Software lease authorization method based on attribute encryption
A technology of attribute encryption and software authorization, applied in the fields of instruments, digital data processing, computer security devices, etc., can solve the problems of complex leasing process, unable to provide effective protection measures, unable to solve software leasing security problems, etc., to achieve high security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
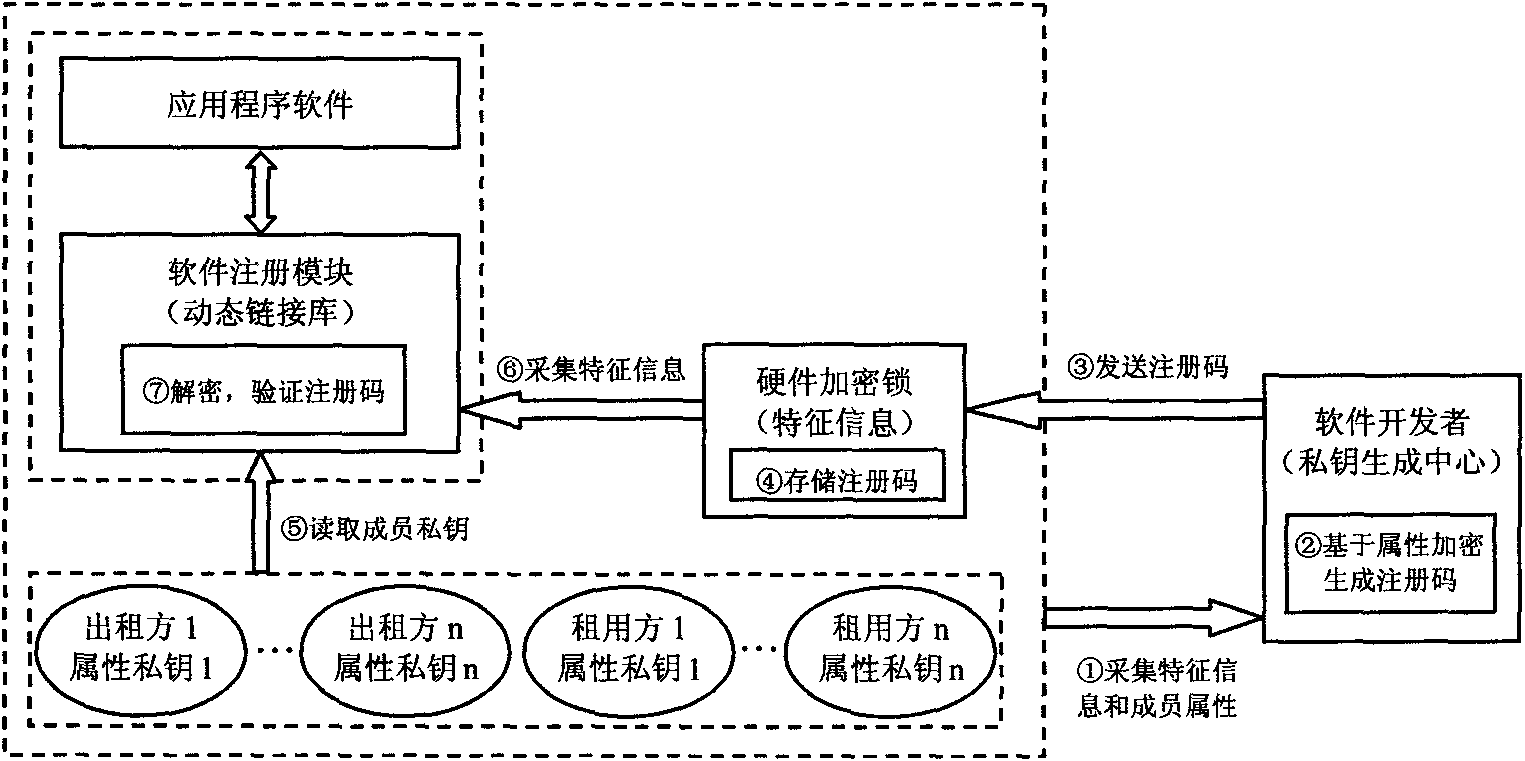
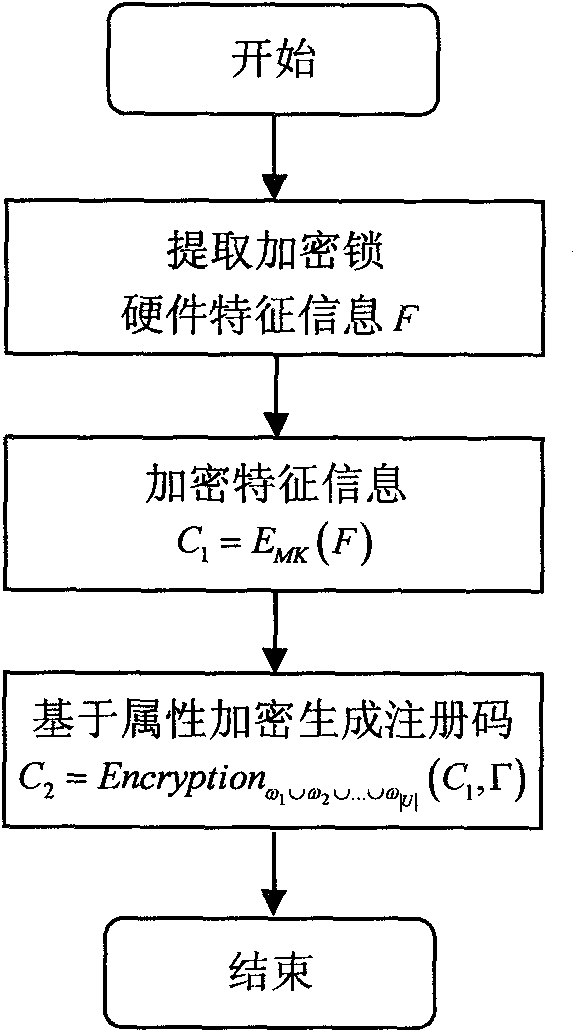
[0013] The present invention will be further described in detail below in conjunction with accompanying drawings and examples. This paper proposes a software authorization method based on attribute encryption. The basic principle is as follows: figure 1 shown. Attribute-based encryption is an extension of identity-based encryption, where identities (public keys) are represented by a series of descriptive attributes and a more flexible access structure is added. Attribute-based encryption has the characteristics of "one-to-many" and fuzzy identity. The encryptor encrypts the message with a set of attributes, and the user who has the private key corresponding to these attributes can decrypt the message.
