Method and device for enabling third generation (3G) user to safely access to network
A security access and network technology, applied in the field of 3G network, can solve problems such as reducing network access security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
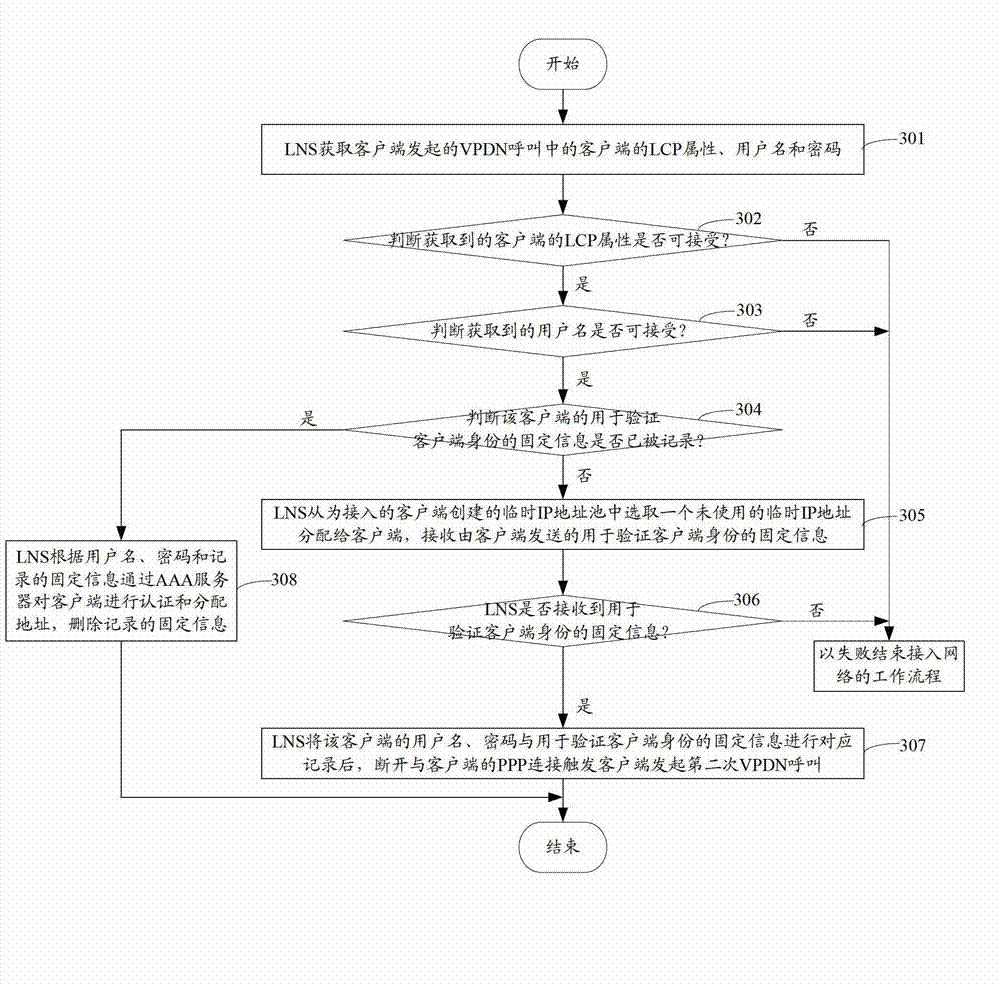
[0062] see image 3 , the present embodiment realizes the safe access network of 3G users through the mode of two-time dialing, and the specific working process includes the following steps:
[0063] Step 301: The LNS acquires information such as the LCP attribute, user name and password of the client in the VPDN call initiated by the client.
[0064] In this step, the VPDN call initiated by the client for the first time is actually completed through the LAC, specifically:
[0065] The client initiates a PPP connection establishment request to the LAC for Point-to-Point Protocol (PPP) LCP negotiation and authentication; when the LAC negotiates and authenticates the client, the LAC initiates a VPDN tunnel establishment request to the LNS. After the tunnel is established, the LAC sends the client The LCP attribute and user name of the client are sent to the LNS, and the LNS authenticates the client through the AAA server.
[0066] Step 302: Judging whether the acquired LCP att...
Embodiment 2
[0092] see Figure 5 , the present embodiment realizes the safe access network of 3G users by dialing once and performing PPP IPCP negotiation again, and the specific work flow includes:
[0093] Step 501: The LNS acquires information such as the LCP attribute, user name and password of the client in the VPDN call initiated by the client.
[0094] Same as step 301, in this step, the VPDN call initiated by the client for the first time is also completed through the LAC, specifically:
[0095] The client initiates a PPP connection establishment request to the LAC for PPP LCP negotiation and authentication. After the LAC negotiates and authenticates the client, the LAC initiates a VPDN tunnel establishment request to the LNS. After the tunnel is established, the LAC sends the client's PPP LCP and user name , password and other information to the LNS, and the LNS authenticates the client through the AAA server.
[0096] Step 502: Judging whether the acquired LCP attribute of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com