Shell technology based software protection method
A software protection and technology technology, applied in the direction of program/content distribution protection, etc., to enhance the ability to protect software and the effect of good software protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
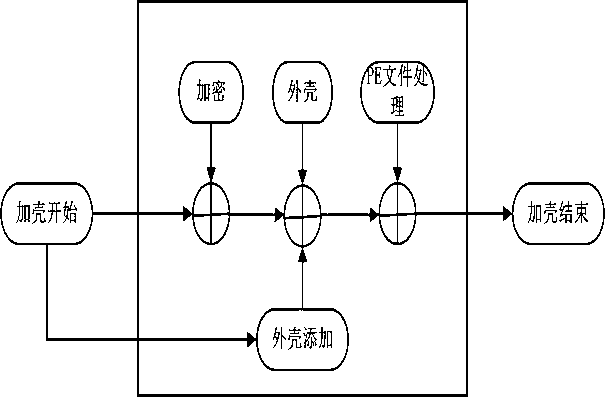
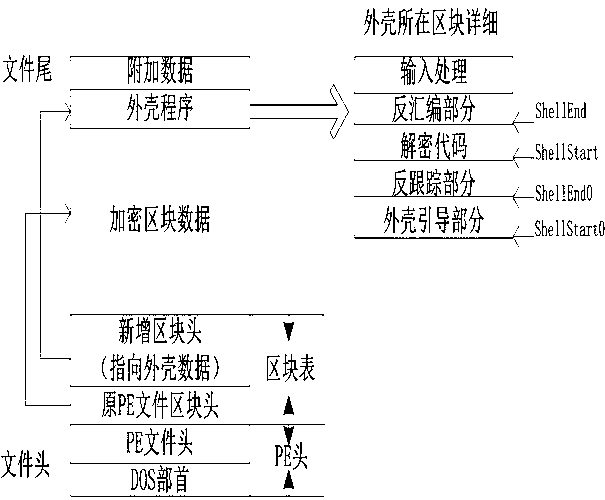
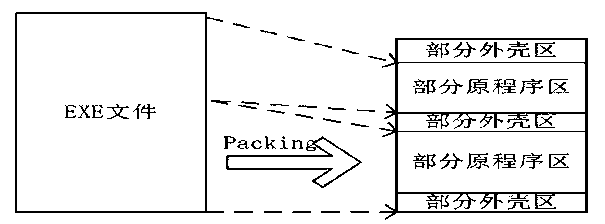
Image
Examples
Embodiment
[0036] The structure of the out-of-order instructions in the out-of-order processing is as follows:
[0037] typedef struct _CODE_FLOW_NODE
[0038] {
[0039] struct _CODE_FLOW_NODE *pNext; / / next node
[0040] BOOL bGoDown; / / whether to jump down
[0041] DWORD dwBits; / / jump range
[0042] DWORD dwType; / / Instruction type
[0043] BOOL bFar; / / Whether it is a far jump
[0044]DWORD dwMemoryAddress; / / Current memory address
[0045] LPBYTE pFileAddress; / / current file address
[0046] DWORD dwGotoMemoryAddress; / / The memory address after the jump
[0047] LPBYTE pGotoFileAddress; / / The address of the file after the jump
[0048] DWORD dwInsLen; / / Instruction length
[0049] union
[0050] {
[0051] BYTE bOffset;
[0052] WORD wOffset;
[0053] DWORD dwOffset;
[0054] }; / / offset
[0055]} CODE_FLOW_NODE, *PCODE_FLOW_NODE;
[0056] Take the experimental comparison method, use other packing software to pack the PE file and the present in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com