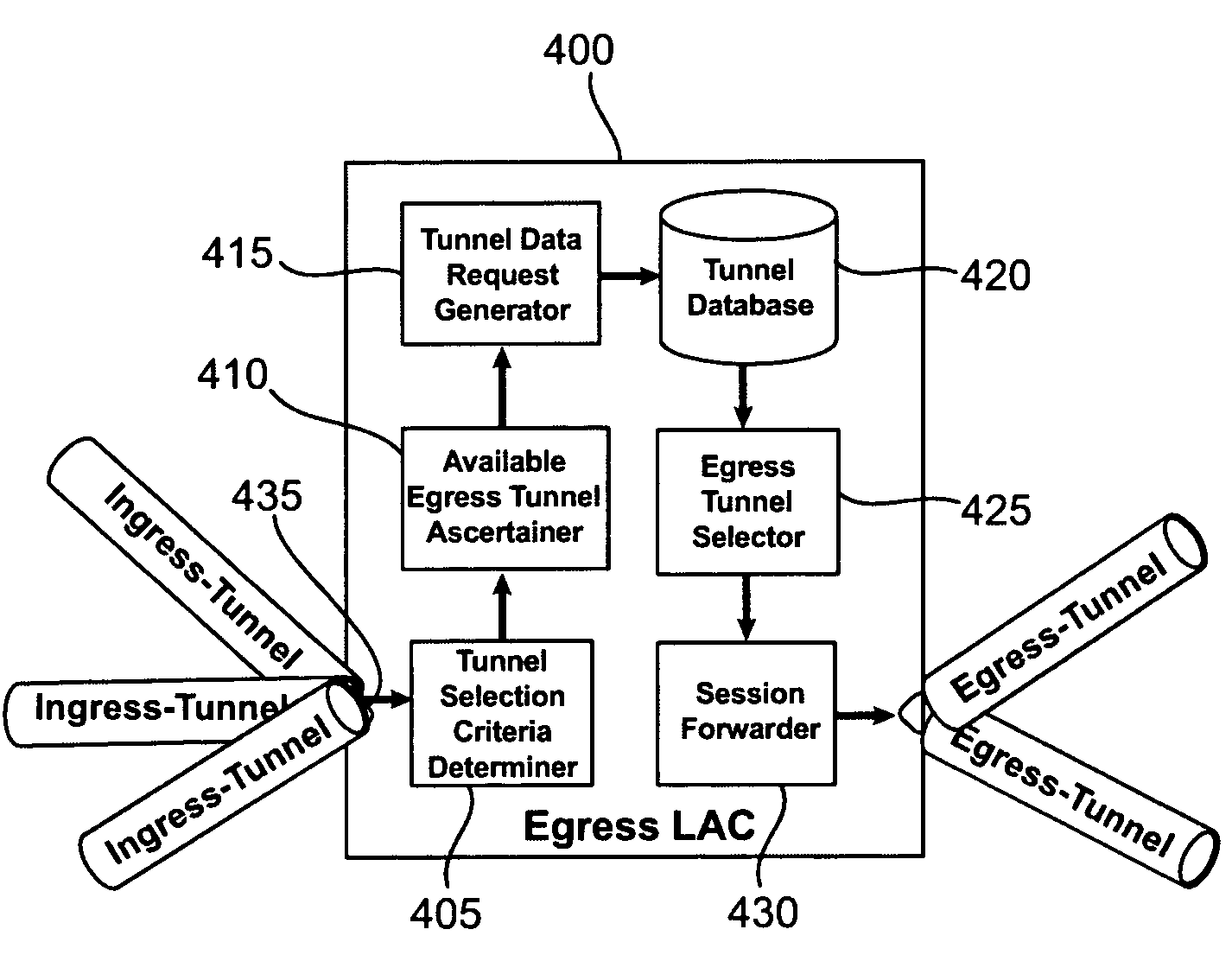
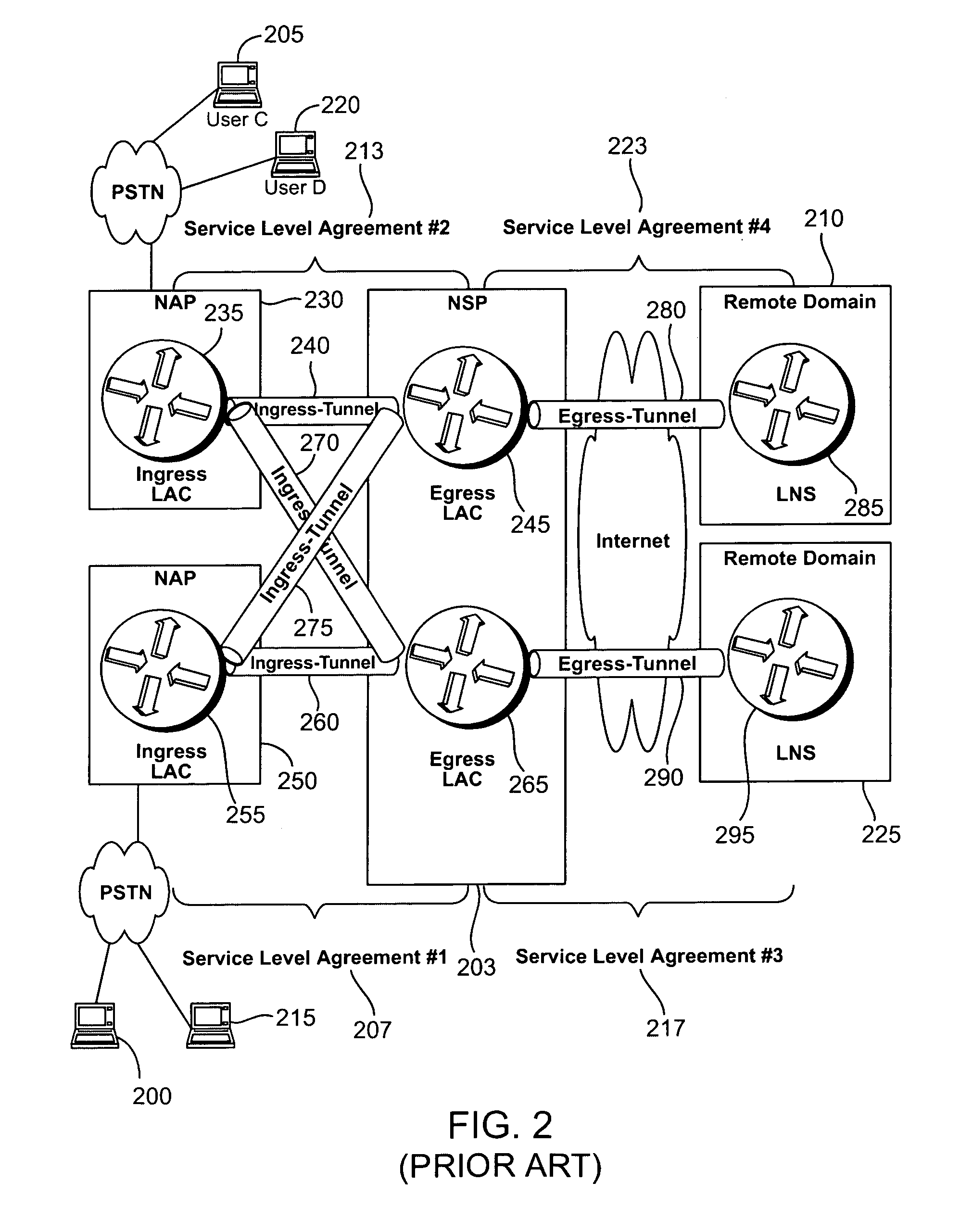
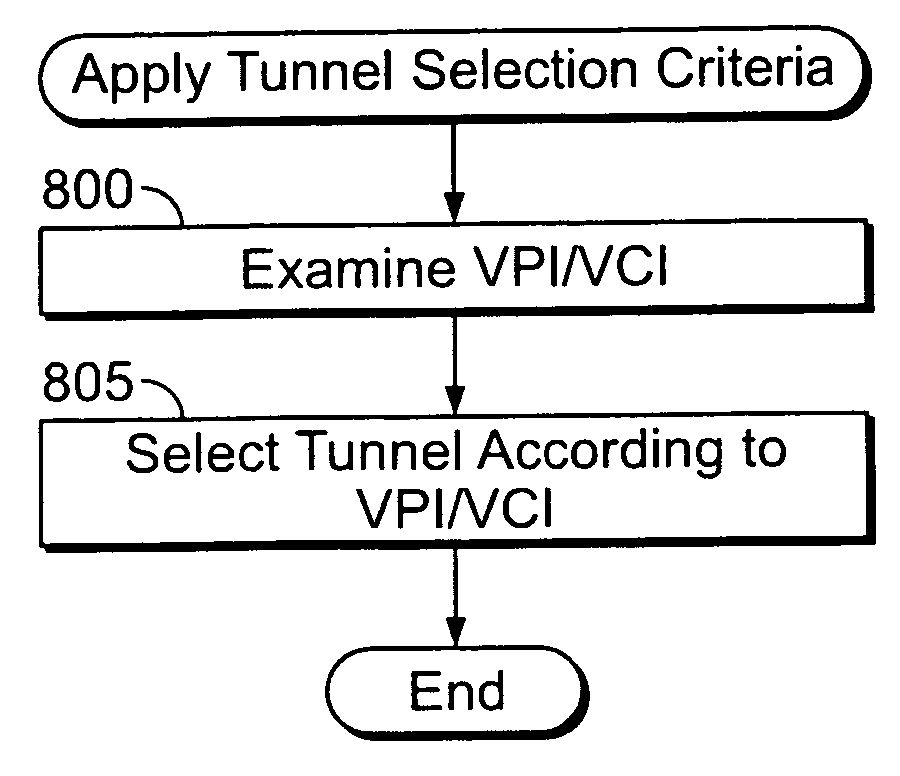
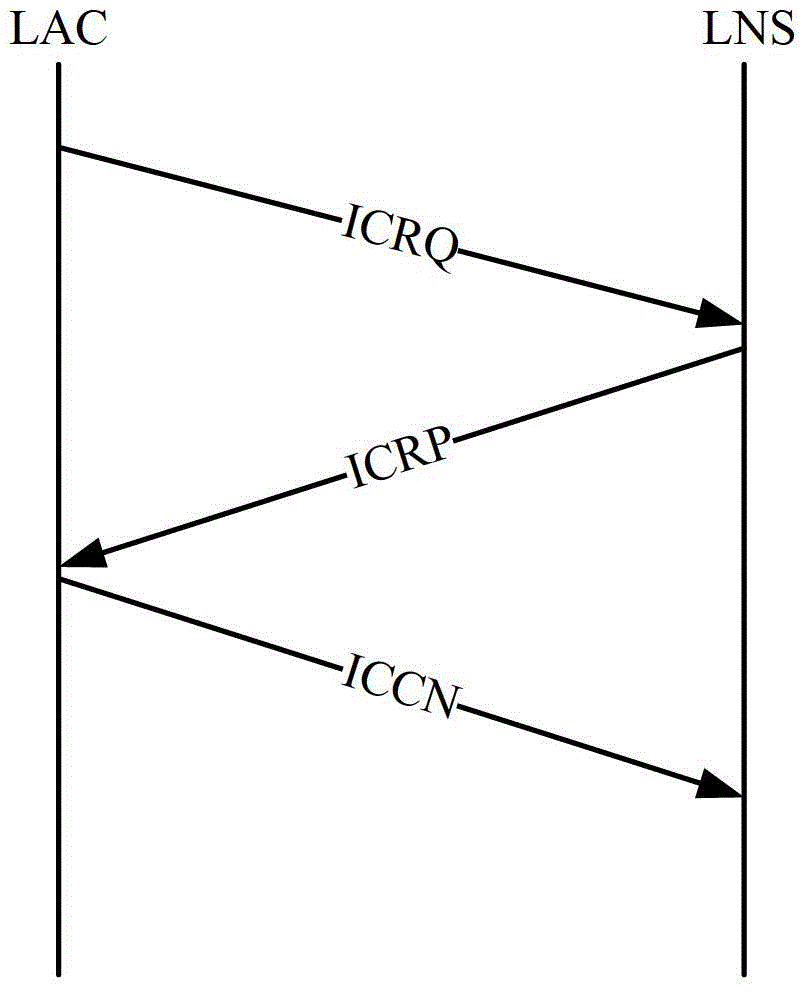
Dynamic multi-hop ingress to egress L2TP tunnel mapping
InactiveUS7023879B1Time-division multiplexData switching networksTelecommunicationsSelection criterion
A method for dynamic ingress to egress tunnel mapping from a first communication network to a second communication network includes receiving a tunneled communication from a subscriber using the first communication network, determining egress tunnel selection criteria for the tunneled communication, selecting one of at least one egress tunnel based on the egress tunnel selection criteria and forwarding the tunneled communication on the selected egress tunnel. The egress tunnel selection criteria indicate the basis for selecting one of the egress tunnels. An apparatus for dynamic ingress to egress tunnel mapping from a first communication network to a second communication network includes a receiving interface to receive a tunneled communication from a subscriber using the first communication network, an egress tunnel selection criteria determiner to determine egress tunnel selection criteria for the tunneled communication, an egress tunnel selector to select one of at least one egress tunnel based on the egress tunnel selection criteria and a session forwarder to forward the tunneled communication on the selected egress tunnel. In one aspect of the invention, tunnel mapping is performed between Layer 2 Tunneling Protocol (L2TP) ingress and egress tunnels.
Owner:CISCO TECH INC
Load sharing between L2TP tunnels
InactiveUS7139276B1Multiprogramming arrangementsData switching by path configurationTelecommunicationsSelection criterion
A method for load sharing between tunnels connecting communication networks includes receiving a communication from a subscriber using the first communication network, determining tunnel selection criteria for the communication, selecting one of the at least one tunnel based on the tunnel selection criteria and forwarding the communication on the selected tunnel. The tunnel selection criteria indicate the basis for selecting one of the tunnels. An apparatus for load sharing between tunnels connecting communication networks includes a receiving interface to receive a communication from a subscriber using the first communication network, a tunnel selection criteria determiner to determine tunnel selection criteria for the communication, a tunnel selector to select one of the tunnels based on the tunnel selection criteria and a session forwarder to forward the communication on the selected tunnel. In one aspect of the invention, load sharing is performed between Layer 2 Tunneling Protocol (L2TP) tunnels.
