A method for automatic real-time judging of IT system security situation
A technology of an IT system and a determination method, applied in the field of network information system security, can solve the problems of inability to ensure the predictable threat control of system vulnerability security management, inability to reflect the security threat status of the IT system in real time, and inability to automatically determine the security situation of vulnerabilities in real time, etc. Achieve the effect of improving timeliness and targeting, shortening window time, and reducing system security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
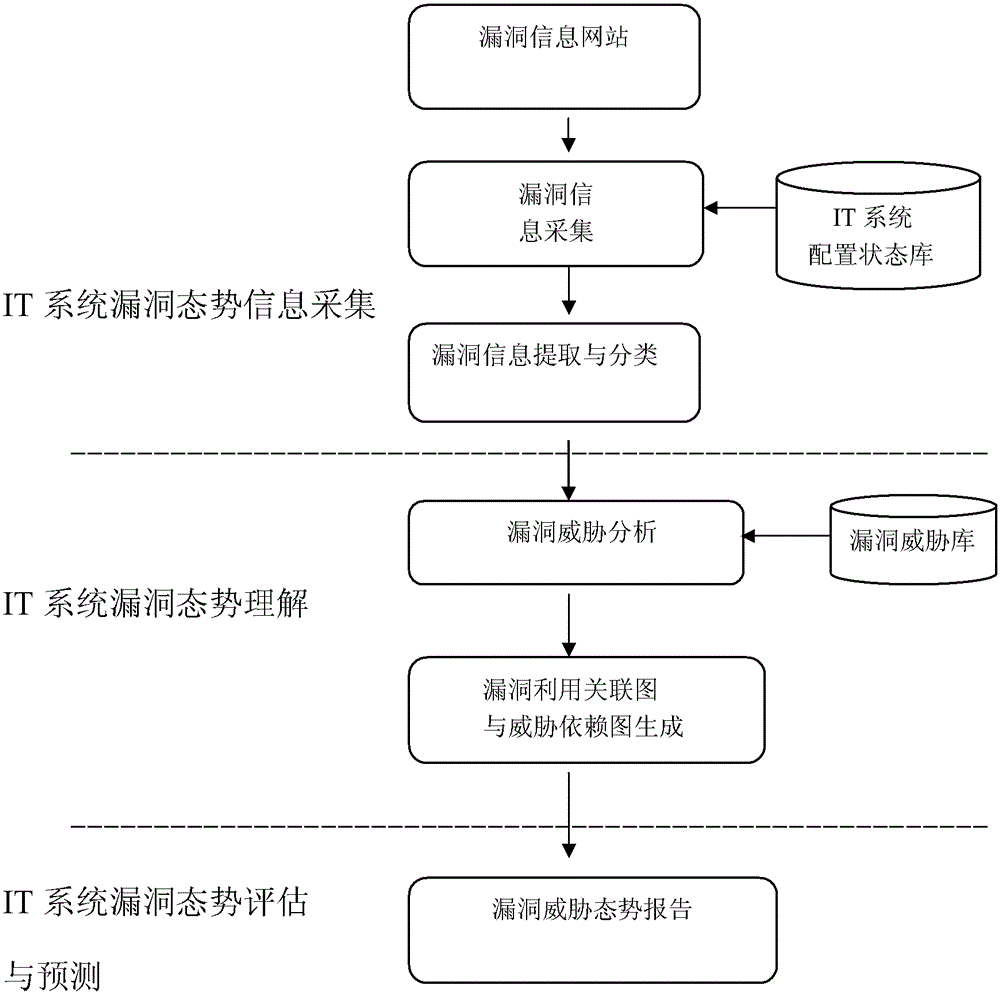
[0045] The method for system security situation analysis proposed by the present invention comprises the following steps:
[0046] 1) Establish a database identifying IT system characteristics and environments. The system characteristic information mainly includes OS system name and version number, database system name and version number, application system name and version number. These feature information can be collected automatically or manually through network management software.
[0047] 2) Establish a threat information source website library. The website library is the status library of the IT system software version. Select a number of current mainstream security websites and add them to the website library as the source of information capture.
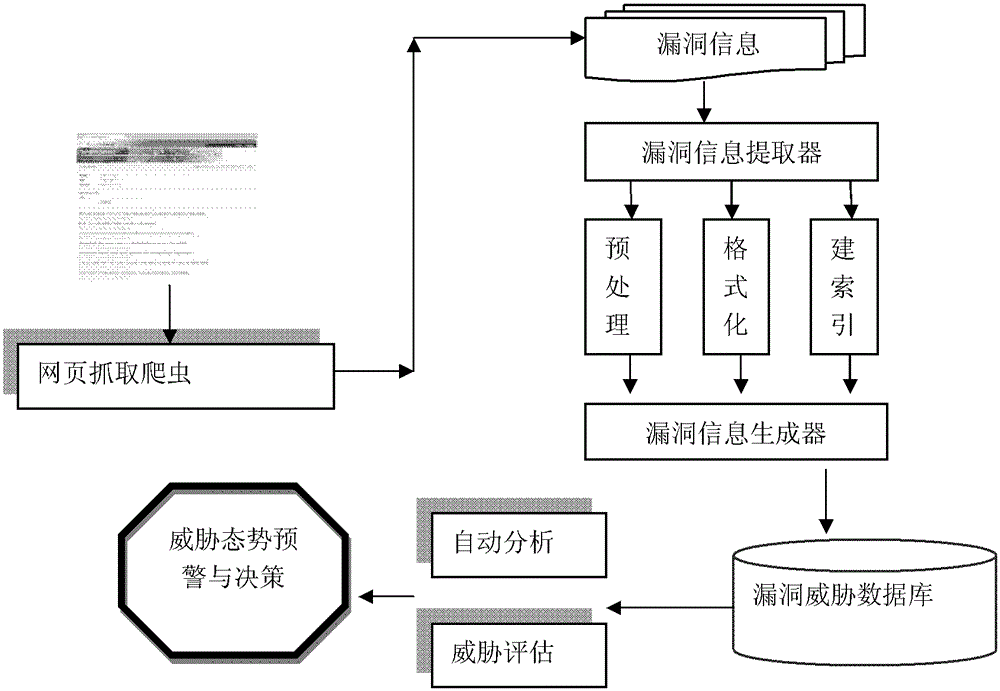
[0048] 3) Implement a program for automatically extracting web pages, which automatically downloads web pages from the threat information source website database, mines security situation vulnerability data, extrac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com