Method, device and ERP (enterprise resource planning) system for user identity and permission validation
An ERP system and user identity technology, which is applied in transmission systems, data processing applications, electrical components, etc., can solve the problems that cannot be realized without the role of ERP system, and mutual login between ERP system and external systems cannot be satisfied, so as to improve performance and the effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] figure 1 The flow of the method for verifying user identity and authority provided by the embodiment of the present invention is shown, and the details are as follows:
[0040] In step S101, identity verification information input by a user is received.
[0041] In the embodiment of the present invention, the identity verification information input by the user is first received, and the identity verification information includes user identification, user name, user password, etc., wherein the user identification may be a user ID, but is not limited to the user ID.
[0042] In step S102, when the identity verification information matches the corresponding user information pre-stored in the user table, a statement is issued, and the statement includes authority verification information.
[0043] In the embodiment of the present invention, a user table may be used to store user information. The user information includes, but is not limited to, the user's username, user i...
Embodiment 2
[0055] In the embodiment of the present invention, authorization verification is divided into three types, which are function authorization verification, field authorization verification and data authorization verification. According to different permission verification types. The permission verification information is different from the permission object. Each will be described in detail below.
[0056] 1. Function authority verification and field authority verification.
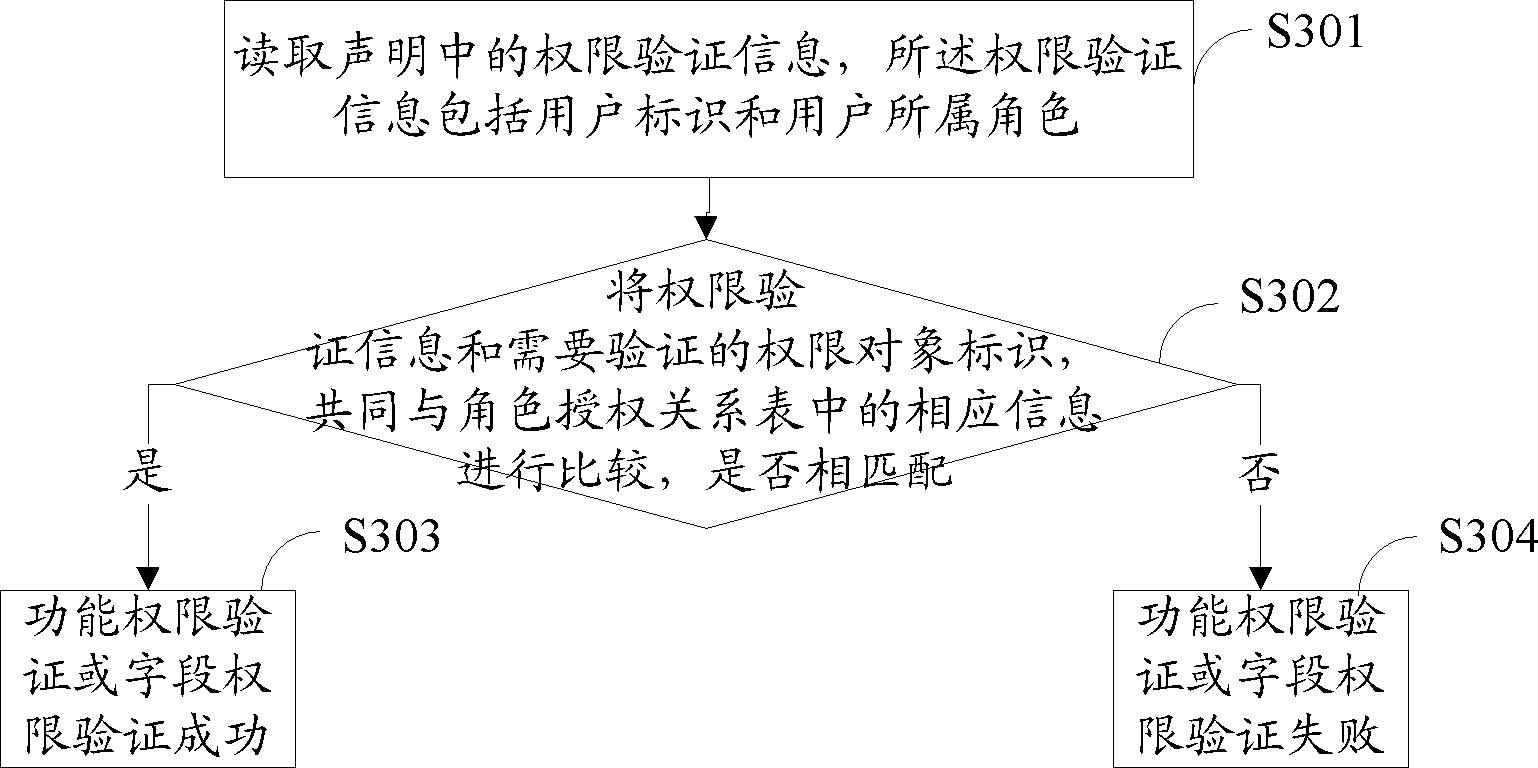
[0057] In the embodiment of the present invention, the methods for verifying function rights and field rights are basically the same. image 3 Shows the detailed flow of function permission verification and field permission verification.
[0058] In step S301, the authority verification information in the statement is read, and the authority verification information includes the user ID and the role to which the user belongs.
[0059] In the embodiment of the present invention, the authority verificatio...
Embodiment 3
[0077] Figure 5 The structure of the user identity and authority verification device provided by the embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown. The device can be a software unit, a hardware unit, or a combination of software and hardware built into the ERP system, or integrated into the ERP system or the application system of the ERP system as an independent pendant. in:
[0078] The identity verification information receiving module 51 is configured to receive the identity verification information input by the user.
[0079] In the embodiment of the present invention, the identity verification information includes a user ID (a user ID is used as an example here, but not limited to a user ID), a user name, a user password, and the like.
[0080] The statement issuing module 52, when the identity verification information received by the identity verificatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com