Method for controlling terminal to enter secret communication, secret communication method and terminal
A control method and a technology of secure communication, which is applied in the field of communication, and can solve the problems such as the indetermination of the timing of the two parties entering the secret call in the secure communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
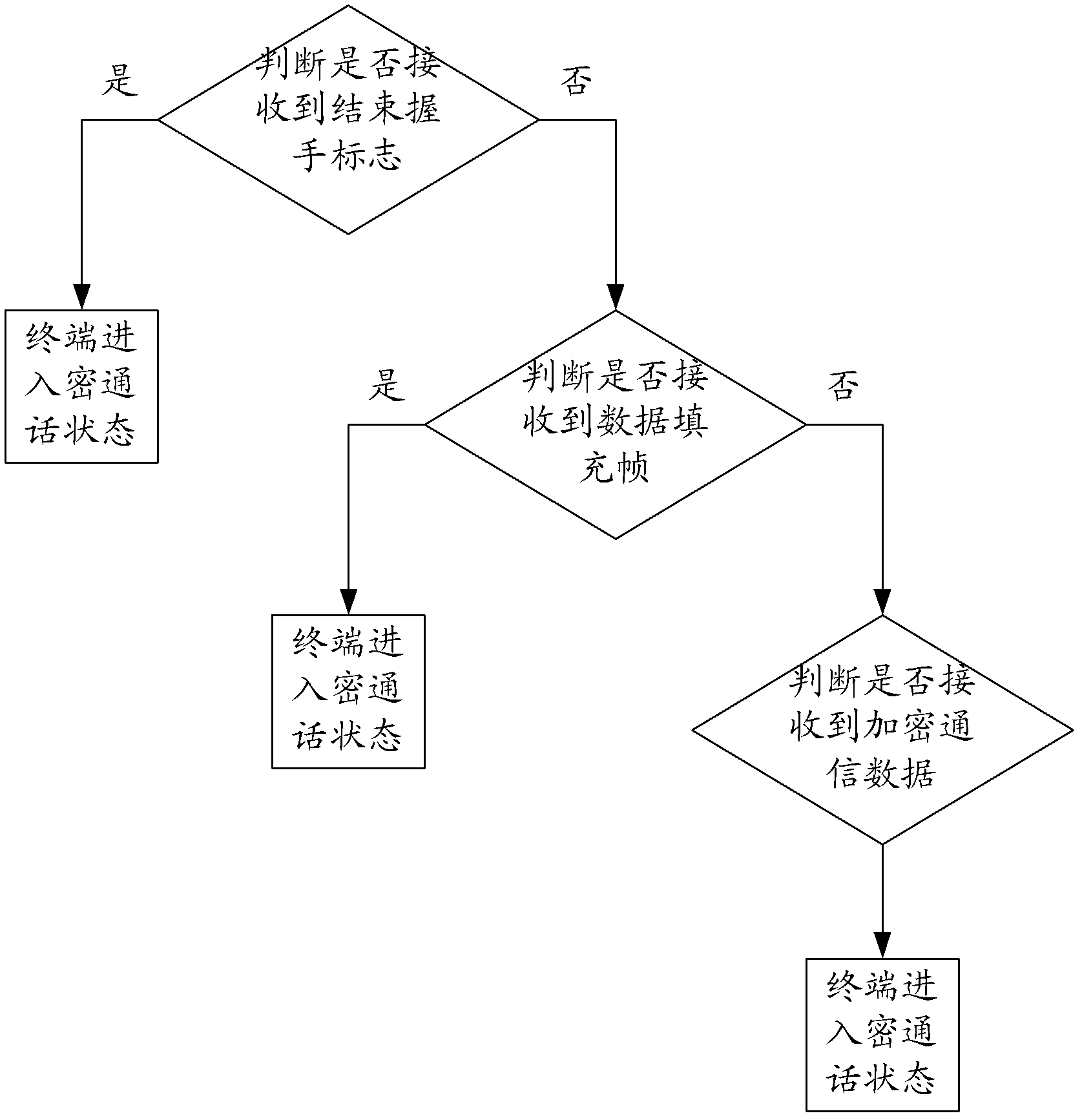
[0037] Please refer to image 3 , which is a schematic flowchart of a method for controlling a terminal entering a secret call according to an embodiment of the present invention. Such as image 3 As shown, the terminal steps as follows:
[0038] Judging whether the end handshake flag is received, if yes, the terminal enters the secret call state.
