Hyper-chaos encryption method for weak password based on quantum cellular neural network
A technology of neural network and encryption method, which is applied in the field of weak password hyperchaotic encryption, can solve problems such as difficult to guarantee security, and achieve the effects of enhanced ability to resist violent attacks, high security level, and convenient memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
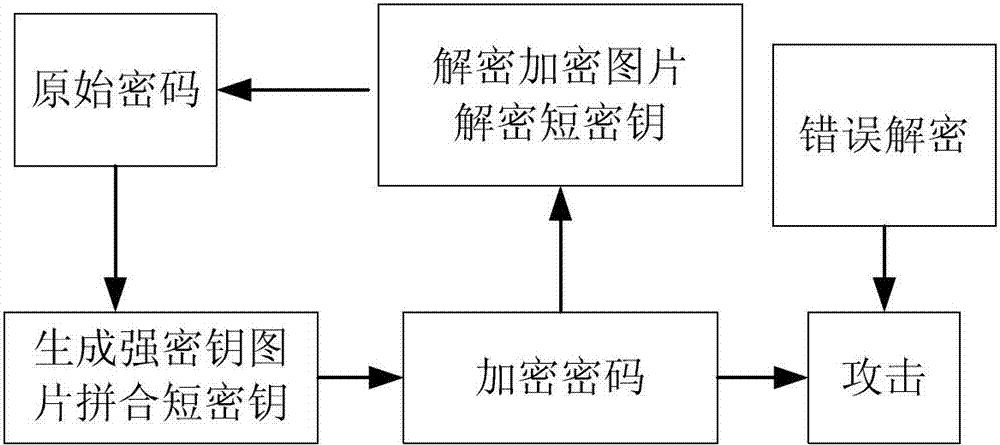
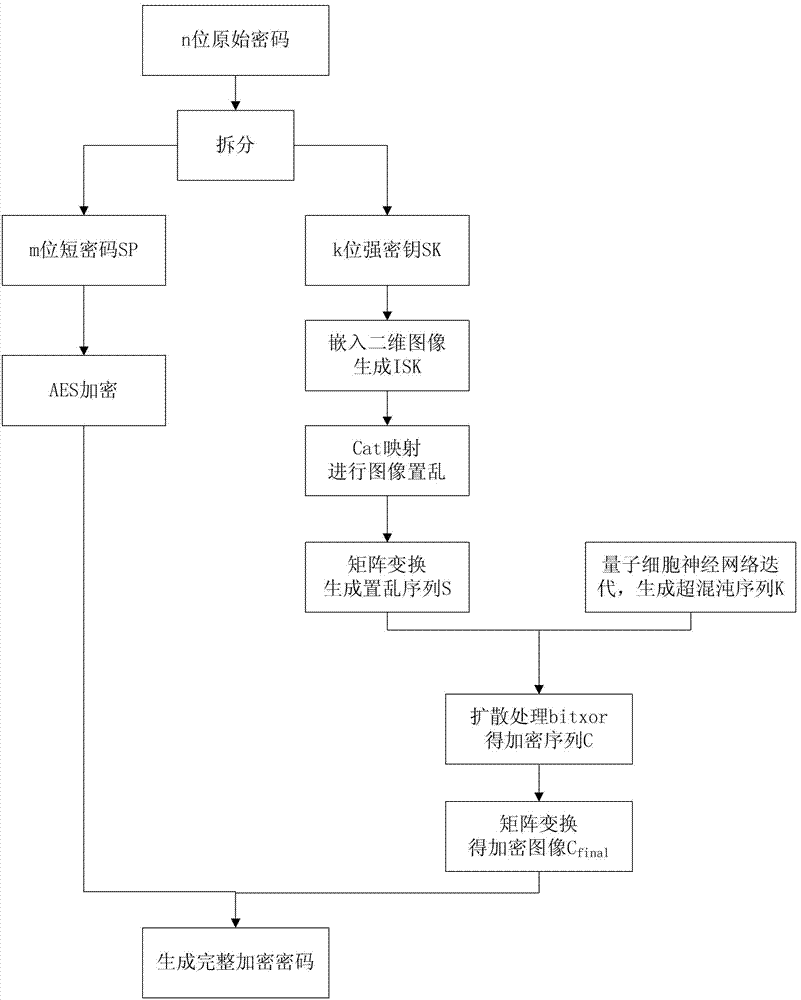
[0019] Specific implementation mode 1. Combination Figure 1 to Figure 3 Illustrate this embodiment, based on the weak password hyperchaotic encryption method of quantum cellular neural network, this method is realized by the following steps:
[0020] A1. Select a password with a length of n as the encryption object, n is a positive integer, and the combination length of n is within a reasonable range (such as 105 combinations);
[0021] B1. Split the n-bit password into m-bit short password SP and k-bit strong key SK;
[0022] C1. Embed the strong key SK into the two-dimensional image to form the image strong key ISK; the difference from the existing encryption technology is that the user is no longer required to memorize the SK. For the human brain, it is far longer to memorize an image. Much easier than memorizing k-bit characters;
[0023] D1. Perform discrete chaotic mapping on the image strong key ISK in step C1, and set control parameters to obtain a scrambled image S...