Owner:CISCO TECH INC
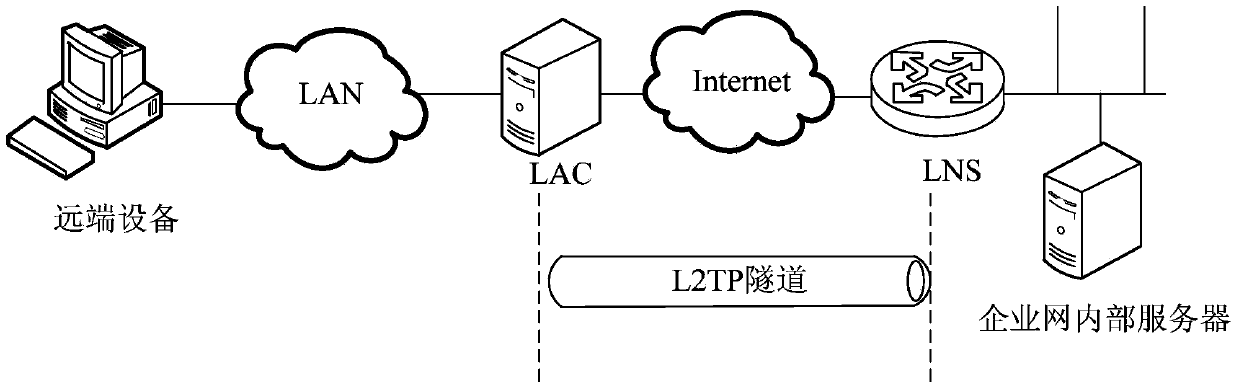
Message forwarding method and equipment
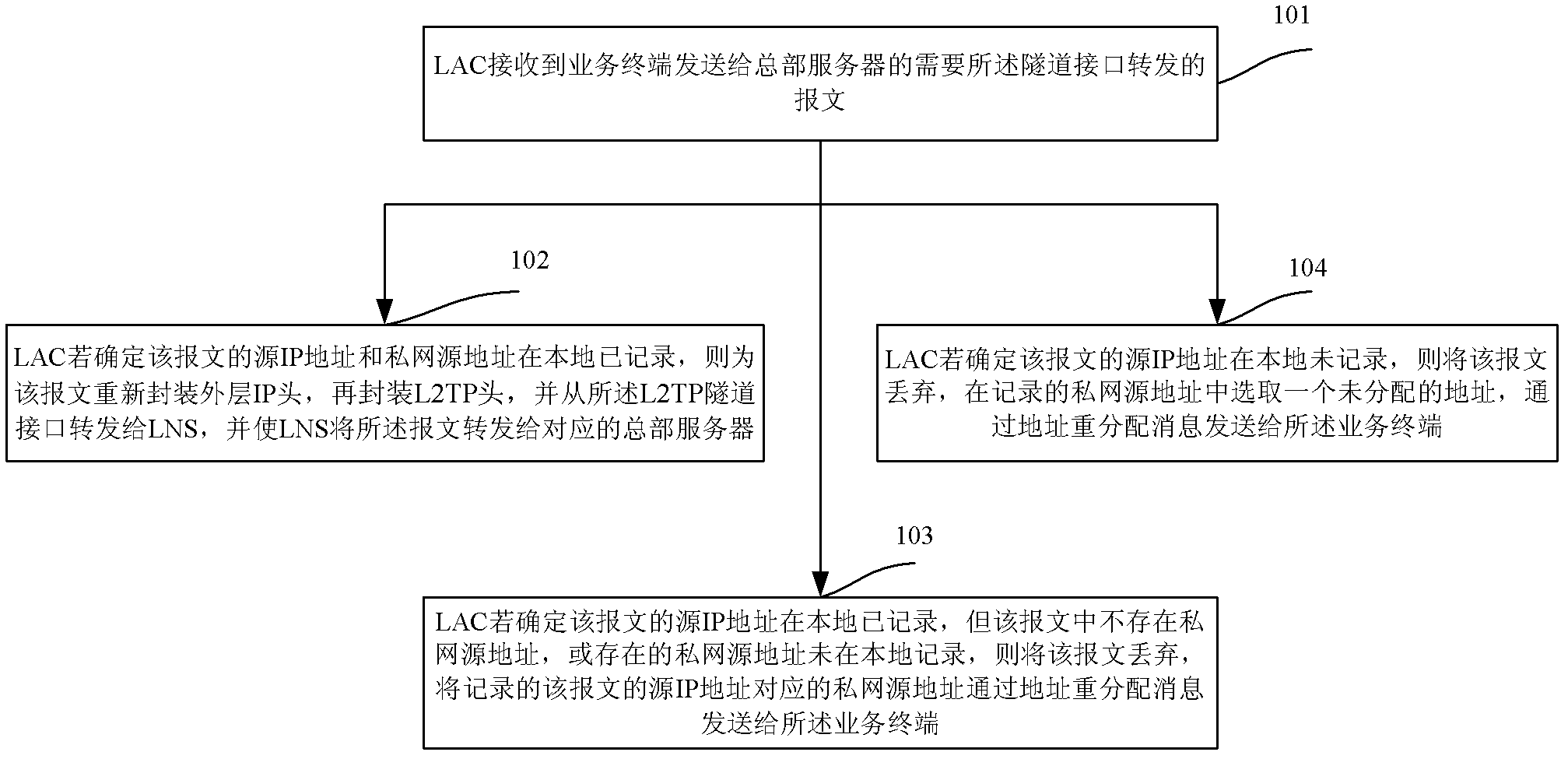
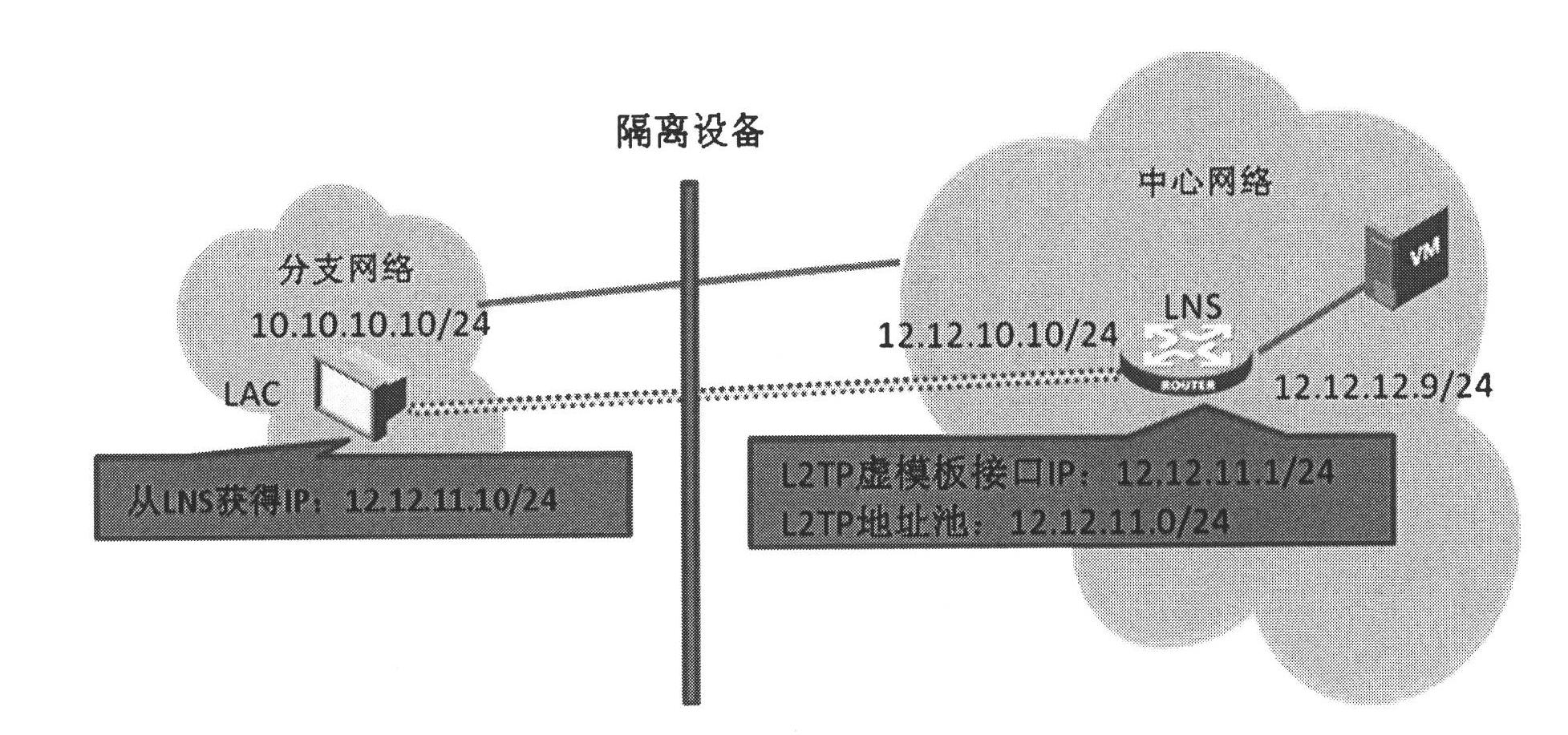
The invention discloses a message forwarding method and equipment which are applied to an L2TP (Layer-2 Tunneling Protocol)-based three-layer branch network. An LAC (L2TP Access Concentrator) obtains the client-side addresses distributed by an LNS (L2TP Network Server) during the process of establishing a session between the LAC and the LNS, and records the client-side addresses as private network source addresses, wherein the number of the client-side addresses is applied by the LNS; and when service terminals need to access a headquarters server, the recorded private network source addresses are distributed to corresponding service terminals, and the service terminals carry out communication with the headquarters server through two-layer IP (Internet Protocol) packages. With the adoption of the message forwarding method and the message forwarding equipment, the pressure of a headquarters router in the maintenance of a plurality of VPNs (Virtual Private Networks) can be lowered, and the trouble of coordinating the re-planning of the IP address fields of a plurality of branch mechanisms is avoided.
Owner:NEW H3C TECH CO LTD
Methods for passing through and assisting in passing through network isolation equipment in Internet protocol (IP) monitoring system, and node
The invention discloses a method for passing through network isolation equipment in an Internet protocol (IP) monitoring system. The method comprises the following steps that: a first monitoring node in an inner network of the network isolation equipment serves as a layer 2 tunneling protocol network server (LNS), and receives a tunnel connection request initiated by a layer 2 tunneling protocol (L2TP) relay which serves as an L2TP access concentrator (LAC); after L2TP tunnel connection is established, the first monitoring node allocates an IP address to the L2TP relay, and activates the IP address of own L2TP virtual interface; the first monitoring node receives a tunnel message from the L2TP relay, decapsulates the tunnel message to obtain an inner-layer IP message with the content of monitoring signaling data, acquires the monitoring signaling data from the inner-layer IP message, and performs corresponding signaling processing; and the first monitoring node encapsulates own generated monitoring signaling data into the inner-layer IP message, encapsulates the inner-layer IP message into the tunnel message, and transmits the tunnel message to the L2TP relay. By the method, the monitoring node can simply and effectively pass through the isolation equipment, and the interference of the isolation equipment in a monitoring service is avoided.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Method and system for protecting layer 2 tunneling protocol (L2TP) network
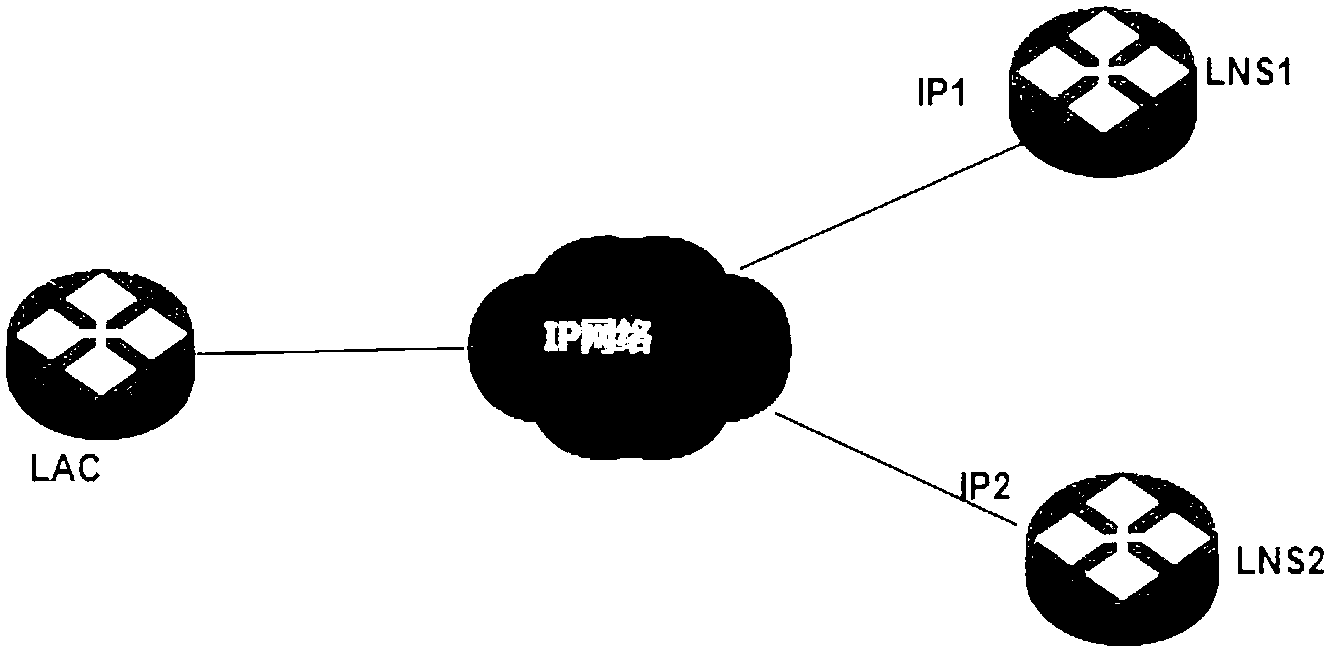
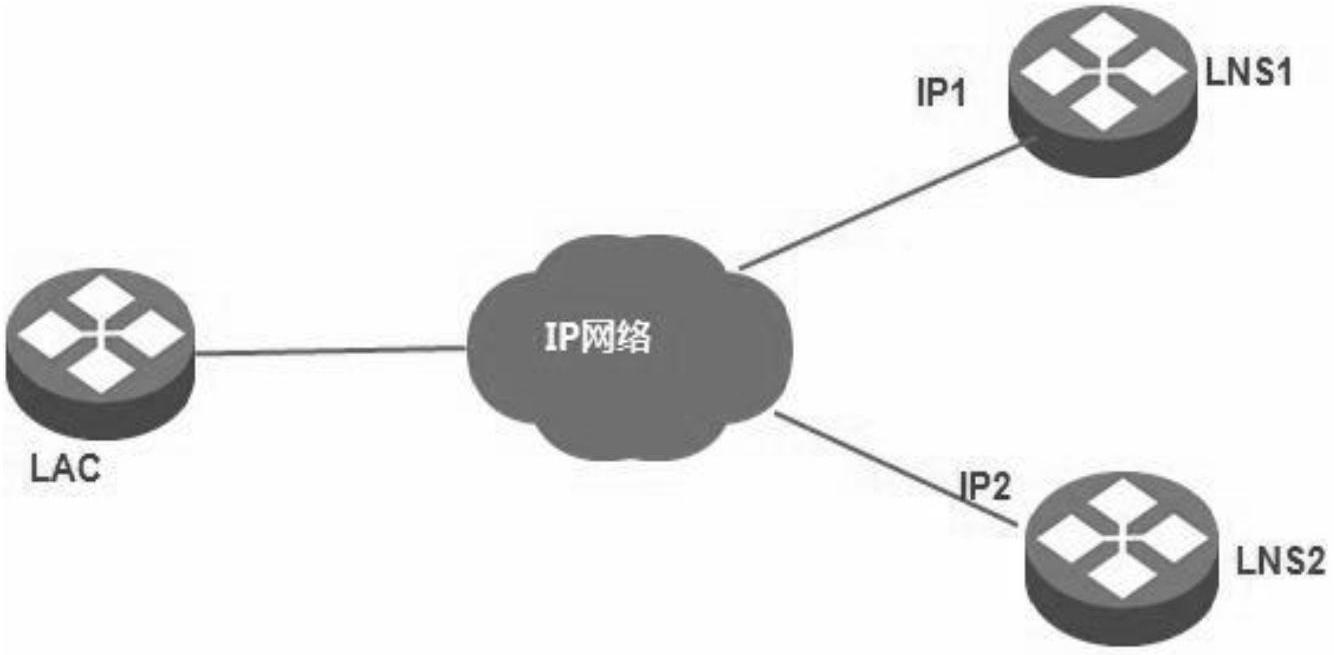
ActiveCN102480423AImprove business reliabilityImprove experienceNetworks interconnectionState switchingProtection system
The invention discloses a method for protecting a layer 2 tunneling protocol (L2TP) network. The method comprises the following steps that: a reserved L2TP network server (LNS) backs up information of the current online L2TP user on a master LNS, information of an L2TP tunnel corresponding to the L2TP user and information of an L2TP session; when the master LNS or a chain on which the master LNS is placed fails, the reserved LNS and the master LNS are subjected to master and reserved state switching; and the reserved LNS updates a route according to the backed information of the L2TP tunnel and the backed information of the L2TP session, and forwards user flow. The invention also discloses a system for protecting the L2TP network. By the system and the method, the failure of the LNS equipment and the chain on which the LNS equipment is placed cannot influence normal service of the L2TP user, and the L2TP user and an L2TP access concentrator (LAC) cannot notice the generation and the recovery of the failure, so that the failure in the L2TP network is eliminated, and the user experience of the L2TP network is improved effectively.
