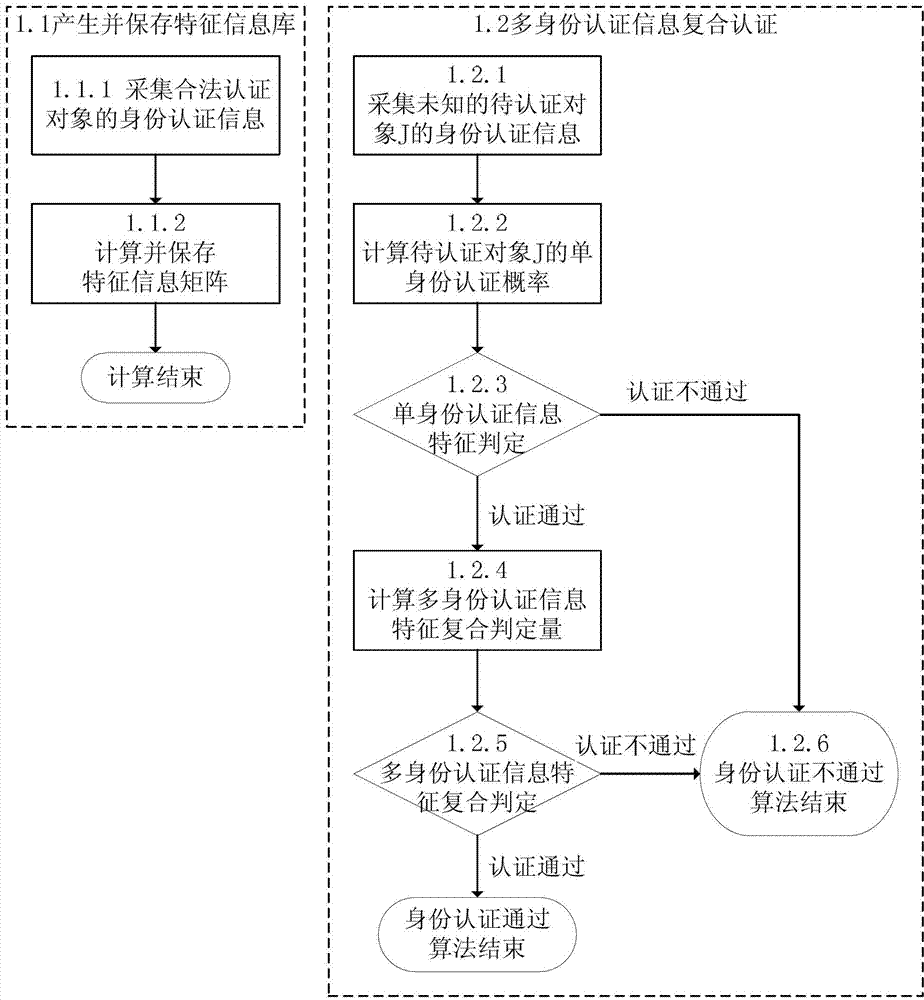
Compound authentication method of multi-identity authentication information feature
A technology of identity authentication and authentication method, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of high possibility of single identity authentication being copied and stolen, different identity authentication methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] Attached below figure 1 This embodiment will be described in detail.
[0069] After describing the system hardware connection relationship and the implementation process in detail, this embodiment illustrates the specific implementation process of the network service platform method of the multi-identity authentication composite algorithm proposed by the present invention through actual calculation, so as to deepen the reader's understanding of the content of the present invention .
[0070] 1. Hardware system design:
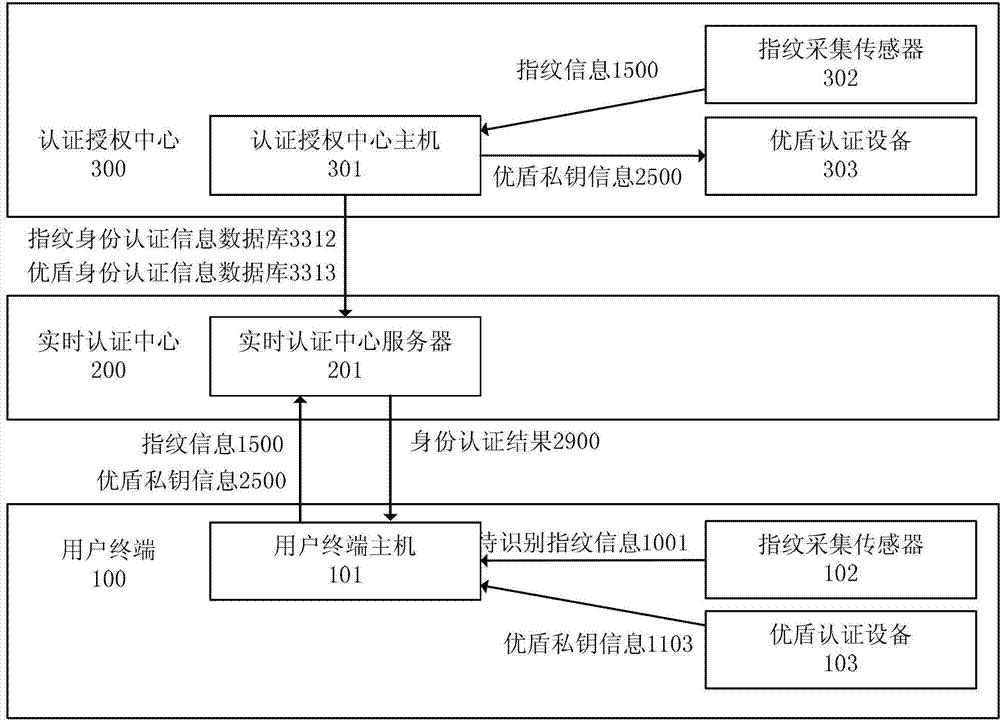
[0071] The multi-identity authentication-based network service system consists of four parts: multiple user terminals (100), a real-time authentication center (200), an authentication authorization center (300), and a characteristic information storage medium (0). The authentication center (300 ) adopts a multi-identity authentication compound algorithm.
[0072] Each user terminal (100) is composed of a user terminal host (101), a fingerprint identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com