Business access method and device based on Layer 2 Tunneling Protocol (L2TP)
A layer-2 tunneling protocol and service access technology, which is applied in the field of service access methods and devices based on the layer-2 tunneling protocol, can solve problems such as increasing the burden on LNS, increasing access delay, and occupying the egress bandwidth of the enterprise network, so as to improve the online experience , Improve utilization and reduce delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] In order to make the object, technical solution and advantages of the present invention clearer, the solutions of the present invention will be further described in detail below with reference to the accompanying drawings and examples.
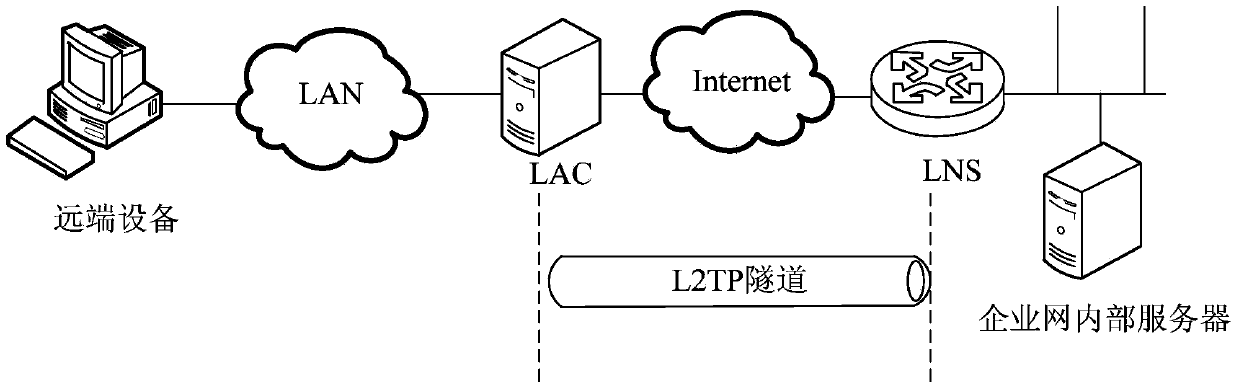
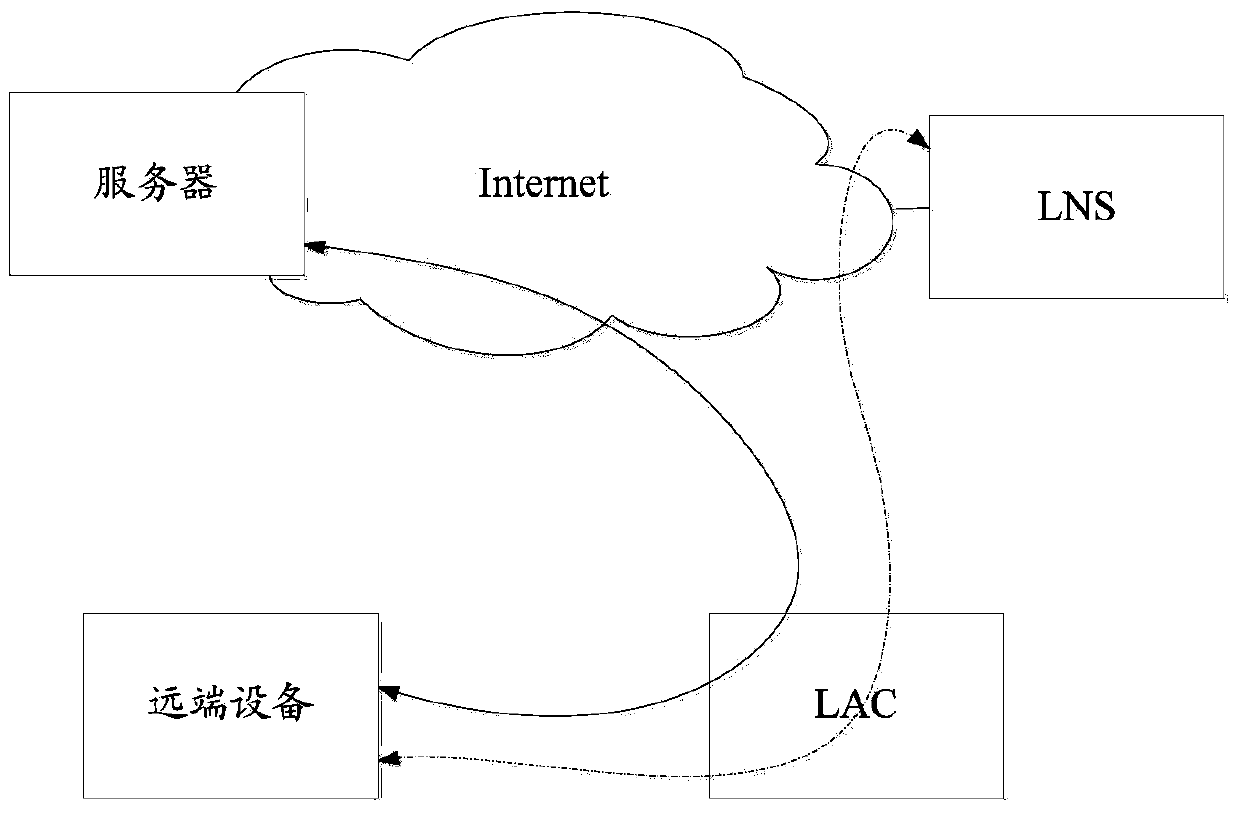