Owner:ZTE CORP
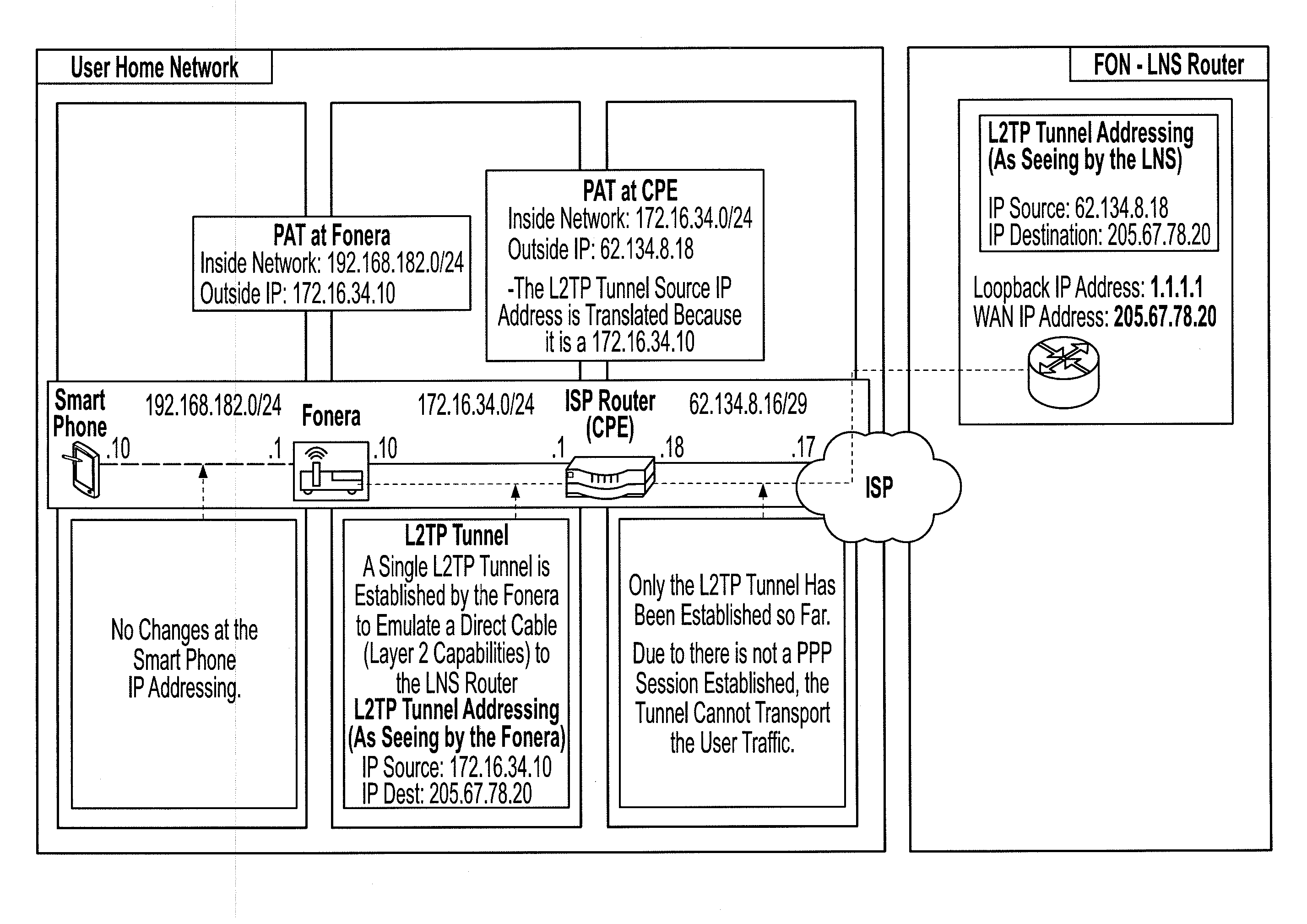
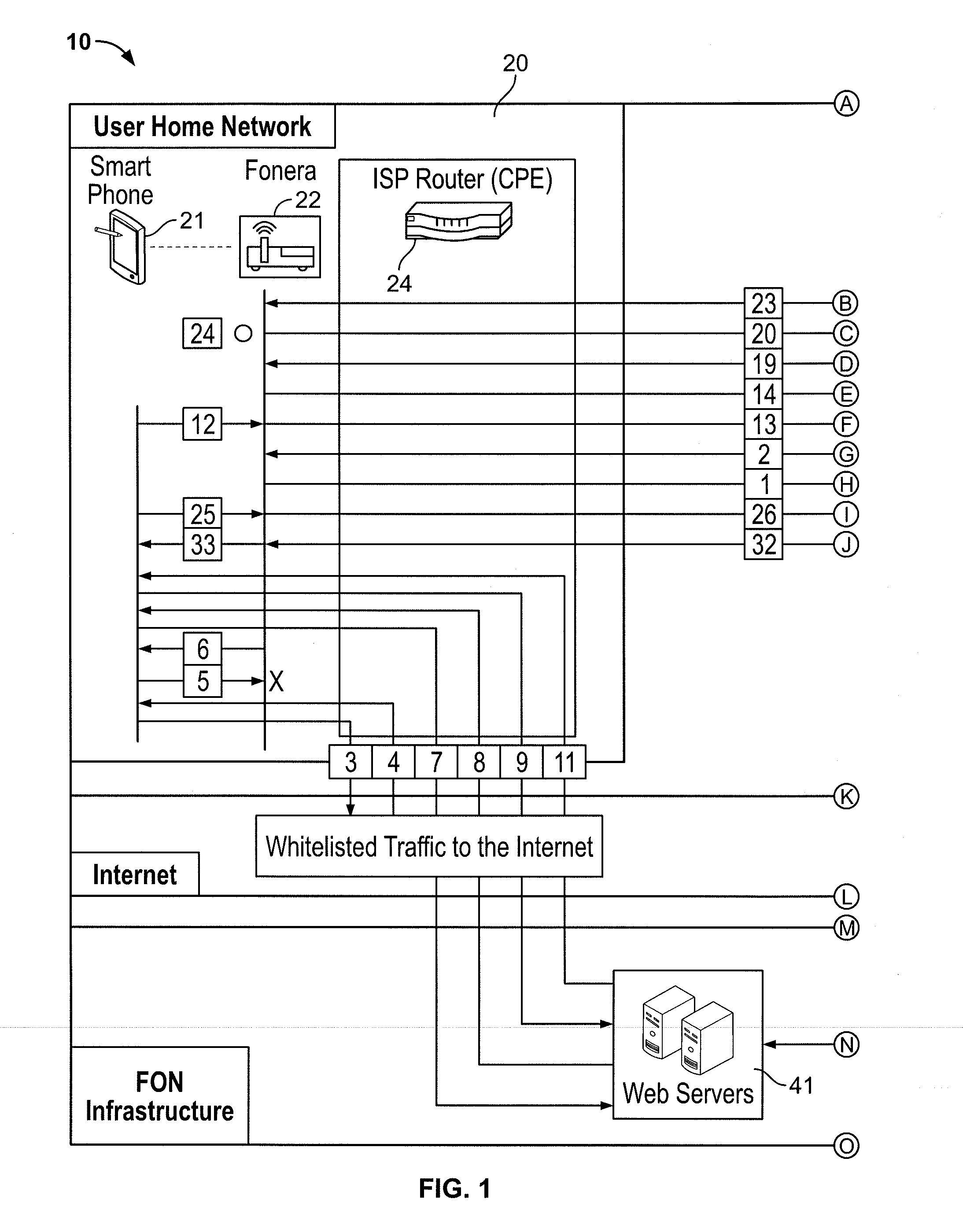
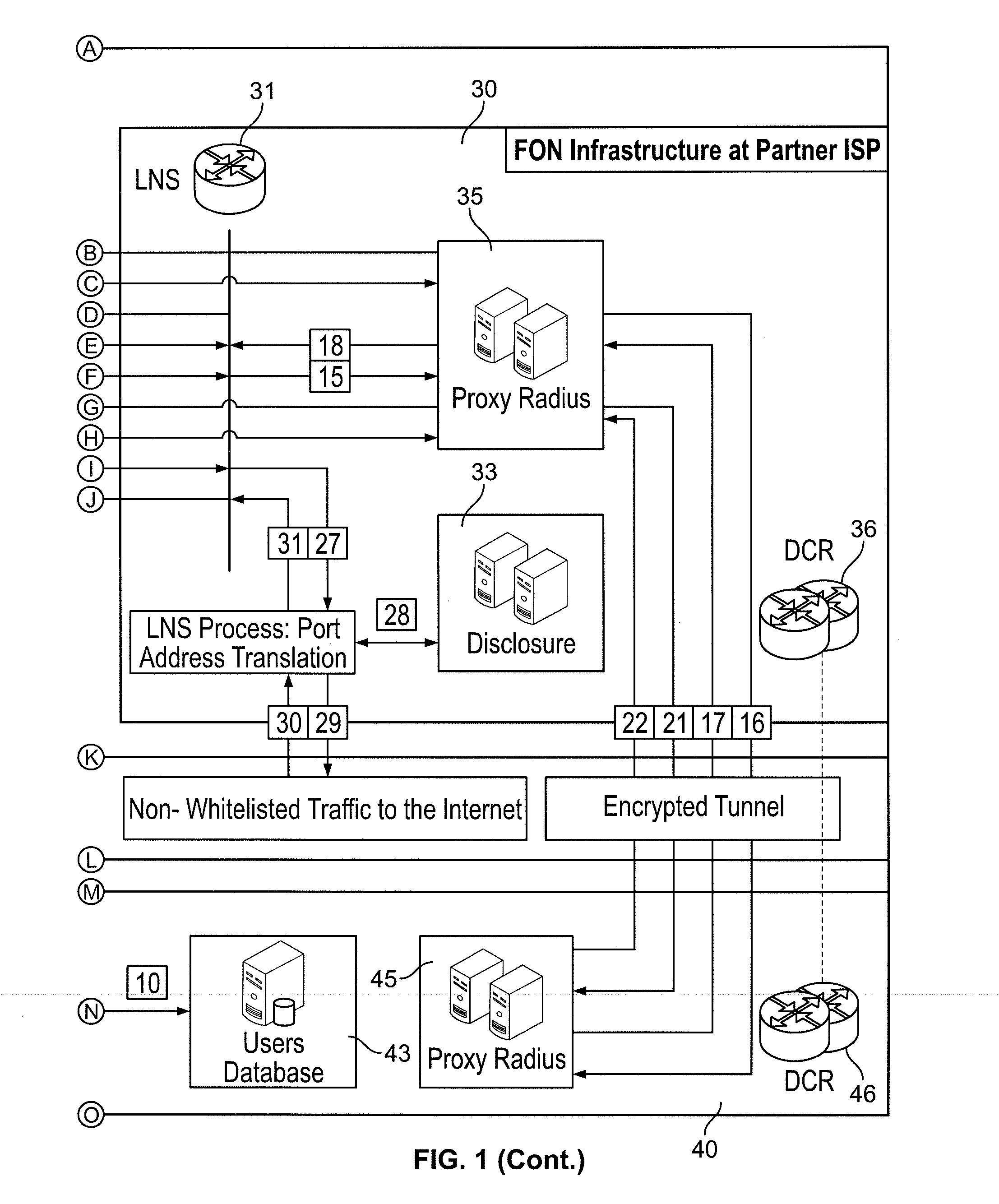
Secure tunneling platform system and method
ActiveUS20130239181A1Less complexMaximum availabilityDigital data processing detailsMultiple digital computer combinationsWireless routerData center
A system identifies a user, even a user behind a wireless router, and provides a virtual tunnel over the internet for communication with the user. A data center at an Internet Service Provider may work in concert with a central data center to authenticate the user and to provide access, for example using a layer 2 tunneling protocol and a point-to-point data (PPP) link protocol. A layer 2 tunneling protocol network server (LNS) may provide public IP address translation services.
Owner:FON WIRELESS
Method and device for backing up lonworks network service (LNS)
ActiveCN102710520ASolve the problem of not being able to back up across three layersImprove networking flexibilityNetworks interconnectionLonWorksGeolocation
The invention provides a method for backing up a lonworks network service (LNS), and the method comprises the steps of receiving and locally storing information of a layer 2 tunneling protocol (L2TP) tunnel transmitted by a second LNS device staying at an active status through an expanded virtual router redundancy protocol (VRRP) message when a first LNS device stays at a standby status, wherein the tunnel information comprises a tunnel identification (ID), a conversation ID and an internet protocol (IP) address of a location area code (LAC); switching the first LNS device to the active status, activating the local stored tunnel information and issuing a host computer route of a virtual IP address to a network when the first LNS device staying the standby status ensures that the second LNS device staying at the active status has failure or receives an L2TP tunnel takeover notice transmitted by the second LNS device staying at the active status; and revoking the issued host route of the virtual IP address when the first LNS device is switched from the active status to the standby status. According to the method and the device, no requirement for the geological location of the devices which are mutually backed up each other exists, so that the networking flexibility is greatly improved.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
LAC-based LFI support for tunneled PPP sessions
ActiveUS20070071035A1Energy efficient ICTTime-division multiplexPoint-to-Point ProtocolNetwork service
An embodiment may provide for link fragmentation and interleaving at an access device located between a point to point link and a tunneled connection. An embodiment may include a method of receiving frames through a tunnel from a network server, fragmenting at least some of the frames from the network server, and sending fragmented and unfragmented frames over a data link to an endpoint device. In some embodiments the frames may be multilink point to point protocol (MLPPP) frames. In yet another embodiment, the frames may be received through a layer two tunneling protocol (L2TP) tunnel. An embodiment may include scanning a frame for PPP options and removing options related to MLPPP negotiation and then forwarding the frame to a network server. An embodiment may comprise means capable of executing the embodiment method or may include instructions that when executed on a machine are capable of the embodiment method. An embodiment may include a device with a first port to send or receive fragmented frames to a data link, a second port to tunnel assembled frames to a network server through a packet network, and circuitry in communication with the first port and the second port, the circuitry to fragment link fragmentation frames to be sent through the first port, reassemble any fragmented frames received from the first port, and send or receive assembled frames through the second port.
