Chaos synchronization encrypting/decrypting method and device using data compression encoding
A chaotic synchronization and data compression technology, applied in the field of information security, can solve the problems of low encryption strength, key management and security protection problems, and encryption speed decline, and achieve the effect of improving encryption security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The following content is only an example, and is not intended to limit the protection scope of the present invention.
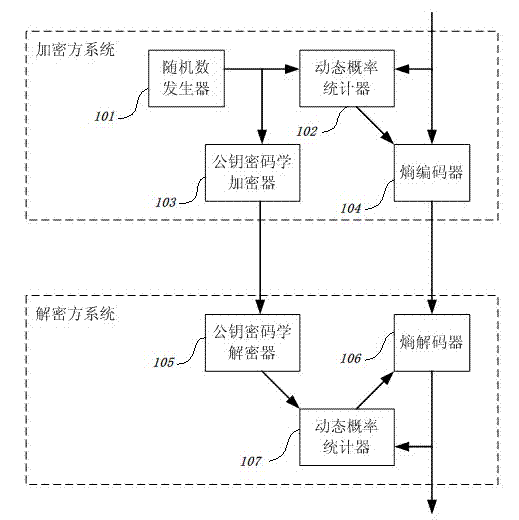
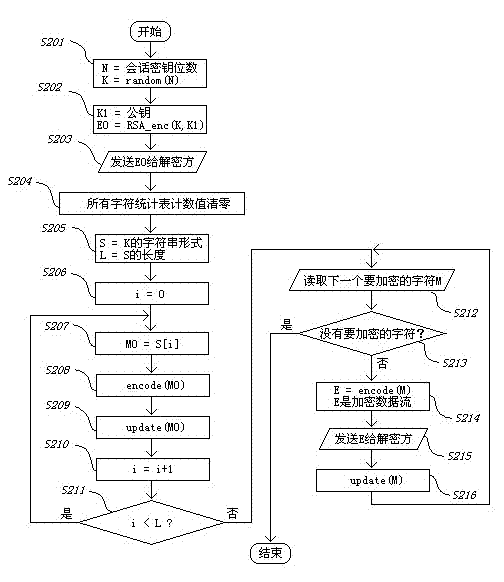
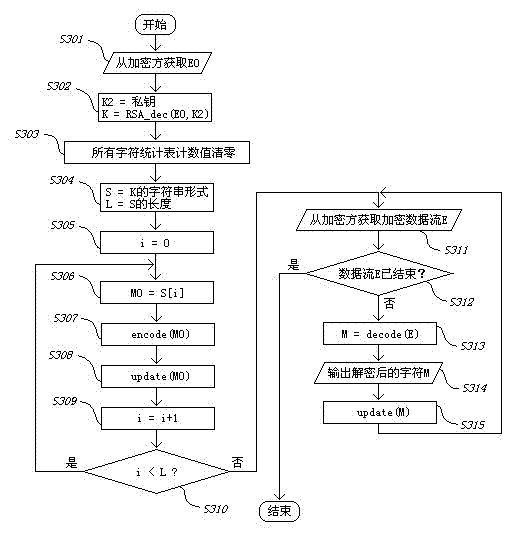
[0071] In view of the problem that the key length of the existing encryption technology will affect the encryption performance, resulting in the problem that the ultra-long key is difficult to be applied in practice, this embodiment uses the adaptive interval encoder for data compression and the dynamic probability statistics of the PPM algorithm as the chaotic dynamic system ,Make the compression coding process a chaotic cryptographic encryption process; combine the public key cryptographic cipher with the chaotic dynamics system, the sender uses the RSA public key cryptographic algorithm to encrypt the randomly generated session key, and then transmits it to the receiver; The sending and receiving parties use the session key to initialize their own chaotic dynamics system to synchronize their system states; the sender uses the initialized system to perfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com