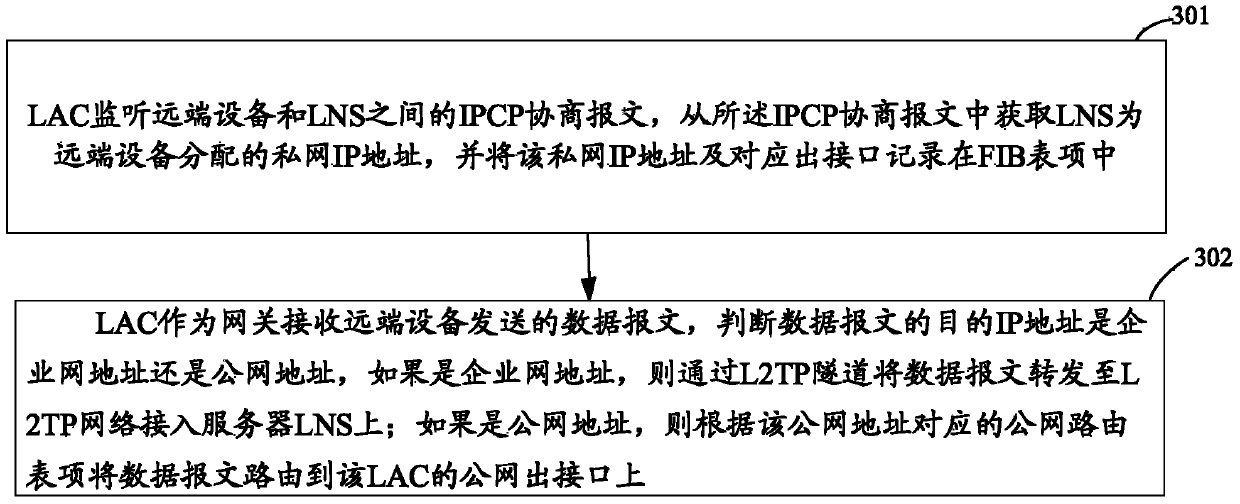
[0017] The main purpose of the present invention is to realize the distribution of user access Internet traffic on the LAC device of the public network, so the setting is mainly based on the LAC device. When processing the data packets of the remote device on the LAC device, before entering the L2TP tunnel, the destination IP address of the data packets is pre-judged, and the different IP addresses are differentiated and processed. In this way, the data packets whose destination IP address is the public network address are directly forwarded to the public network server on the public network outbound interface, and the data packets whose destination IP address is the private network address of the enterprise network are still forwarded t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com