Owner:CISCO TECH INC
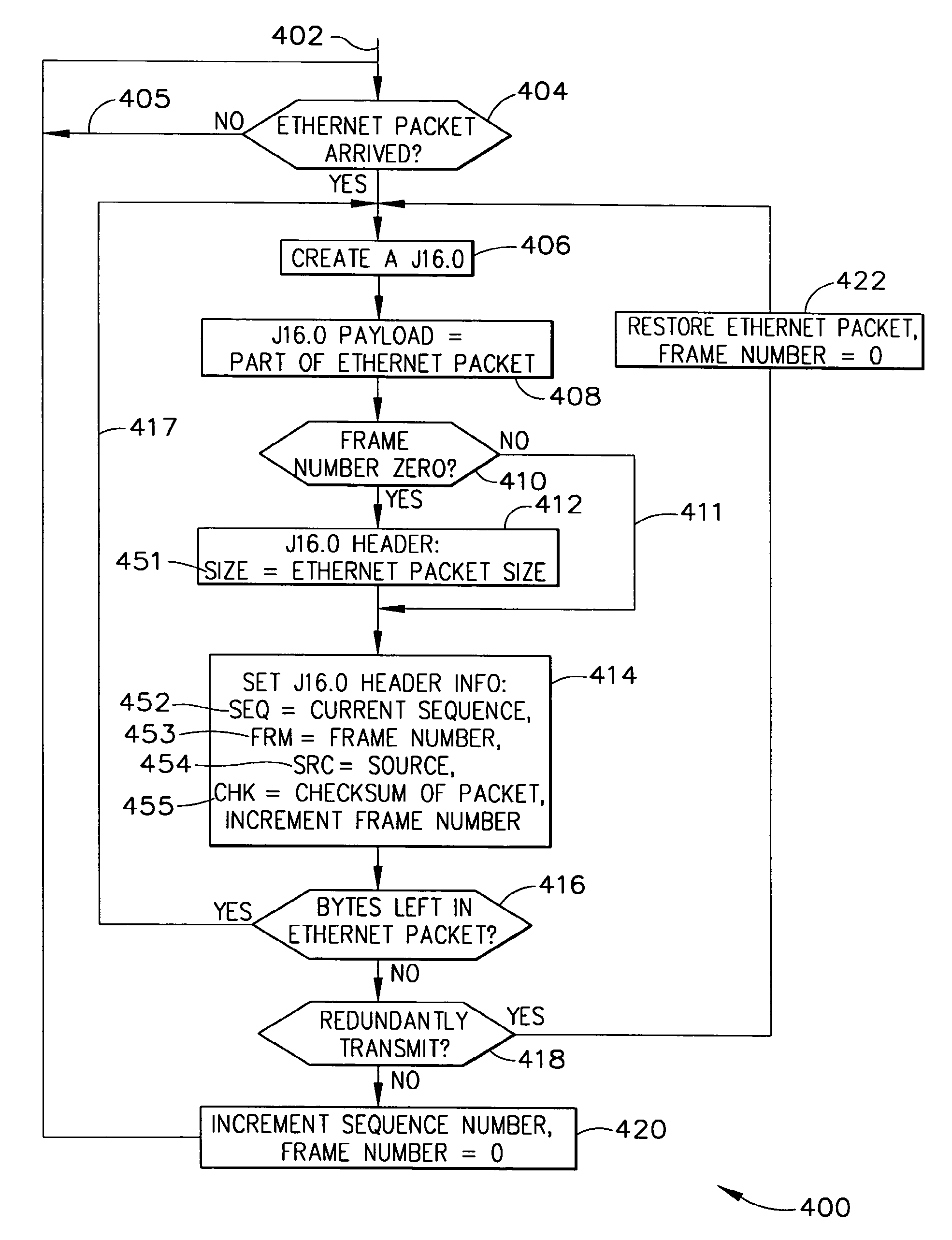
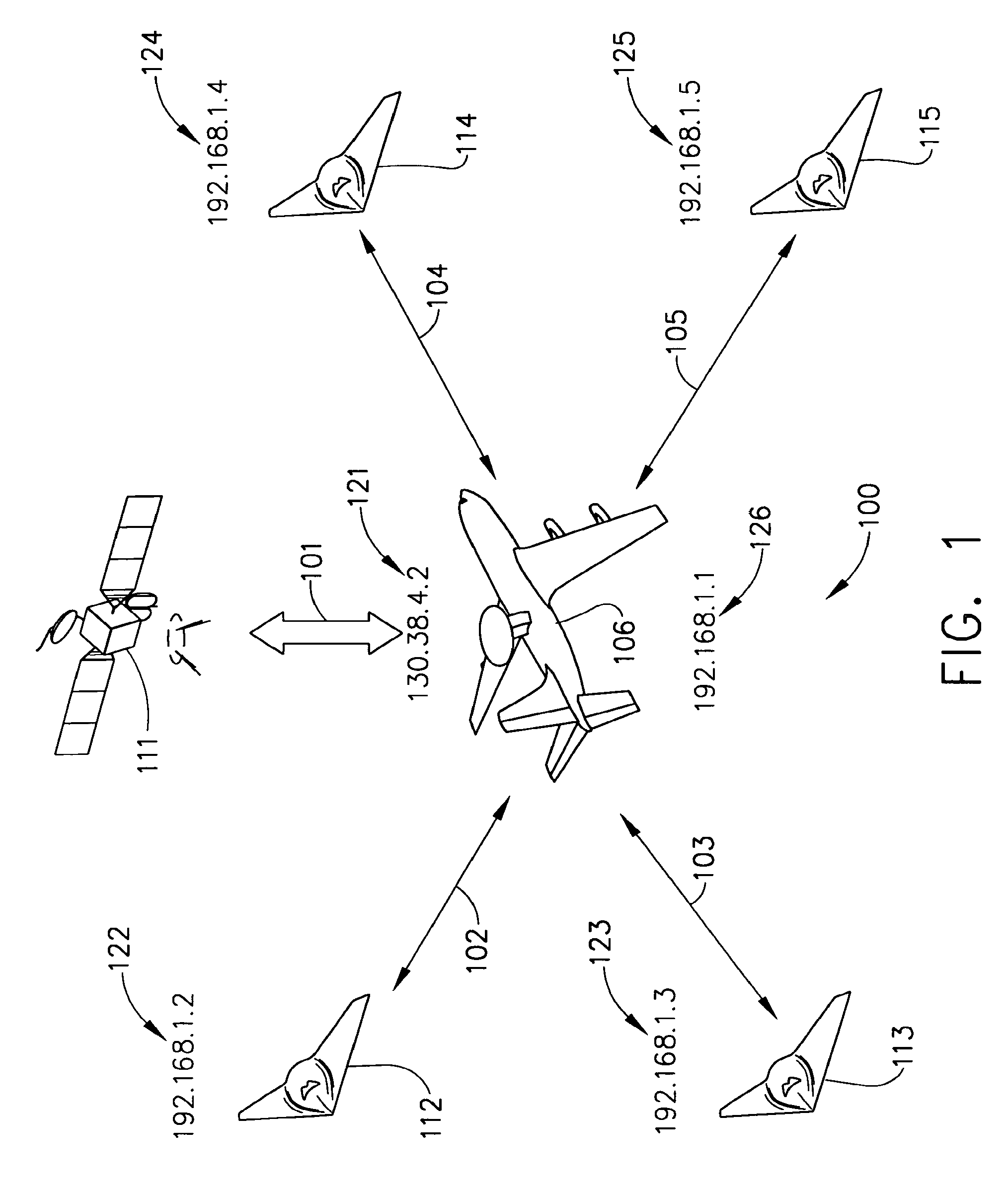
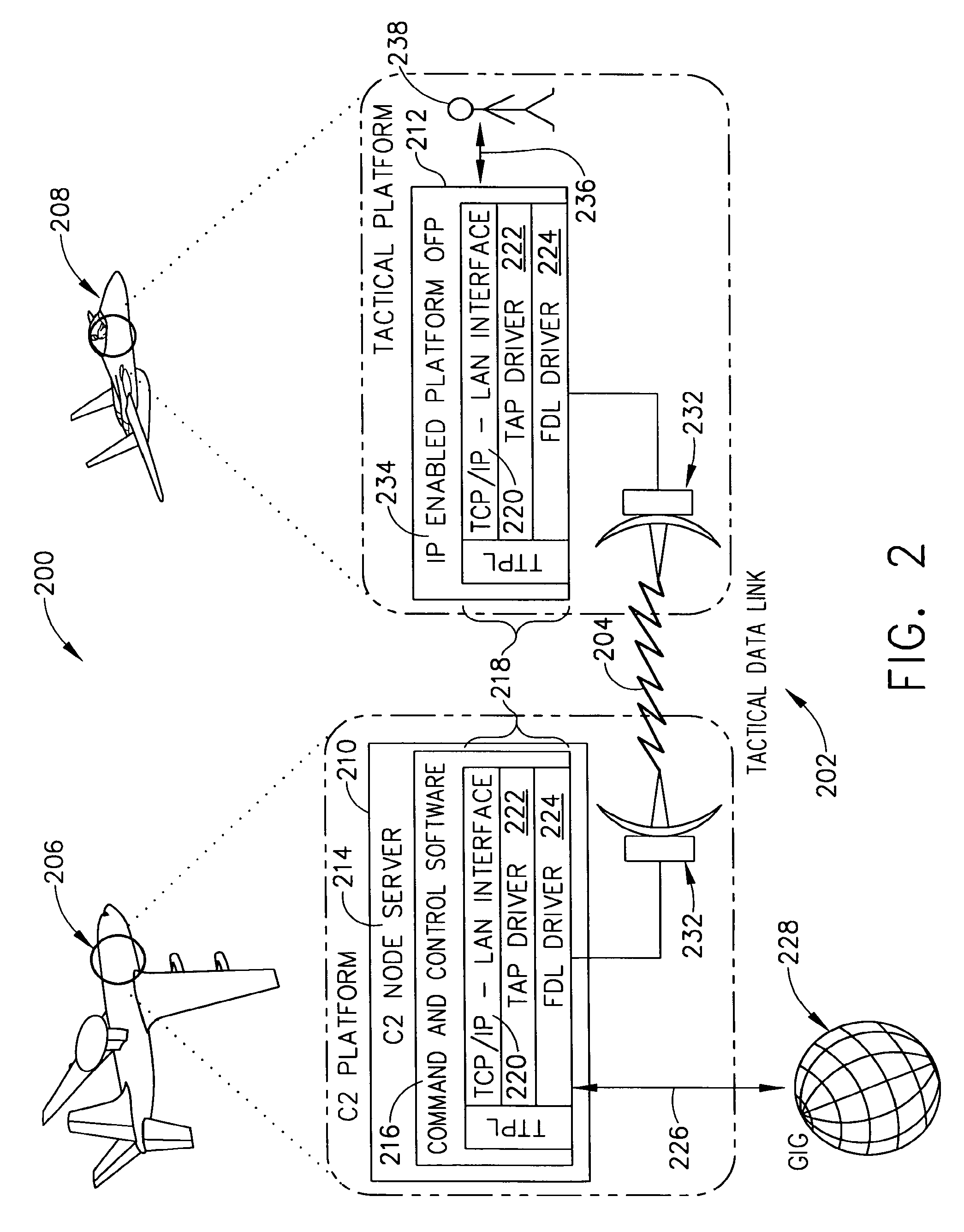
TCP/IP tunneling protocol for link 16
InactiveUS7953110B1Time-division multiplexData switching by path configurationNetwork linkPrivate network
A method and system are provided for executing a protocol for tunneling of transmission control protocol / internet protocol (TCP / IP) packets over a tactical link. The tunneling protocol includes interfacing to a host software on a node of a tactical network using a TAP interface; breaking up ethernet packets from the TAP interface into J16.0 messages that include payload data from the ethernet packet and header information that uniquely identifies the J16.0 message for deterministic reassembly of the ethernet packet from the stream of J16.0 messages in which it is included. The J16.0 messages may be transmitted using a fighter data link over a tactical network link. At the destination node of the link, the J16.0 messages may be reassembled into ethernet packets, allowing the tactical network to be implemented as virtual private network having (internet protocol) IP addresses for each node.
Owner:THE BOEING CO
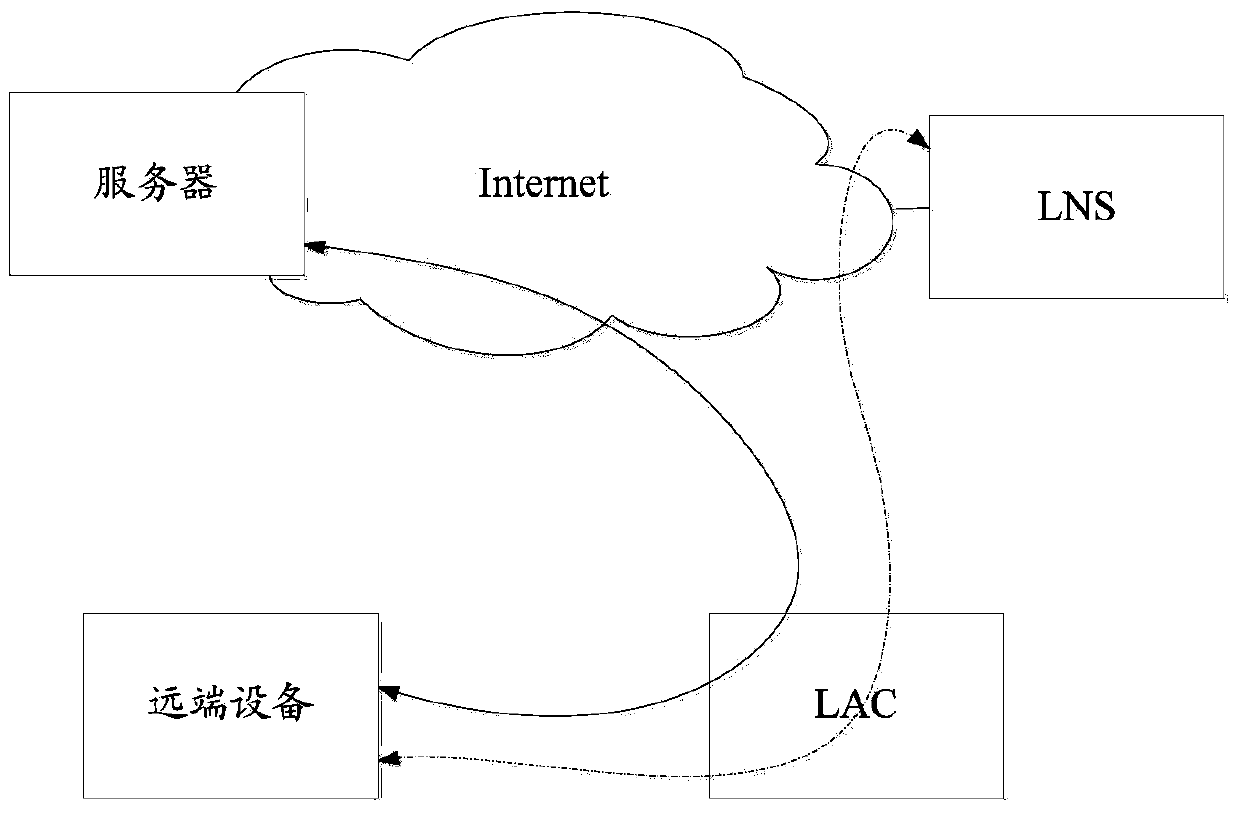
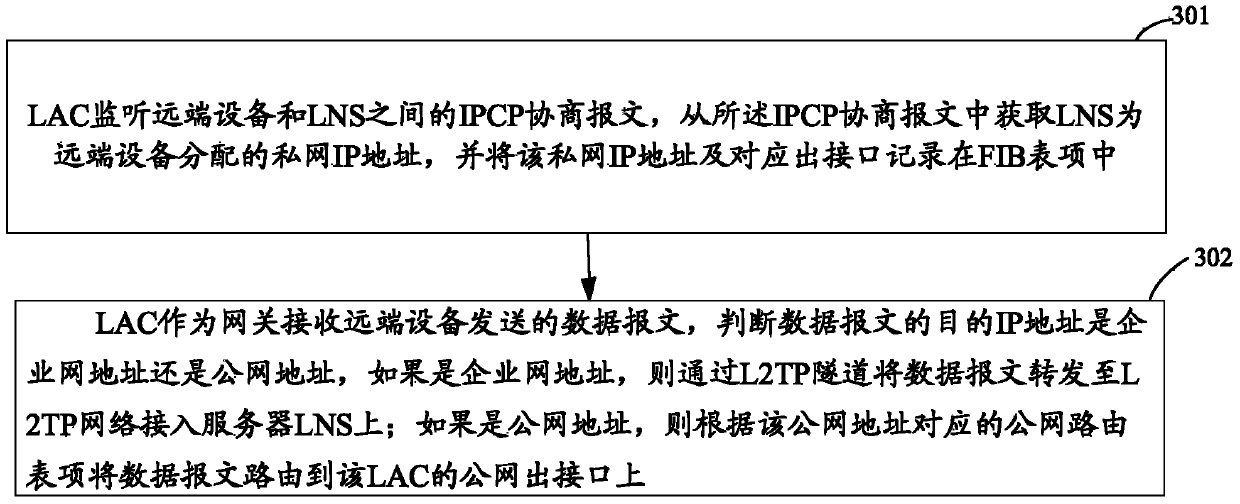
Business access method and device based on Layer 2 Tunneling Protocol (L2TP)
InactiveCN103747116AReduce the burden onIncrease profitNetworks interconnectionRouting tableAccess method
The invention discloses a business access method based on a Layer 2 Tunneling Protocol (L2TP). The method comprises the steps that an L2TP Access Concentrator (LAC) serving as a gateway receives a data message sent by far-end equipment, and judges whether the target IP address of the data message is an enterprise network address or a public network address, if the target IP address is the enterprise network address, forwarding the data message to an L2TP Network Server (LNS) for accessing through an L2TP tunnel, and if the target IP address is the public network address, routing the data message to a public network outcoming interface of the LAC according to a public network routing table entry corresponding to the public network address. The invention also discloses the LAC. After the business access method and the LAC are adopted, the burden of enterprise network LNS equipment is reduced, and the Internet bandwidth utilization rate of an enterprise network is improved.
