Data encryption method and system
A data encryption and data technology, applied in the computer field, can solve the problem of low data security in cloud storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
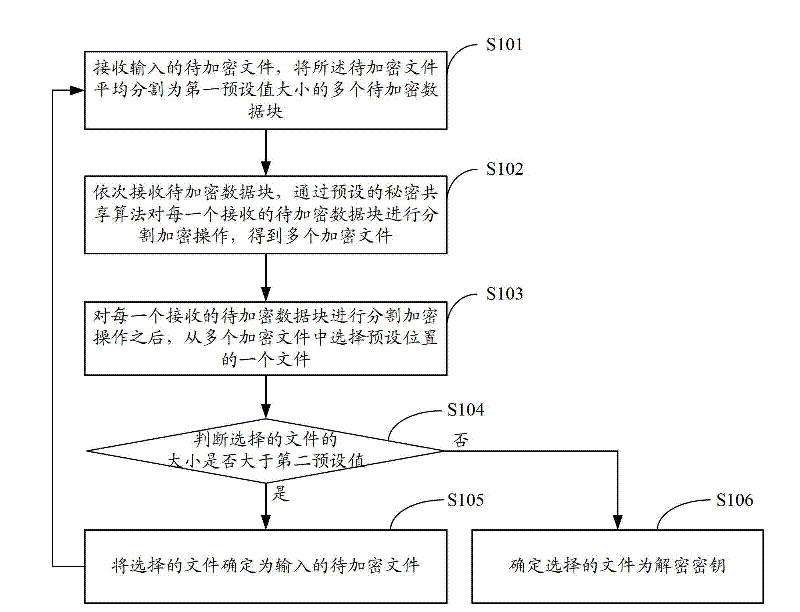
[0027] figure 1 The implementation flow of the data encryption method provided by Embodiment 1 of the present invention is shown, and the details are as follows:
[0028] In step S101, an input file to be encrypted is received, and the file to be encrypted is evenly divided into a plurality of data blocks to be encrypted with a size of a first preset value.
[0029] In the embodiment of the present invention, when the input file to be encrypted is received, in order to improve the encryption speed of the file, the file to be encrypted is evenly divided into a plurality of data blocks to be encrypted with the size of a first preset value, and the preset value can be Set according to the hardware configuration of the encryption platform, which can be 256, 1024, etc. For example, when the first preset value is 256, the file to be encrypted is divided into multiple data blocks to be encrypted with a size of 256 bytes.
[0030] In the specific implementation process, the size of t...
Embodiment 2
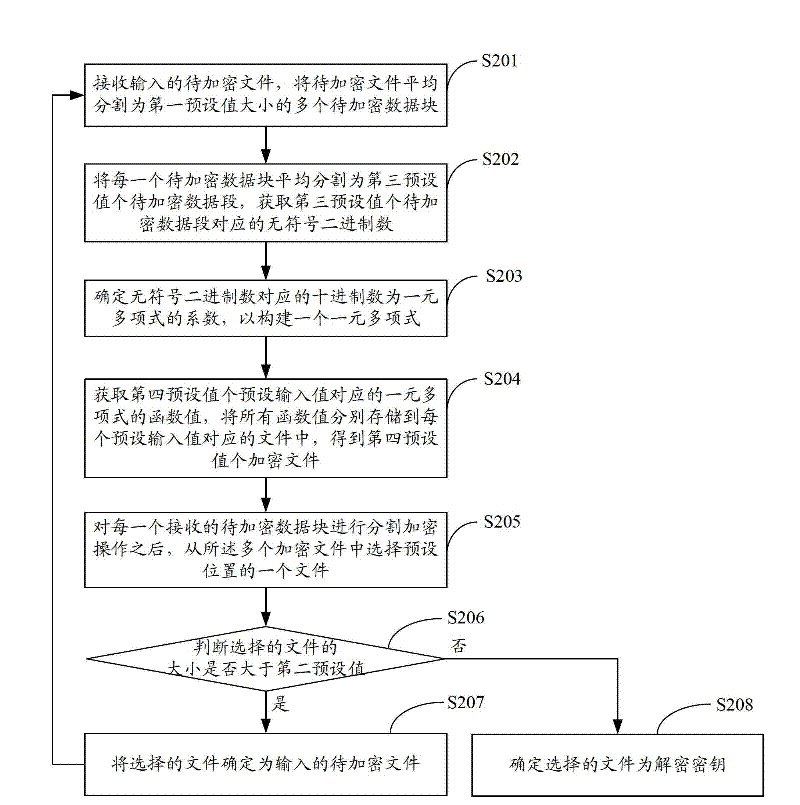
[0041] In the embodiment of the present invention, each received data block to be encrypted is segmented and encrypted by using the unary polynomial solution principle, thereby simplifying the data encryption process and increasing the encryption speed.
