Intranet security unified management platform and management method of management platform
A management platform and information system technology, which is applied in the field of integrated network security system, can solve problems such as access equipment cannot access the network, heavy workload, lack of guidance to access the network, etc., and achieve the effect of access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
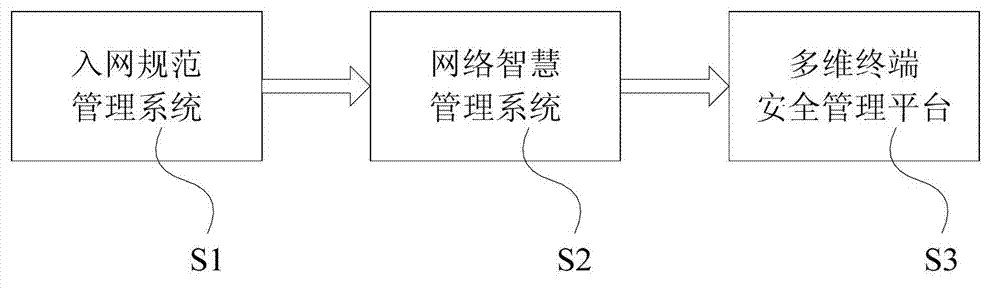
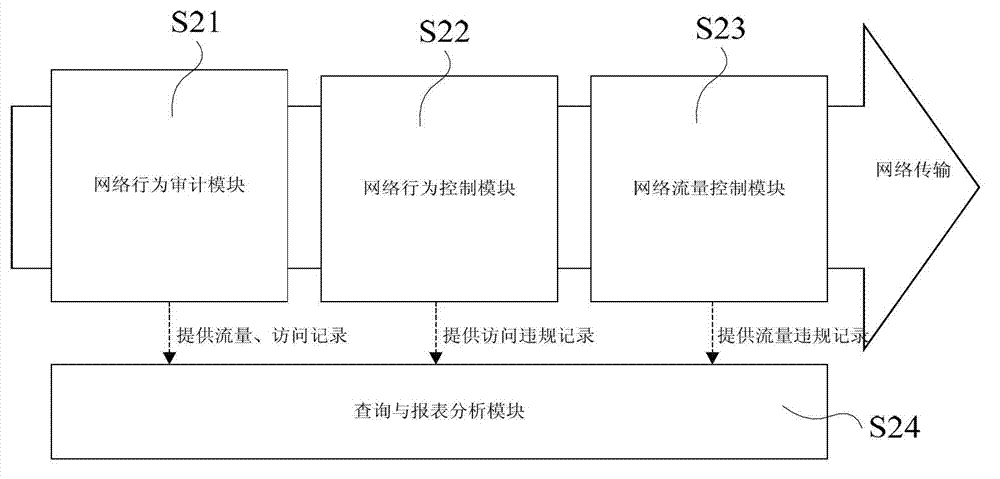
[0041] An information system intranet security unified management platform, including such figure 1 The network access standard management system S1, the network intelligent management system S2, and the multi-dimensional terminal security management platform S3 are shown. The network access standard management system S1 performs access control on network access equipment and personnel security, and the network intelligent management system S2 is aimed at The device network flow and network access behaviors are controlled and audited, and the multi-dimensional terminal security management platform S3 performs real-time monitoring and management response for terminal configuration and application management.
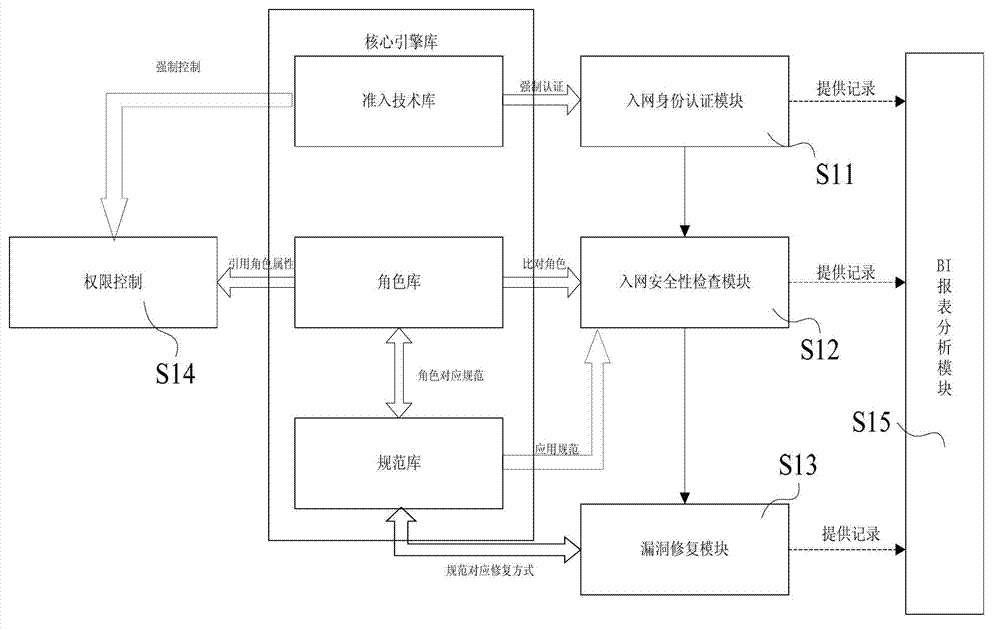
[0042] see figure 2 , the network access specification management system S1 includes a network access identity authentication module S11, a network access security inspection module S12, a vulnerability repair module S13, an authority control module S14, a BI report anal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com