Owner:NEW H3C TECH CO LTD
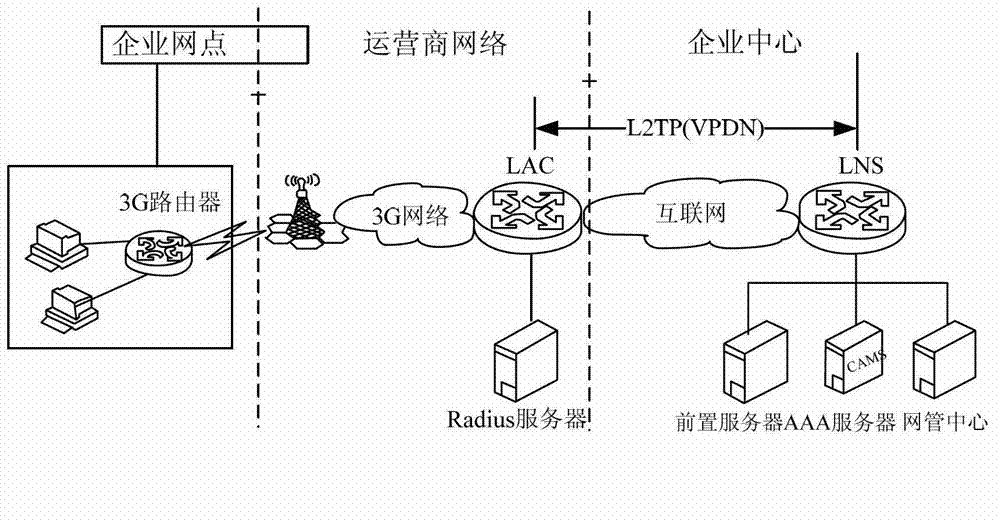
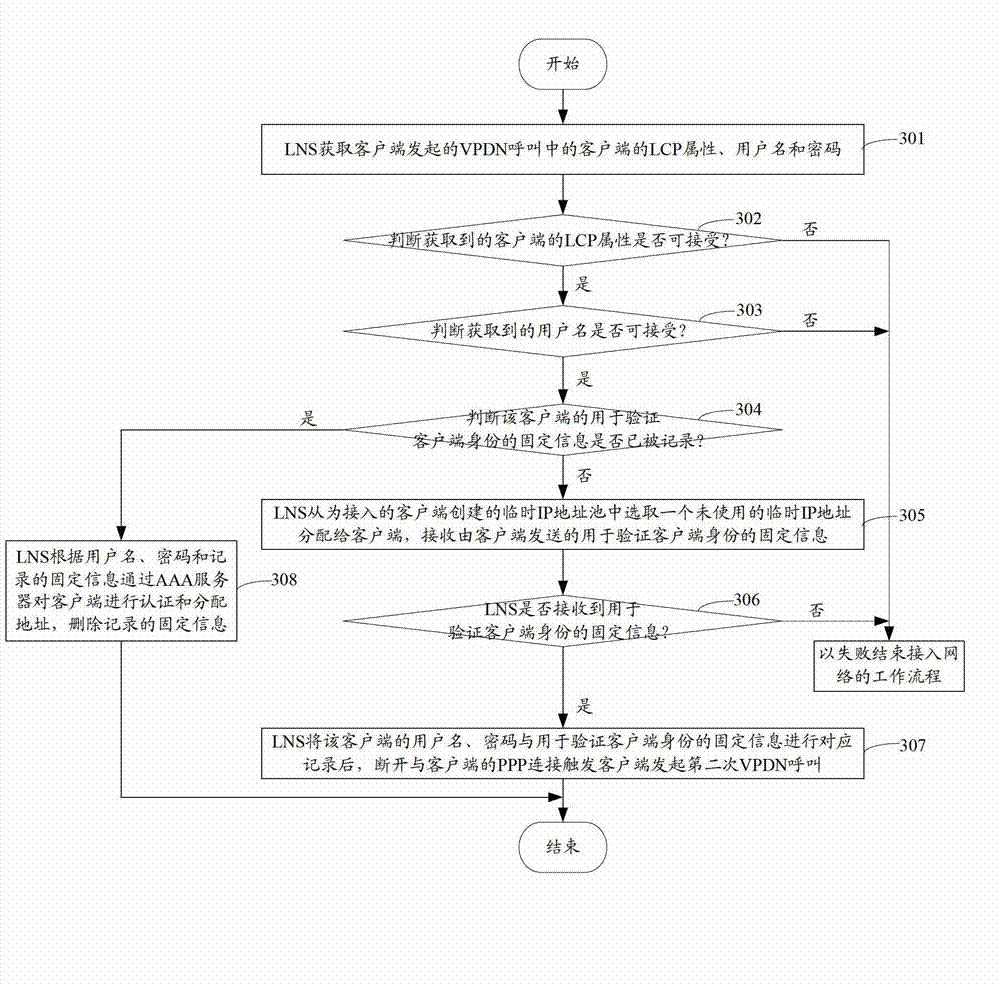
Method and device for enabling third generation (3G) user to safely access to network
The invention discloses a method and a device for enabling a third generation (3G) user to safely access to network. When a link control protocol (LCP) attribute and a user name of a client, which are acquired by layer 2 tunneling protocol network server (LNS), are acceptable, an temporary internet protocol (IP) address is selected from an established temporary IP address pool and distributed to the client, fixed information which is sent by the client and can verify the client identity is received, when the fixed information is received, the fixed information is correspondingly recorded with the user name and a password, the point-to-point protocol (PPP) connection with the client is disconnected to trigger the client to initiate a second time virtual private dial-up network (VPDN) call, the client is informed of the specified IP address which is distributed by authentication, authorization and accounting (AAA) server to the client according to the recorded fixed information, the user name and the password, or when the fixed information is received, the fixed information, the user name and the password are directly sent to the AAA server to verify the client, and after the client passes the authentication, the client is informed of the specified IP address which is distributed by the AAA server to the client. By means of the method and the device, the client can access to network only when the client is subjected to safety authentication by the LNS, and the safety of network access is improved.
Owner:NEW H3C TECH CO LTD
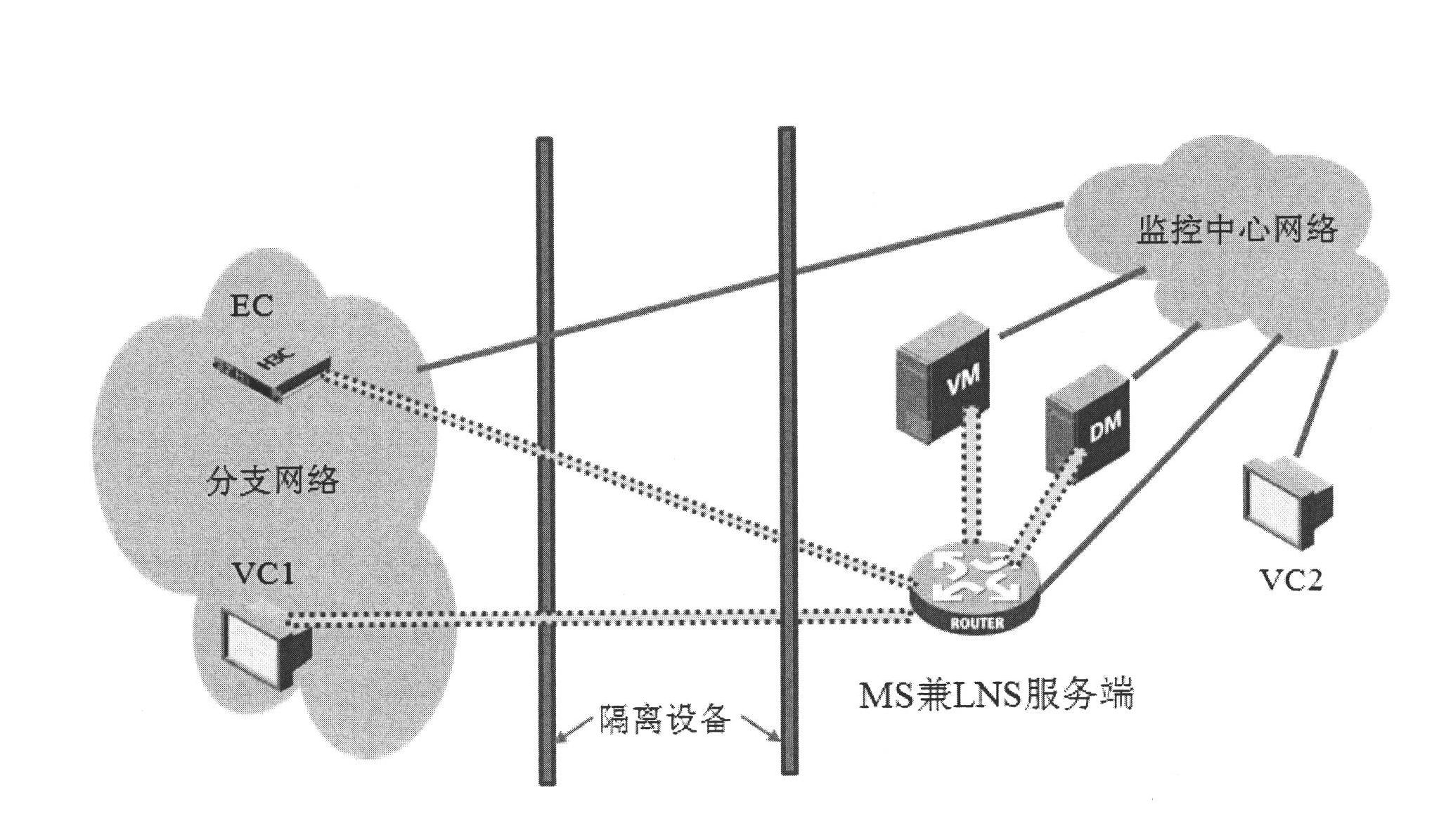
Method and device for saving WAN (wide area network) bandwidth in IP (internet protocol) monitoring system
ActiveCN102546350ASolve the problem of bandwidth consumptionSolve consumptionNetworks interconnectionInternet protocol suiteMonitoring system
The invention provides a method for saving WAN (wide area network) bandwidth in an IP (internet protocol) monitoring system. The monitoring system further comprises an EC (electronic computer), a VC (visible computer) and an LNS (L2TP (layer 2 tunneling protocol) network server), wherein at least the EC and the VC are in L2TP tunnel connection with the LNS. The method comprises the following steps: receiving registration messages sent by the EC and the VC, storing address information of EC and VC in the registration messages; after establishing a transmission channel for monitoring video streams on the L2TP between the EC and VC, issuing commands of trying to communicate with an intranet of an opposite terminal to the EC and the VC; receiving an intranet communication trying report sent by the VC, judging whether the EC can communicate with the VC through the intranet according to the address information of the report message and the self-stored address information; if so, sending a communication mode switching command to instruct the EC to switch to an intranet communication mode from the L2TP tunnel communication mode. The method can be used for effectively solving the WAN bandwidth consumption problem in a tunnel mode.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
Method for simulating L2TP dialing
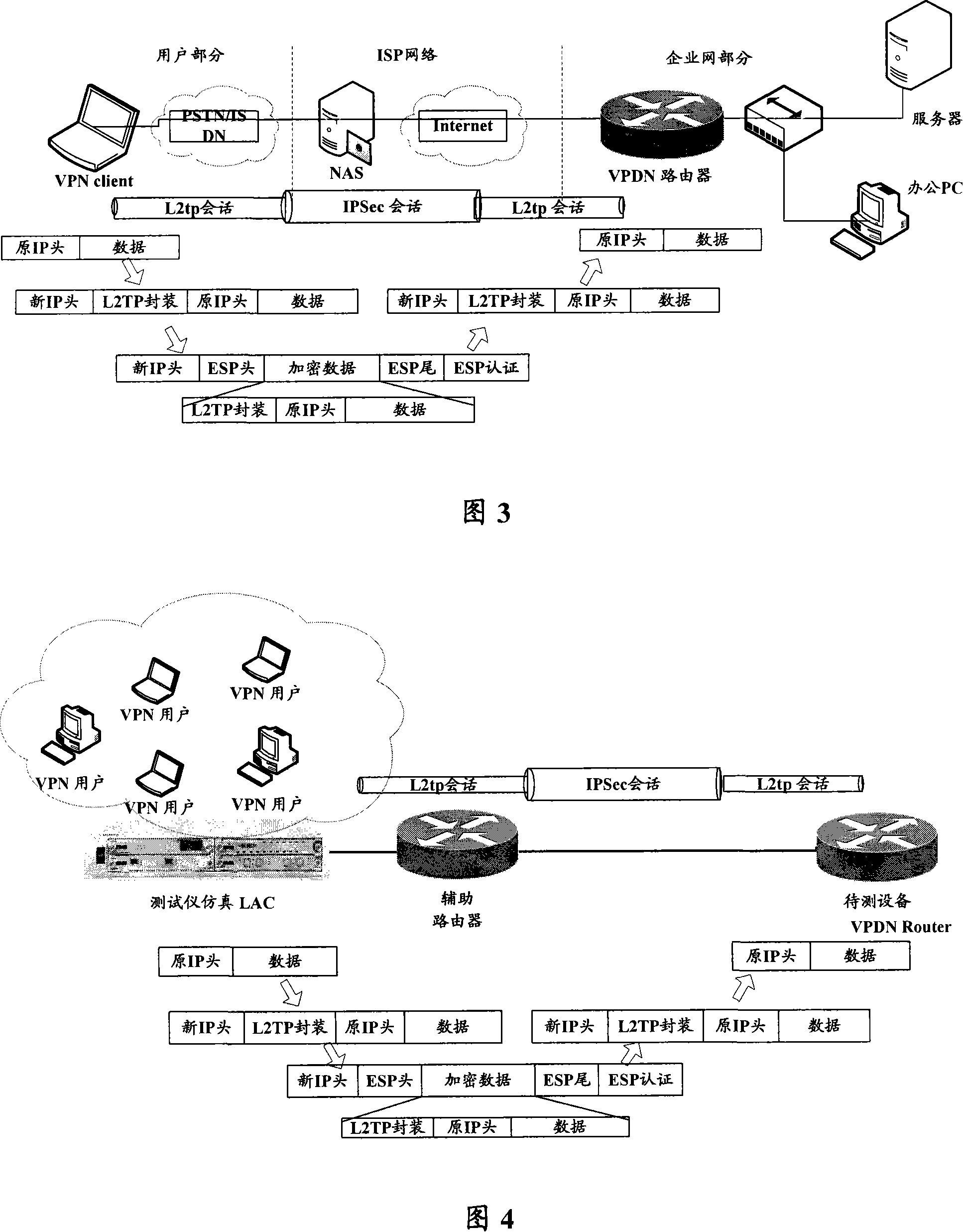
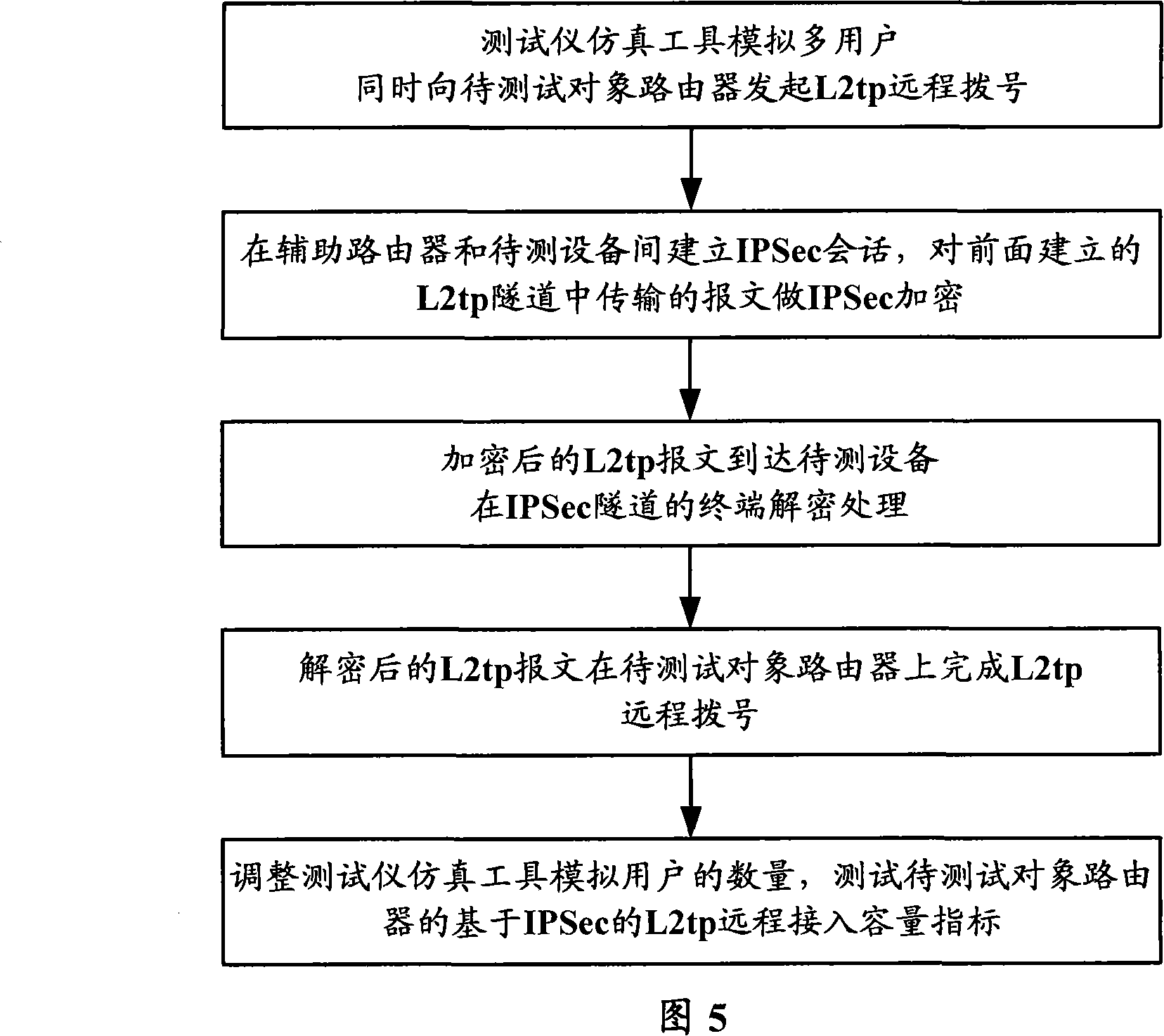
ActiveCN101227344ARealize simulationSolve technical problemsNetworks interconnectionIPsecComputer science
The invention provides a method for simulating a layer 2 tunneling protocol L2TP to dial, the method comprises utilizing a test instrumentation to simulate a L2TP user to switch in, having a conversion with IPSec which is established by tested equipment after doing densification treatment with IP security IPSec tunneling mode for the message such as L2TP which is sent out by the test instrumentation through an auxiliary router, and finishing remote dial of L2TP. The method of simulating L2TP to dial of the invention can simulate a large amount of users and can simultaneously switch in VPN on the base of L2TP form of IPSec.