[0042] figure 2 The implementation flow of the data encryption method provided by Embodiment 2 of the present invention is shown, and the details are as follows:
[0043] In step S201, an input file to be encrypted is received, and the file to be encrypted is equally divided into a plurality of data blocks to be encrypted with a size of a first preset value.
[0044] In step S202, each data block to be encrypted is equally divided into a third preset value of data segments to be encrypted, and an unsigned binary number corresponding to the third preset value of data segments to be encrypted is obtained.
[0045] In the embodiment of the present invention, the data blocks to be encrypted are received sequentially, and a spli...
Embodiment 3
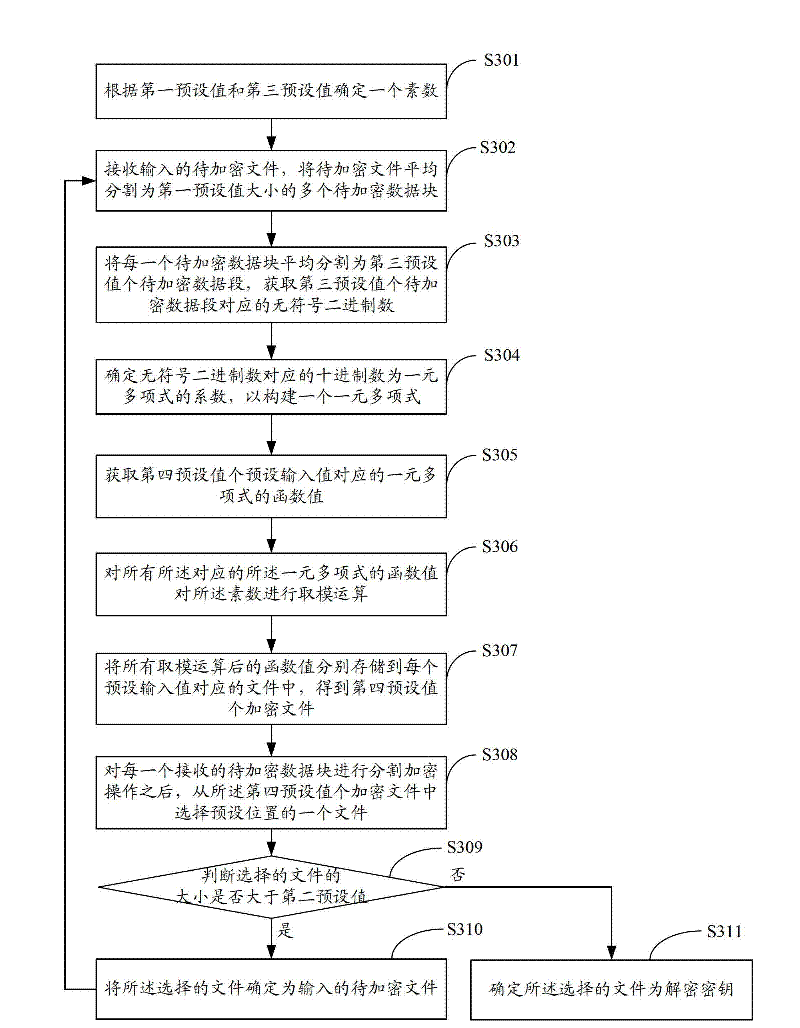
[0062] image 3 The implementation process of the data encryption method provided by Embodiment 3 of the present invention is shown, and the details are as follows:
[0063] In step S301, a prime number is determined according to the first preset value and the third preset value.
[0064] In the implementation of the present invention, in order to facilitate the preservation of the function value of the unary polynomial in the partition encryption process, a sufficiently large prime number needs to be determined in advance, and the function value of the unary polynomial is used to perform a modulo operation on the prime number to obtain a value within the range of the prime number , so as to facilitate the processing and storage of data, and prevent the occurrence of abnormal events in the process of saving function values. Specifically, a prime number can be determined according to the size of a plurality of data blocks to be encrypted when the file to be encrypted is evenly...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com