Method and device for detecting errors of kernel extension module on basis of access rule control
An expansion module and error detection technology, applied in the field of computer security protection, can solve problems such as difficult deployment, and achieve the effects of improving security, reducing losses, and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] A kernel extension module error detection method based on access rule control, mainly comprising the following steps:
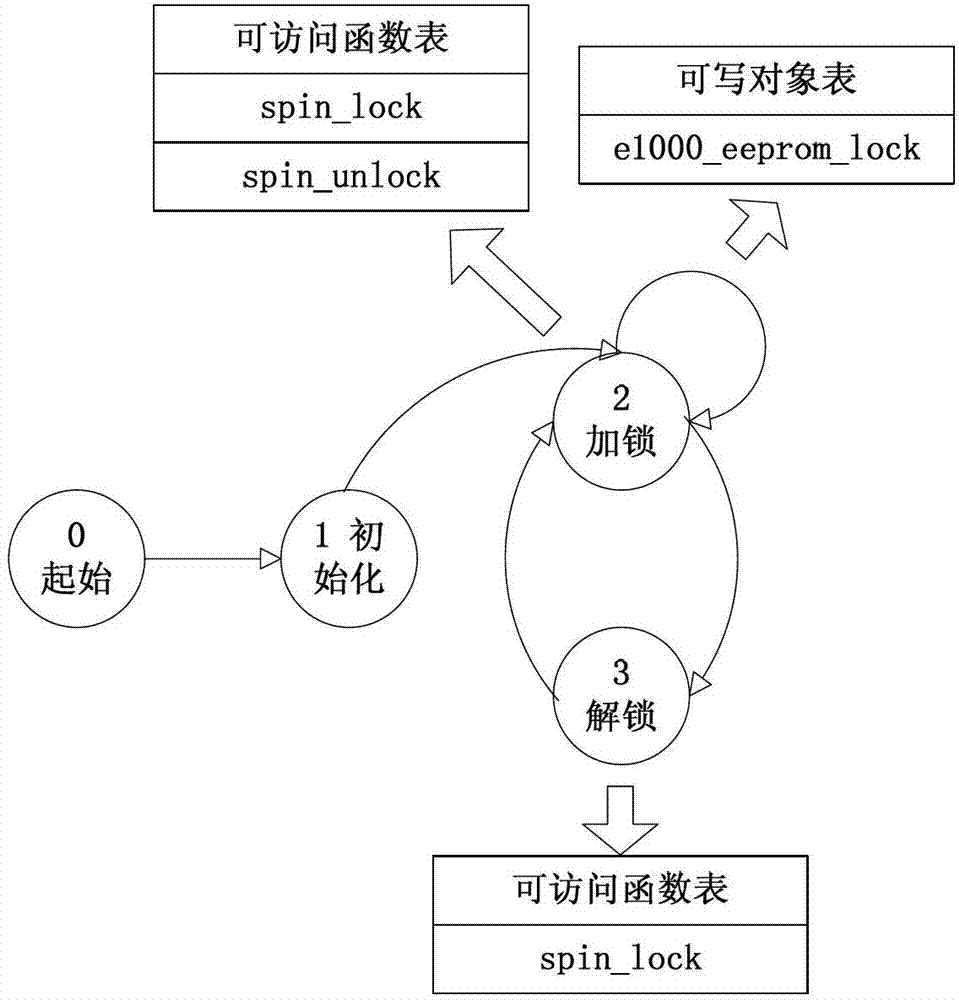
[0032] S1. Set kernel function usage rules for the kernel extension module; the usage rules can be established rules, or some specific rules customized by some organizations or system owners that are not directly related to the established rules; for example, in the Linux operating system Spin locks are used to ensure mutually exclusive access to critical sections. There are two types of operations in the interface functions: locking and unlocking. Among them, "spin locks cannot be unlocked before they are locked" is a kernel extension about spin locks. The kernel function usage rules of the module; similarly, it is also a usage rule that the kernel cannot be used again after being released; it is even a reasonable usage rule that the kernel must be cleared before the first use.
[0033] In this embodiment, the spin lock is taken as an example for illu...
Embodiment 2
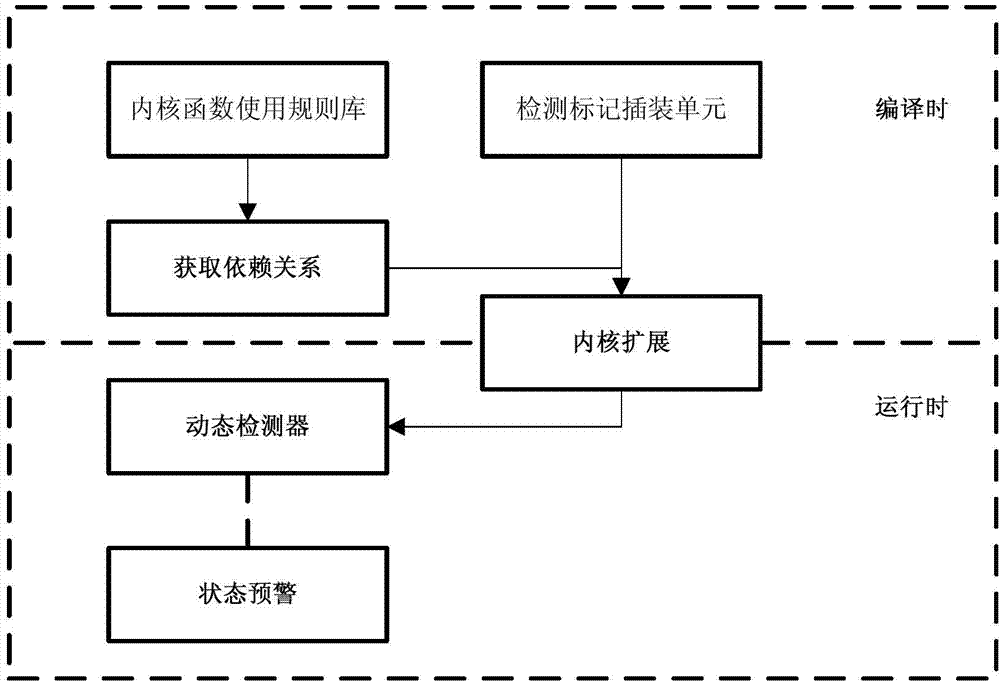
[0053] The present invention also provides a device according to the access rule control-based kernel extension module error detection method described in Embodiment 1, such as figure 2 As shown in : including usage rule library, marking instrumentation unit and dynamic detector respectively connected with the kernel extension module to be detected; the usage rule library contains kernel function usage rules related to the kernel extension module, and the marking insertion unit is used according to the Adding an instrumentation mark to the necessary interface found by the usage rules in the usage rule base, the dynamic detector monitors the running state of the kernel extension module in real time according to the insertion flag, and transfers the kernel extension module to an unsafe state alert the operating system kernel.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com