Separate storage method for electronic documents
An electronic document, separate technology, applied in the direction of preventing unauthorized use of memory, etc., can solve the problems of high cost of effective key management, difficult to implement authentication and authorization mechanism, and difficult to obtain encryption algorithm, so as to achieve low implementation cost and prevent Leaked, low-cost effects
Inactive Publication Date: 2008-08-27
孙巍(CN)
View PDF0 Cites 11 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In fact, high-strength encryption algorithms are difficult to obtain, and the rapid development of computing technology has greatly improved the ability to crack passwords; the cost of effective key management is also huge; perfect authentication and authorization mechanisms are difficult to implement in small-scale systems, so It is very difficult to realize low-cost high-intensity security management without destroying the integrity of electronic document information
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
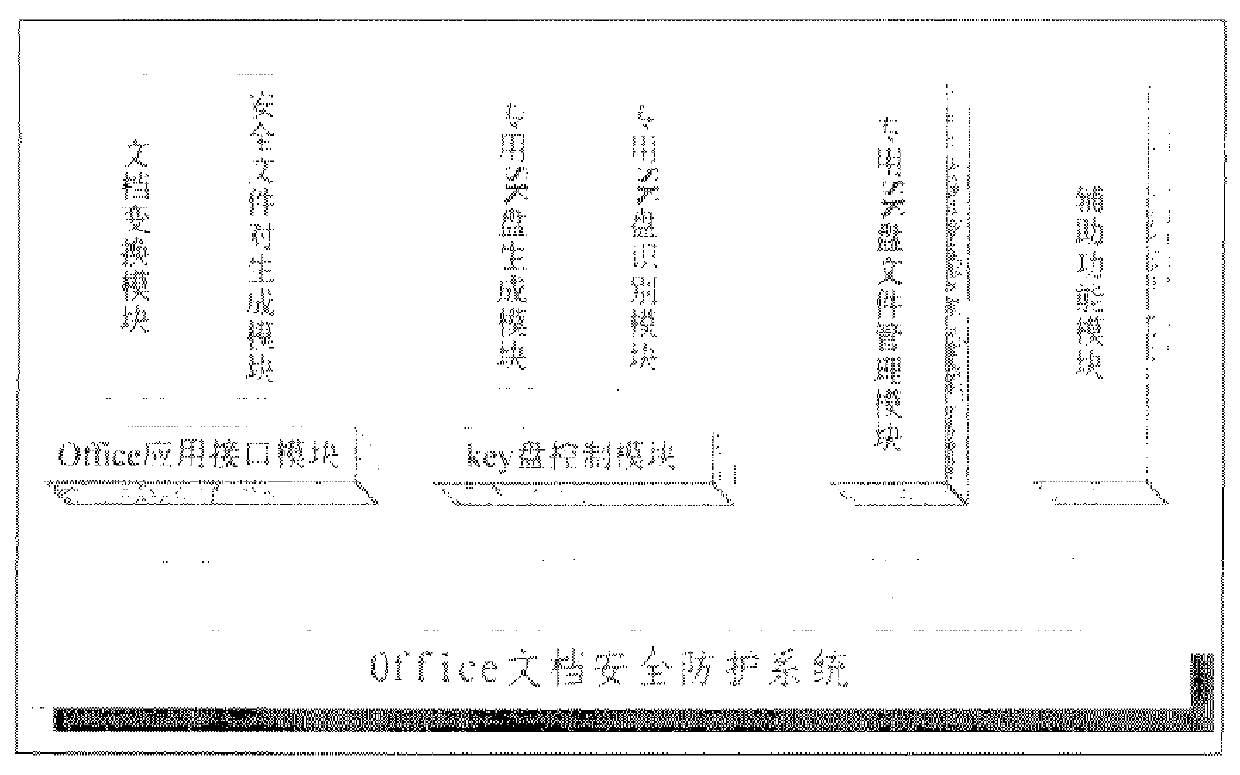
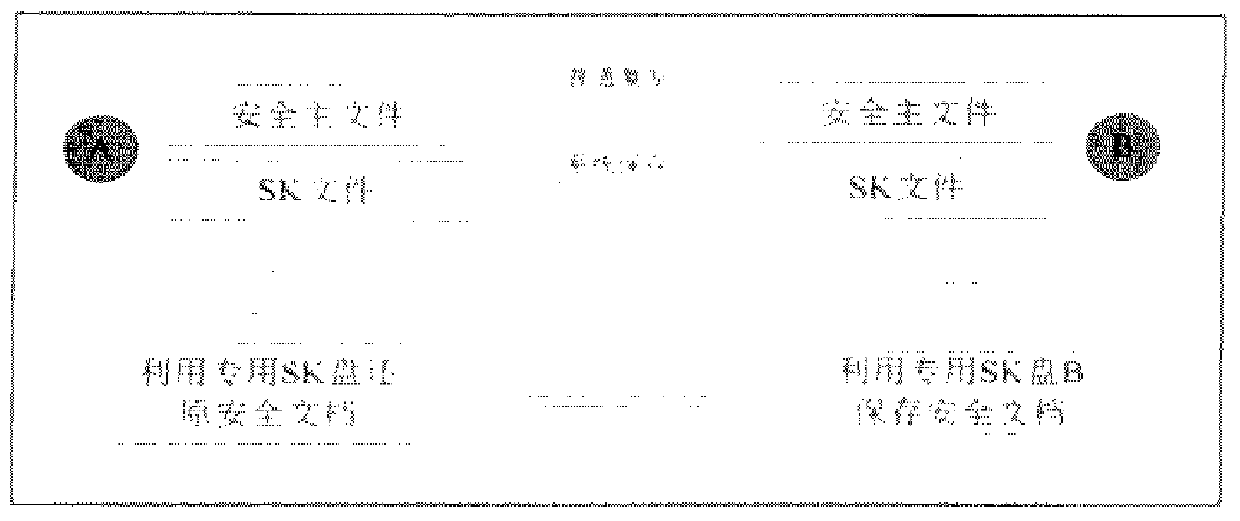
The invention relates to a separate storage method for electronic documents. The method implements the conversion and information extraction of the electronic document and realizes separate storage on different storage media, and the information stored in different storage media realizes the recovery of the electronic document according to the reverse process of the above-mentioned process. The present invention uses separate storage based on information extraction to destroy the integrity of protected electronic document information and realize high-strength protection of electronic documents, that is, by adopting separate storage including steps such as transformation, extraction, and restoration, the integrity of information is destroyed. Integrity, after the protected electronic document is stored by the present invention, since the information in any storage medium is incomplete, and the corresponding information stored in the two storage media is not merged, the content of the electronic document cannot be restored, so as long as the two storage media Separate storage can achieve the purpose of ensuring that electronic documents are not illegally read, diffused, and stolen, and prevent electronic documents from being leaked; the implementation cost is small, and it is simple and easy.
Description
a technical field The invention belongs to electronic document storage technology for the purpose of information security protection, in particular to a separate storage method for electronic documents. Two background technology The security management of electronic documents mainly refers to the security management of text, image, video, audio, data and other information stored in the form of files in the computer. At present, there are many technical means. In summary, there are mainly: 1) Access control based on identity authentication. Typically, the server centralized storage method is adopted, and the client endows the corresponding read, write, copy, delete and other permissions after the server authenticates the user identity. 2) Encrypted storage method. Files are encrypted and stored in storage media such as hard disks, mobile hard disks, and U disks. The security of files depends on the security of keys and the strength of encryption algorithms. Encrypted mobile...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F12/14
Inventor 孙进朱晓阳单懿
Owner 孙巍(CN)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com