Stored data integrity protection method of memory addition validator
A technology of integrity protection and memory data, which is applied in the direction of electrical digital data processing, instruments, computer security devices, etc., can solve the problems of high overhead, shorten the verification path, etc., and achieve the effect of reducing time and space overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
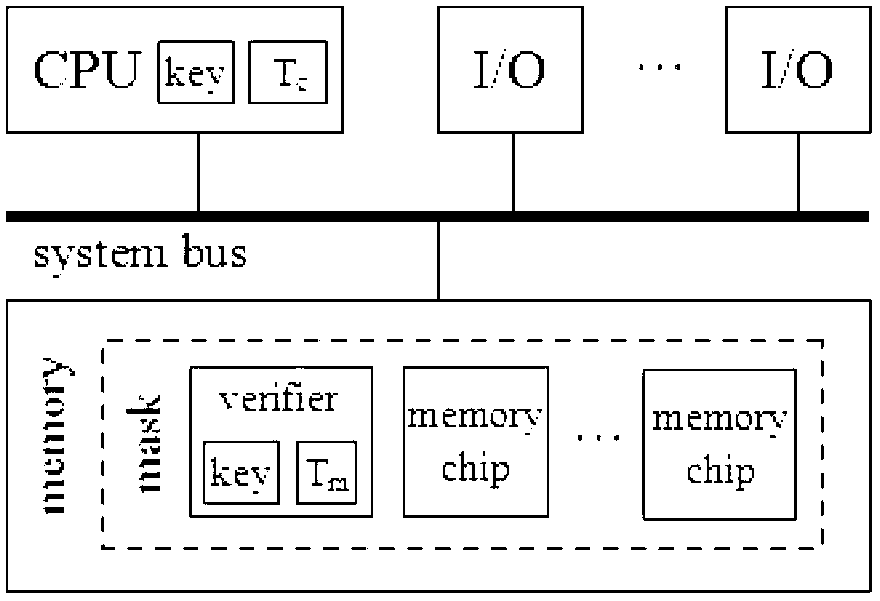
[0019] The present invention is described in more detail below in conjunction with accompanying drawing example:
[0020] Combined with the attached drawings, the verifier is the verifier added in the memory, which has the same key as the CPU, and the mask is the encapsulation of multiple memory chips (memory chip) and verifier to protect it from hardware attacks. Set up a checker capable of information summary calculation in the memory, and realize the protection of the main memory through three main processes: initialization, writing data and reading data, respectively described as follows.
[0021] (1) Initialization
[0022] Set the same key for the CPU and the verifier, and each maintain a counter for synchronization. Initially, the values of the two counters can be set to 0.
[0023] (2) Write data block
[0024] When writing a data block, add 1 to the counter of the CPU, connect the cache line data to be saved, the counter value and the cache line address, use the k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com