Method for simulating L2TP dialing
A technology of virtual private dial-up and router, which is applied in the direction of data exchange through path configuration, digital transmission system, electrical components, etc. It can solve problems such as difficulties, no composite application, and inability to meet the situation when a large number of users access at the same time, to achieve The effect of solving technical problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Hereinafter, the method for simulating L2TP dialing in the present invention will be described in detail with reference to accompanying drawings 1-5.
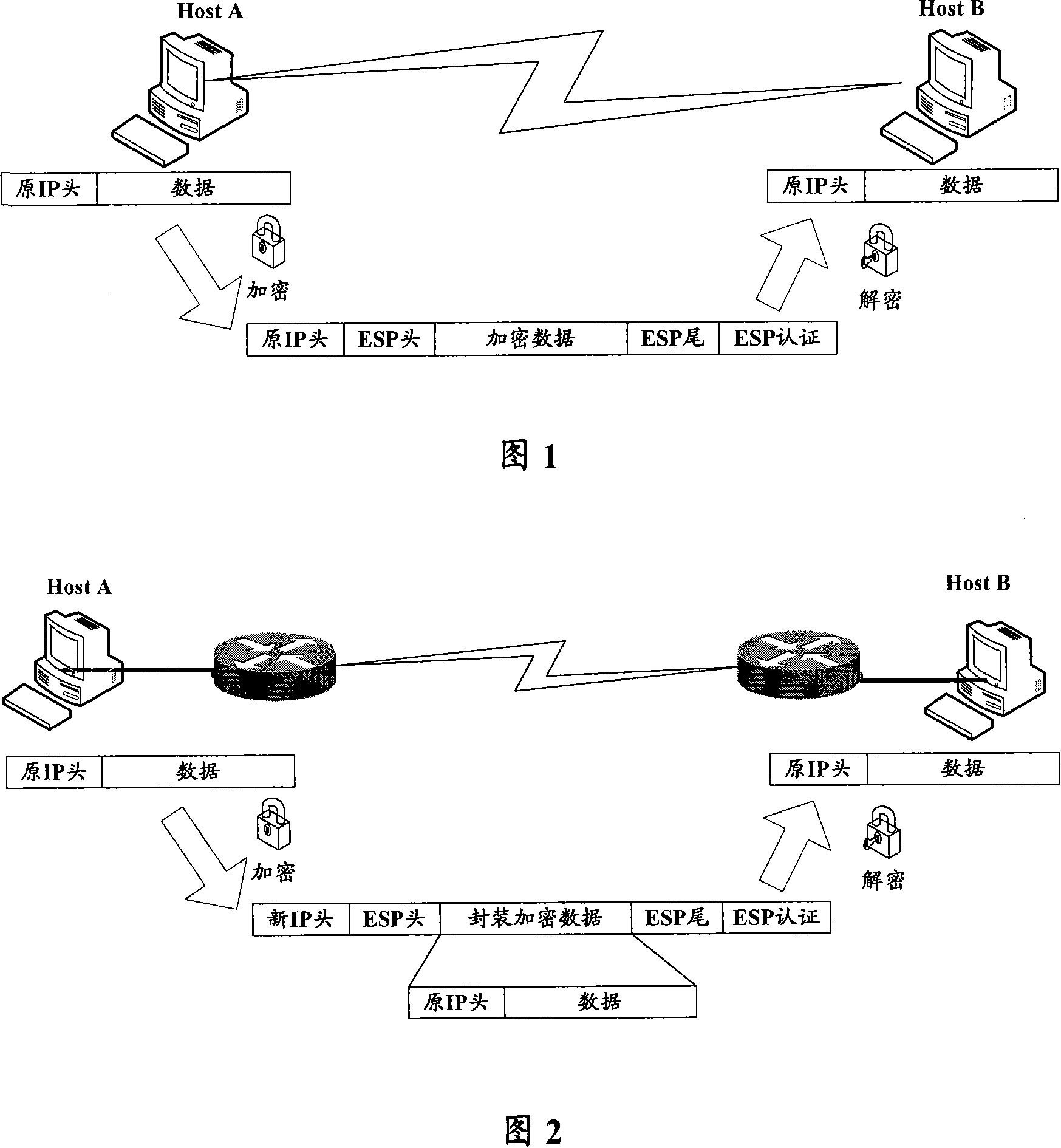
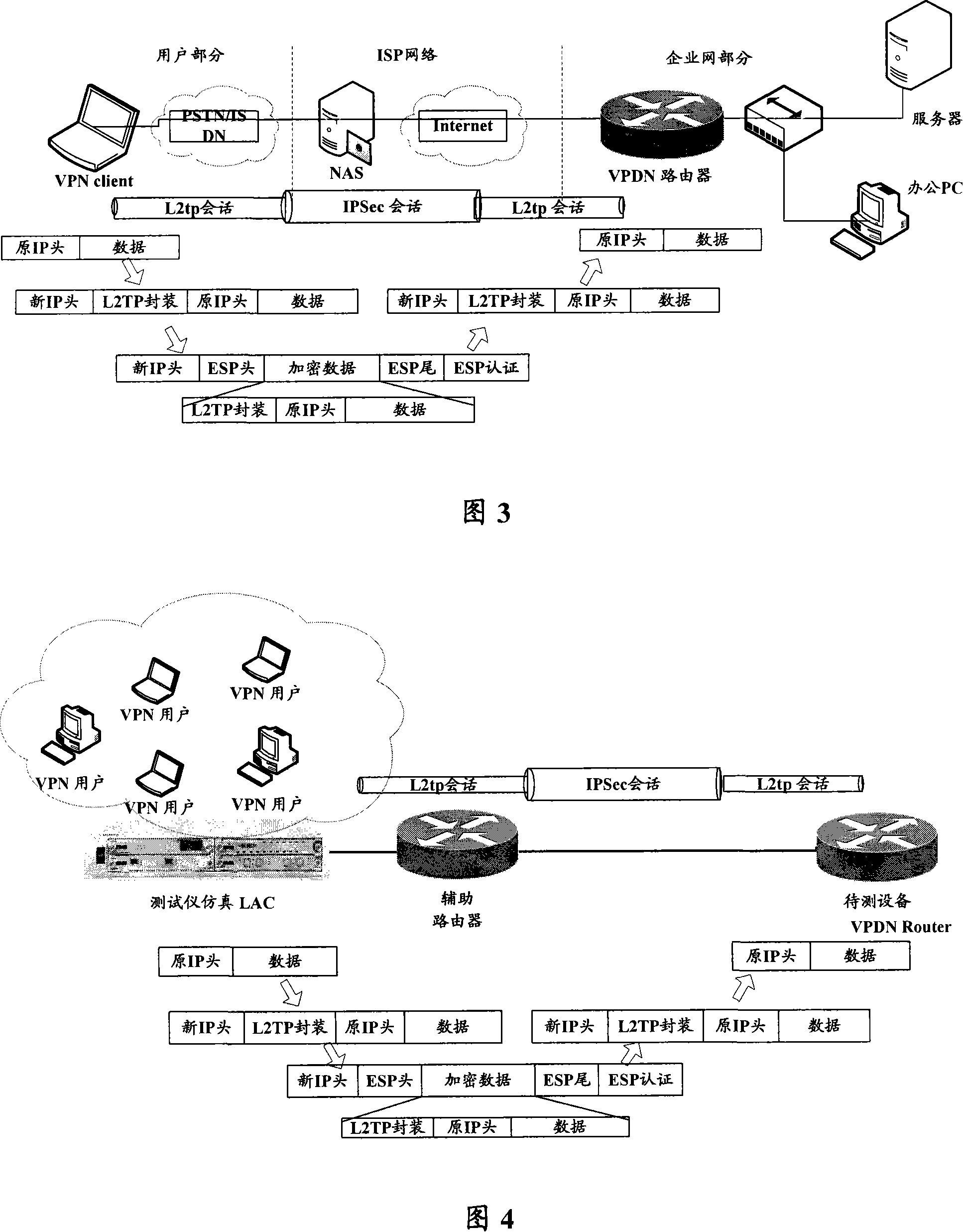
[0029] The core idea of the present invention is: use test meter to simulate L2TP user access, add high-performance router in front of test meter to do the encryption processing of IPSec tunnel mode to the message of L2TP type that test meter sends, the message through processing like this, for For the router to be tested, it is equivalent to that the PC user directly initiates access through the IPSec-based L2TP policy, which is almost the same as the actual application scenario.
