Credential verification and issuance through credential service providers
A certificate and issuer technology, applied in user identity/authority verification, wireless communication, secure communication devices, etc., can solve the problems of inability to verify, difficult to verify the authenticity of ID cards, and expensive verification infrastructure.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] A term is used herein in the broadest manner in which it is to be interpreted, even if it is used in conjunction with a detailed recitation of a particular embodiment of that term. Certain terms may be highlighted below; however, any limiting terms will be clearly defined in this section.
[0023] The embodiments described below can be implemented through programmable circuits programmed or configured by software and / or firmware, or through special function circuits as a whole, or a combination of the above. The special function circuit (if present) can be implemented in the following forms, for example: one or several application-specific integrated circuits (ASICs), programmable logic devices (PLDs), field programmable logic gate arrays (FPGAs), etc. .
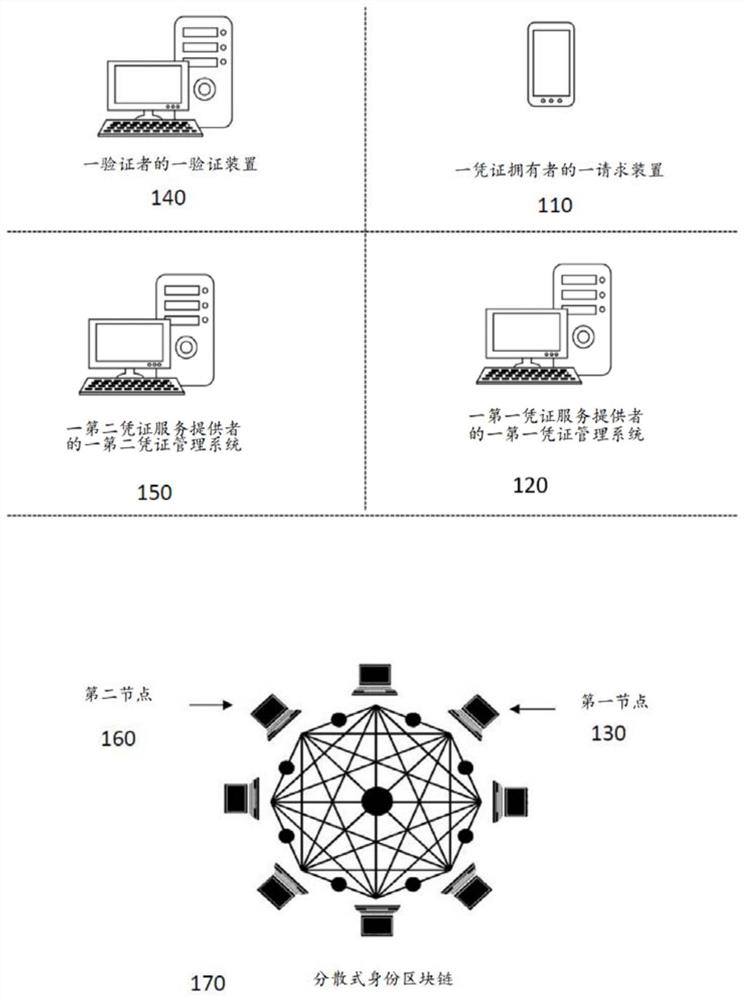
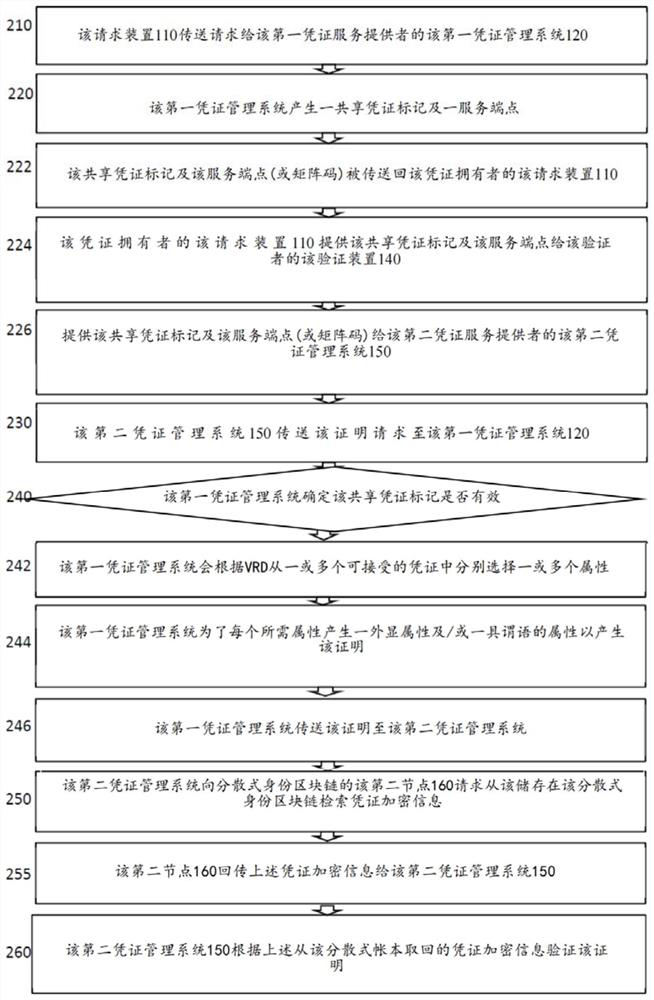
[0024] The embodiments described below relate to one or more methods, systems, devices, and computer-readable media that can store processor-executable steps for verifying a credential A required credential for the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com