Owner:ZTE CORP
System and method for transporting digital baseband streams in a network environment
ActiveUS8964641B2Time-division multiplexWireless commuication servicesApplication programming interfaceMulti protocol
A method is provided in example embodiments that include receiving a radio signal stream and segmenting the radio signal stream into segments. The segments may be packetized and transported in packets over a pseudowire in a packet-switched network. The radio signal stream can be reconstructed from the segments. In more particular embodiments, the pseudowire may be a multi-protocol label switching pseudowire or a layer 2 tunneling protocol pseudowire, for example. In yet other specific example embodiments, the radio signal stream may be received using a common public radio interface or a femtocell application programming interface.
Owner:CISCO TECH INC
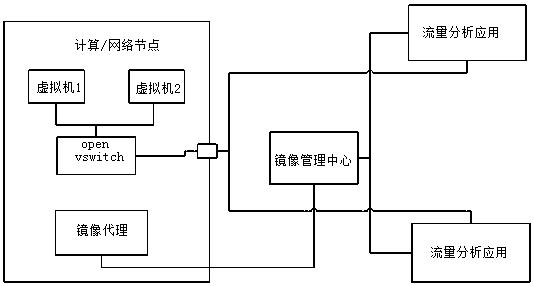
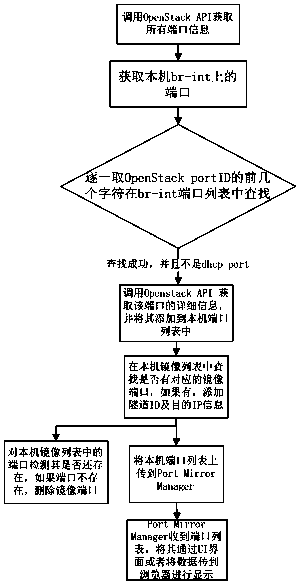
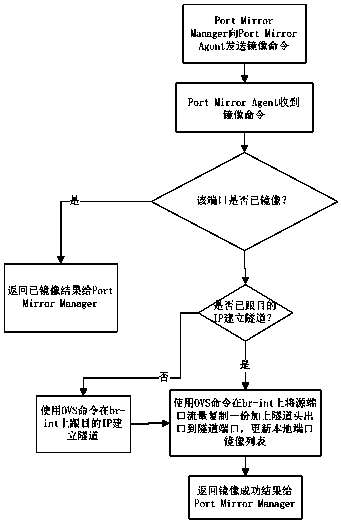
OpenStack traffic collection method based on tunneling protocol
InactiveCN108111384AEasy to analyzeConvenient and free choiceNetworks interconnectionTraffic capacityPublic network
The invention provides an OpenStack traffic collection method based on a tunneling protocol. The method specifically includes the following steps: a mirroring proxy and a mirroring management center are set, wherein the mirroring proxy is deployed on a network node or a computing node of OpenStack, and the mirroring management center is deployed on other physical equipment or virtual machines; themirroring management center sends a mirroring command to the mirroring proxy; and after receiving the mirroring command, the mirroring proxy adds a tunnel header to the traffic of a specified sourceport that is copied and sends the tunnel header and the traffic to a corresponding traffic analysis application through a tunnel established with a destination IP. Compared with the prior art, the virtual machines or virtual networks or services to which the aggregated traffic belongs can be conveniently distinguished, and the traffic of a mirroring virtual machine, the traffic of the virtual networks to the outside and the traffic of a virtual router to a public network can be conveniently and freely selected.
Owner:北京科来数据分析有限公司
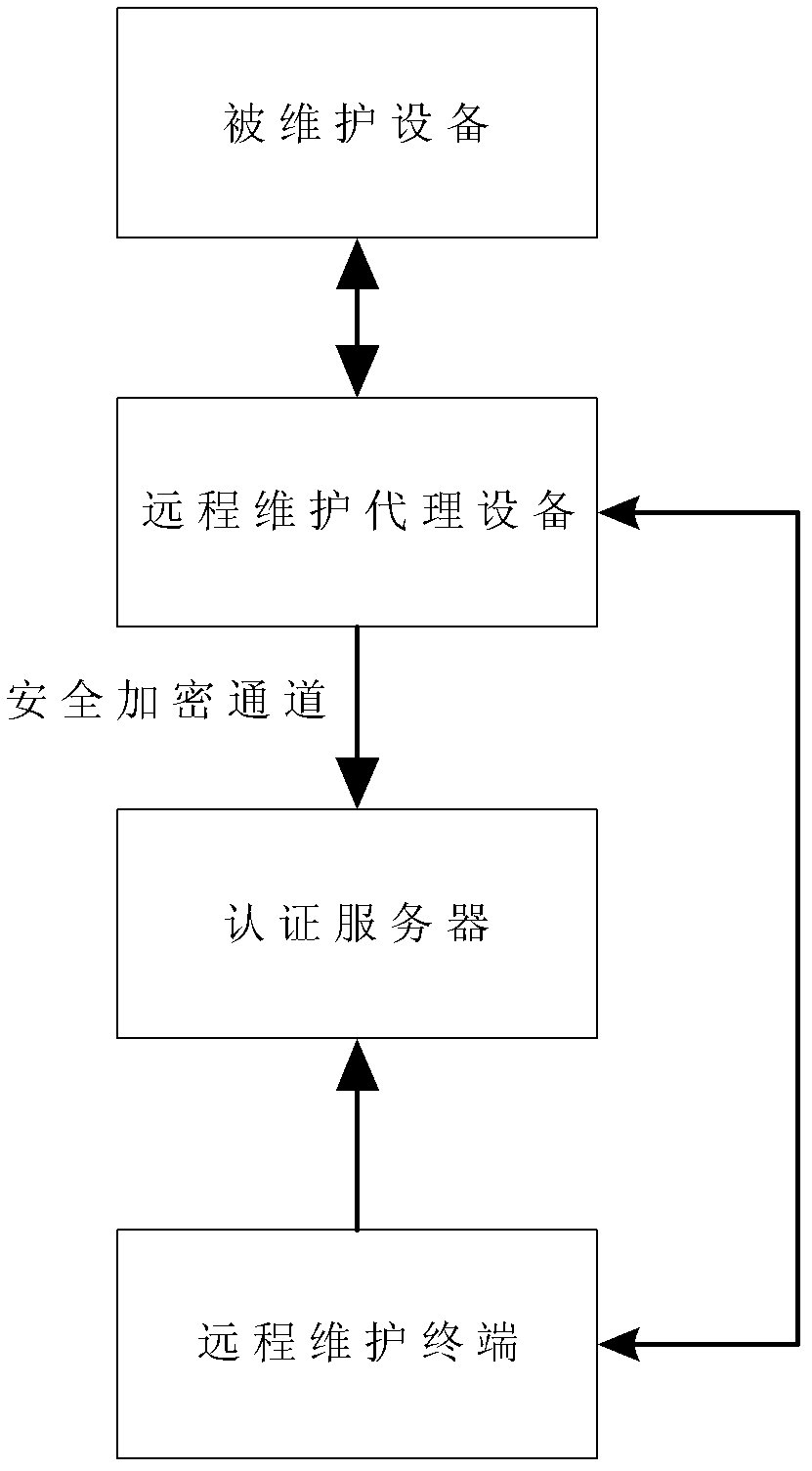
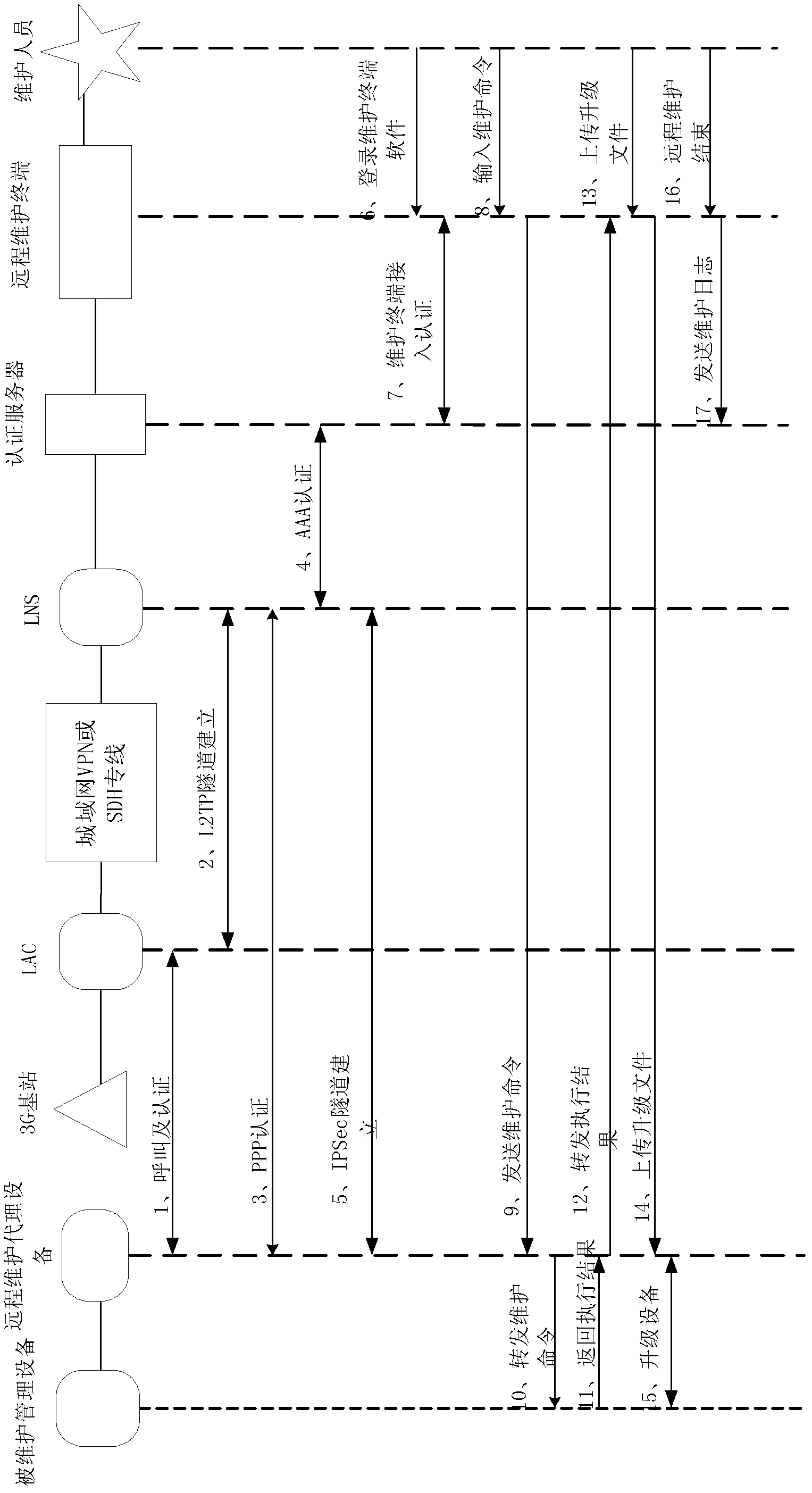
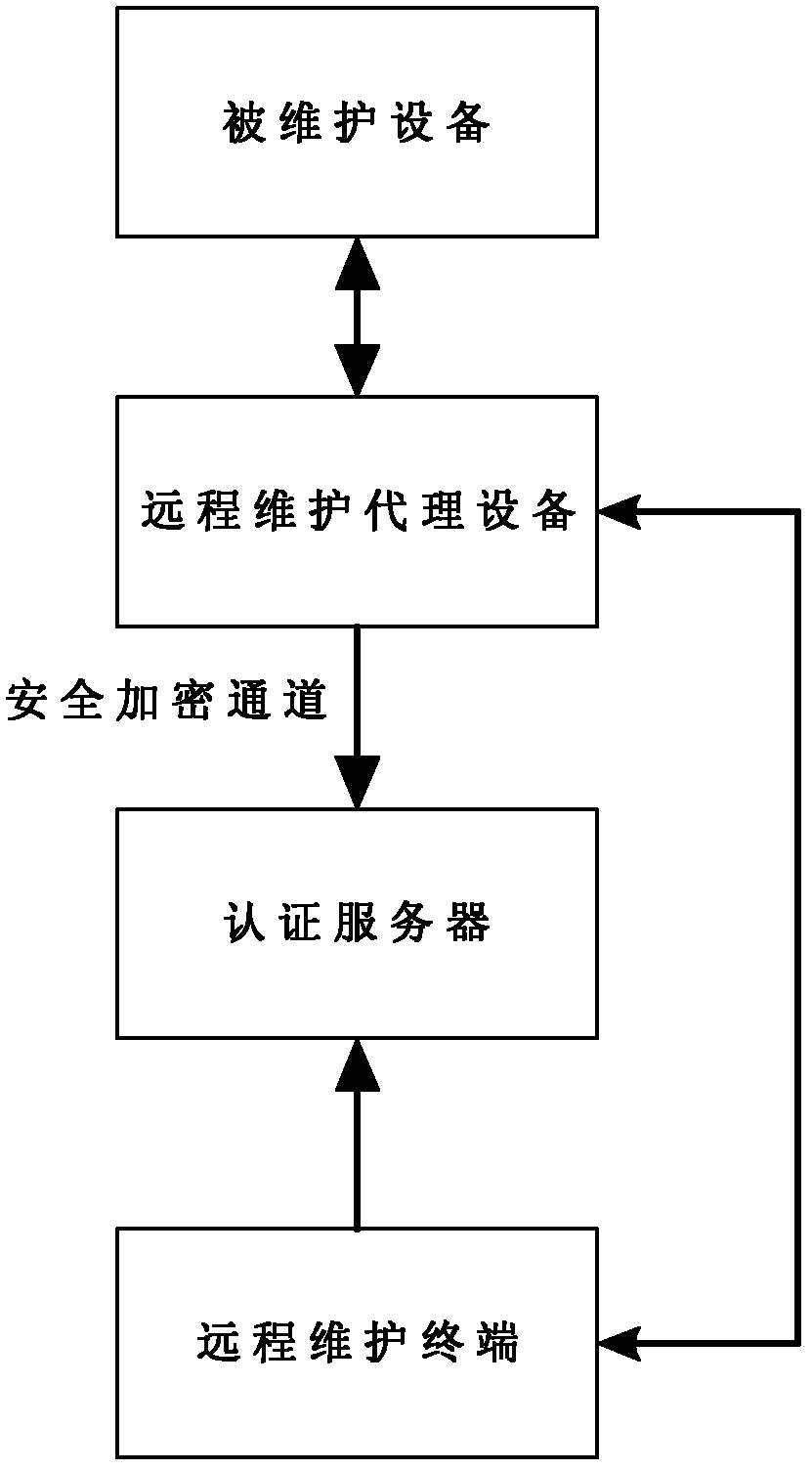
Network equipment remote maintenance system and maintenance method
InactiveCN102647300ARespond promptly to maintenance needsEnsure safetyData switching networksThird generationAuthentication server
The invention relates to the network equipment management and maintenance technology, and discloses a network equipment remote maintenance system and a method, which solve the problems of long period, high cost and poor safety and reliability of the conventional prior in network equipment maintenance. The network equipment remote maintenance system comprises remote maintenance agent equipment, an authentication server and a remote maintenance terminal, wherein the remote maintenance agent equipment constructs an encrypted secure channel with a L2TP (layer 2 tunneling protocol) network server through a 3G network, and is used for receiving data sent by the remote maintenance terminal through a secure connection channel and forwarding the data to the equipment to be maintained, and for receiving the uploaded data of the equipment to be maintained and forwarding the data to the remote maintenance terminal through the encrypted secure channel; the authentication server is used for access authentication of the remote maintenance agent equipment and the access authentication of the remote maintenance equipment; and the remote maintenance terminal is used for receiving maintenance command input of a remote maintenance personnel, and for sending the maintenance command to the remote maintenance agent equipment and receiving the uploaded maintenance result. The network equipment remote maintenance system provided by the invention is suitable for network equipment maintenance.
