Method and system for accessing internet by mobile terminal
A mobile terminal and Internet technology, applied in the transmission system, electrical components, wireless communication, etc., can solve the problem that identity information can only be used to access the same website, access to the Internet is not safe, and achieve the effect of ensuring safety and avoiding loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
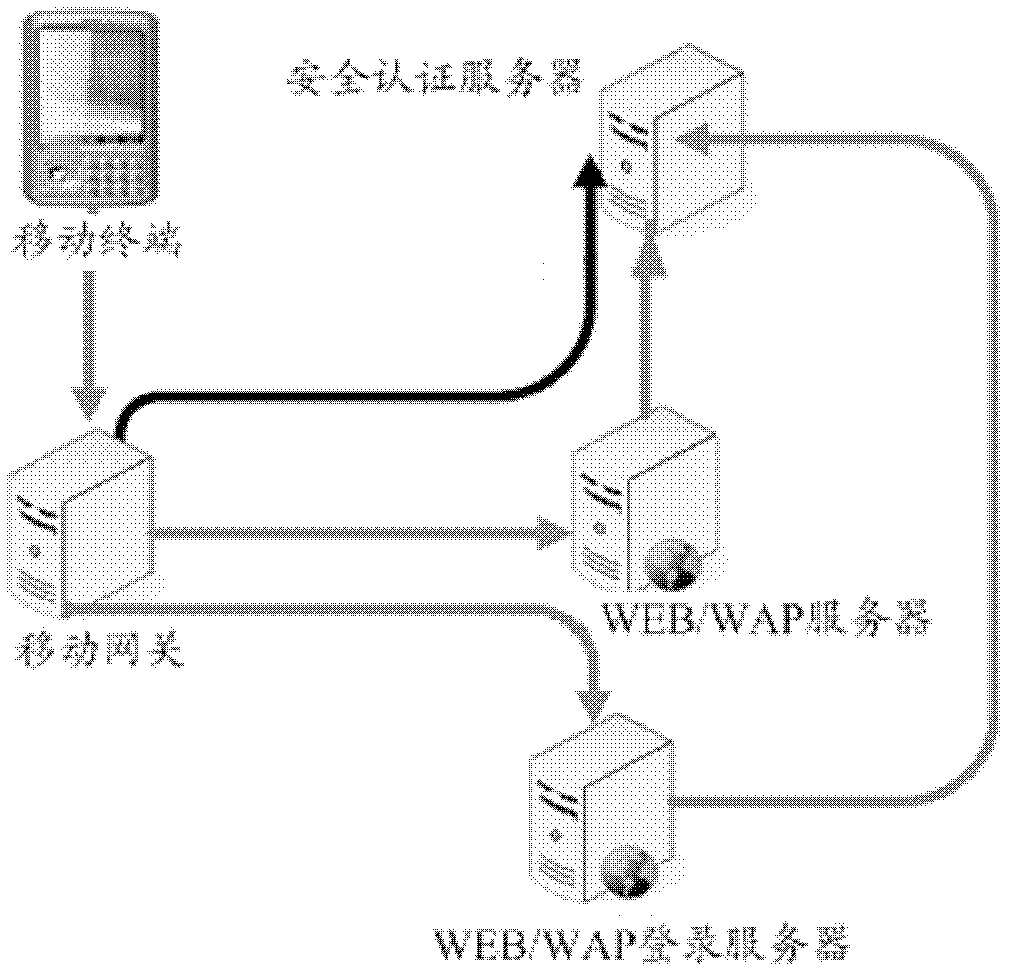
[0068] In this example, if figure 2 As shown, the system for a mobile terminal to access the Internet may include a mobile terminal, a mobile gateway, a security authentication server, a WEB / WAP server, and a WEB / WAP login server, wherein the mobile terminal is a mobile device capable of running a browser, such as a mobile phone; The gateway is used to provide access capabilities for mobile terminals to access the Internet, the security authentication server is used to provide security verification services and mobile terminal configuration delivery services; the WEB / WAP server is used to provide Internet access services, and can provide mobile terminals with access Web pages and other content of the website; the WEB / WAP login server is used to provide login services for Internet websites, and can provide mobile terminals with content such as login pages that need to visit the website.
