Method and device for controlling access request on basis of proxy gateway
An access request, proxy gateway technology, applied in the field of communication, can solve problems such as attacks and data cannot be processed, achieve flexible protection measures, improve security and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
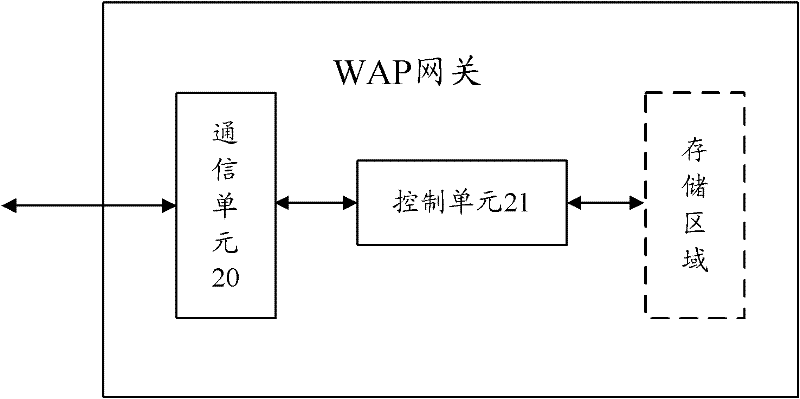
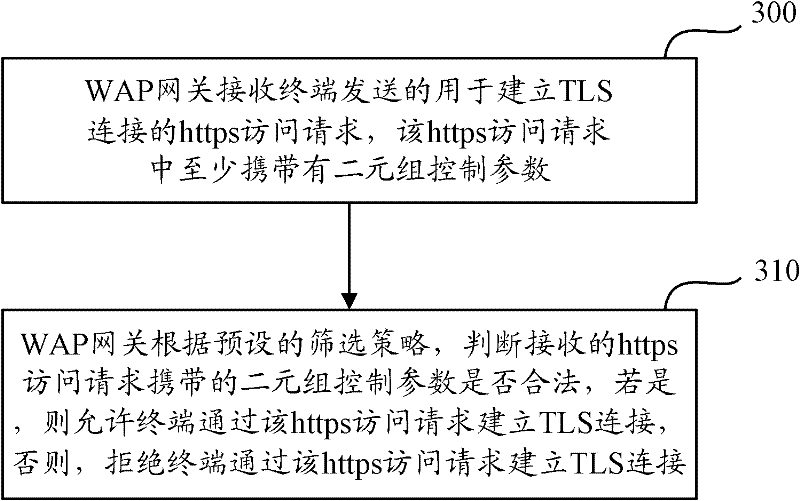
[0018] In order to realize the control of the proxy gateway to the Https access request, prevent the terminal from performing abnormal operations on the proxy gateway through the TLS tunnel, thereby improving the security of the proxy gateway application system, in the embodiment of the present invention, the proxy gateway receives the terminal to establish a TLS connection. https access request, the https access request carries at least a 2-tuple control parameter, and the proxy gateway judges whether the 2-tuple control parameter carried by the received https access request is legal according to the preset screening strategy, and if so, allows the terminal Establish a TLS connection through the https access request; otherwise, reject the terminal to establish a TLS connection through the https access request.
[0019] In the embodiment of the present invention, the so-called proxy gateway can be a WAP gateway or a WEB gateway, and the so-called two-tuple control parameter can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com