Authentication method, equipment and system
An identity verification method and identity verification technology, which is applied in the direction of user identity/authority verification, etc., can solve problems such as complex operations and manual input information security defects, and achieve the effect of simplifying operating procedures, avoiding cumbersome operations and security vulnerabilities, and ensuring matching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
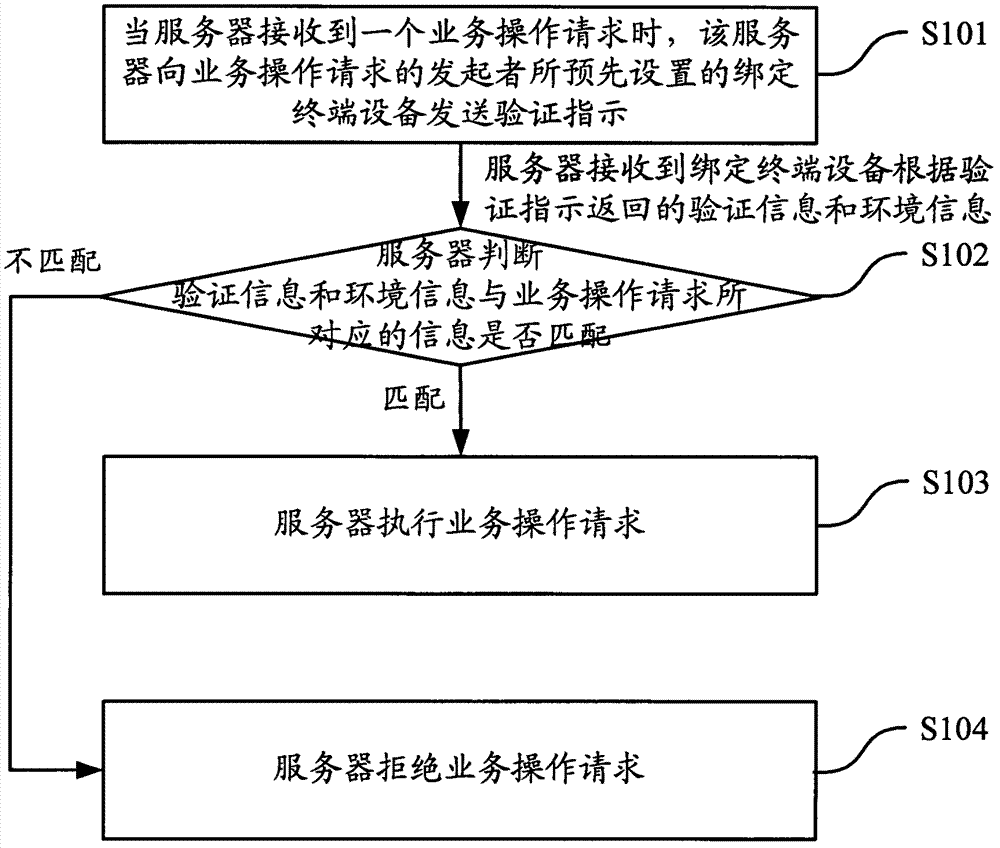
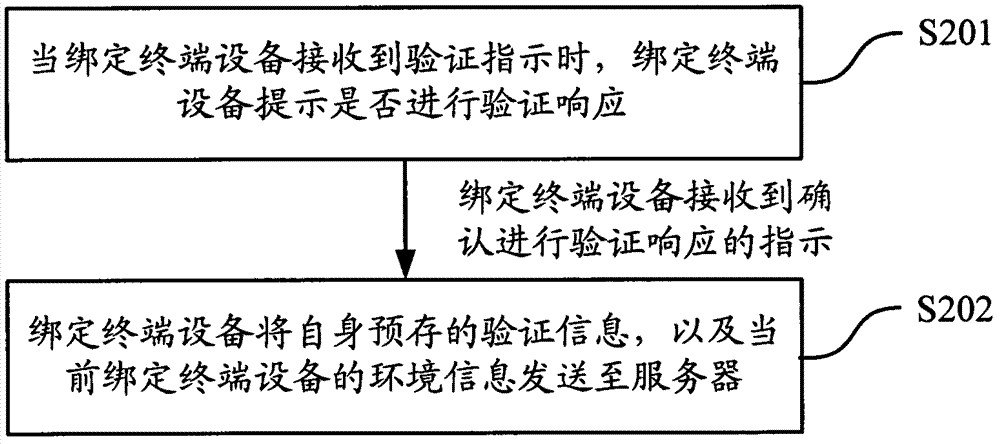
[0048] As mentioned in the background technology, many sensitive operations in the real world and on the Internet need to verify the identity of the user to determine whether the operation is legal, such as opening a door, opening a car, withdrawing money from an ATM, online payment, online shopping, etc. However, whether the verification methods in the existing technical solutions are static verification or dynamic verification, they all need to rely on cumbersome manual input operations, and there are security loopholes such as phishing hazards.