Owner:MAIPU COMM TECH CO LTD
Method and system for message transmission
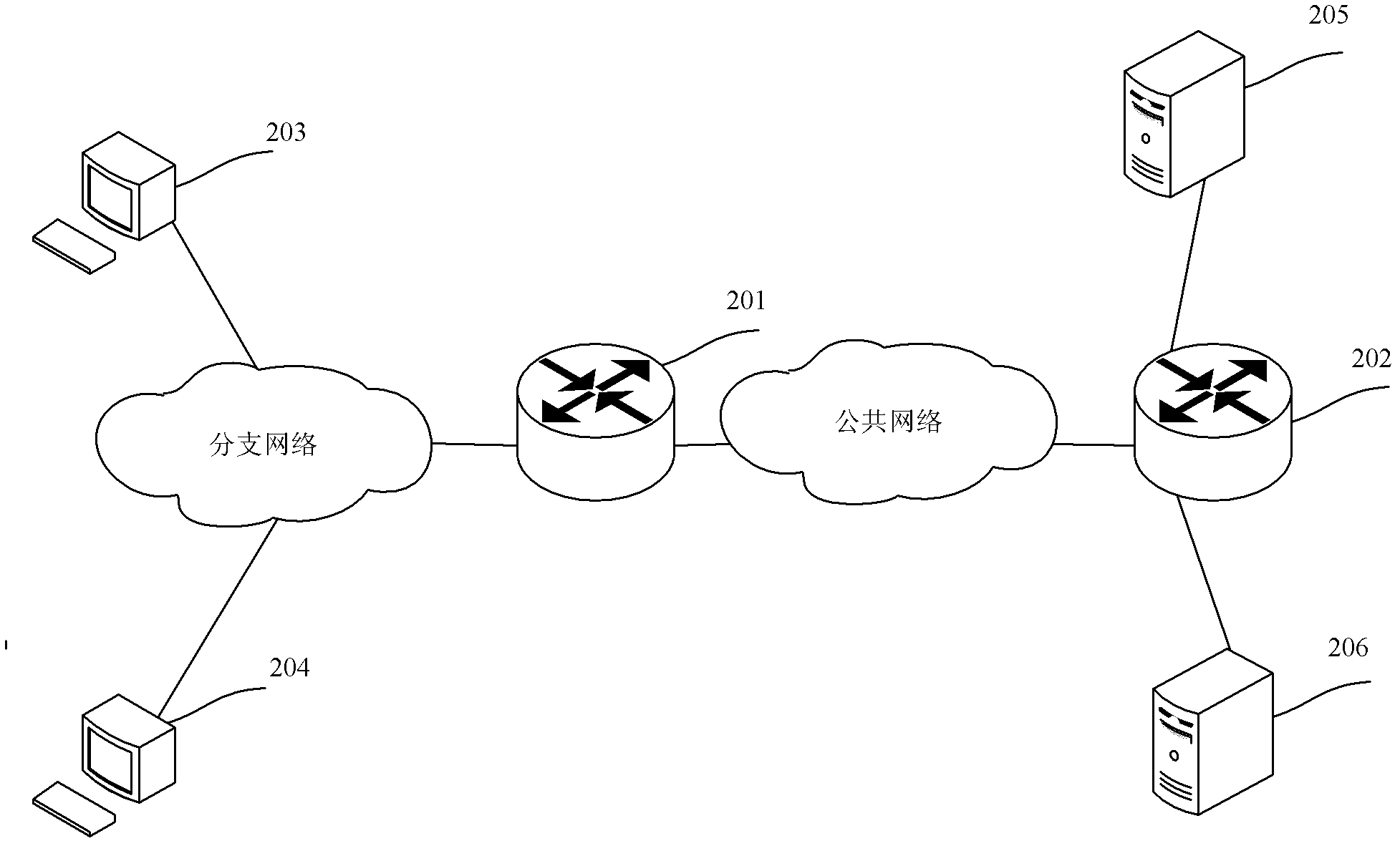
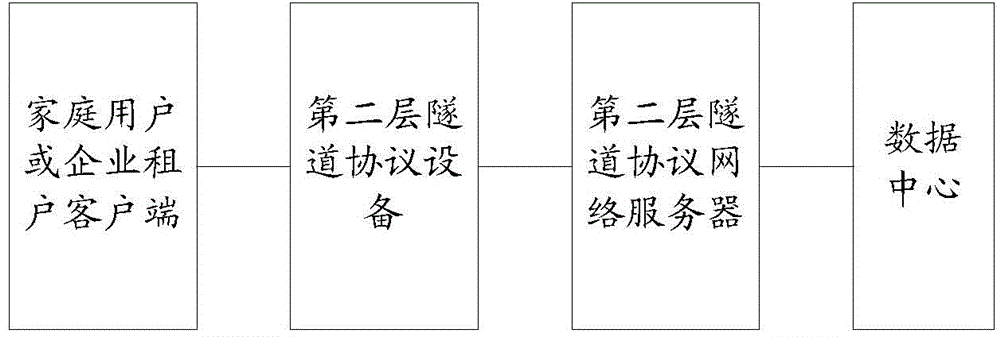
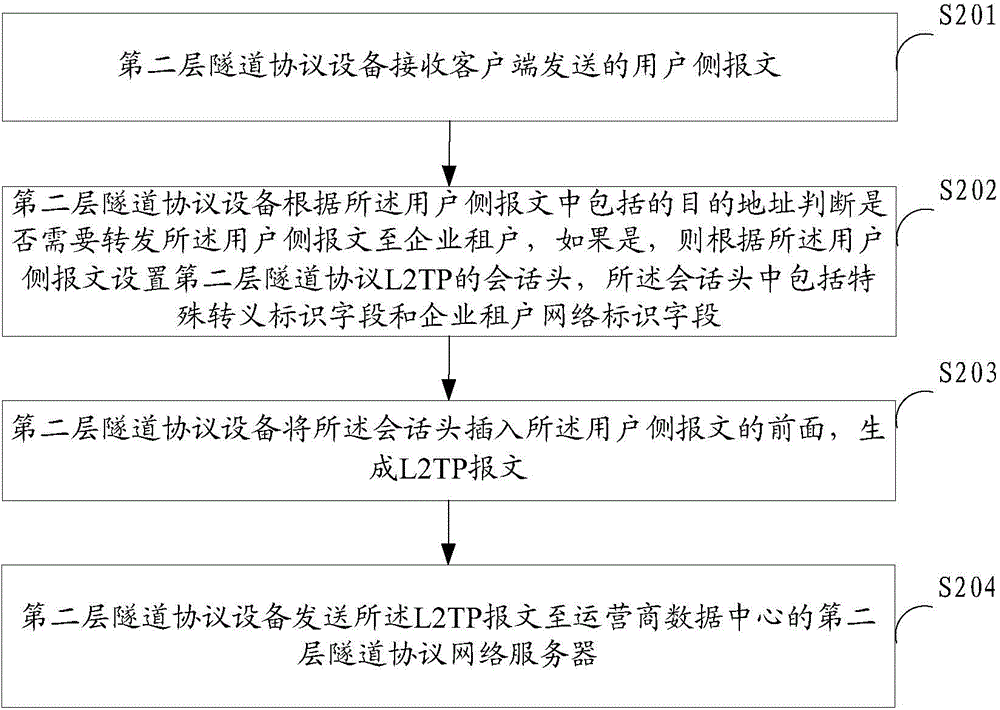
ActiveCN104954333ADoesn't cause MTU issuesObvious advantagesNetworks interconnectionData centerClient-side
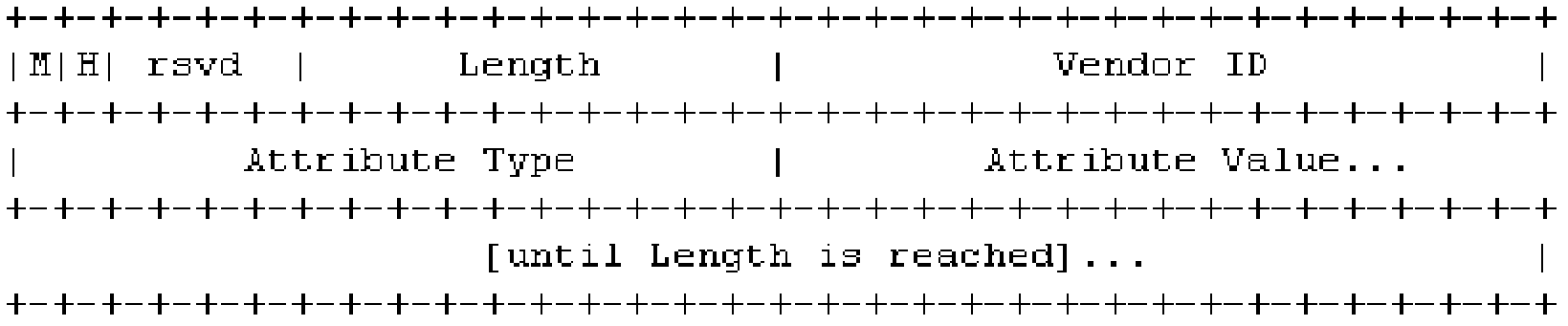
The present invention is applied to the field of cloud computing, and provided are a packet forwarding method and system. The method comprises: receiving, by a layer 2 tunneling protocol device, a user-side packet sent by a client; according to a destination address contained in the user-side packet, judging, by the layer 2 tunneling protocol device, whether the user-side packet is required to be forwarded to an enterprise tenant, and if so, setting a session header of a layer 2 tunneling protocol (L2TP) according to the user-side packet, the session header comprising a special escaped identifier field and an enterprise tenant network identifier field; inserting, by the layer 2 tunneling protocol device, the session header in the front of the user-side packet so as to generate an L2TP packet; and sending, by the layer 2 tunneling protocol device, the L2TP packet to a layer 2 tunneling protocol network server of an operator data centre. The present invention will not bring an additional data header, and will not cause an MTU problem of a network device, so that the advantage caused by an escape action is obvious.
Owner:HUAWEI TECH CO LTD
L2TP-based (layer 2 tunneling protocol based) wireless access system and interaction method thereof
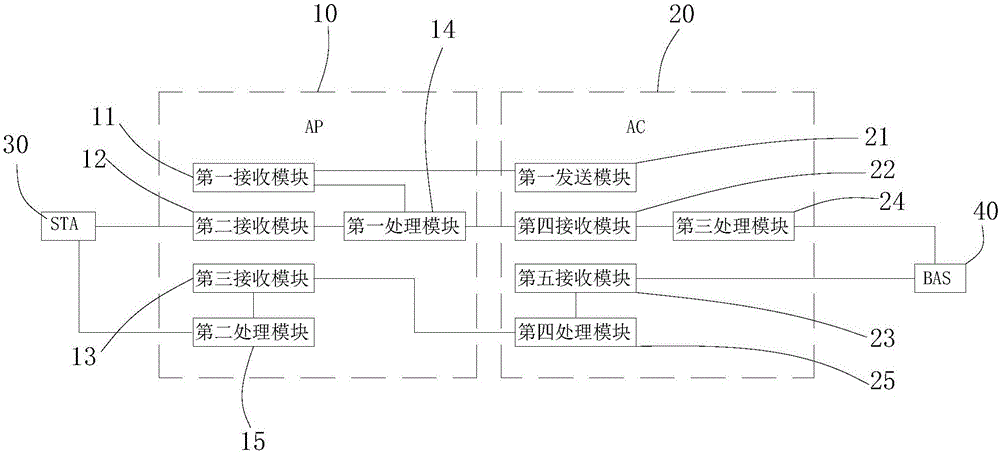
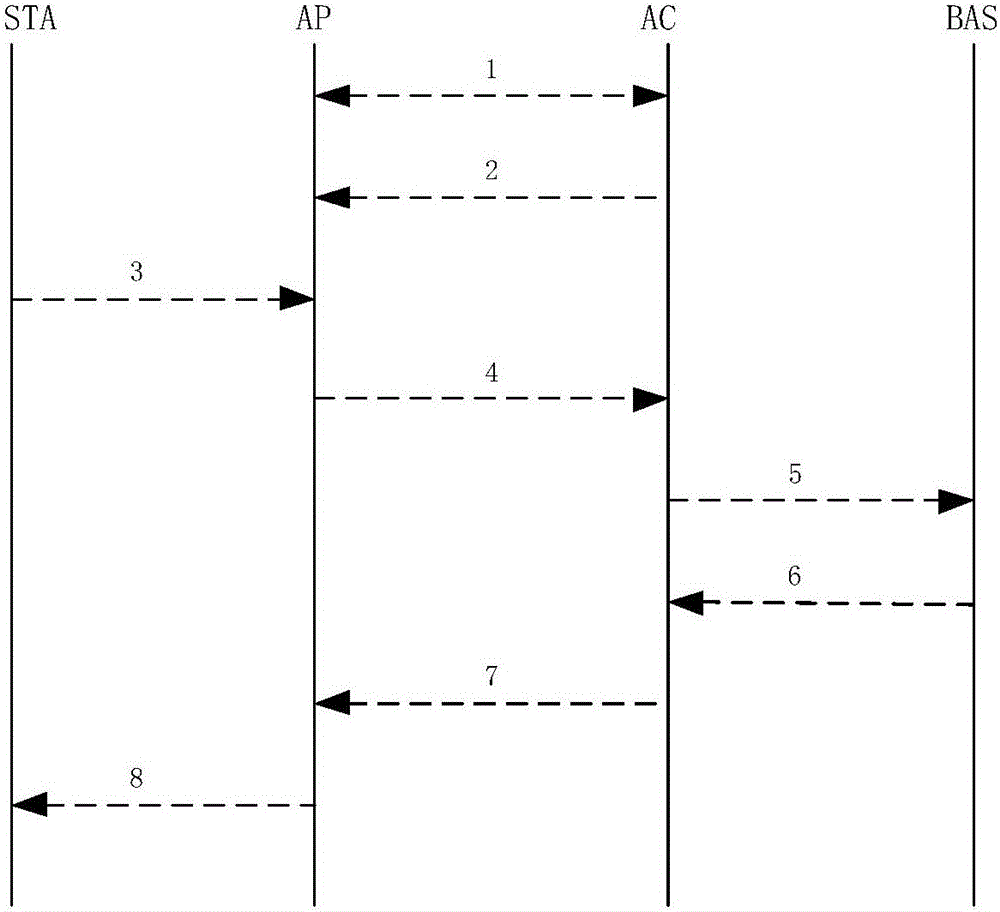
InactiveCN106793013ARealize data interactionReduce overheadAssess restrictionData switching networksThe InternetBroadband
The invention relates to an L2TP-based (layer 2 tunneling protocol based) wireless access system and an interaction method thereof; the interaction method comprises the steps of allowing a wireless access point to join a wireless access controller through internet; allowing the wireless access controller to issue a wireless local area network configuration and L2TP tunnel configuration to the wireless access point; allowing a wireless client which is online to transmit a data message to the wireless access point; allowing the wireless access point to package the data message and transmit to the wireless access controller; allowing the wireless access controller to unpackage the packaged data message, and transmit to a broadband access server of an extranet device by means of layer 2 forwarding; allowing the broadband access server of the extranet device to return a message of Ethernet frame to the wireless access controller; allowing the wireless access controller to find a path of the wireless client through a port mapping table, perform L2TP layer 2 tunnel packaging on the message and transmit to the wireless access point; allowing the wireless access point to unpackage the packaged message and forward to the wireless client. The standard L2TP is used herein to allow data interaction among the STA (station), AP (access point), AC (access controller) and BAS (broadband access server), with good compressing and encrypting properties and low cost.
