Enabling users to select between secure service providers using key escrow service
A technology of security services and security components, which is applied in the use of key escrow services to enable users to choose fields between security service providers, and can solve problems such as inaccessibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
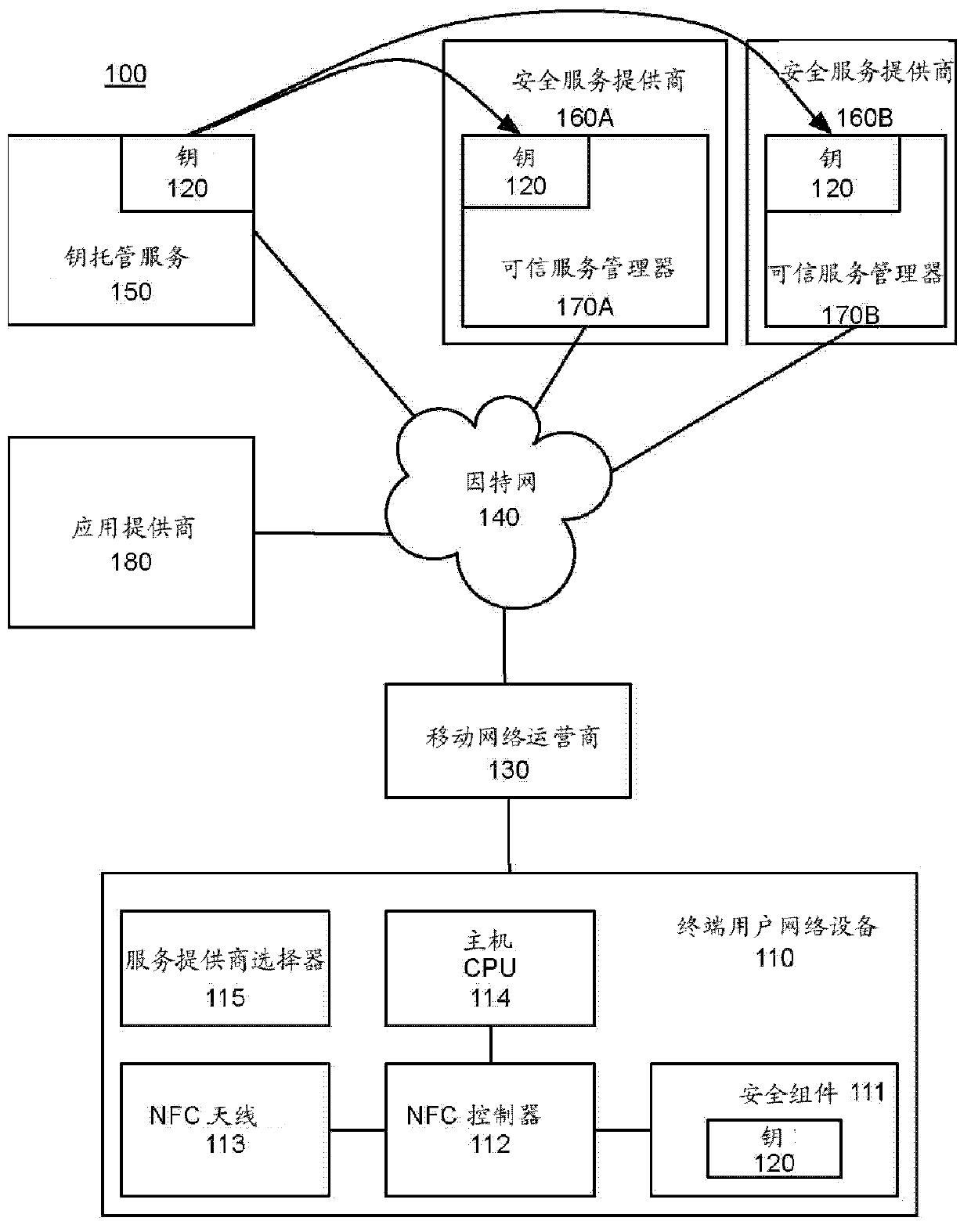
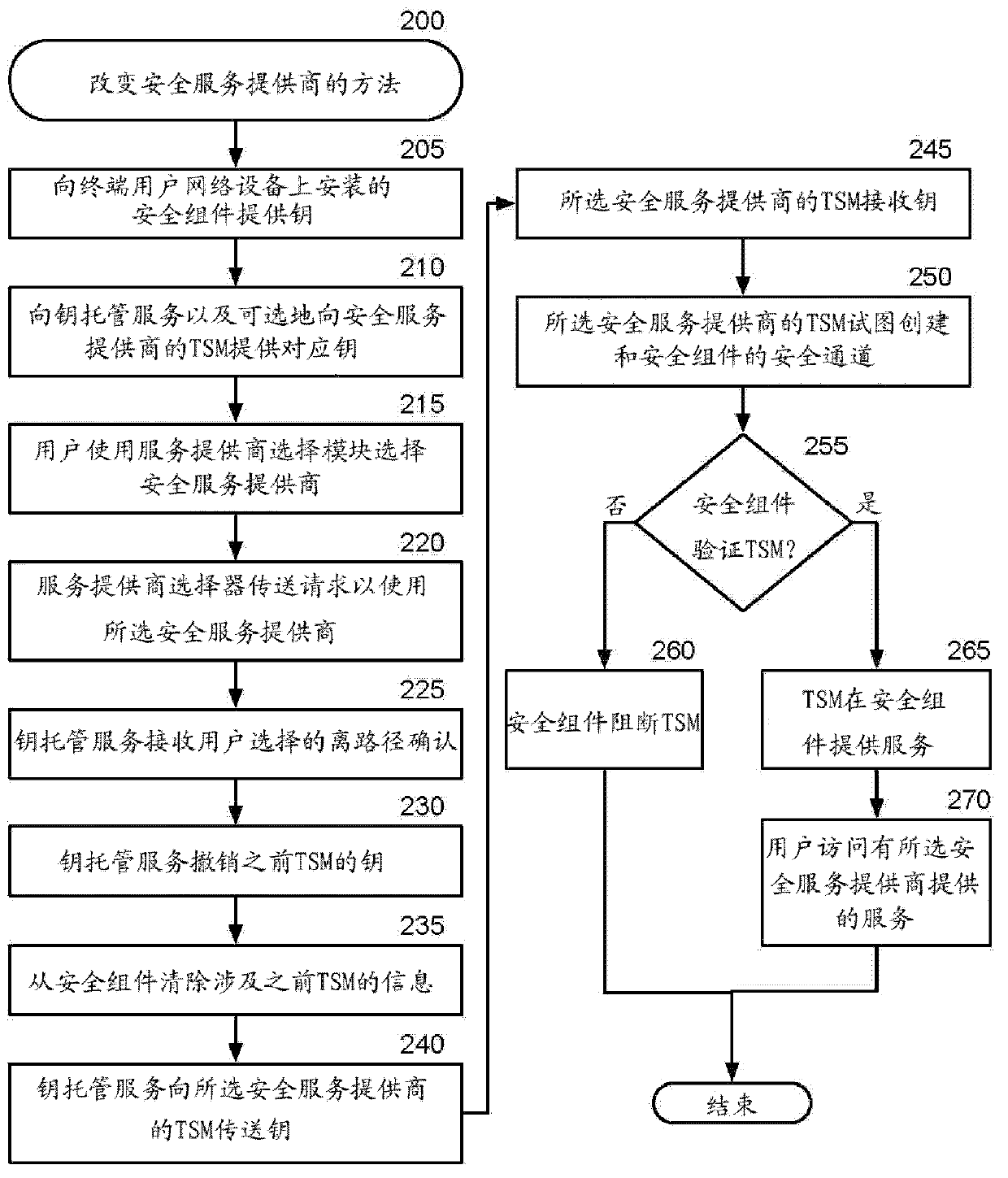
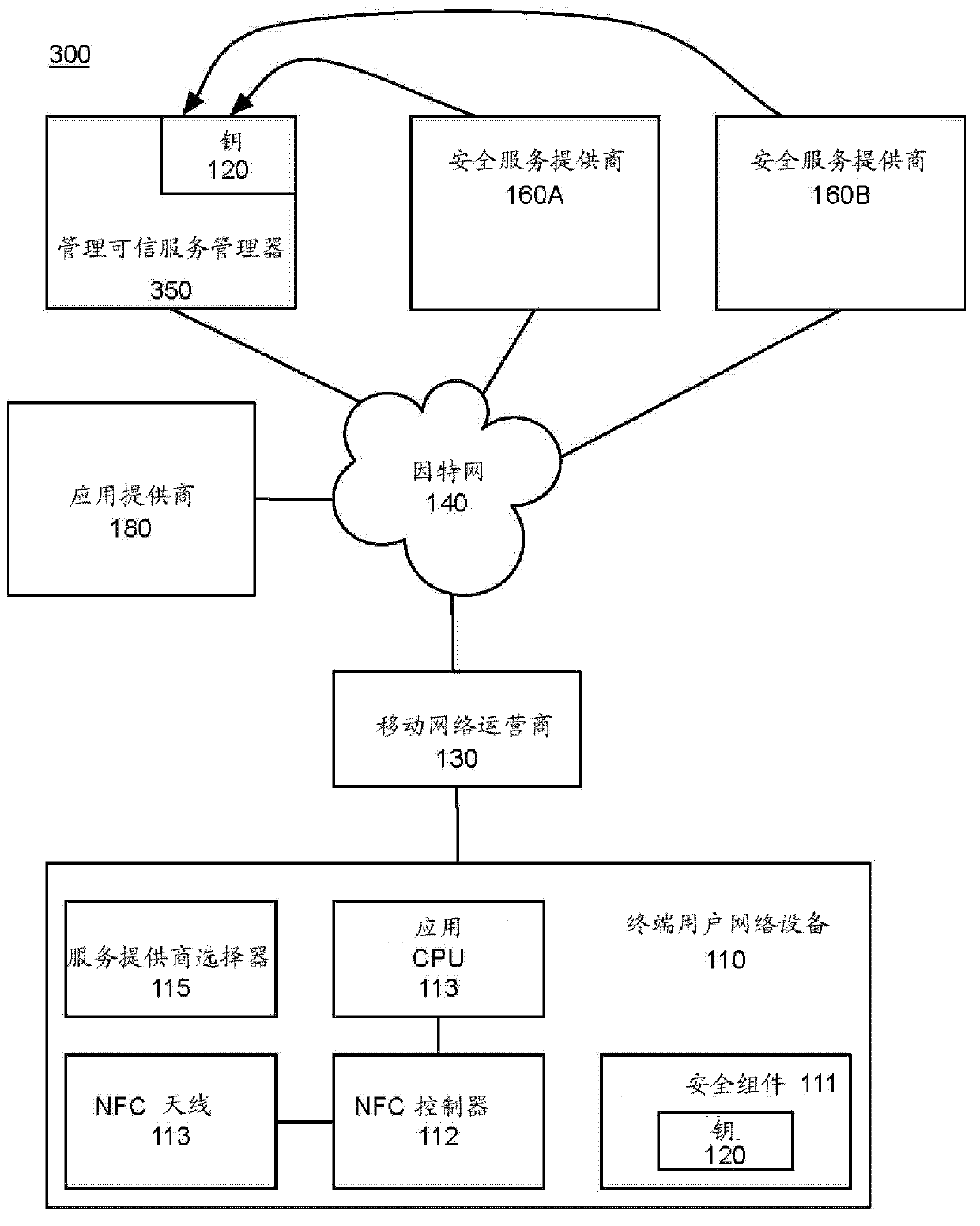
[0012] overview
[0013] The methods and systems described herein enable an end user of a communication device, such as a mobile phone, to select a security service provider to use a security component stored on the communication device. In one embodiment, the system includes a key escrow service that manages keys for one or more users and one or more security service providers. Typically, the security component and one or more keys for the security component are installed on each user communication device when the communication device is manufactured. These keys, or corresponding keys, are provided to a key escrow service. Each user device also includes a service provider selector ("SPS") module or software application that enables the user to select from available security service providers. The SPS transmits information identifying the selected service provider to the user's secure component over the secure channel in response to the user's selection. The key escrow serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com