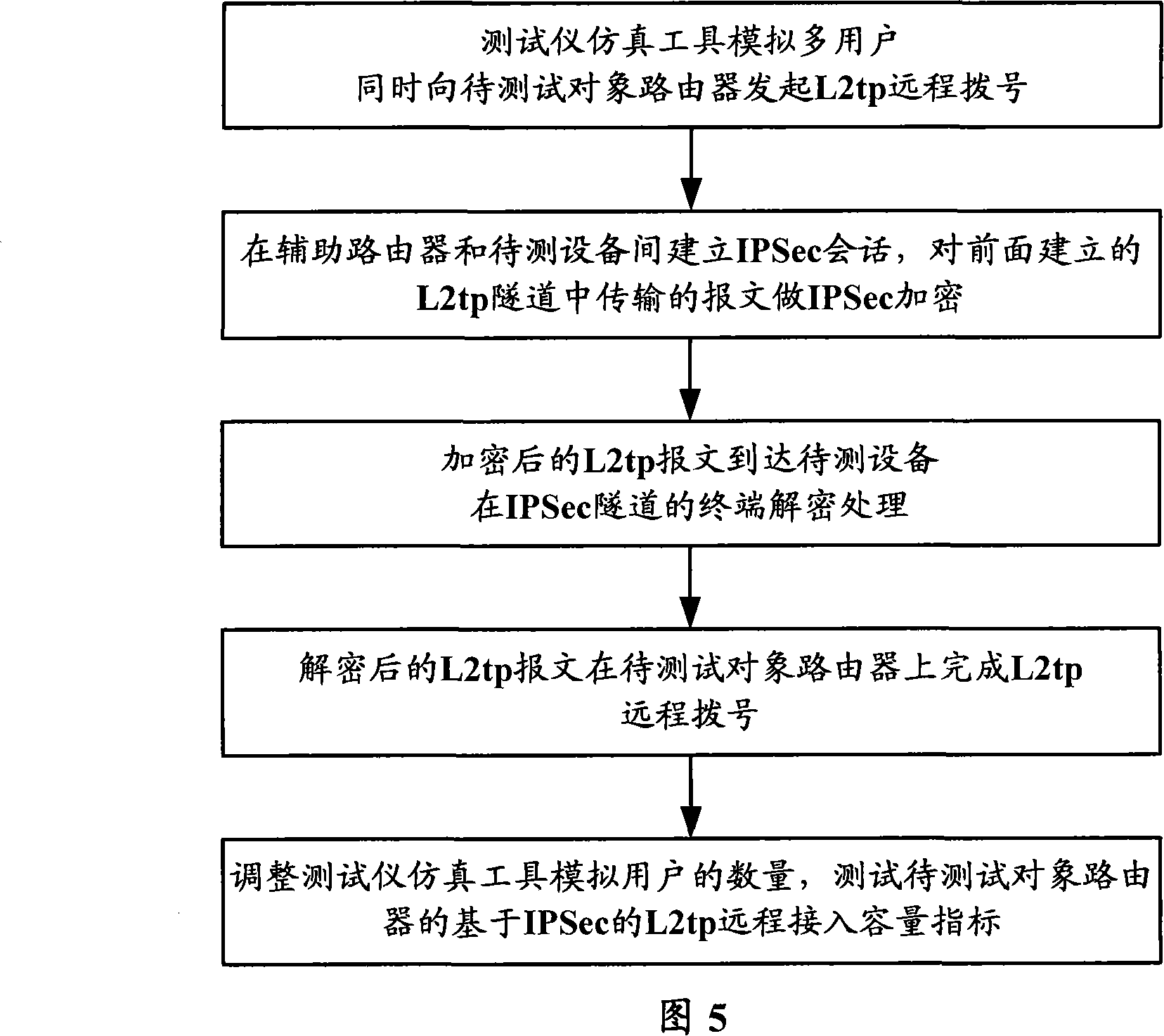
[0030] Since the test instrument can simulate the access of a large number of L2TP users, and the IPSec encryption processing performance of the auxiliary test router is better than that of the device under test, so as to achieve the purpose of testing the IPSec-based L2TP service limit index of the router. As shown in FIG. 4 , it is a sche...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com