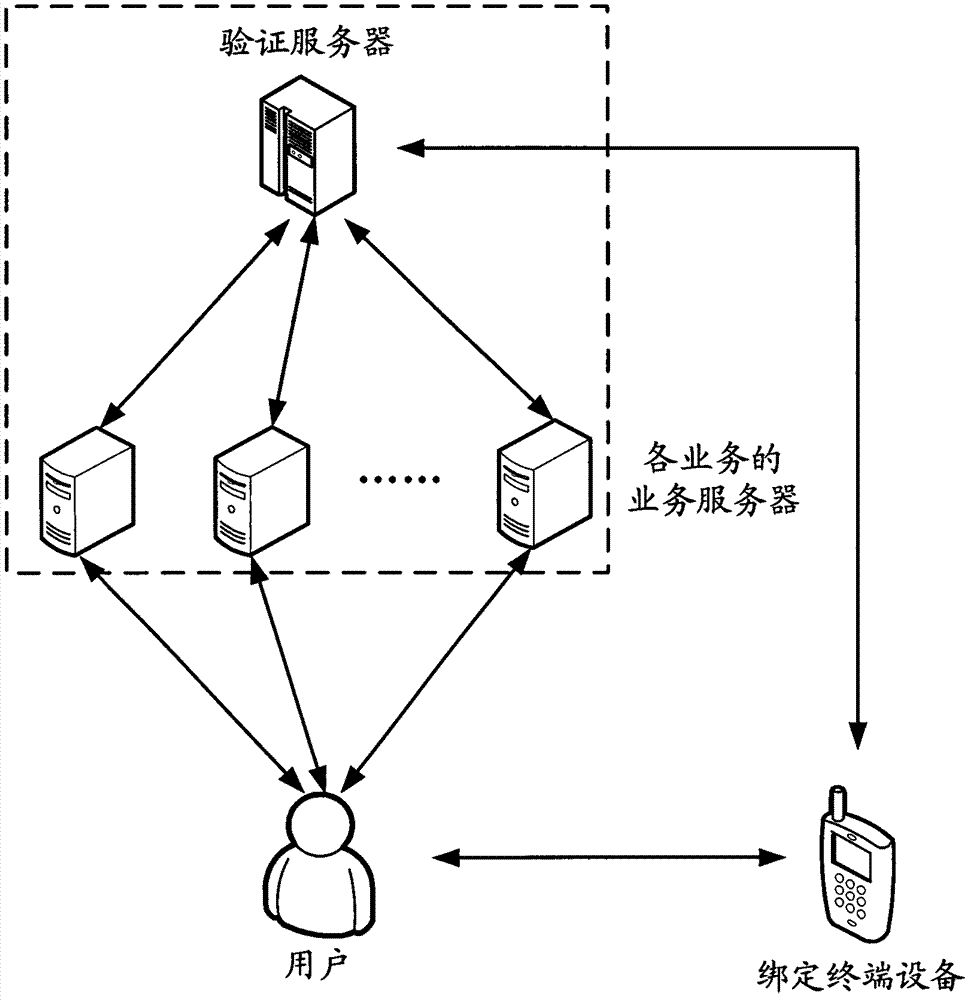
[0049] Based on this, the embodiment of this application proposes a method of triggering the binding terminal device to directly report the pre-stored verification information and the actually collected environmental information for identity verification. On the one hand, it simplifies the operator's operating procedures and avoids manual input of verification information. The cumbersome operations and security loopholes brought abo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com