Mobile learning system and using method thereof
A learning system and a technology for prompting users, applied in transmission systems, electrical components, etc., can solve the problems that mobile learning systems cannot meet controlled applications and safety traceability requirements, reduce memory consumption, improve verification efficiency, and improve loading. The effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
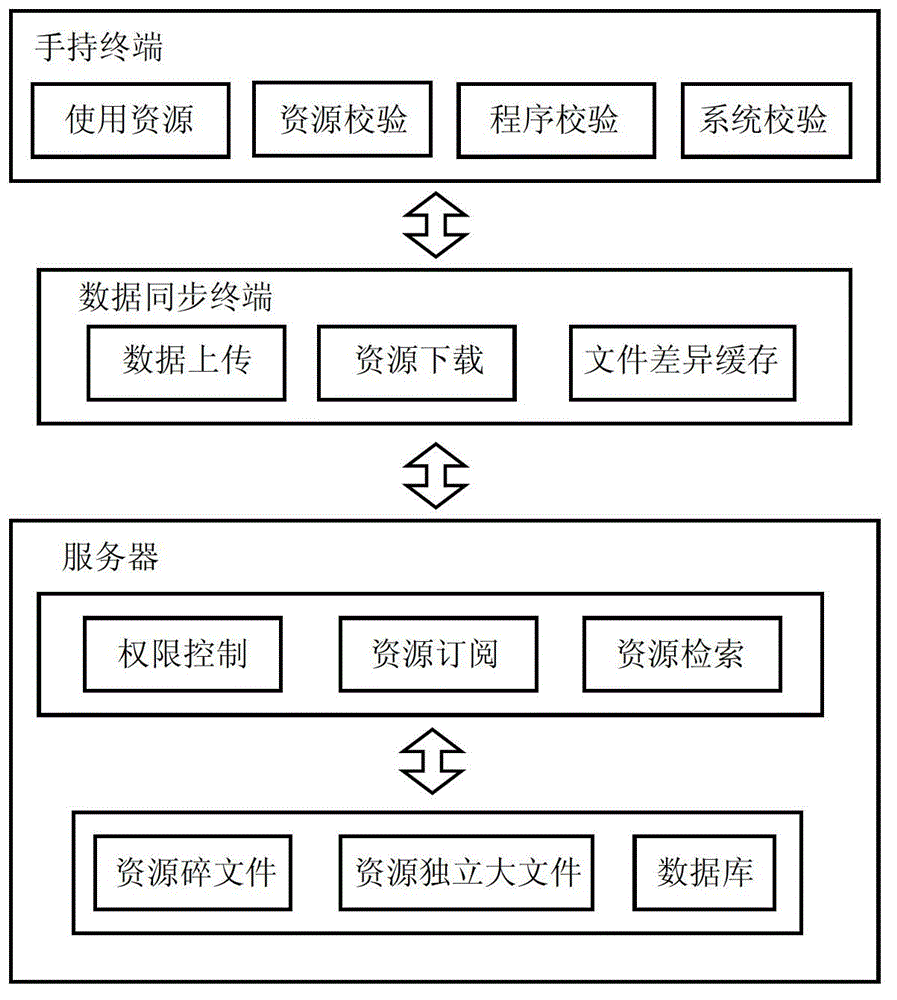
[0065] The usage method of video resources in the system of the present invention:
[0066] 1) Book resources are stored in the system as fragmented files;
[0067] 2) The application verifies the resource, uses the directory package, and extracts the characteristic value according to the attribute information;
[0068] 3) Read the number of files in the directory and the total size of the files, combine this information in a fixed format, and perform MD5 calculation on the combined string to obtain a 16-digit MD5 value, which is the check code;
[0069] 4) Compare the calculated check code with the check code in the system resource properties. If they match, it proves that the resource is correct; otherwise, it fails to open;
[0070] 5) Extract the usage count in the resource attribute. When the count is greater than 1, the user is prompted to use the resource and save the count by one; when it is zero, the user will not be able to open the file for use; when the count is m...