specific Embodiment approach 2
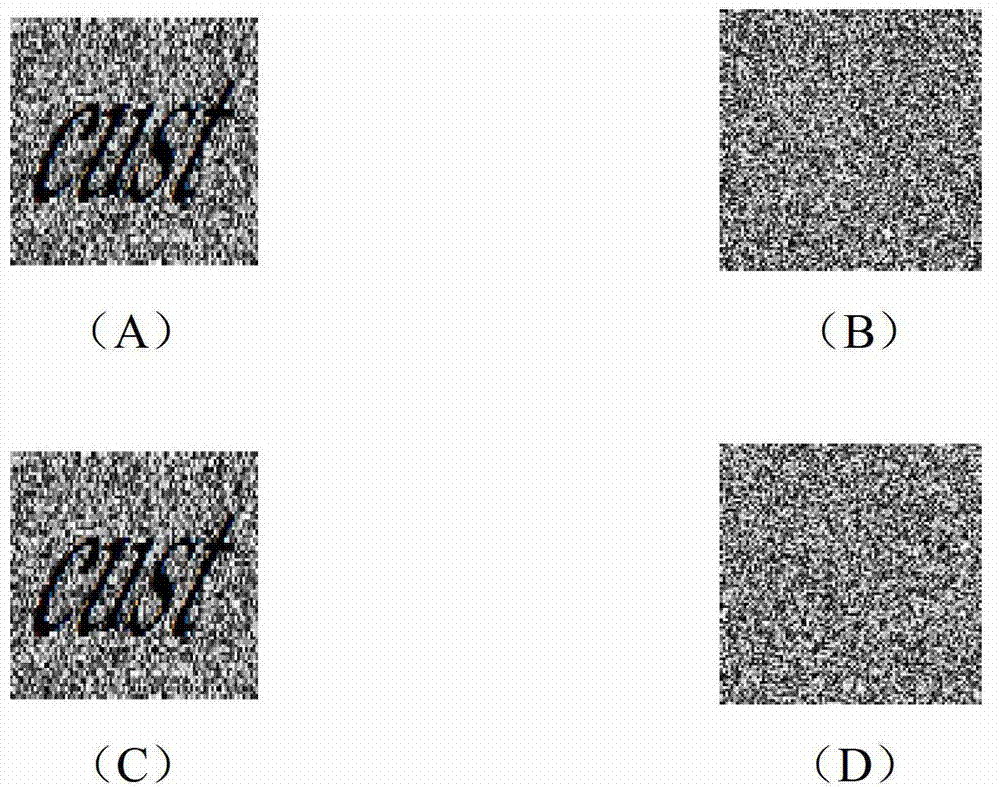
[0041] Specific embodiment two, combine image 3Describe this implementation mode, this implementation mode is an embodiment of the quantum cellular neural network-based weak password hyperchaotic encryption method described in the first specific implementation mode:
[0042] 1. Select the seven-digit password "custABC" as the encryption object, of which the first four digits "cust" are the strong key SK, and the last three digits "ABC" are the short password SP;
[0043] 2. Embed "cust" into a two-dimensional image to generate a 128×128 pixel image strong key ISK;
[0044] 3. According to the chaotic map shown in equation (1), set the control parameters p=36, q=3, perform image scrambling processing on the image strong key ISK, and obtain the scrambled image S_ISK. And the scrambled image S_ISK is arranged in order from top to bottom and from left to right to obtain a scrambled sequence S;
[0045] 4. According to the hyper-chaotic system shown in formula (2), set the initi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com