[0014] (1) Initialization of the attribute-based encryption system.
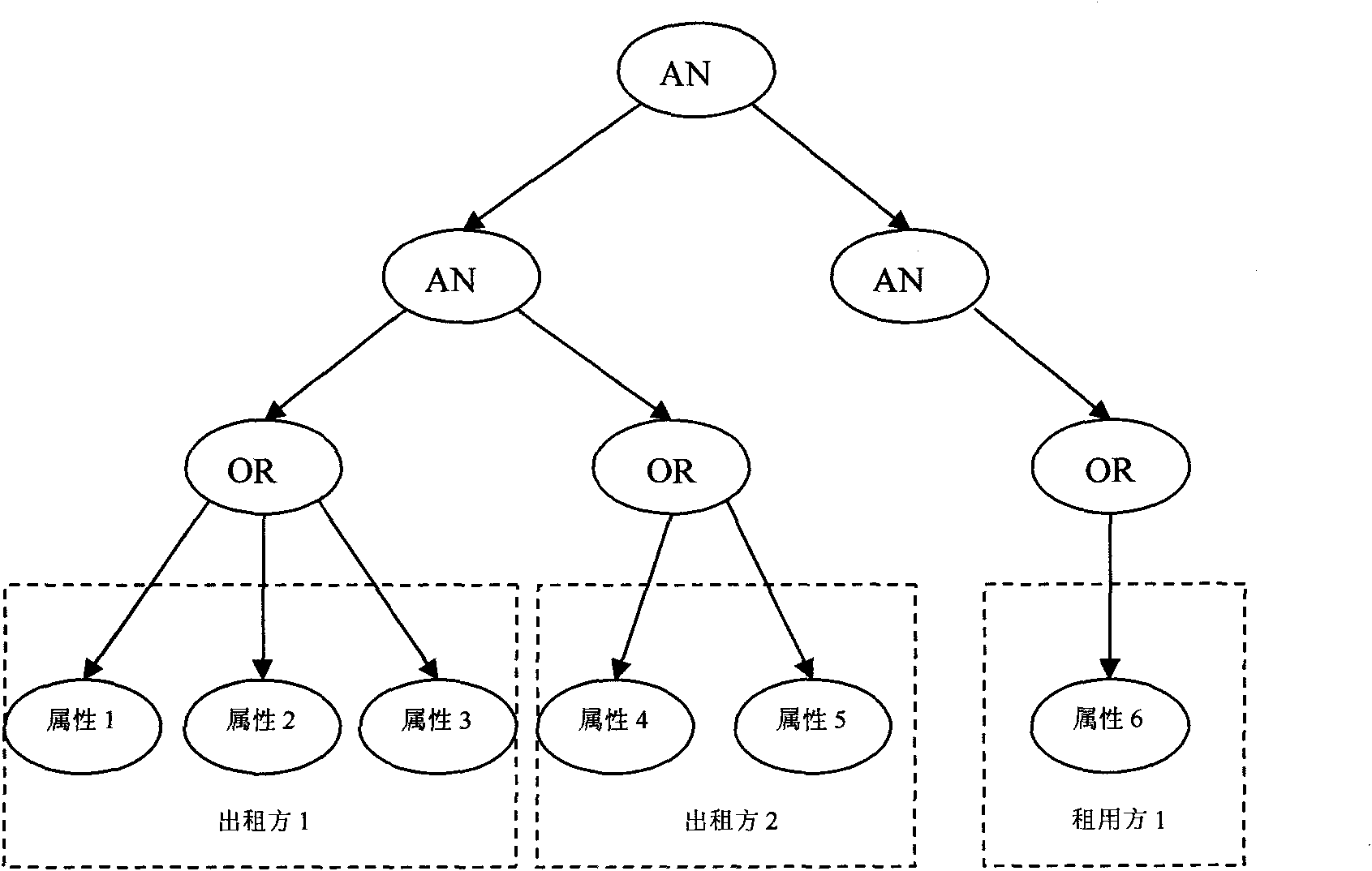
[0015] The private key generation center PKG (generally acted by the software owner) sets the lease member set as U={u 1 , u 2 ,...u |U|}, the number of members is |U|. The attribute set is W. The acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com