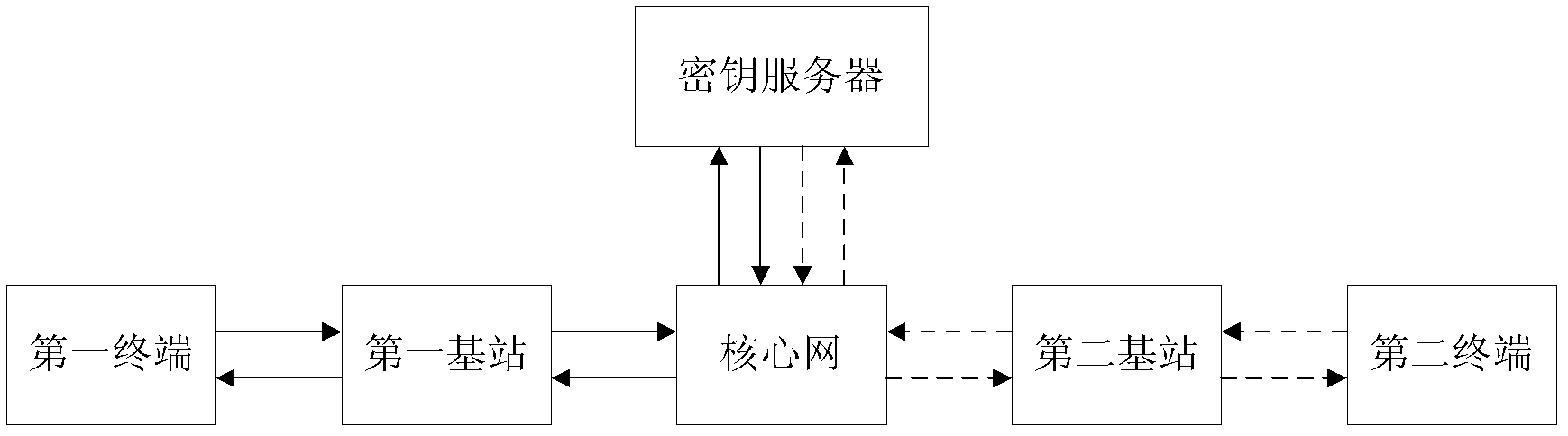
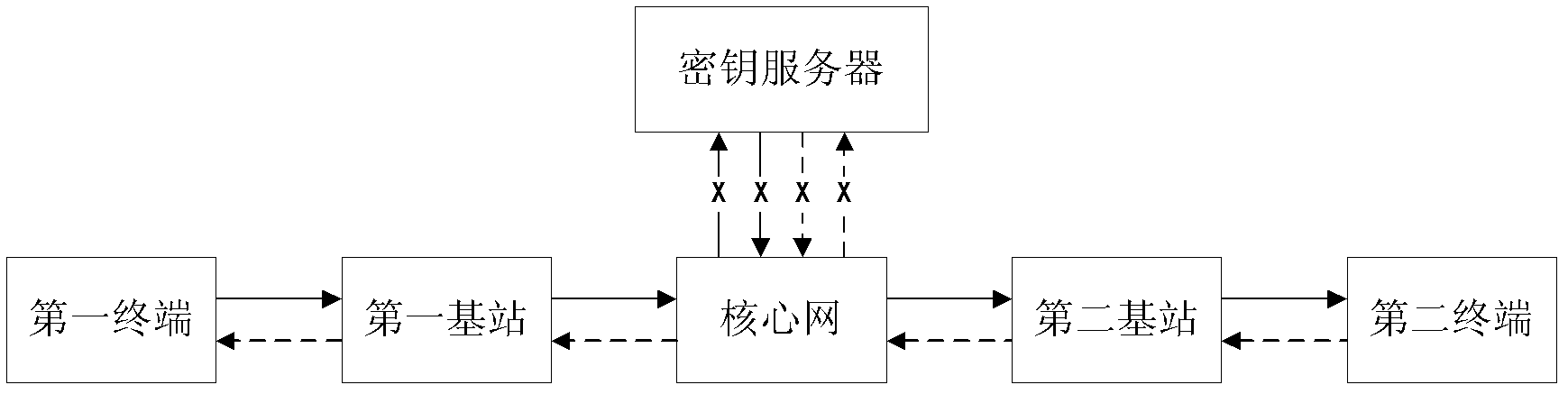
[0039] In this embodiment, the terminal is the communicating parties for secure communication, including the first terminal and the second terminal, and the key server can simultaneously send the handshake end flag to the first terminal and the second terminal.
[0040] Specifically, the key server may use a data link to send the end handshake flag to the terminal. When performing secure voice communication, the data link is a 12.2k voice link; and when performing secure video communication, the The above data link is a 64k video link. In addition, when the secure communication parties are conducting secure video communication,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com