Method and device for intercepting behaviors of program, and client equipment
A program execution and program technology, which is applied in the field of intercepting program behavior and client devices, can solve problems such as disconnection and inability to effectively intercept malicious programs, and achieve the effect of improving protection capabilities and effective interception.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
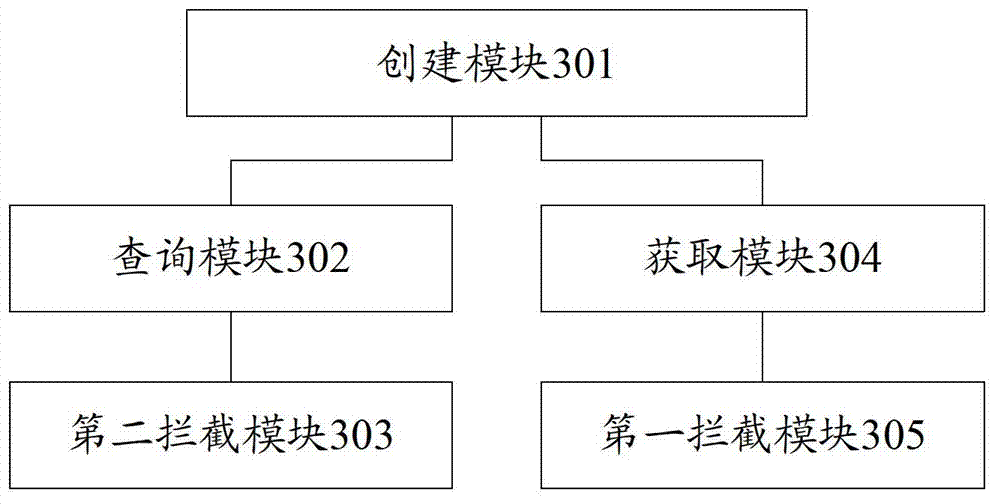
Image
Examples
example 1
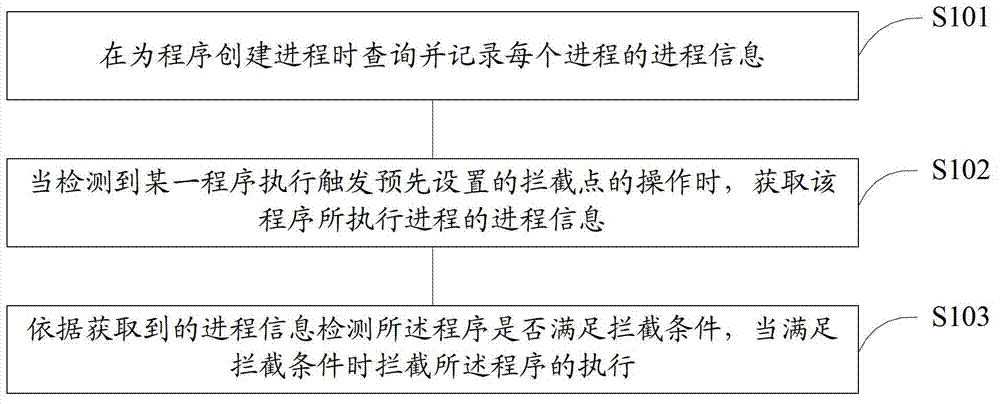
[0169] a.exe is a malicious program, which will first disconnect the network when it is running, and then trigger an interception point by writing a system startup item in the registry for self-starting.
[0170] Before using the technology proposed by the present invention, the active defense intercepted the writing behavior of the registry. When trying to obtain the file level of a.exe, because the network has been disconnected, it cannot be obtained. In order to avoid error prompts, only Choose to allow it to do so.
[0171] And after using the technology that the present invention proposes, will inquire and record its process information when creating a process (i.e. before running) for a.exe, when detecting registry writing behavior, judge that current network can't be connected, The file level of the current process will be obtained by querying the previous records, thereby normally intercepting the execution of this program.
example 2
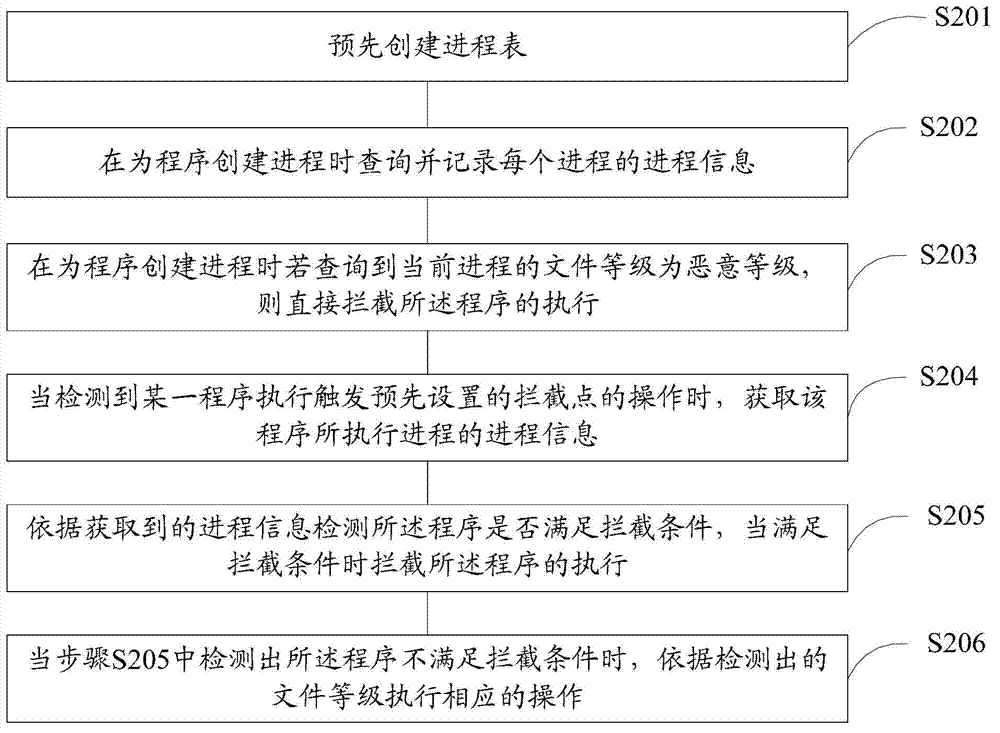
[0173] Combined with the process chain to handle the situation of network disconnection. For example: a.exe is an unknown program, b.exe is a white program that can be used (white use), when a.exe is running, it will disconnect the network, and then call b.exe to write and start item, thus triggering the interception point.
[0174] When creating processes for a.exe and b.exe, the process information is recorded, such as the file level of the process executed by a.exe is malicious level, the file level of the process executed by b.exe is security level, and a.exe The executed process is the parent process of the process executed by b.exe.
[0175] When b.exe executes the operation of writing to the registry, the interception point is triggered, and the active defense creates a relationship through the previously recorded process. It can be known that b.exe is created by a.exe, so the process executed by b.exe is obtained at the same time and the file level of the process exe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com