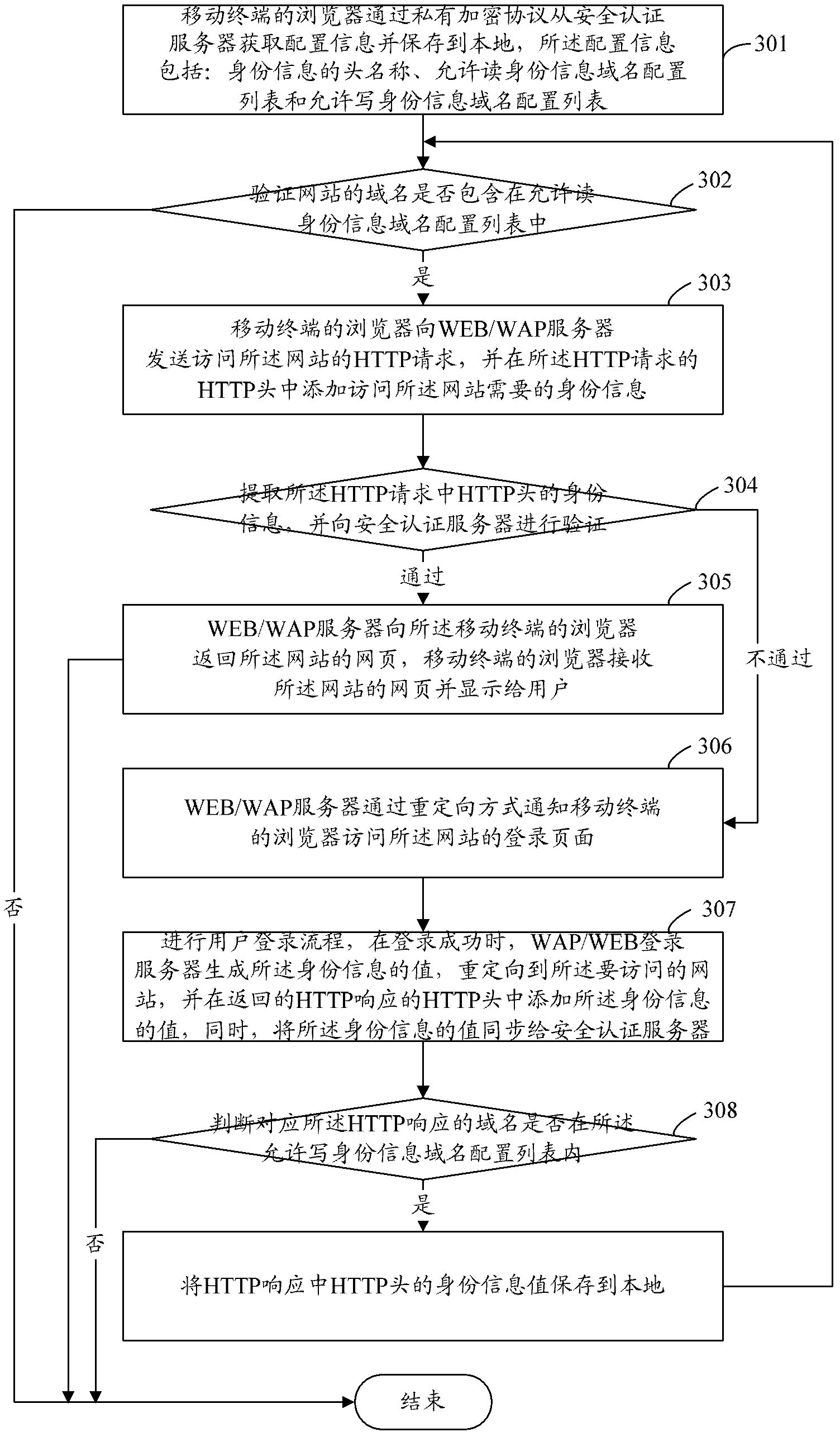
[0069] In this example, by figure 2 In the system shown, the specific flow of the mobil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com