A method, device and system for realizing network identification conversion
A network identification and identification technology, applied in the field of communication, can solve the problems of network development restrictions, private network IP addresses cannot be repeated, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
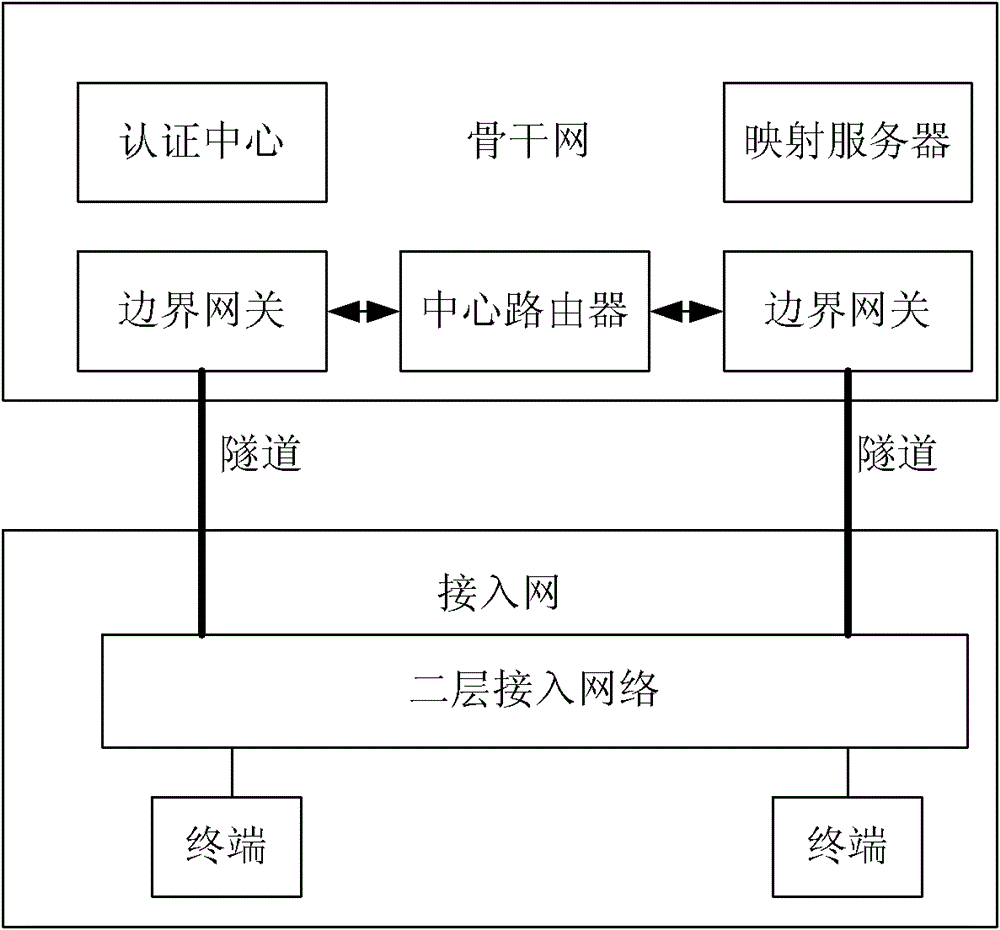
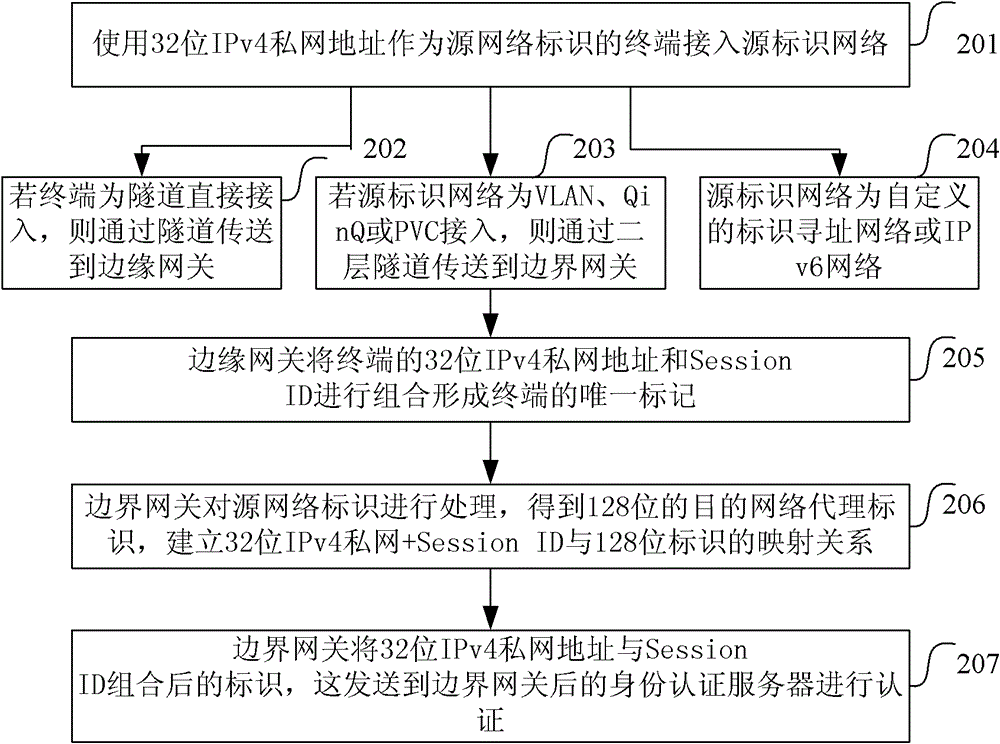
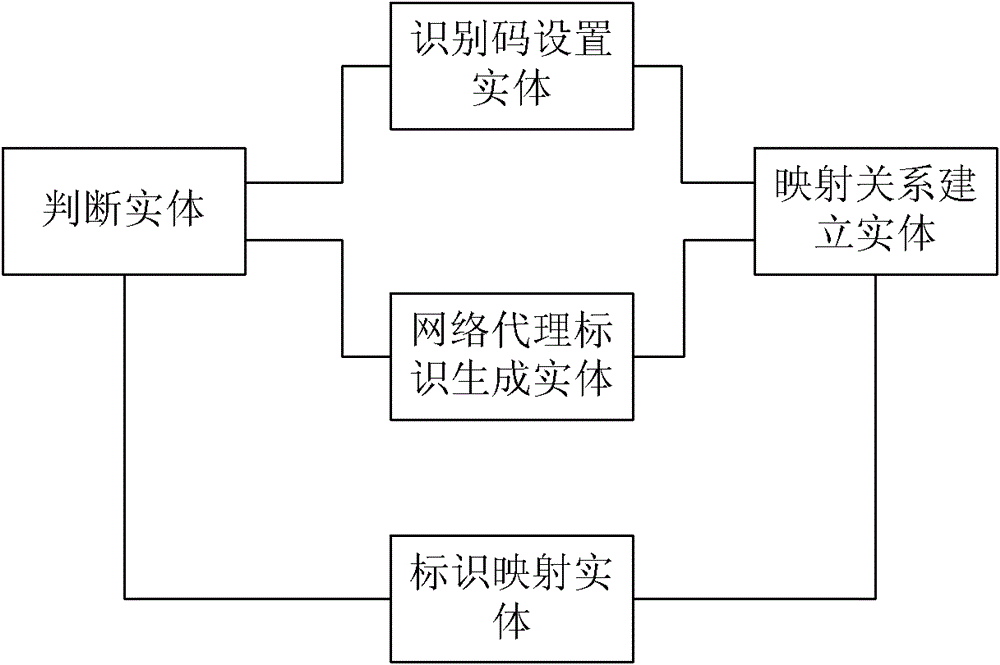
[0045] In this embodiment, the border gateway sets a proxy ID for the routing and forwarding network, that is, the destination network proxy identifier (P-RID), and identifies the terminal through the double identifier of the source network identifier plus the Session ID (session identifier), and establishes the source network identifier+ The mapping from the Session ID to the target network proxy ID provides the basis for the border gateway to obtain the target network location ID based on the target network proxy ID, and can realize the reuse of the source network ID.
[0046] In this embodiment, when the terminal moves, the P-RID remains unchanged and the RID changes. The P-RID is regarded as the proxy identifier of the RID in the access network. In this embodiment, the mapping relationship between the terminal identification code and the P-RID is established information, the edge gateway can obtain the corresponding P-RID according to the identification code of the terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com