Owner:SHENZHEN GRENTECH CORP LTD
Virtual private network access method and device for mobile user
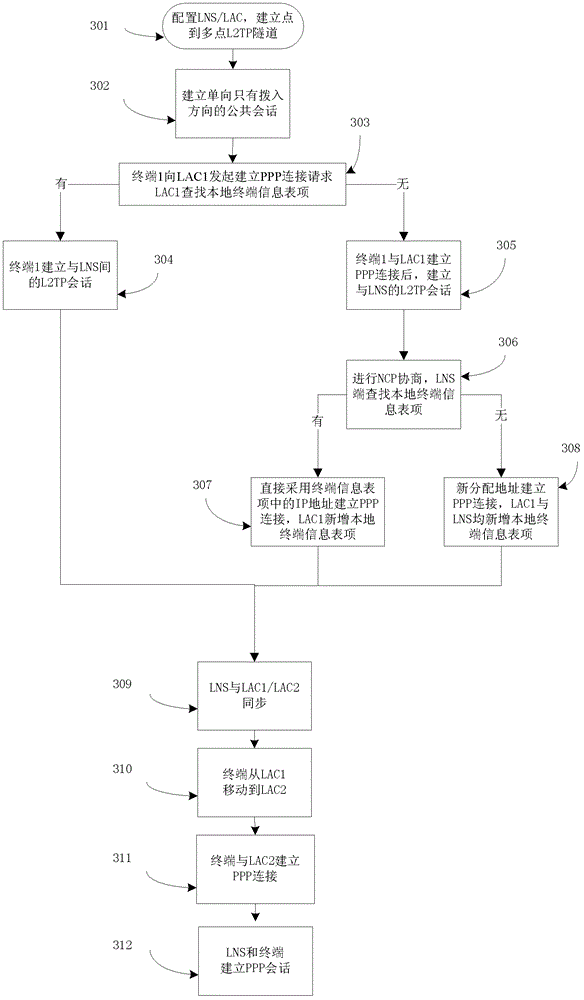
ActiveCN102724767AQuick buildAvoid long interruptionsConnection managementNetworks interconnectionAccess methodPrivate network
The invention discloses a virtual private network access method and a virtual private network access device for a mobile user. The method and the device support the mobile user to access the virtual private network. The method comprises the following steps of: establishing a permanent layer 2 tunneling protocol (L2TP) channel between an L2TP network server (LNS) and a first L2TP access concentrator (LAC), and also establishing the permanent L2TP channel between the LNS and a second LAC in an LAC active initiation way; establishing a public session and synchronizing the second LAC after an L2TP session between a terminal and the first LAC is established; and when the terminal moves from a first LAC network into a second LAC network, rapidly accessing the LNS and establishing the L2TP session without changing an Internet protocol (IP) address of the terminal. The LACs and the LNS are provided with a terminal information table entry and a revocation timer, the LNS is also provided with a message synchronization device for conveniently realizing LAC information synchronization. By the method and the device, the terminal can access the virtual private network by using the same IP address when the terminal moves, so that all service applications based on network IP and network rights are not changed during roaming.
Owner:NEW H3C TECH CO LTD
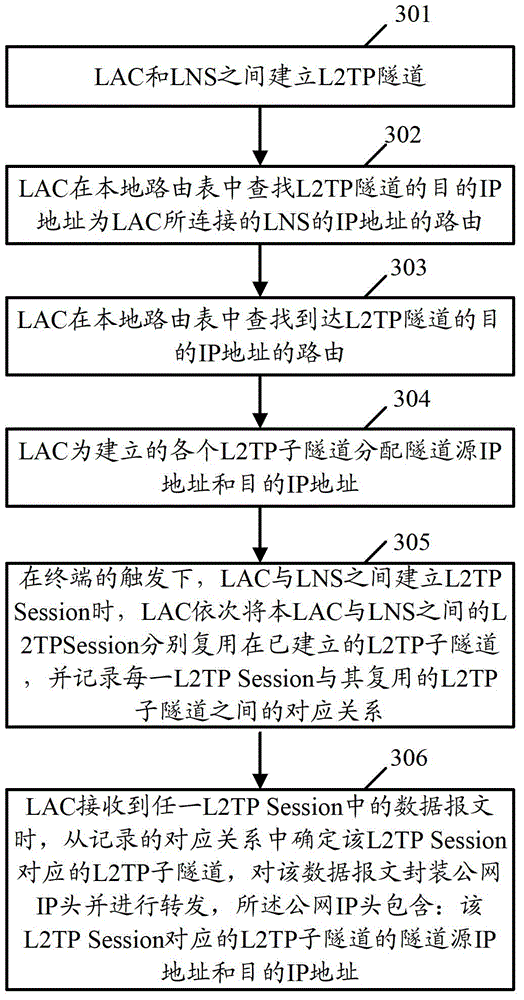
Method and device for sharing load of data message used for L2TP (layer 2 tunneling protocol) networking
ActiveCN102752221AReasonable use of bandwidthIncrease profitNetworks interconnectionIp addressPublic network
The invention provides a method and a device for sharing the load of data message used for L2TP (layer 2 tunneling protocol) networking. The method comprises the following steps: an LAC (L2TP access concentractor) establishes L2TP subtunnels which are subordinate to an L2TP main tunnel together with an LNS (L2TP network server) according to the number of target IP addresses reached the L2TP main tunnel, allocates tunnel source IP (internet protocol) addresses and tunnel target IP addresses to each L2TP subtunnel and multiplexes the L2TP sessions between the LAC and the LNS in sequence on the established subtunnels respectively; the LAC determines the L2TP subtunnels on which the L2TP sessions are multiplexed when receiving the data message in any one L2TP session, packages and forwards public network IP heads for the data message to avoid the congestion due to too heavy load of a part of links, wherein the packaged public network IP heads comprise the tunnel source IP addresses and the tunnel target IP addresses of the L2TP subtunnels on which the L2TP sessions are multiplexed.
Owner:XINHUASAN INFORMATION TECH CO LTD
Method for accessing private network through layer 2 tunneling protocol and server
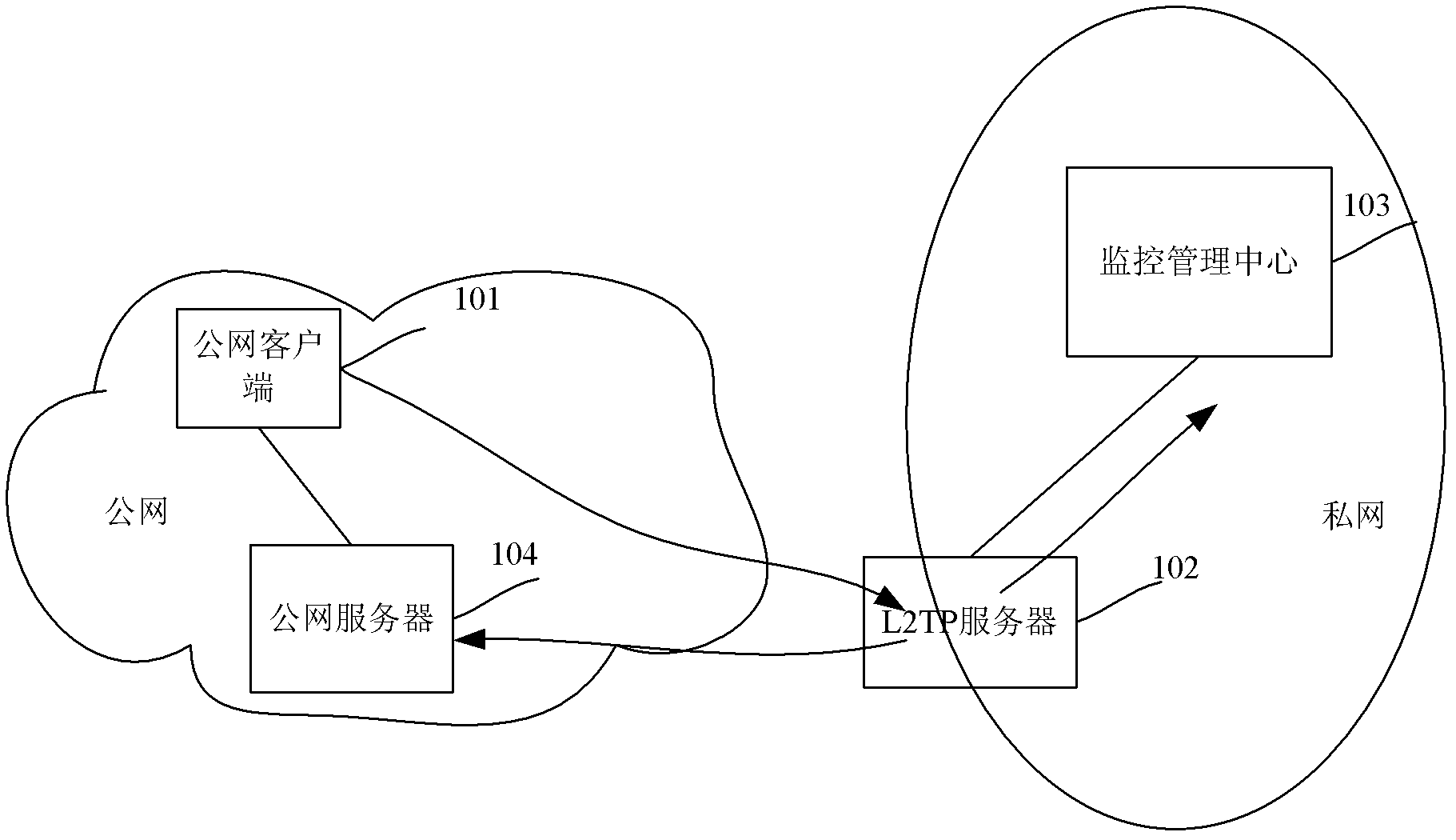
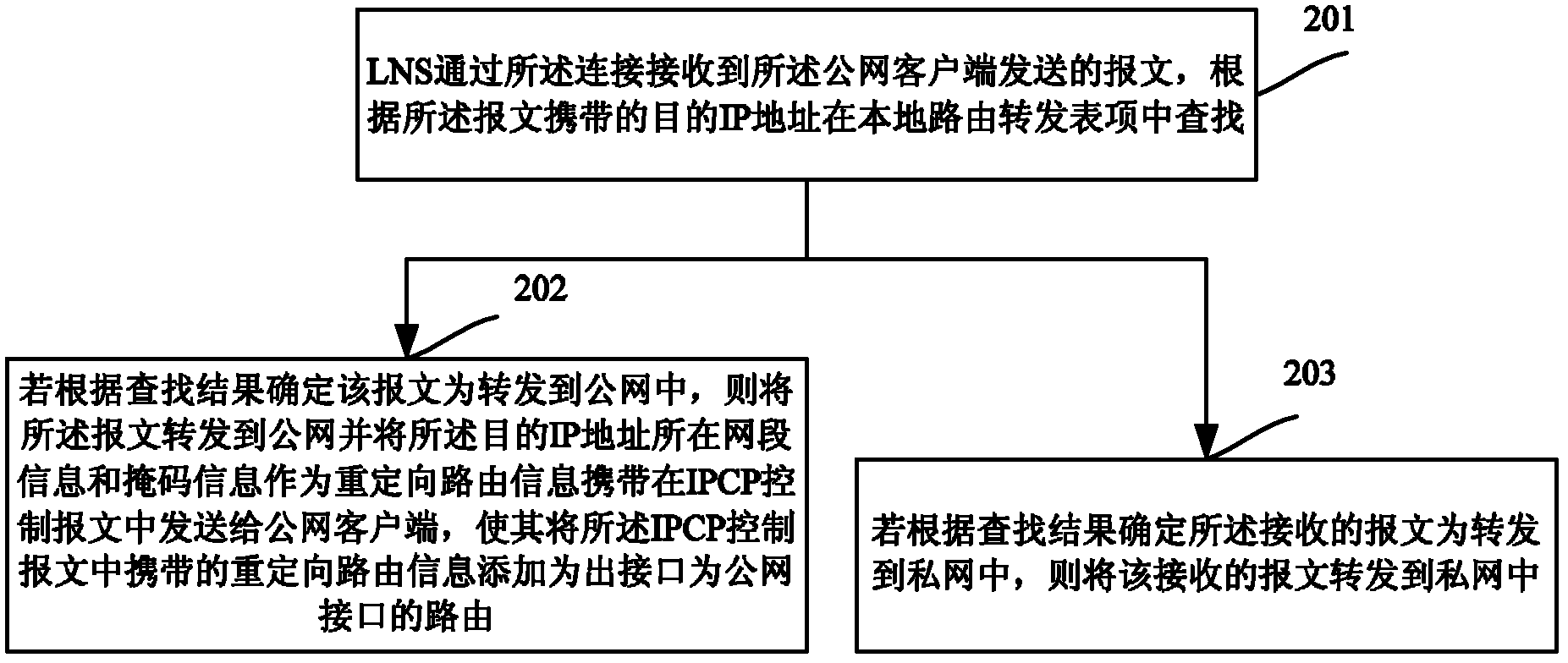
The invention discloses a method for accessing a private network through a layer 2 tunneling protocol, which includes that: when receiving message sent by a public network client side and needing to be transmitted into the public network, a lonworks network server (LNS) sends a network segment where a target address carried by the message locates in and mask information to the public network client side, and the public network client side adds corresponding redirection route information in a route with an output interface as an interface of the public network, wherein network segment information and the mask information serve as redirection route information. Based on the same concept, the invention further provides a server. By aid of the server, on the basis of not affecting private network accessing of the public network client side, the public network client side can access the public network conveniently without performing any manual configuration.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com