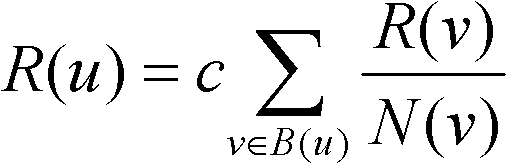Detection method for phishing site
A phishing website and detection method technology, applied in the transmission system, electrical components, etc., can solve the problems of high false negative rate of detection and easy bypass of phishing website detection, and achieve the effect of increasing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in detail below through specific embodiments and accompanying drawings.
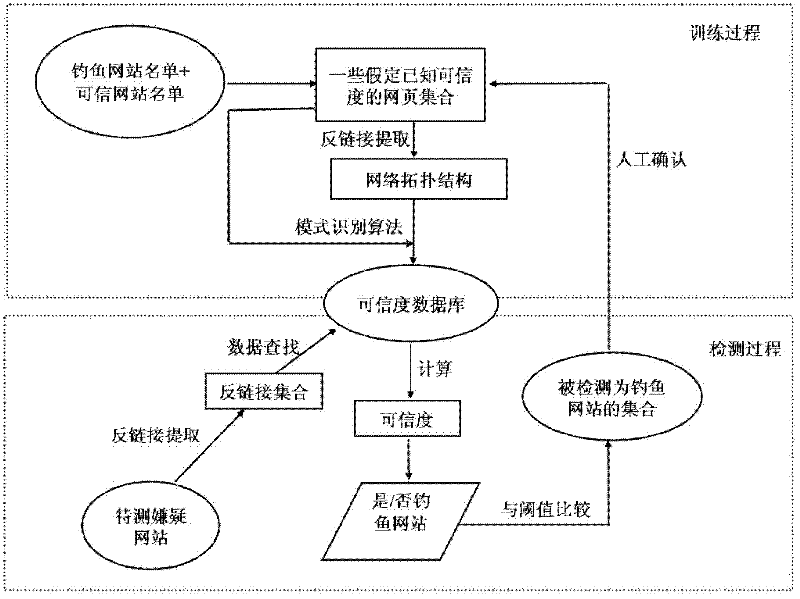
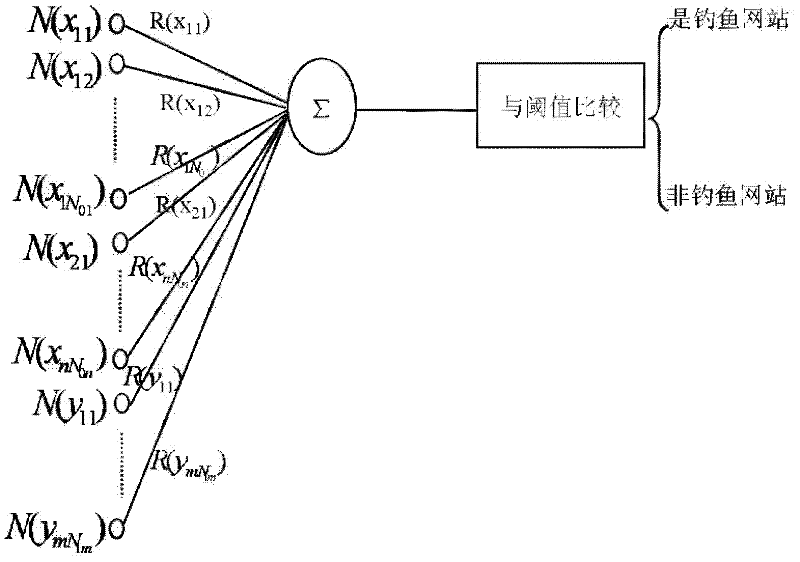
[0031] figure 1 It is a flow chart of the method for detecting a phishing website in this embodiment. The method can be divided into two stages: training process and detection process. In the training process stage, the credibility database is mainly established, and in the detection process stage, the detection of suspected websites is mainly completed. The method mainly includes three steps: extracting the network structure according to the seed set, obtaining the credibility database according to the pattern recognition method, and detecting phishing websites according to the credibility database. The specific implementation methods of the three steps are described below.
[0032] 1) Extract the network structure according to the seed set
[0033] Since the credibility and topology of the entire network are not known at the beginning, it is necessary to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com