Embodiment 2
[0072] Application method in the system of the present invention:
[0073] 1) The application program in the system is written into the system once and installed when the handheld terminal is initialized;
[0074] 2) After the application in the system is installed, the initialization tool extracts the application signature;
[0075] 3) Extract 50 bytes backward from the beginning of the file, extract 50 bytes from the middle of the file, and extract 50 bytes forward from the end of the file;
[0076] 4) According to the extraction order, combine the extracted content, perform MD5 operation on the combined string, and get 16 as the MD5 value, which is the check code;
[0077] 5) Record the calculated check code in the specified file of the system;
[0078] 6) Before opening the application for use, the user extracts the verification code according to steps 3) and 4). If they are consistent, the application is opened, otherwise the opening fails.
Embodiment 3
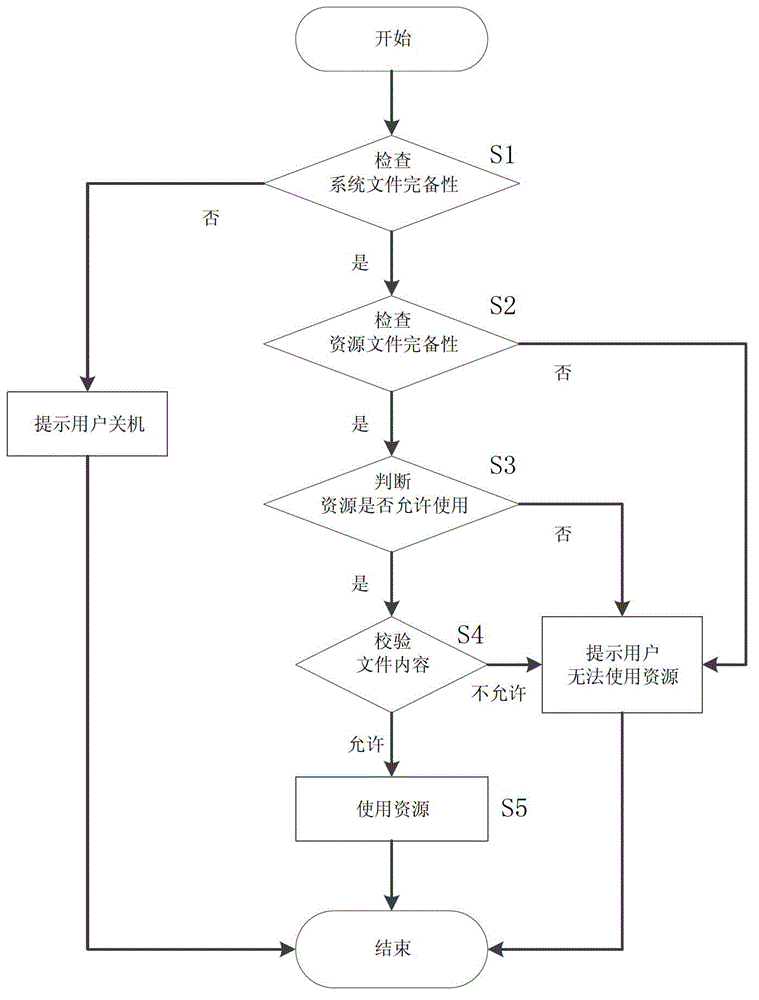
[0080] The method for system self-test of the present invention:
[0081] 1) The system automatically runs the only desktop program after booting and running, and starts the detection thread at the same time;
[0082] 2) Firstly, check the completeness of the system files of the handheld terminal;
[0083] 3) For independent large files, use multi-point combination verification to extract feature values, extract 50 bytes backward from the beginning of the file, extract 50 bytes from the middle of the file, and extract 50 bytes forward from the end of the file, according to the order of extraction , combine the extracted content, perform MD5 operation on the combined string, and get 16-bit MD5 value, which is the check code;
[0084] 4) For scattered files, use the method of packaging and extracting feature values in a unified manner, read the number of files in the directory, the total size of the files, combine this information in a fixed format, and perform MD5 operations...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com